OPSWAT SBOM
Automated SBOM generation for code & containers.
Stay compliant and secure in the software supply chain. With OPSWAT Software Bill of Materials (SBOM), developers can identify known vulnerabilities, validate licenses, and generate component inventory for open-source software (OSS), third-party dependencies, and containers.
10+
5M+
Hidden Threats, Increased Complexity
Tracking dependencies in a large codebase is challenging. Monitoring vulnerabilities in open-source software (OSS) requires constant effort and resources. Hackers exploit vulnerabilities in OSS to gain access to source code, spread malware, and steal data. Moreover, failing to understand licensing in open-source components can lead to legal or intellectual property violations.
It’s unsurprising that governments and industry now mandate SBOMs to ensure a secure software supply chain. OPSWAT SBOM enhances software supply chain security, enabling teams to secure their applications and stay compliant.

You Develop Solutions. We Manage Risks.
Identify & Track Open-Source Software
Accurately identify open-source components and monitor critical software updates and vulnerability patches from 5 million libraries.
Standardized SBOM Structure for Tool Interoperability
Advancing SBOM standardization with industry-standard formats like SPDX and CycloneDX to simplify SBOM generation, sharing, and consumption.
Reduce Vulnerabilities in Software & Containers
Compare software components to a database of 17,000+ vulnerable libraries to reduce risk exposure in source code and containers.
Stop Threats Infiltrating Your Software Supply Chain
Quickly scan files with OPSWAT Multiscanning by leveraging 30+ leading anti-malware engines to proactively detect over 99% of known malware.
Detect & Secure Secrets in Your Codebase
Detect secrets and passwords in your codebase by integrating with Proactive DLP to automatically generate SBOM/SCA and protect your CI/CD pipeline.
Avoid Costly License Violations
Validate and use approved licenses for OSS and third-party dependencies. Identify high-risk licenses like GNU GPL, GNU LGPL, and more.
Flexible, Automated Scanning
Constantly assess regulatory and internal security guidelines through real-time reports tailored for security engineers and Governance, Risk, and Compliance (GRC) teams.
Cost & Resource-Efficient
Reduce costs by automatically scanning for vulnerabilities in software components and containers.
A Unified Solution for Securing Software

SBOM for Code
Empower developers to identify, prioritize, and address open-source dependencies' security vulnerabilities and licensing concerns.
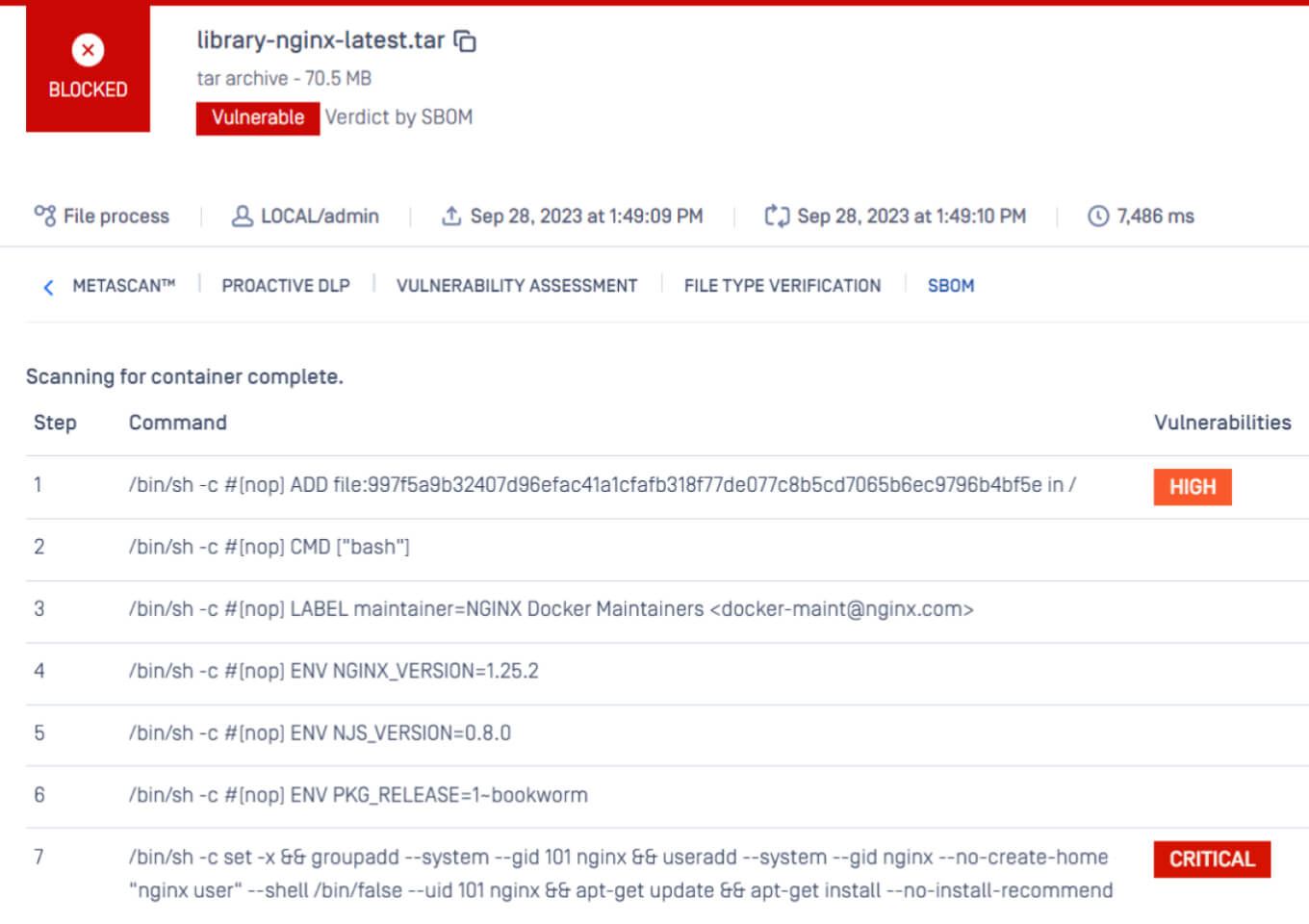
SBOM for Containers
Analyze container images and generate SBOM for the package name, version info, and potential vulnerabilities.
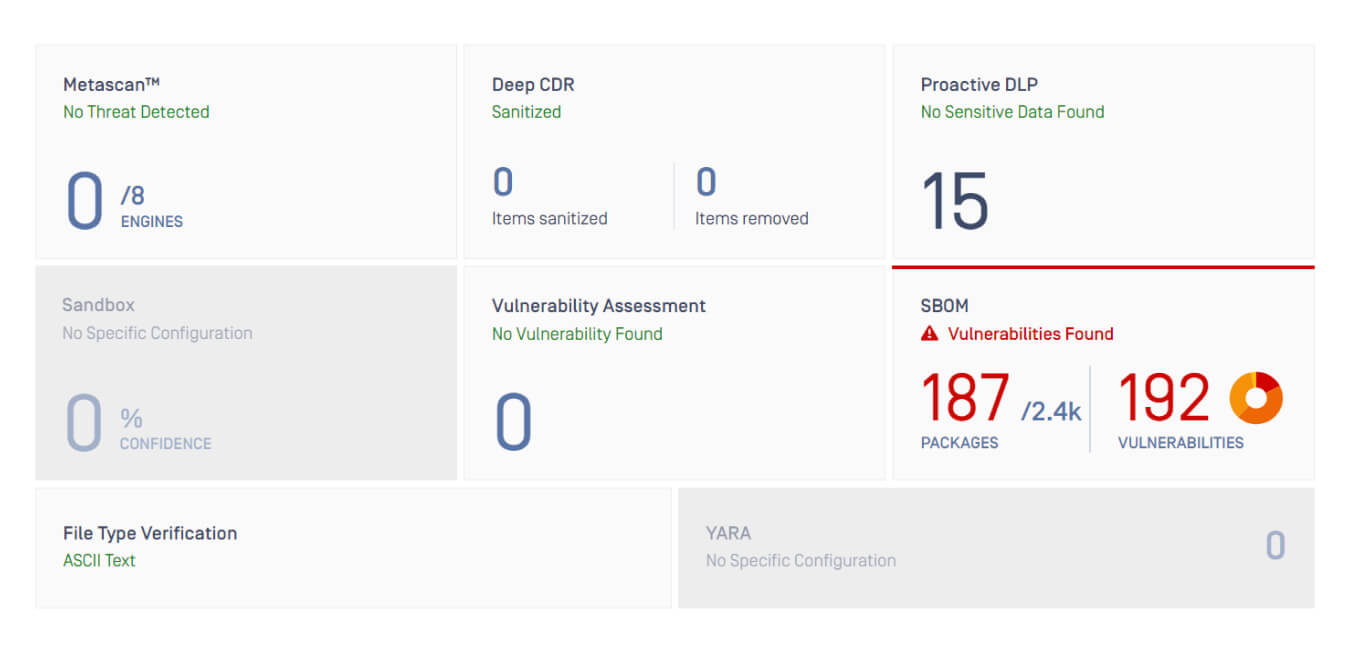
SBOM for Supply Chain Security
Secure the software supply chain from a single platform to increase security, decrease risk, and deliver safe software.
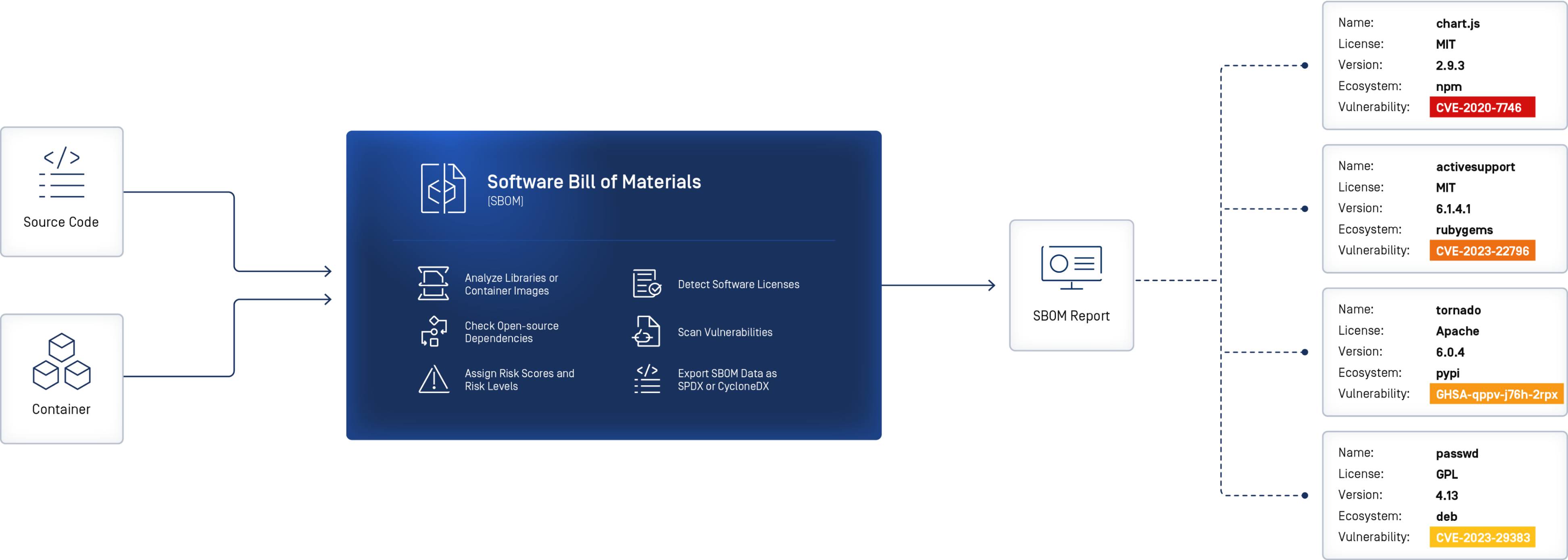
Analyze, Detect, Generate
1. Analyze source code and containers
2. Detect components and vulnerabilities
3. Export SBOM to SPDX or CycloneDX format.
“One of the biggest contractual risks I have to take care of is to make sure we don't become a supply chain risk ourselves to our customers; so we're using MetaDefender Core to help us in that endeavor.”
Learn More About OPSWAT SBOM
Software Bill of Materials (SBOM) Explained
Software Supply Chain Security: What It Is and Why It's Critical