MetaDefender InSights TI
Proactive Threat Intelligence to Stay Ahead of Cyber Adversaries
Leverage InSights TI to detect, analyze, and neutralize threats in real time—ensuring your organization stays one step ahead of attackers.
Stay Ahead of Evolving Threats with Near Real-Time Intelligence
InSights TI is a comprehensive threat intelligence solution designed to provide your organization with real-time, actionable data on adversary tactics, techniques, and procedures (TTPs). Our curated intelligence feed helps you detect and mitigate threats before they can impact your business, delivering timely insights across a range of attack vectors, including malware, phishing, and vulnerability exploitation. Whether you’re managing complex security operations or defending a small network, InSights TI gives you the tools to make informed decisions and respond quickly.
Near Real-Time Intelligence Powered by Advanced Data Collection and Analysis
InSights TI delivers timely and enriched threat data to help your security team respond faster and with greater accuracy.

Data Collection and Aggregation
InSights TI aggregates data from multiple sources, ensuring comprehensive coverage.
Near Real-Time Threat Updates
Continuous updates provide your team with the latest information on threats.
Actionable Intelligence
The data provided is enriched with detailed threat classifications and contextual information.

Seamless Integration
InSights TI integrates with your existing security platforms.
Transform Your Security with Next-Generation Intelligence and Capabilities
InSights TI offers a powerful set of features designed to improve threat detection, streamline response times, and provide deeper insights into your threat landscape.
Near Real-Time Threat Detection
Stay ahead of evolving threats with continuously updated intelligence on malware, phishing, and adversary tactics.
Curated Intelligence Feeds
Access highly curated, actionable threat data that is tailored to your organization’s needs, allowing your team to focus on critical threats.
Proactive Threat Hunting
InSights TI empowers security teams to proactively hunt for threats and adversary infrastructure, preventing attacks before they escalate.
Seamless Integration
Integrate with SIEM, SOAR, TIP, and XDR platforms for automated threat detection, enrichment, and response—eliminating manual processes and reducing human error.
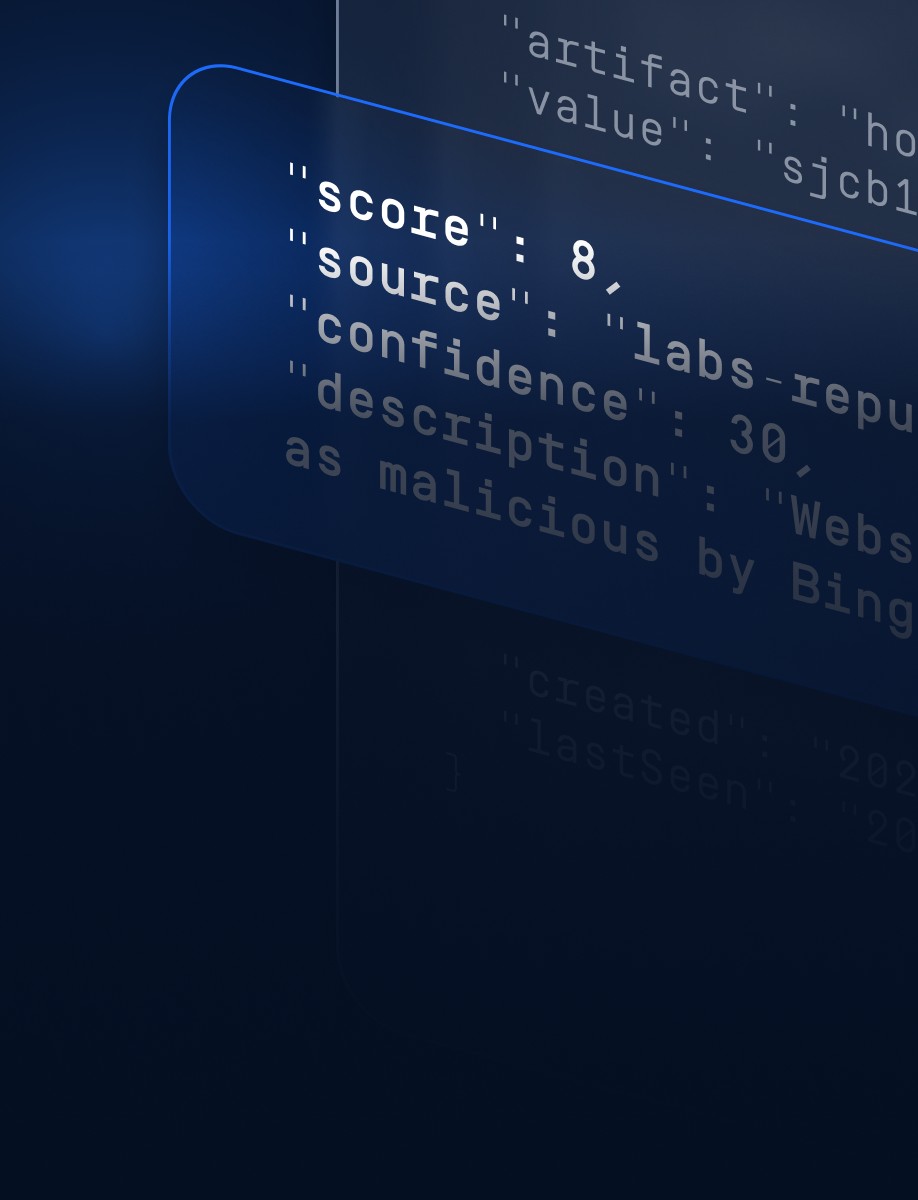
Contextualized Threat Insights
Each threat is enriched with detailed descriptions, reputational scoring, and classifications, helping your team prioritize and take action with confidence.
Purpose-Built for Every Sector
MetaDefender InSights empowers organizations with industry-focused threat intelligence, ensuring proactive defense and compliance across critical sectors.
Technical Documentation
Getting Started
Deployment & Usage
Unlock the Full Potential of Our Products