Zero-Day Detection
for MetaDefender Cloud
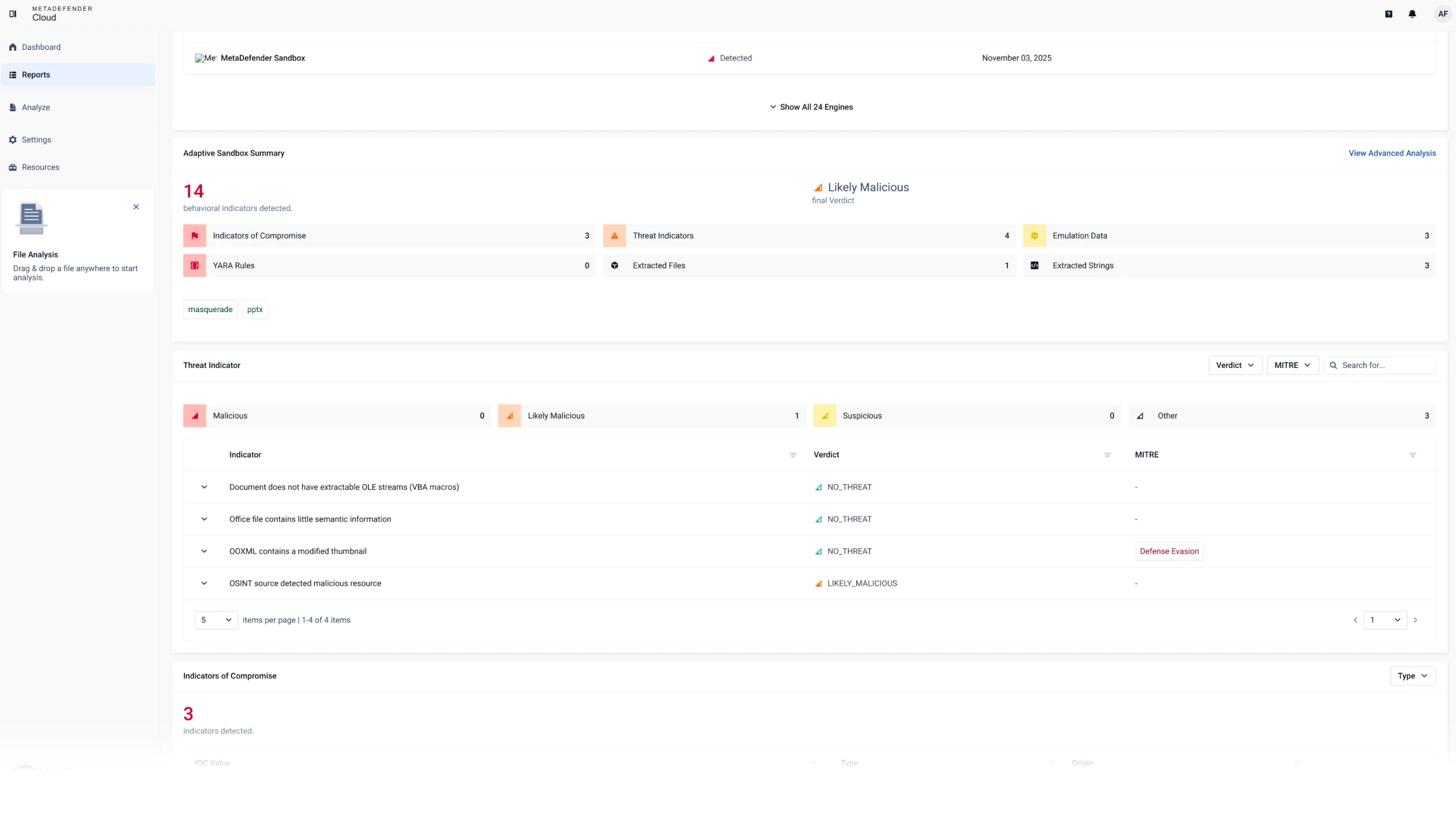
The Adaptive Sandbox detonates evasive malware in a secure cloud environment and
feeds results into threat intelligence to shrink time-to-insight.
- Unmatched Zero-Day Detection
- Real-Time Threat Analysis
- Set up instantly
Unified Zero-Day Detection

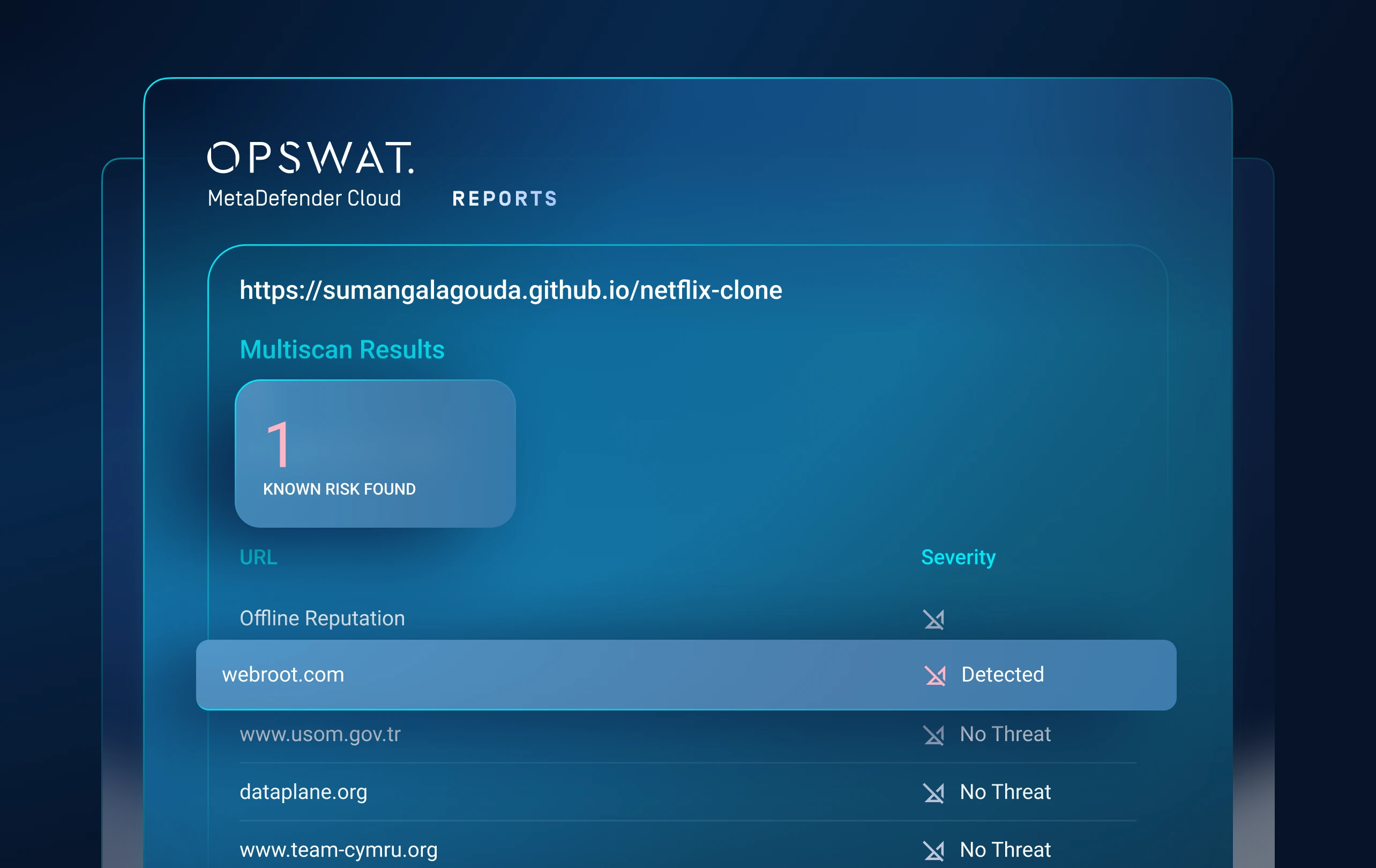
Layer 1: Threat Reputation
Expose Known
Threats Fast
Stop the flood of known threats.
Checks URLs, IPs, & domains in real time or offline to detect malware, phishing, & botnets.
Blocks reused infrastructure & commodity malware and forces attackers to rotate basic indicators.
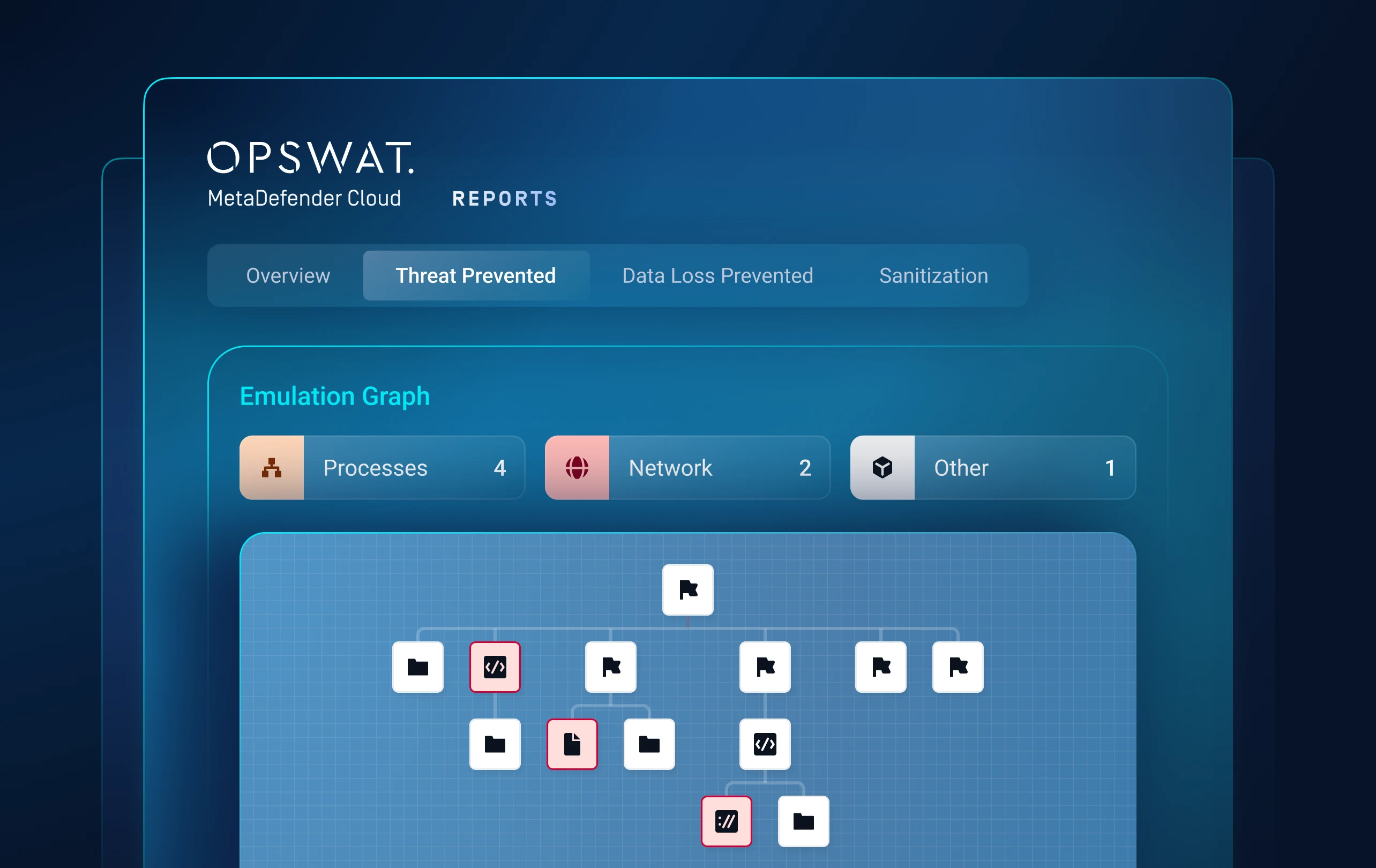
Layer 2: Dynamic Analysis
Uncover Unknown
Threats
Detects evasive malware hiding from traditional sandboxes.
An emulation-based sandbox analyzes files to detect hidden threats like ransomware.
Exposes artifacts, loader chains, script logic and evasion tactics.
Layer 3: Threat Scoring
Prioritize Threats
Reduce alert fatigue.
Threat risk levels are ranked to quickly highlight priority threats in real-time.
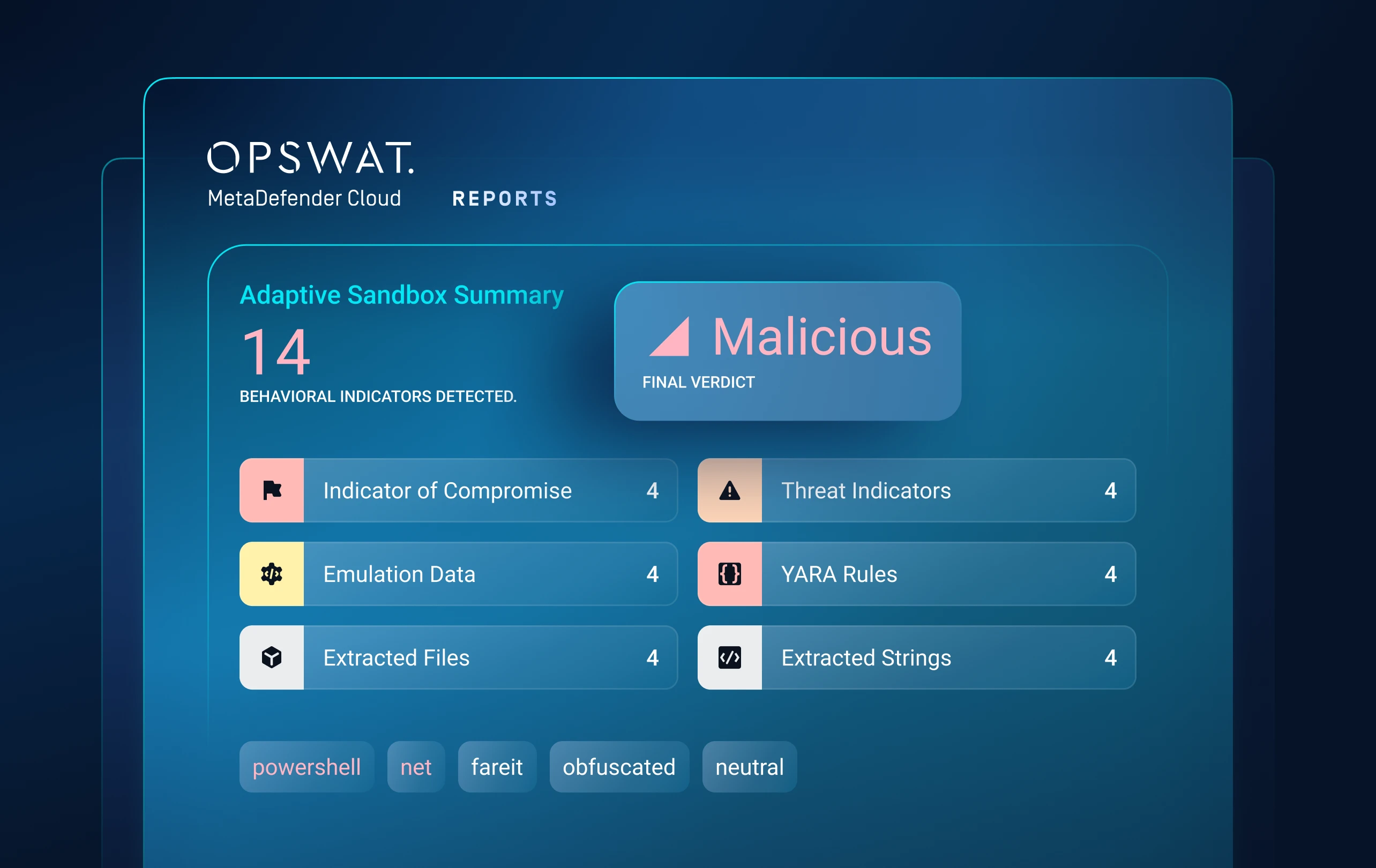
Layer 4: Threat Hunting
Identify Malware
Campaigns
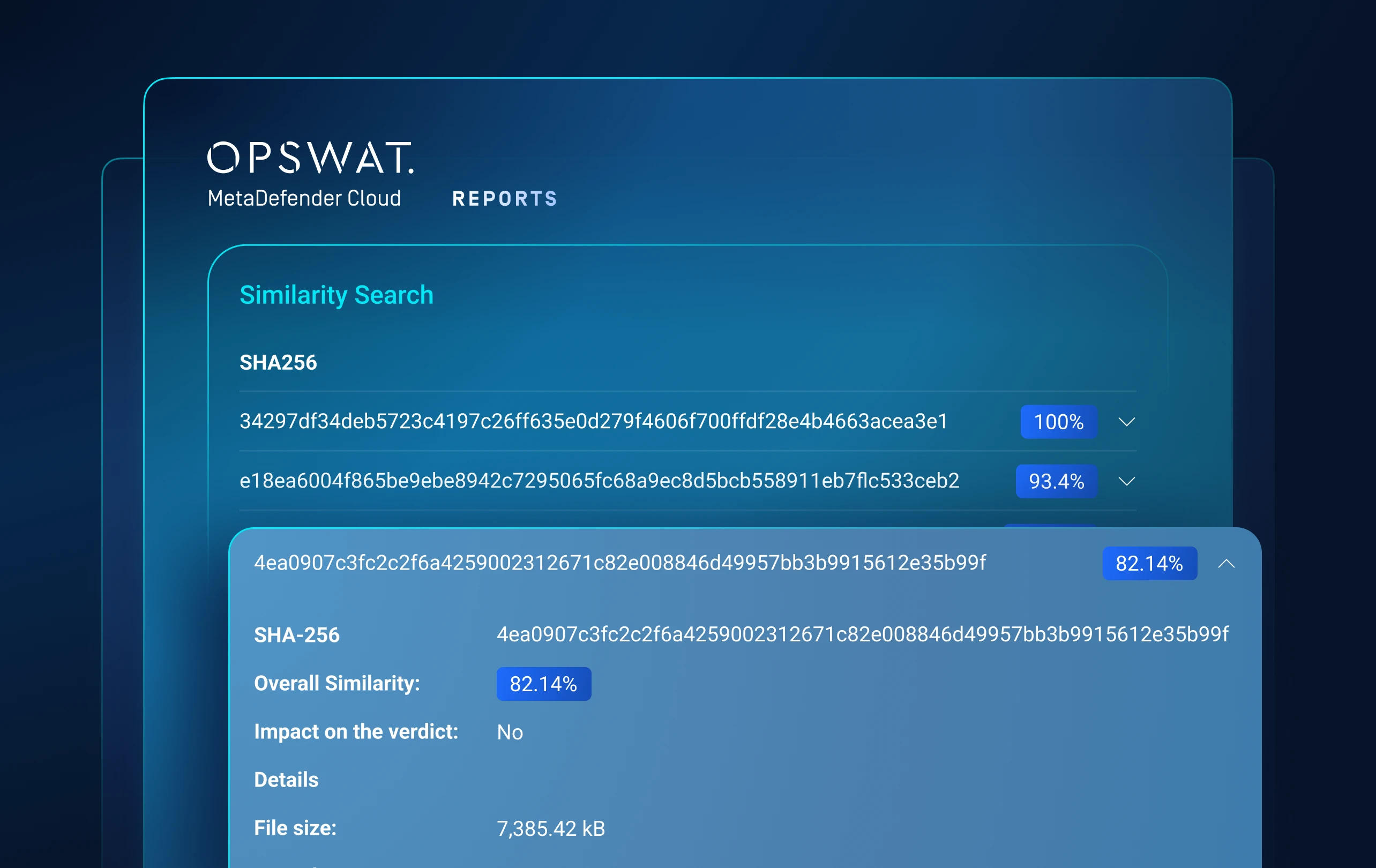
Machine-Learning Similarity Search
Threat Pattern Correlation matches unknown threats to known malware, tactics, infrastructure and more.
Uncovers malware families and campaigns, forcing attackers to overhaul tactics and infrastructure.
Get Started in 3 Simple Steps
OPSWAT Activates Access
Your package is activated by an OPSWAT representative.
Drag and Drop Files
Select a file for dynamic analysis.
Get Results
View sandbox verdicts, threat scores, & IOCs directly within your Cloud dashboard.
- MetaDefender Cloud
- MetaDefender Cloud
- MetaDefender Cloud
Adaptive Sandbox Engine Features
for MetaDefender Cloud
The following table outlines Adaptive Sandbox for MetaDefender Cloud engine feature set. It doesn’t include platform features, such as the API coverage, configurable Access Control List (ACL), OAuth integration, Common Event Format (CEF) syslog feedback, etc.
Please contact us to book a technical presentation and get a run-through of all platform features and capabilities.
Adaptive Sandbox Integrations
for MetaDefender Cloud
Inside OPSWAT / SaaS Ecosystem
- MetaDefender Cloud public APIs (files, hashes, URLs, domains)
- Reputation and threat intelligence APIs (URL, domain, IP, hash lookups)
- Other OPSWAT cloud modules and services

External / 3rd-party Integrations
- REST API for file, URL, IP, and domain submissions with sandbox analysis results
- SIEM / logging platforms through API or event export
- Developer tools (CI/CD pipelines, repositories, SDKs, plugins)
- SOAR / orchestration platforms through API integration

Cross-environment / Hybrid
- Private file processing / scanning options for sensitive environments
- On-prem MetaDefender Core using Cloud reputation and threat intelligence services

Support Compliance
with Regulatory Requirements
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are
implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure.
Recommended Resources

MetaDefender Aether for Cloud

SANS Detection & Response Survey

2025 OPSWAT Threat Landscape Report
FAQs
Large-scale, cloud-native detonation for files and URLs-perfect for email security/OEMs and teams that need elastic capacity without running their own sandbox farm.
Enhanced ML web threat detection (multi-label classification, structure/style analysis), PDF phishing heuristics, brand detection, and JavaScript/clipboard emulation to surface "template kits," QR smuggling, and low complexity phishing at scale.
Simple API (submit file/URL, get verdict/IOCs), plus MISP/STIX exports, Splunk SOAR/Cortex XSOAR connectors, and auto-generated YARA for follow-on hunting.
Auto-scaling with fast emulation keeps latency low while avoiding VM overhead; policy routing ensures you only detonate what's necessary-so you control volume and spend.
Yes-mix cloud for burst/URL analysis with on-prem sandbox for sensitive or sovereign data. Policies decide where each sample runs.