Protecting the World's Critical Infrastructure
The OPSWAT cybersecurity platform gives public and private sector organizations the critical advantage in protecting their most complex environments.
Into the Breach
A New Cybersecurity Docuseries Hosted by
Kari Byron
Join MythBusters’ Kari Byron as she investigates critical vulnerabilities
in cybersecurity, uncovering how real today’s threats are and what’s
being done to stop them.


Ready to Rethink Cybersecurity?
Turn Your World Upside Down
Cybersecurity Upside Down is part technical guide, part personal
journey, and part call to action.
Author Benny Czarny shares the frustrations, failures, and insights
that led to the development of prevention-first security — grounded
not in theory, but in real-world constraints and adversarial reality.


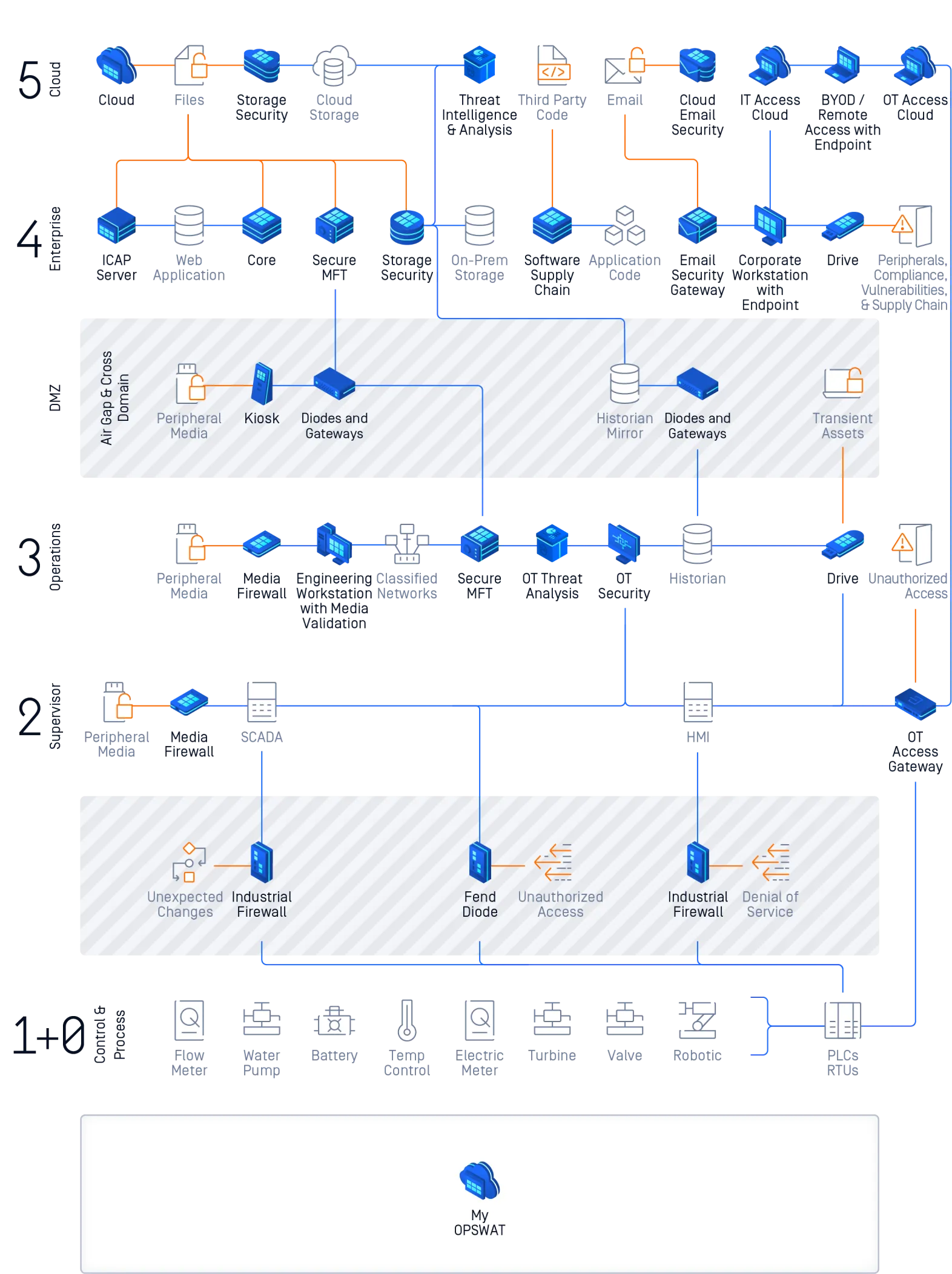
Cybersecurity for Critical Environments

Protect Your Critical Environment From File-Borne Threats on Any Media Type and Enforce Compliance All the Way Through to the Endpoint


Secure Your Software Development Lifecycle and Meet Compliance Standards


Protect Your Critical Environment From File-Borne Threats on Any Media Type and Enforce Compliance All the Way Through to the Endpoint


Secure Your Software Development Lifecycle and Meet Compliance Standards



Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.
The MetaDefender Platform

Explore the Platform

Trusted to Protect Critical Networks
We understand the evolving threat landscape and have spent the last 20 years innovating resources that solve some of the biggest challenges in critical infrastructure cybersecurity
Trusted Globally to Defend What's Critical
OPSWAT is trusted by 2,000+ organizations worldwide to protect their critical data, assets, and networks from device and file-borne threats.
#1 Market Leader in Multiscanning and Deep CDR™ Technology

Deep CDR™ Technology: First and Only to Achieve 100% Total Accuracy Rating from SE Labs
Global Reach, Trusted Expertise.
We’re here to help. Whether it’s answering your questions and supporting the installation and implementation of OPSWAT solutions or managing them entirely, our experts have your back no matter where you are in the world.
What You Need to Know in Cybersecurity
Featured Articles

OPSWAT Research Center
All the information you need to make smarter cybersecurity decisions.
Expertise & Insights
Staying informed is critical in the rapidly changing threat landscape. Learn directly from our experts with insights surrounding today's most significant risks.
Free Tools
MetaDefender Cloud for Community
MetaDefender Access for Community
MetaDefender Endpoint
Learn How OPSWAT Can Protect Your Critical Infrastructure
What are you waiting for? Get started with one of our experts today and discover how the MetaDefender Platform can prevent threats from impacting your critical infrastructure.