Stop Attacks & Hunt Threats
Real-time threat reputation checks with automated threat hunting in the cloud.
- Real-Time Threat Checks
- Automated Threat Hunting
- Continuously Updated
OPSWAT is Trusted by
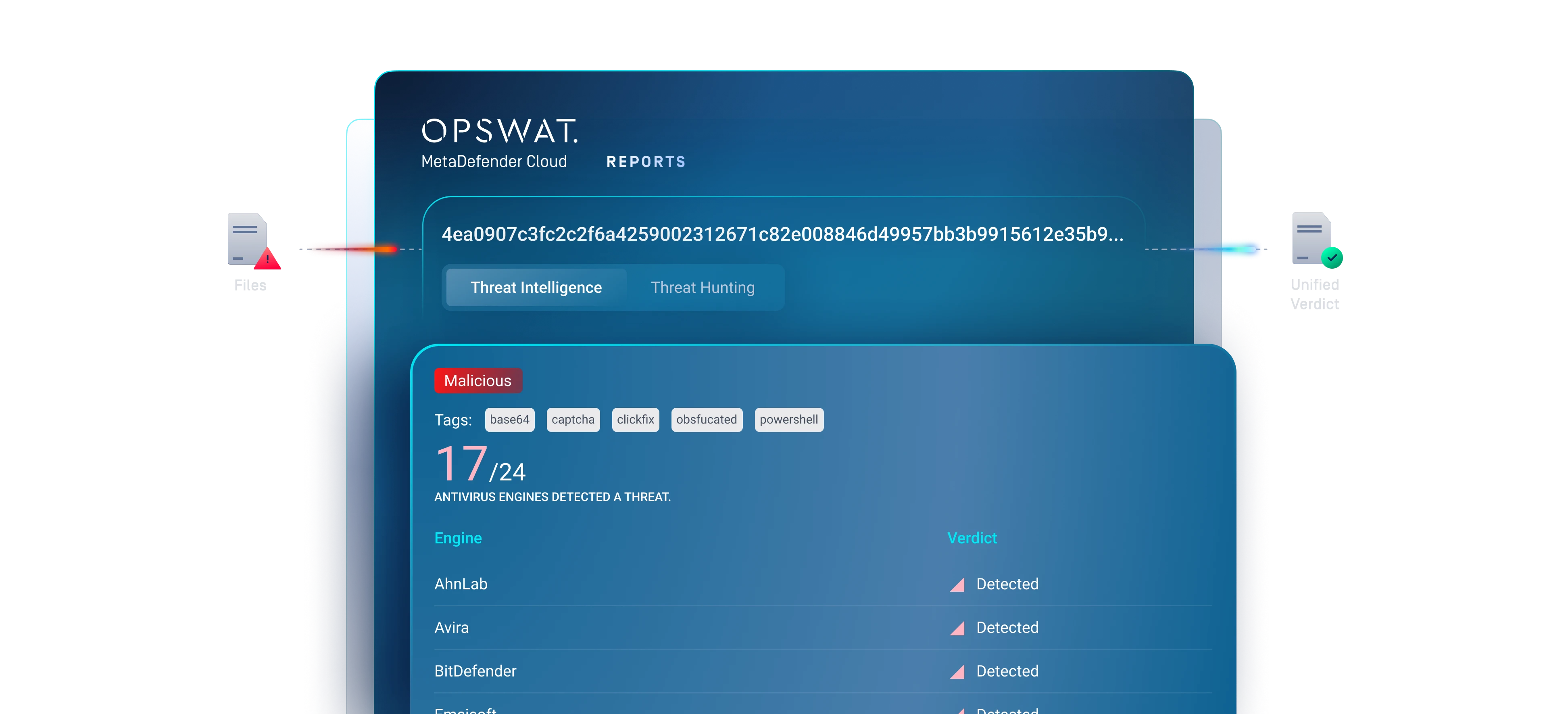
Real-Time Threat Checks & Automated Hunting
MetaDefender Threat Intelligence delivers real-time threat reputation and automated threat hunting
to help teams detect and stop emerging threats earlier. Global sandbox telemetry updates threat indicator lists, enriching every lookup with
deeper context, faster detection, and clearer threat correlations.
Deep Threat Visibility for Rapid Response
Harness billions of threat indicators & AI-powered pattern matching to outpace evasive malware.
Threat Reputation Service
- Access to 50+ billion hashes, IPs, URLs, and domains
- Supports bulk and individual searches via a REST API
- Scans IP addresses, URLs, and domains using up to 30 providers
- Correlates hashes to millions of known applications and CVEs
- Continuously updated with new IOCs and threat intelligence

Threat Hunting Pattern Correlation
- Aggregates verdicts, reports, and IOCs for proactive investigation.
- Threat hunting identifies similarities between new and known malware
- Enables correlation across samples to identify related campaigns or threat families.
- Integrates with SIEM, SOAR, and Central Management for unified visibility and faster response.

Empower Threat Hunting
with Data-Driven Threat Intelligence
Support Compliance
with Regulatory Requirements
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are
implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure.
Get Started in 3 Simple Steps
Recommended Resources
MetaDefender Threat Intelligence

SANS Detection & Response Survey

2025 OPSWAT Threat Landscape Report
FAQs
A behavior-enriched TI service that fuses massive reputation datasets with live sandbox telemetry so your blocklists and detections are driven by what malware actually does, not just static indicators.
Normalized IOCs (hashes, IPs, domains, URLs, certificates, registry keys), threat scores, family/cluster links via ML similarity, and MITRE-mapped behaviors-delivered via API or export.
OSINT often lags and misses evasive/new samples. MetaDefender Adaptive Threat Intelligence continuously adds data from OPSWAT’s adaptive sandbox technology that detonates unknown threats, then pushes fresh indicators back into your API.
Direct REST API, on-prem cache for low-egress sites, and turnkey integrations (SIEM/SOAR).
Cleaner alerts, faster hunts (campaign clustering) and fewer whack-a-mole rules thanks to behavior-anchored intelligence.



































