The Challenge of Securing Software Supply Chains
Supply Chain Risks Across the SDLC
Faster development prioritizes speed over security. Automated CI/CD pipelines can propagate vulnerabilities quickly across environments. With cross-departmental collaboration as teams scale, gaining visibility into these risks is even harder.
Vulnerable Source Code and Containers
The reliance on third-party open-source software introduces vulnerabilities at every stage of the SDLC (software development lifecycle). Modern micro-services architecture also creates opportunities for exploitation across all container layers.
Resource Allocation for Compliance
An increased focus on compliance (e.g. SOC 2, ISO 27001, NIST) demands more transparency and control. Balancing security and compliance efforts with operational needs requires more resources.
Exposed Hardcoded Secrets
Sensitive information is often embedded in code or left unprotected in repositories. Exposed hardcoded credentials provide easily exploitable opportunities for attackers, leading to leakage of sensitive information or illegitimate access to code repositories.
Continuous Monitoring Complexity
Manually tracking software components consumes time and resources. Without the right tools, organizations struggle to monitor their supply chain for emerging risks. Delayed detection can amplify the impact of an attack.
Why OPSWAT?
Multi-Layered Threat Prevention
Detect vulnerabilities and software dependencies. Protect your supply chain from malware with multiscanning. Generate SBOMs (software bills of materials) and continuously track your software components.
Software Transparency Compliance
Uncover PII and secrets in source code with Proactive DLP™. Automate the inventory of software components with SBOM to maintain software integrity, helping organizations stay compliant with regulations like SOC2 and ISO 27001.
Source Code and Container Security
Secure both source code and container images with flexible workflows that can be scheduled or triggered by specific actions. Reduce maintenance costs with an integrated solution that fits seamlessly into your CI/CD pipeline.
Easy to Use and Maintain
Easily integrate into your existing CI/CD tools, or solutions from third-party vendors. Manage roles and automate remediation steps like email alerts and pull request approvals to streamline security management.
Premium Support
Get help when you need it, 24 hours a day, 7 days a week. OPSWAT offers enterprise-level support that ensures quick and reliable assistance tailored to your specific needs.
5 Million
vulnerability database
10+
programming languages
99%+
detection rate with Metascan
Download Sample SBOM Report
Learn How MetaDefender Software Supply Chain Helps You Protect Your Infrastructure
Integrations Made Simple
Whether your team uses source code repositories, container registries, binary services, or a combination of tools, MetaDefender Software Supply Chain provides native integrations with popular platforms to secure throughout your SDLC.
Comprehensive, Multi-Layered Defenses
Metascan™ Multiscanning
With 30+ commercial anti-malware engines, Metascan technology increases detection rates and effectively prevents malware from infecting workstations, containers, or source code.
- Detects malware early in the SDLC.
- Prevents malicious packages (npm, PyPI, etc.), especially in open-source software.
- Flexible AV engines packages to choose from.
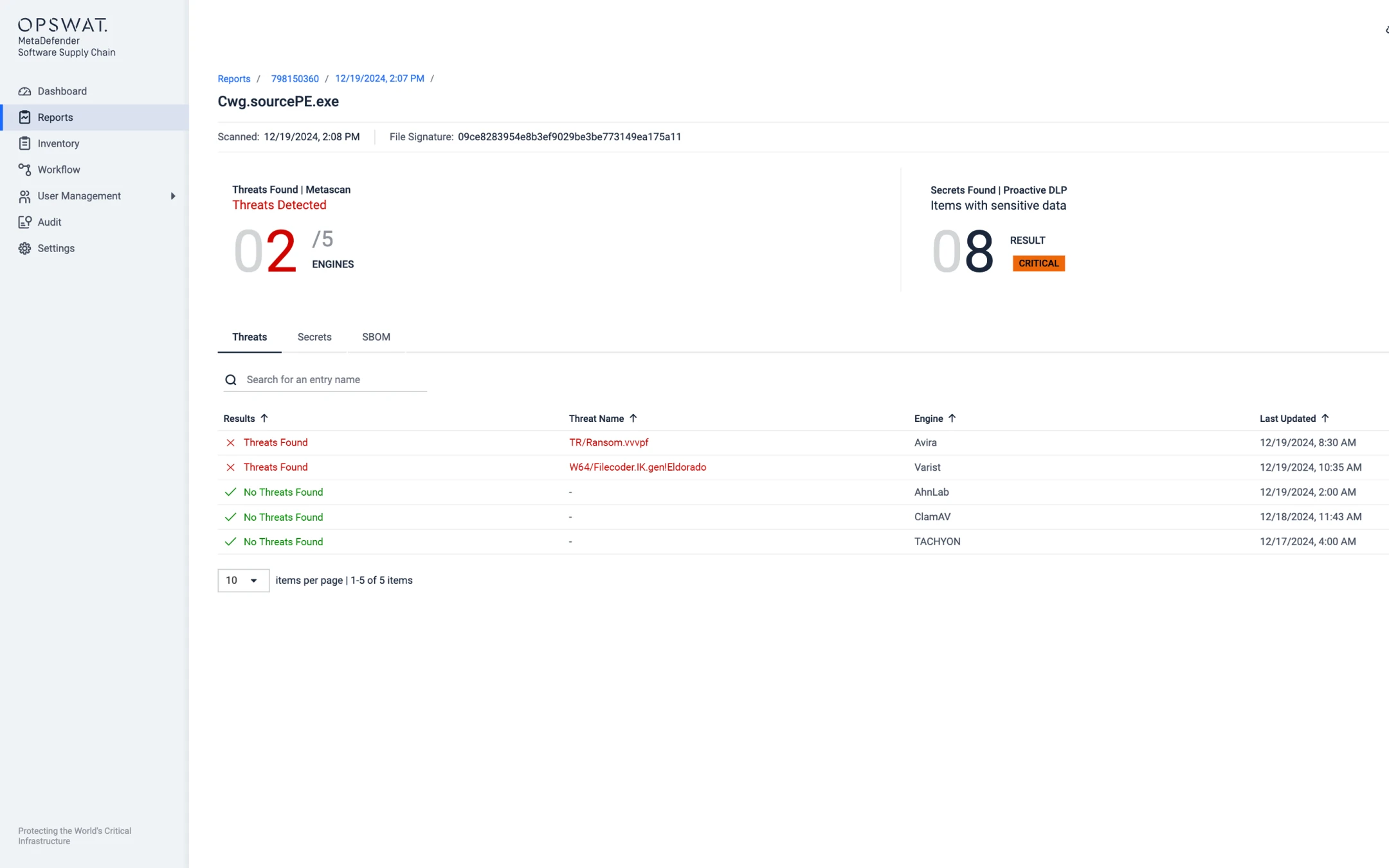
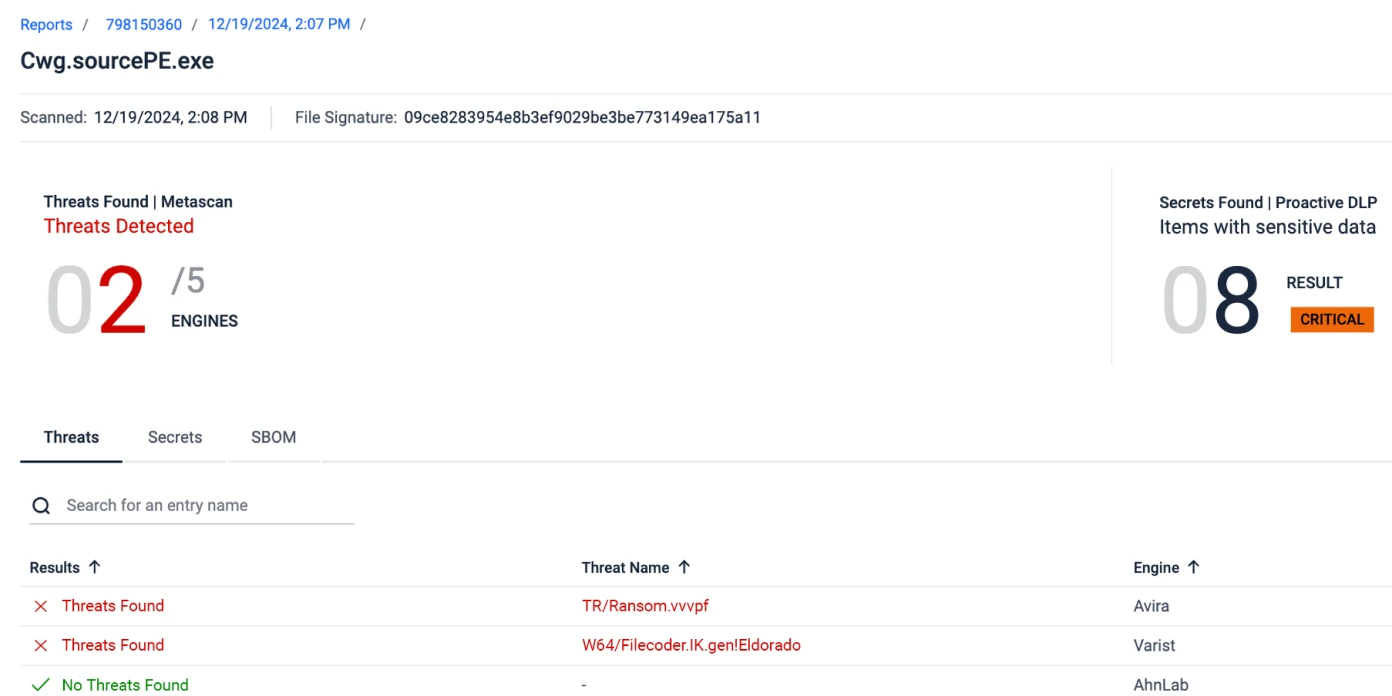
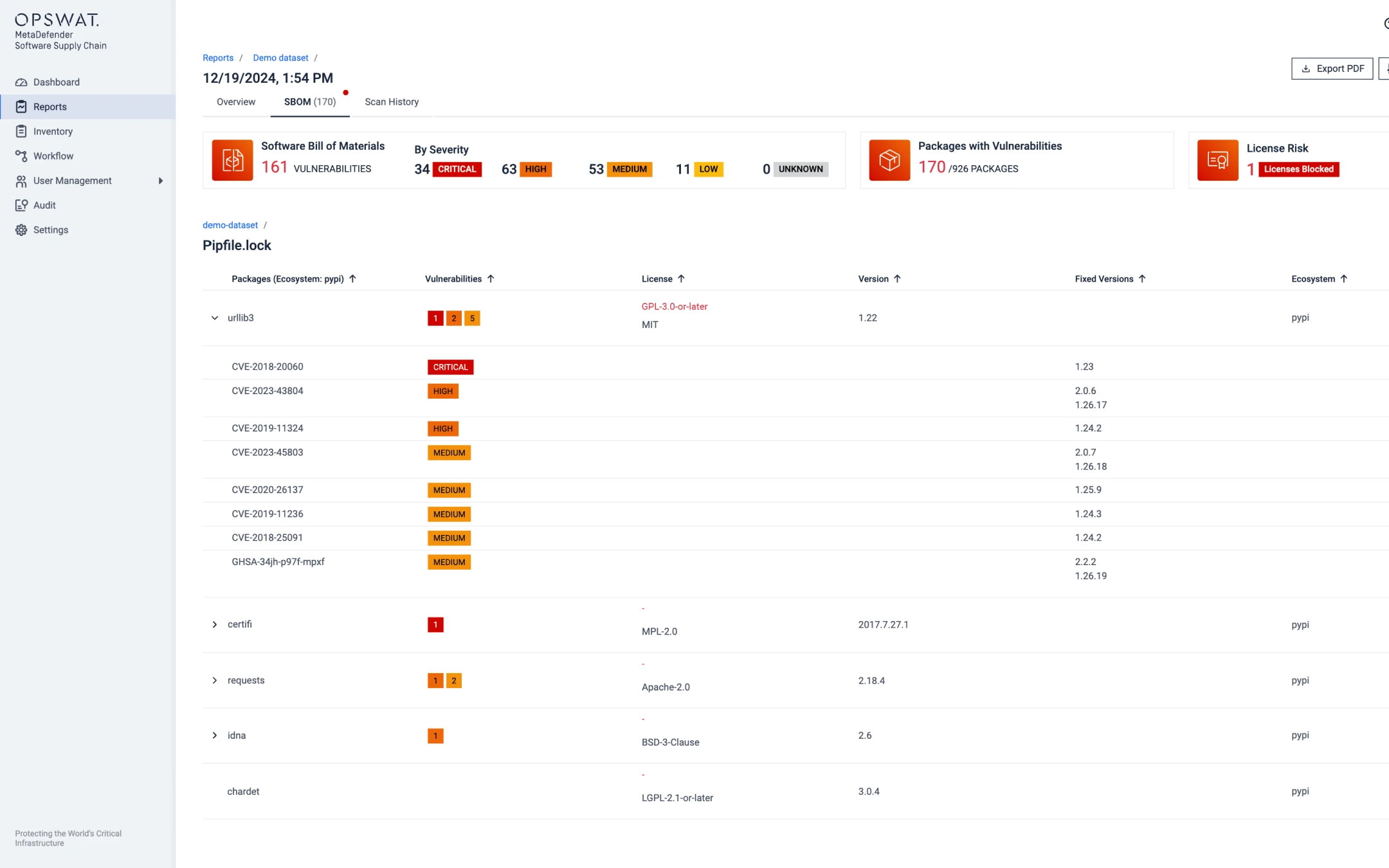
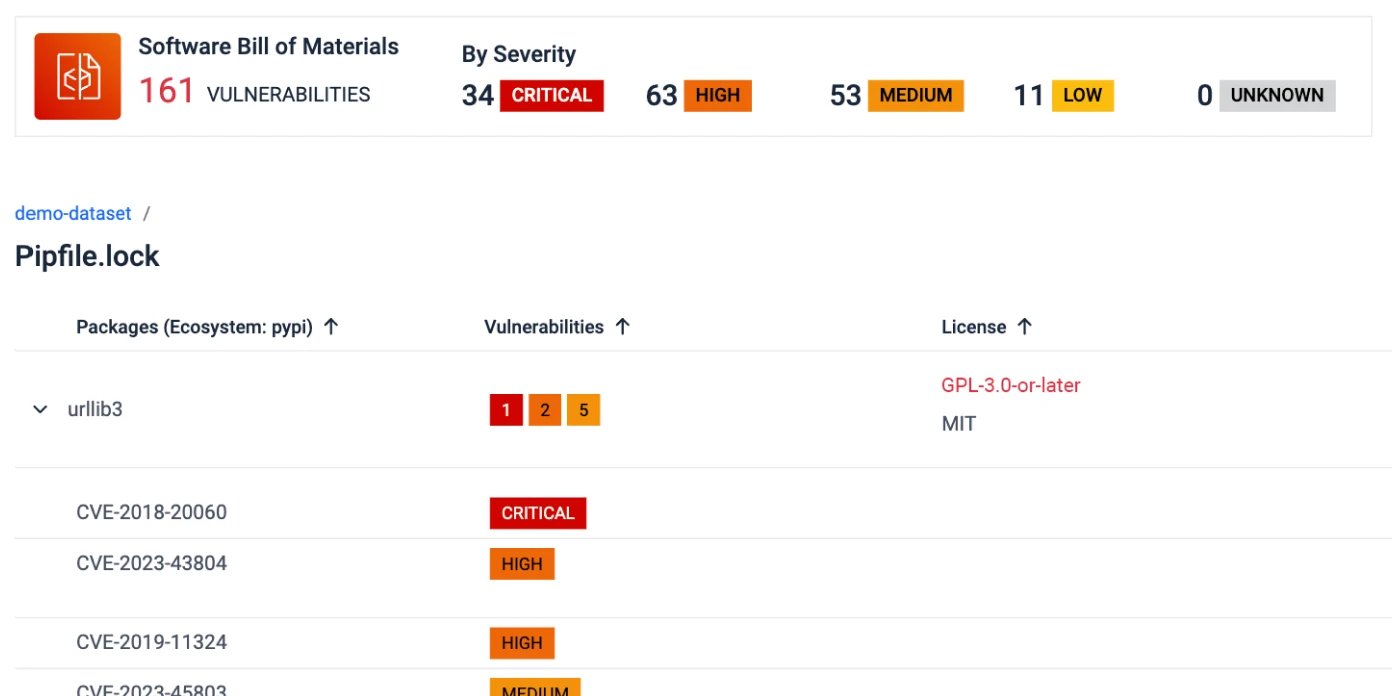
SBOM Generation
MetaDefender SBOM provides developers with an inventory of software components, enabling the detection of vulnerabilities and threats without hindering development speed.
- Monitor critical updates and patches in software components and dependencies, with support for 10+ programming languages.
- Standardized SBOM: Use formats like SPDX and CycloneDX for easy SBOM generation and sharing.
- Validate OSS licenses and avoid high-risk licenses.
- Generate real-time reports for security and GRC (governance, risk, and compliance) teams.
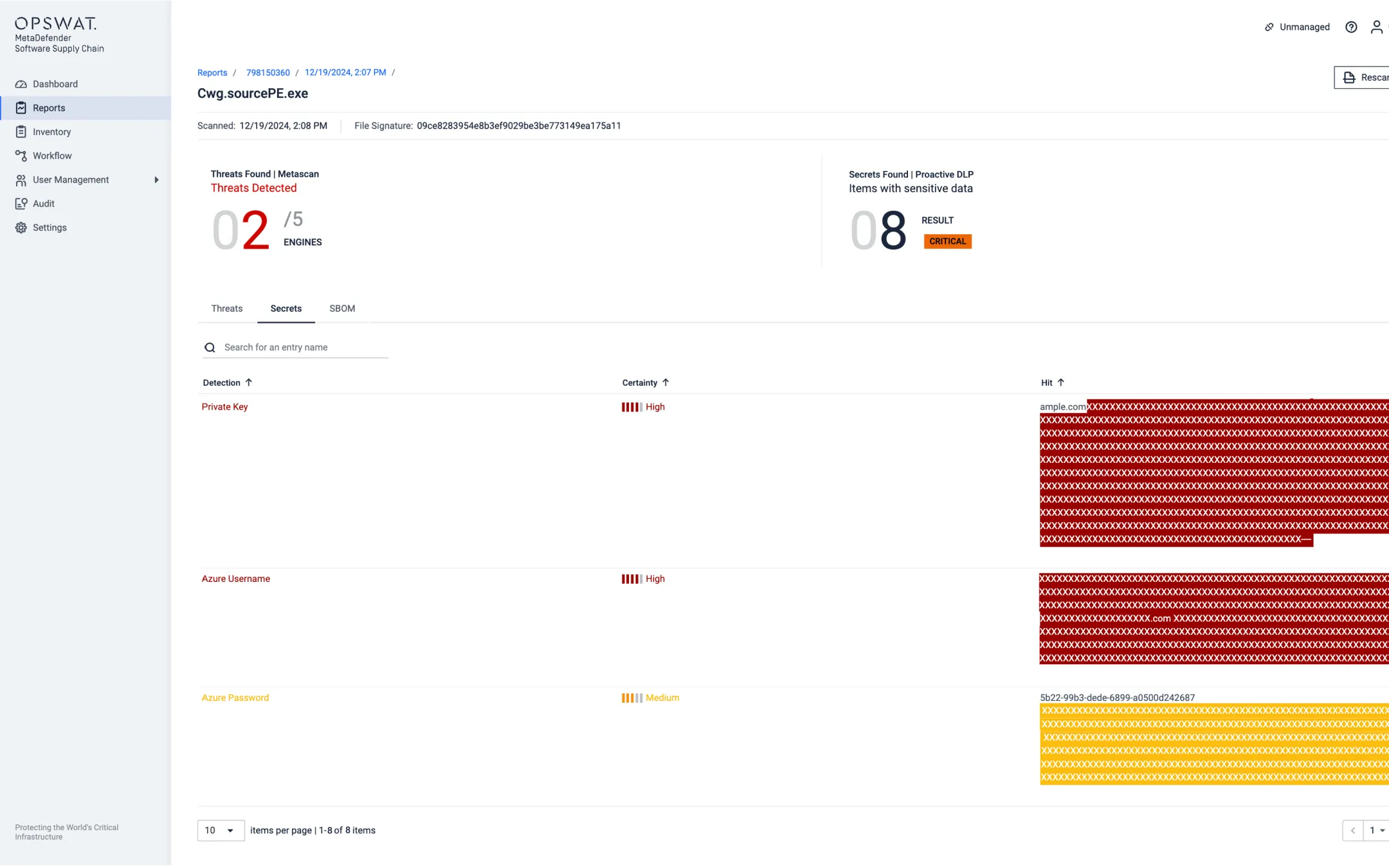
Proactive DLP™
Proactive DLP technology detects sensitive information left in source code. Stay compliant with data protection mandates and keep your SDLC free from unwanted PII leaks.
- Usernames, passwords, access tokens, secrets, authentication IDs, API keys, private keys.
- AWS, GCP, Azure, IBM credentials.
- PostgreSQL and MySQL credentials.

Build Secure, Compliant, and Scalable Software with Confidence
Don’t Just Take Our Word for It.

“We’re using MetaDefender there to scan everything as we build it, to make sure we’re not becoming that supply chain risk.”
Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.