Stop Tomorrow's Attacks
Detect zero-day threats and evasive malware using dynamic analysis with built-in threat intelligence.
- 99.9% Zero-Day Efficacy
- 20X Faster Analysis
- Analyze All Files at the Perimeter
OPSWAT is Trusted by
Why Traditional Tools Don’t Cut It
Zero-day attacks & evasive malware now easily get past traditional, static or slow security tools.


Threat Evasion
Modern malware is engineered to outsmart static defenses, using environment checks, timing delays, and sandbox detection to hide malicious behavior.
These threats adapt in real time, exploiting blind spots in traditional tools to slip through before signatures or heuristics can react.


Slow Incident Response
Overwhelmed teams face too many alerts and too little context.
Without fast triage and clear prioritization, analysts lose critical time investigating false positives while real threats move laterally and exfiltrate data undetected.


Limited Visibility
Fragmented systems create blind spots between network, endpoint, and application layers.
When detection isn’t unified, threats can linger unseen, undermining both prevention and response efforts across the environment.

Poor Scalability
Traditional tools weren’t built for today’s data volumes or the speed of modern attacks.
As file and traffic loads grow, detection pipelines stall, analysis queues expand, and security gaps widen, leaving organizations exposed.
127%
increase in multi-stage
malware complexity*
7.3%
of OSINT files reclassified
as malicious within 24 hours*
703%
surge in credential phishing
attacks in late 2024*
*According to test data of over one million file scans.
Unified Zero-Day Detection

Layer 1: Threat Reputation
Expose Known
Threats Fast
Stop the flood of known threats.
Checks URLs, IPs, & domains in real time or offline to detect malware, phishing, & botnets.
Blocks reused infrastructure & commodity malware and forces attackers to rotate basic indicators.
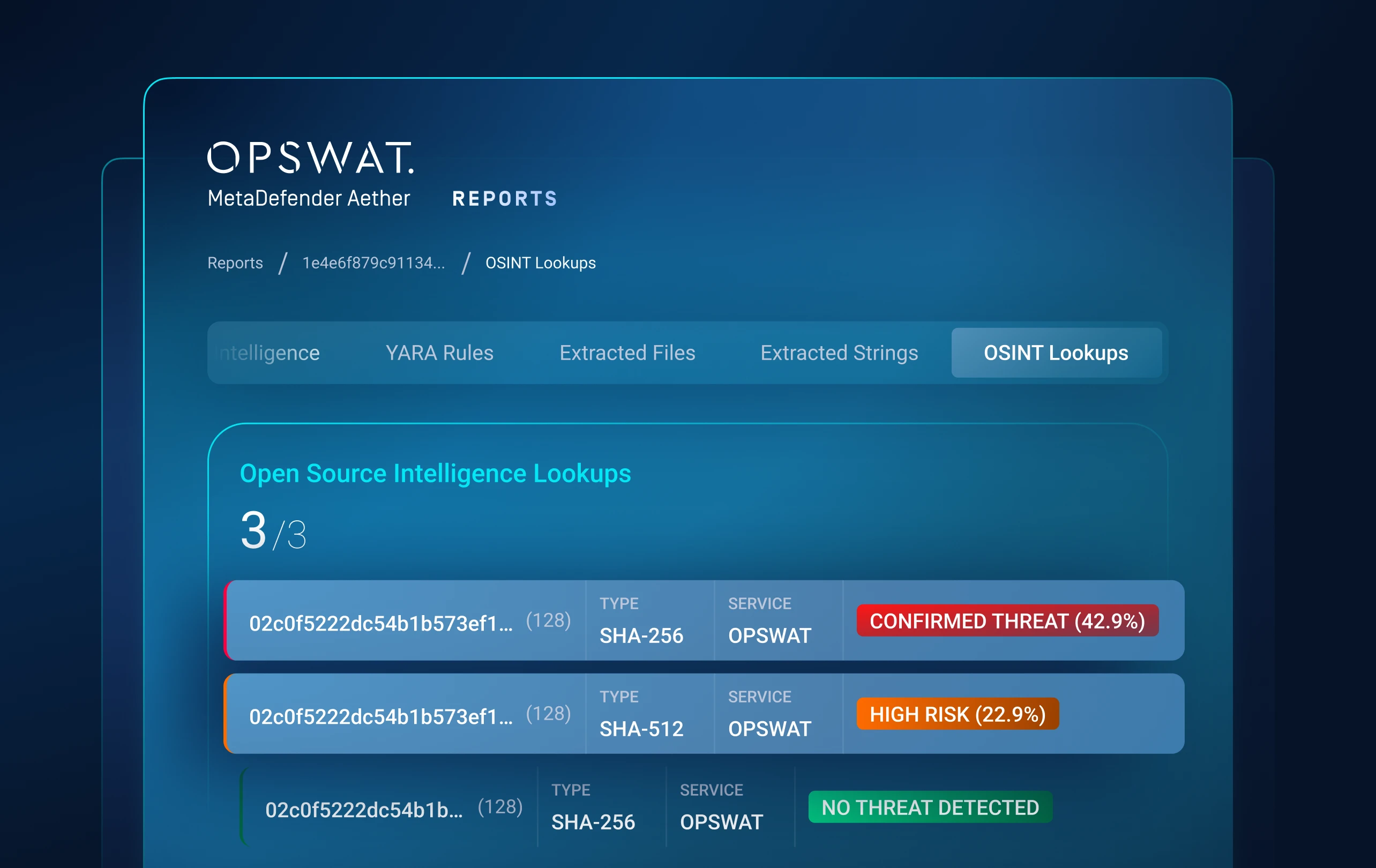
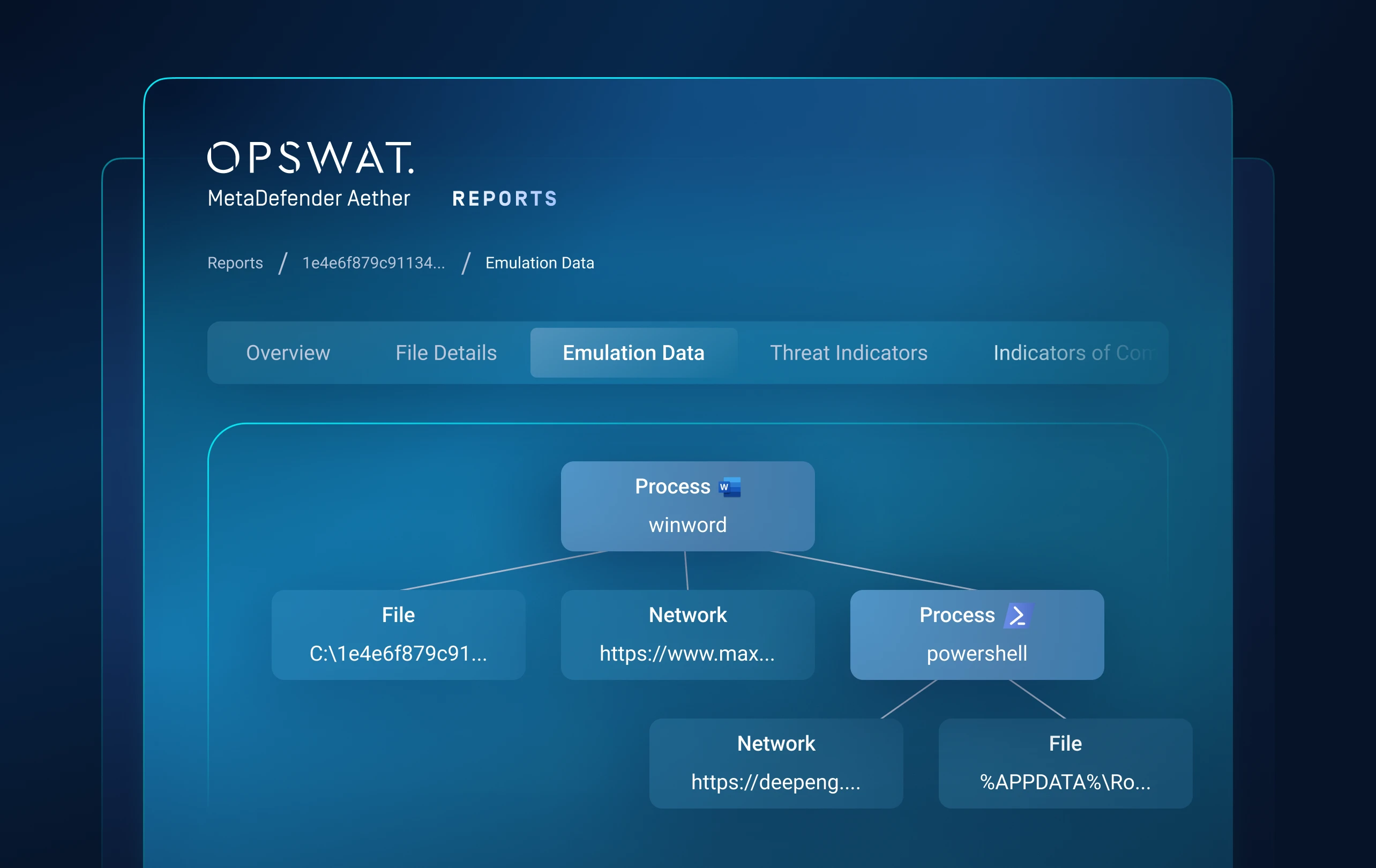
Layer 2: Dynamic Analysis
Uncover Unknown
Threats
Detects evasive malware that hides from traditional sandboxes.
An emulation-based sandbox analyzes files to detect hidden threats like ransomware.
Exposes artifacts, loader chains, script logic and evasion tactics.
Layer 3: Threat Scoring
Prioritize Threats
Reduce alert fatigue.
Threat risk levels are ranked to quickly highlight priority threats in real-time.
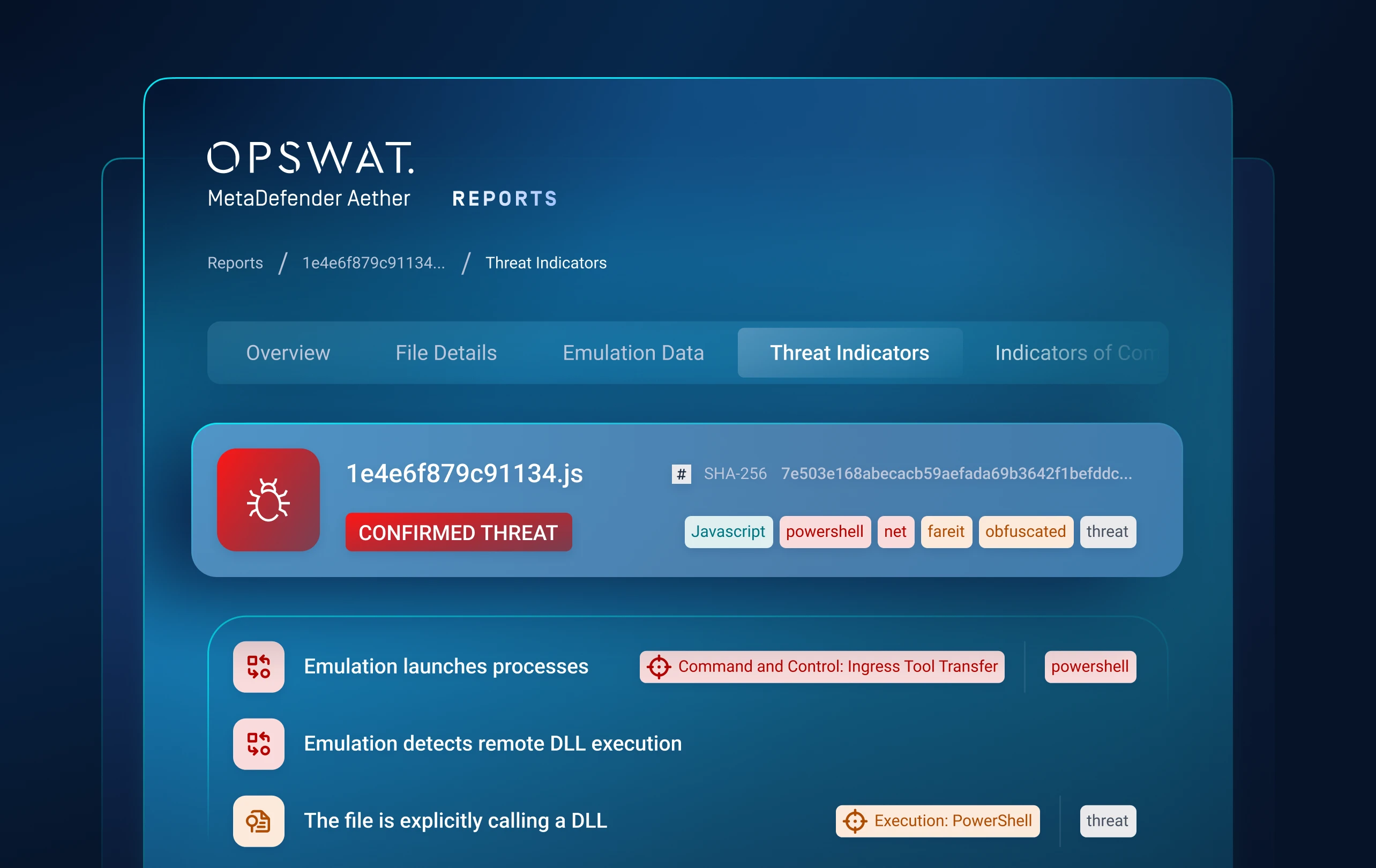
Layer 4: Threat Hunting
Identify Malware
Campaigns
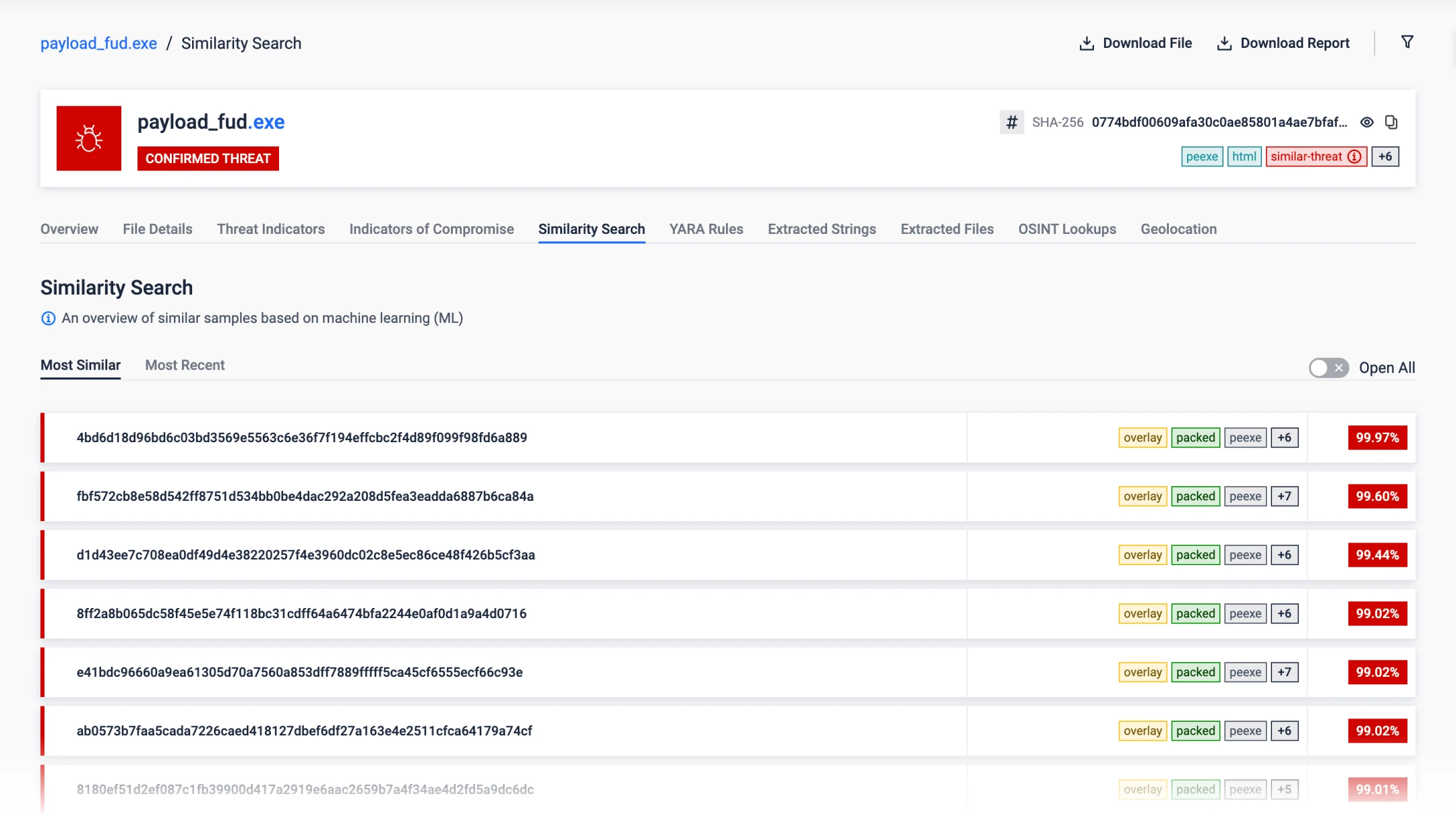
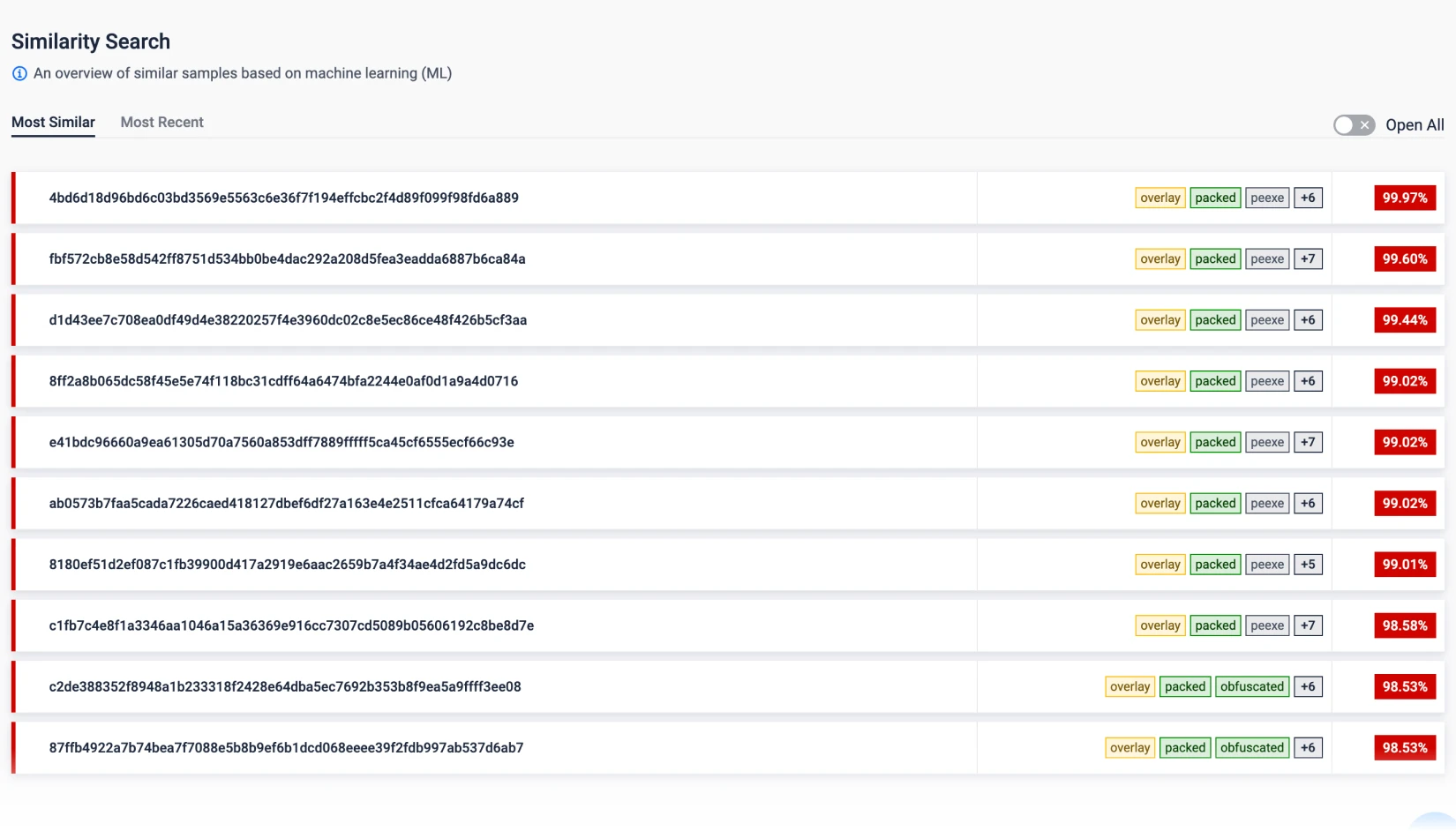
Machine-Learning Similarity Search
Threat Pattern Correlation matches unknown threats to known malware, tactics, infrastructure and more.
Uncovers malware families and campaigns, forcing attackers to overhaul tactics and infrastructure.
“Fastest Speed We’ve
Ever Tested.”
Venak Security
330+
Detectable Brands
for ML-Based
Phishing Detection
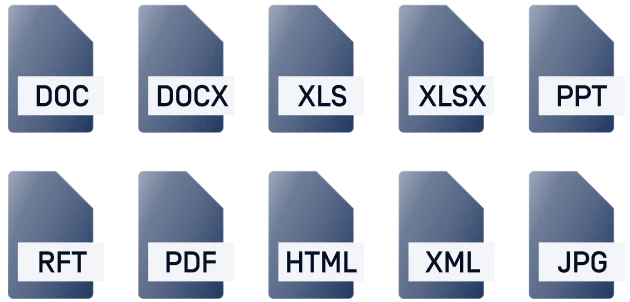
50+
File Types
Extract artifacts,
images, & more
>14
Automated Malware
Family Extraction
Integrate Easily
We stop the attacks that
no one knows exist.
20x
Faster than Traditional Solutions
Deep Visibility & Rapid Response
Harness billions of threat signals & machine-learning threat similarity search.
Deep Structure Analysis
Quickly analyze 50+ file types, including LNK and MSI, to extract embedded content, artifacts, and images.
Automated decoding, decompilation, and shellcode emulation—along with Python unpacking, macro extraction, and AutoIT support—deliver deep visibility into hidden threats.
Dynamic Analysis
Detect and classify active threats using machine learning and targeted detonations in specific application stacks or environments.
Bypass anti-evasion checks, emulate JavaScript, VBS, and PowerShell scripts, and dynamically adapt control flows to uncover unknown threats.
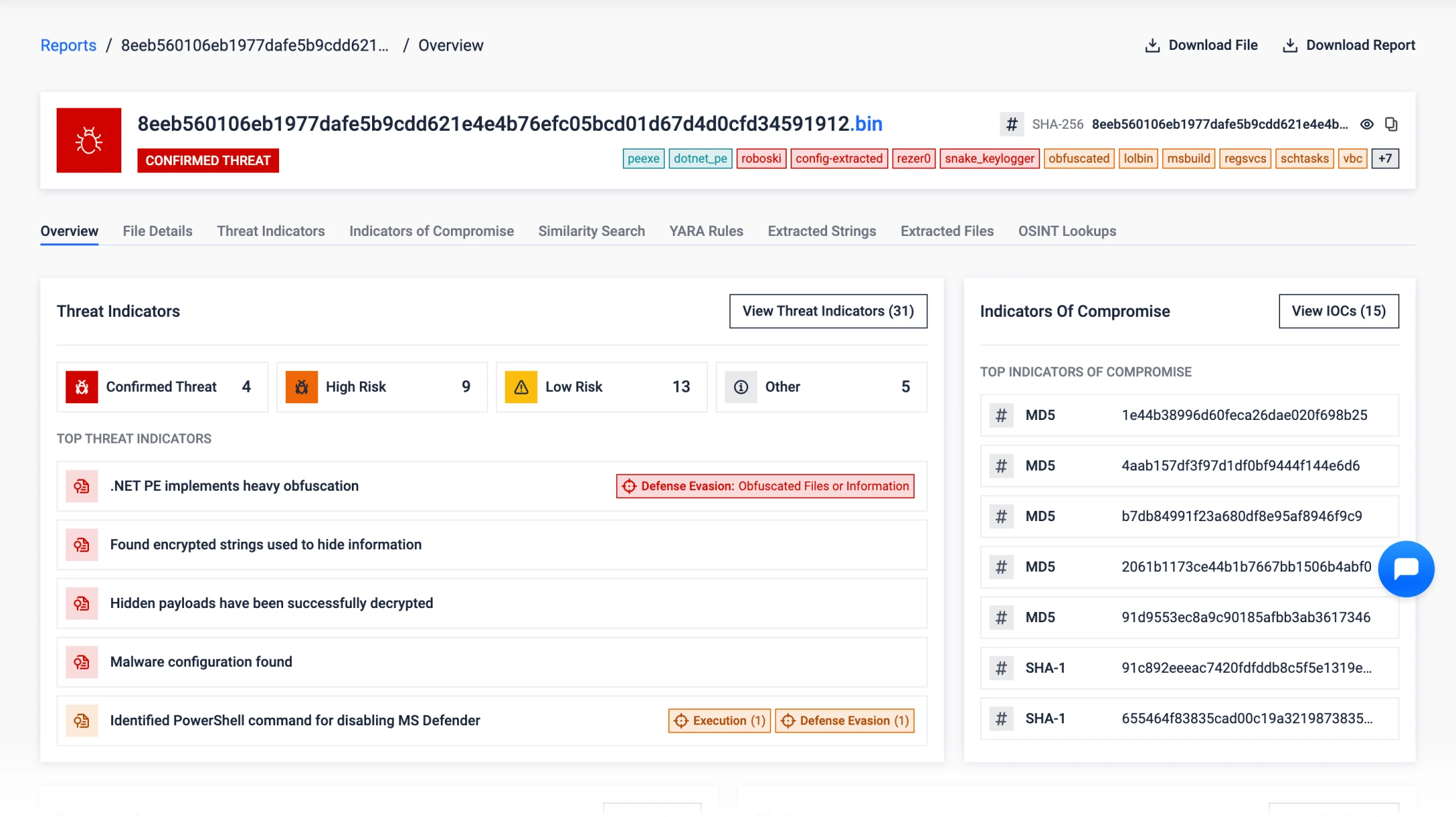
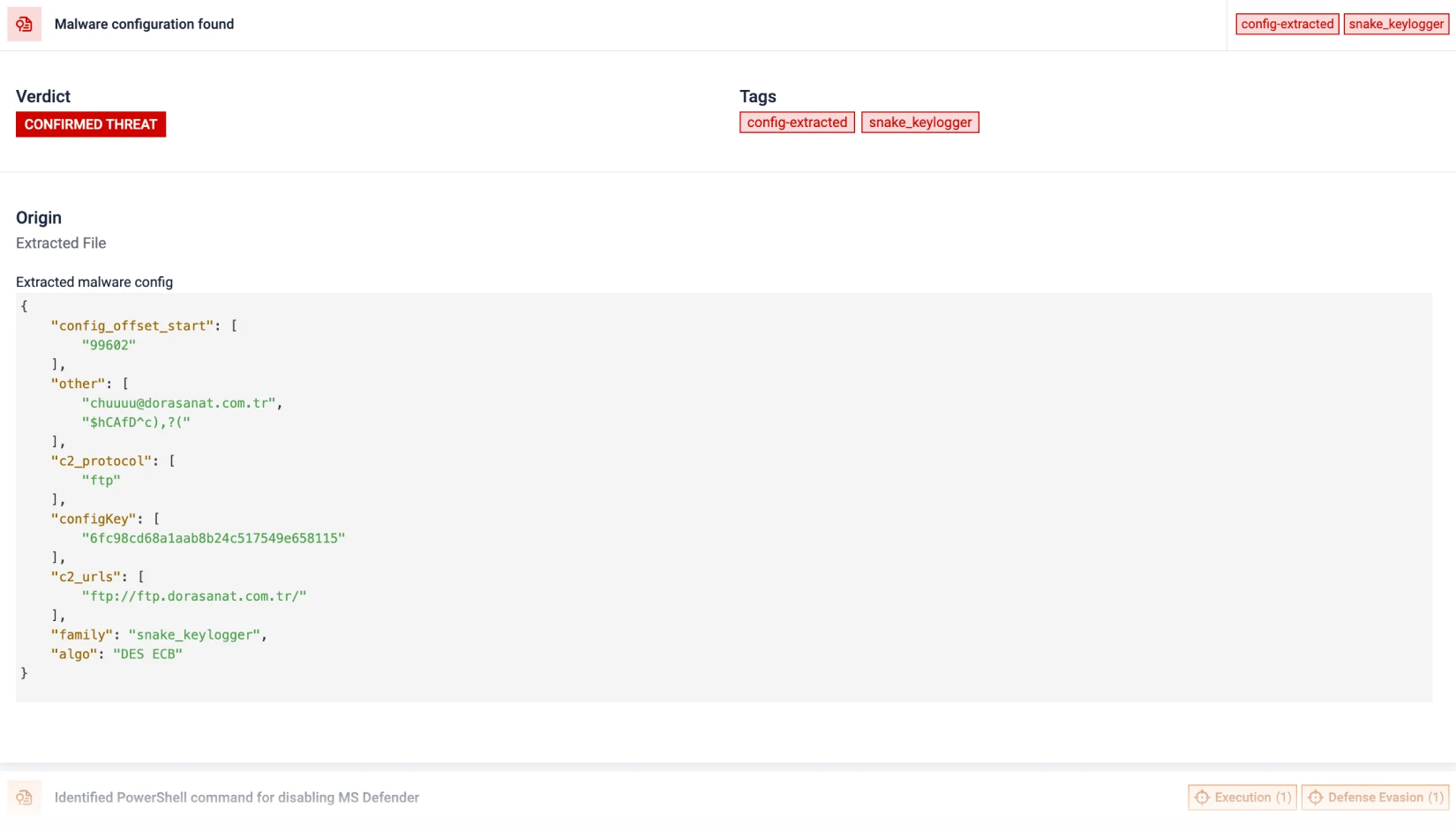
Threat Detection & Classification
Detect 330+ phishing brands—even offline—using Machine Learning (ML) analysis.
Correlate IOCs, identify malicious intent with 900+ behavioral indicators, extract configurations from 18+ malware families, and detect unknown threats through similarity-based clustering.
- MetaDefender Aether
- MetaDefender Aether
- MetaDefender Aether
Threat Intelligence & Integration
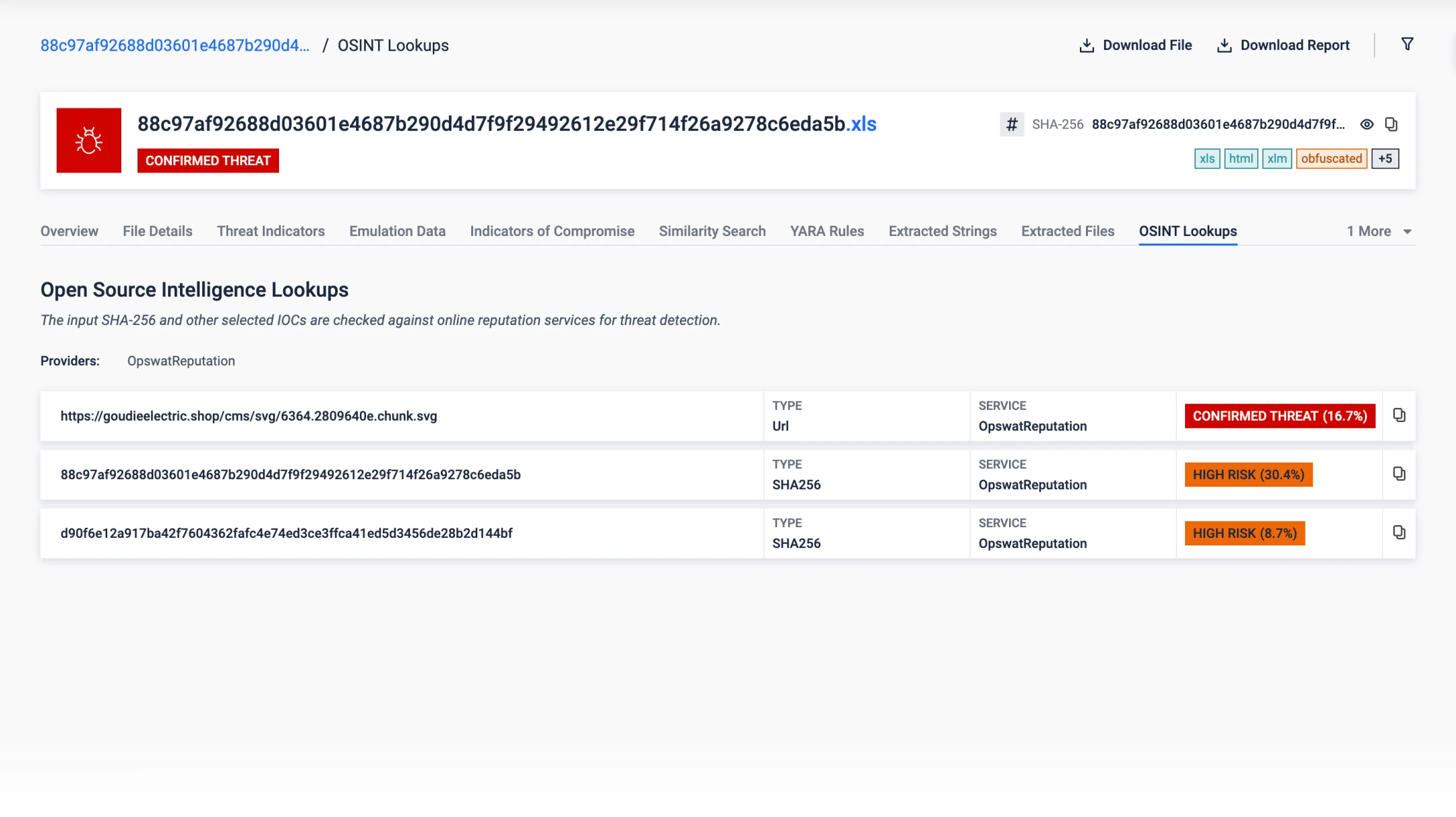
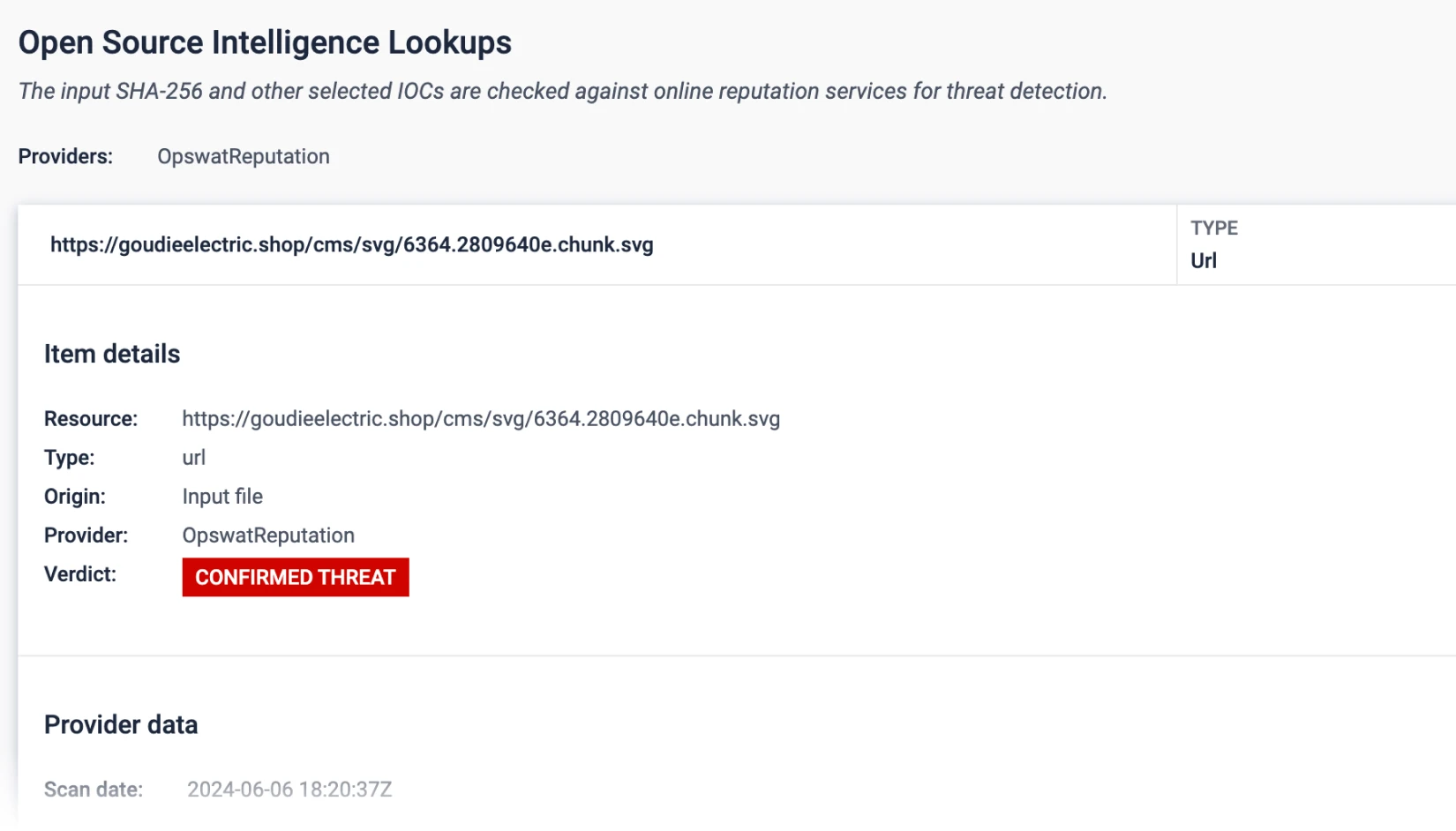
Automated threat hunting and real-time detection integrate seamlessly across intelligence sources.
The system exports to MISP and STIX formats, queries the MetaDefender Cloud Reputation Service, connects with open-source intelligence vendors, and automatically generates YARA rules for each detected threat.
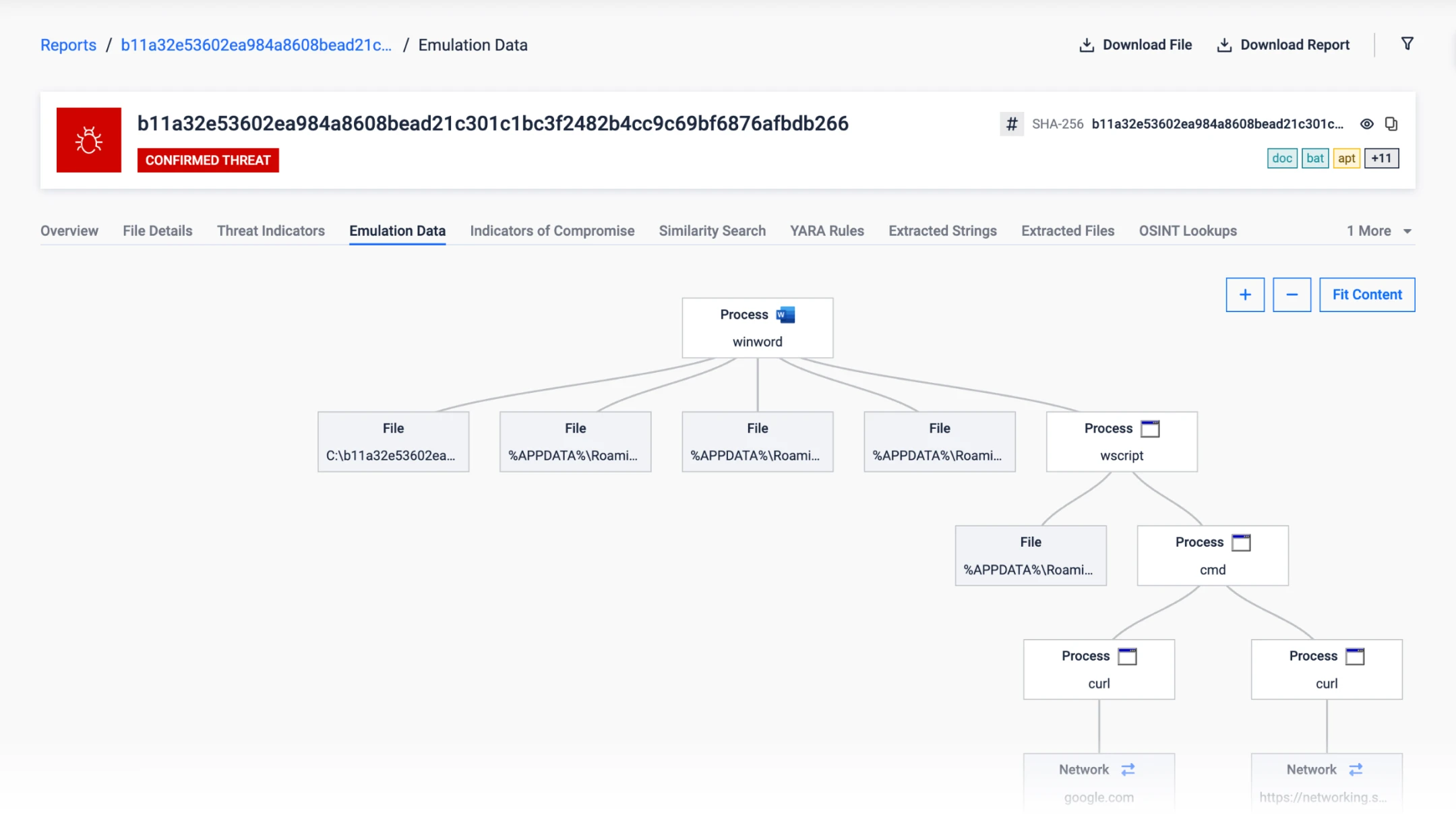
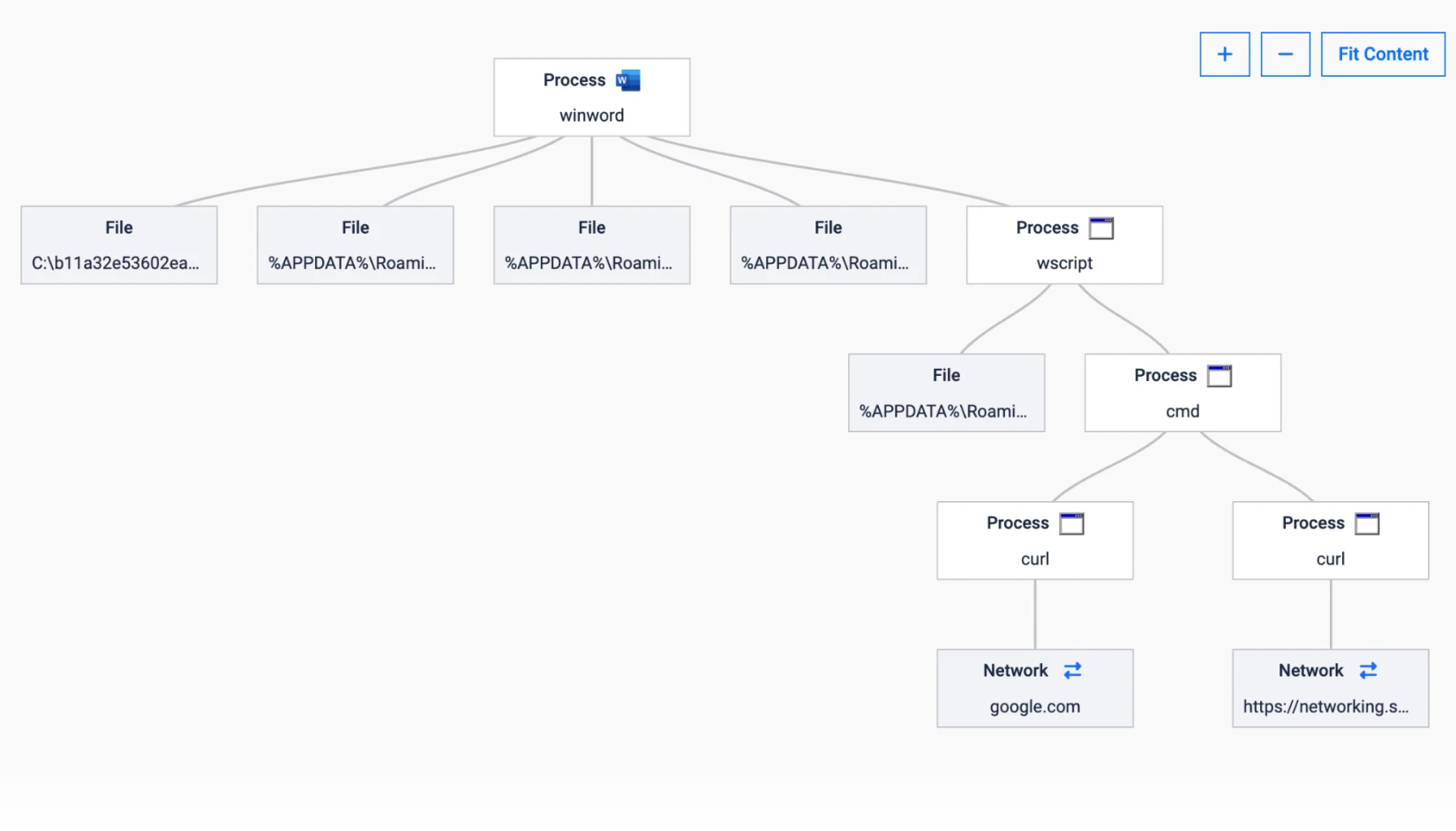
Next-Gen Anti-Evasion Engine
Extracts indicators of compromise from highly evasive malware and detonates targeted attacks so analysts can focus on high-value findings.
The sandbox defeats advanced evasion techniques including long sleeps and loops, user or domain checks, geofencing, OS locale checks, VBA stomping, advanced auto-execution behaviors such as mouse-hover triggers, and task scheduler abuse.
- MetaDefender Aether
- MetaDefender Aether
Powering Zero-Day Detection
Across Every Environment
OPSWAT’s Zero-Day Detection solution is built on a unified suite of technologies that combine sandboxing, adaptive intelligence, &
behavioral analysis to expose unknown threats at speed & scale—on-premises, in the cloud, or anywhere in between.

MetaDefender Threat Intelligence™
Identify zero-day related threats, assess file reputation in real time, and respond faster to emerging risks with machine-learning threat similarity search and threat reputation checks. Security teams gain enriched threat intelligence to ensure stronger defenses against evolving malware and targeted attacks.
Unlock Zero-Day Detection Across Solutions
Discover how zero-day detection can be brought to your network perimeter,
ensuring all files gain advanced zero-day detection without performance delays.
Detonator - The Endless Quest
for Zero-Day Detection
The Story Behind OPSWAT’s Industry-Leading Dynamic Analysis Technology
The Story Behind MetaDefender Aether
Jan Miller – CTO, Threat Analysis at OPSWAT
Jan Miller is a pioneer in modern malware analysis, known for launching platforms that transformed how the industry detects evasive threats. After founding Payload Security and later driving Falcon X at CrowdStrike, he continued innovating with Filescan.io, later acquired by OPSWAT. As an AMTSO Board member, he champions transparency while advancing techniques that blend dynamic analysis with threat intelligence to expose evasive malware.
Dynamic Analysis Evolves with Built-in Threat Intel
MetaDefender Aether fuses CPU-level emulation, behavioral analytics, and adaptive threat intelligence (threat reputation, scoring, similarity search). This means faster zero-day verdicts and richer context that powers threat hunting and automated response across your security stack.
Validated Speed
& Security by AMTSO
Aligned with Anti-Malware Testing Standards Organization (AMTSO), Venak Security test confirms OPSWAT’s Adaptive Sandbox leadership.
Trusted Globally to Defend What's Critical
OPSWAT is trusted by 2,000+ organizations worldwide to protect their critical data, assets, and networks from
device and file-borne threats.
Purpose-Built for Every Sector
Support Compliance
with Regulatory Requirements
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are
implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure.
Recommended Resources

MetaDefender Aether for Core

SANS 2025 Detection & Response Survey

2025 OPSWAT Threat Landscape Report
FileScan.io Community
Uncover hidden threats with insightful malware analysis
powered by OPSWAT’s MetaDefender Aether
technology—try it free.
FAQs
It closes the blind spot on unknown, file-based threats by combining reputation checks, emulation-based dynamic analysis, and behavioral intelligence-so you see in-memory payloads, obfuscated loaders, and phishing kits that signatures and endpoint tools miss.
It plugs in at ingest (ICAP, email, MFT, web), enriches your SIEM/SOAR (MISP/STIX, Splunk SOAR, Cortex XSOAR), and feeds back high-fidelity IOCs and MITRE-mapped behaviors to improve detections across all your tools.
No. Reputation "great-filter" removes most noise instantly; suspicious files are detonated in an emulation sandbox that's 10× faster and 100× more resource-efficient than legacy VM sandboxes-keeping file flow fast while still catching the 0.1% zero-day threats that matter.
Yes. Deploy cloud, hybrid, or fully on-prem/air-gapped (RHEL/Rocky Linux supported), with offline mode and certificate whitelisting, role-based access, audit logs, and data-retention controls for NIS2/IEC 62443/NIST-style environments.
Reduced incident volume/MTTR (fewer false positives, richer context), earlier detection of OSINT-silent threats, and measurable risk reduction for file workflows (email, MFT, portals). Most customers start with a scoped POC on their real traffic, then expand.