Enterprise Data Storage Solution
with Multi-Layered Security
Protect your on-premises, hybrid, and cloud storage with a comprehensive data storage solution designed to prevent breaches, minimize downtime, and ensure compliance.
2M+
Files Processed Per Hour for
Enterprise-Scale Workloads
99.2%
Threat Detection with
30+ AV Engines
100%
Protection Score Validated by SE Labs
Deep CDR Testing
Enterprise Data Storage Security for
Every Use Case
Product Overview
Learn how MetaDefender Storage Security protects data at rest across on-premises, hybrid, and cloud storage
by applying multiscanning, Deep CDR, and automated scanning policies throughout the data lifecycle.
Why Choose MetaDefender for Enterprise Storage Security?
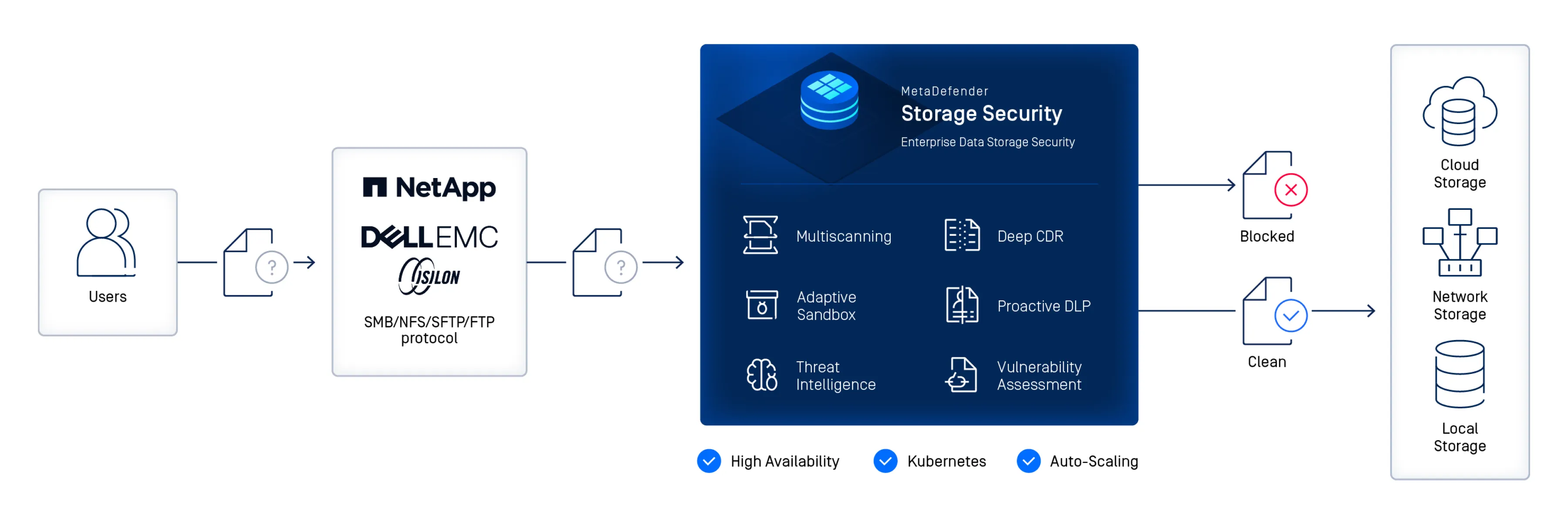
Protect files at rest with a data storage solution that delivers robust malware and data security for both on-premises and cloud storage, keeping your critical workflow secure.
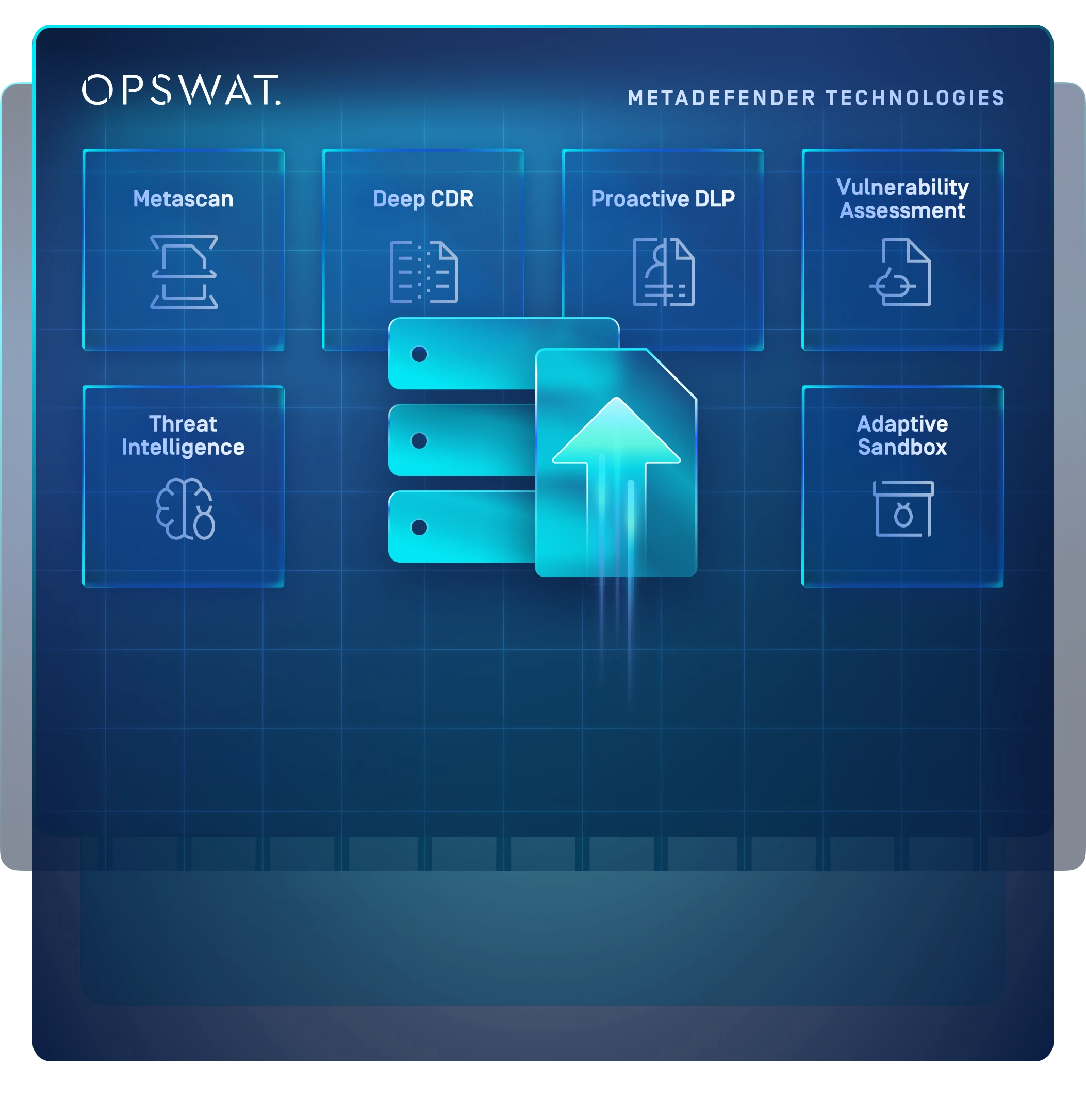
All-in-One Threat Detection and Prevention Platform
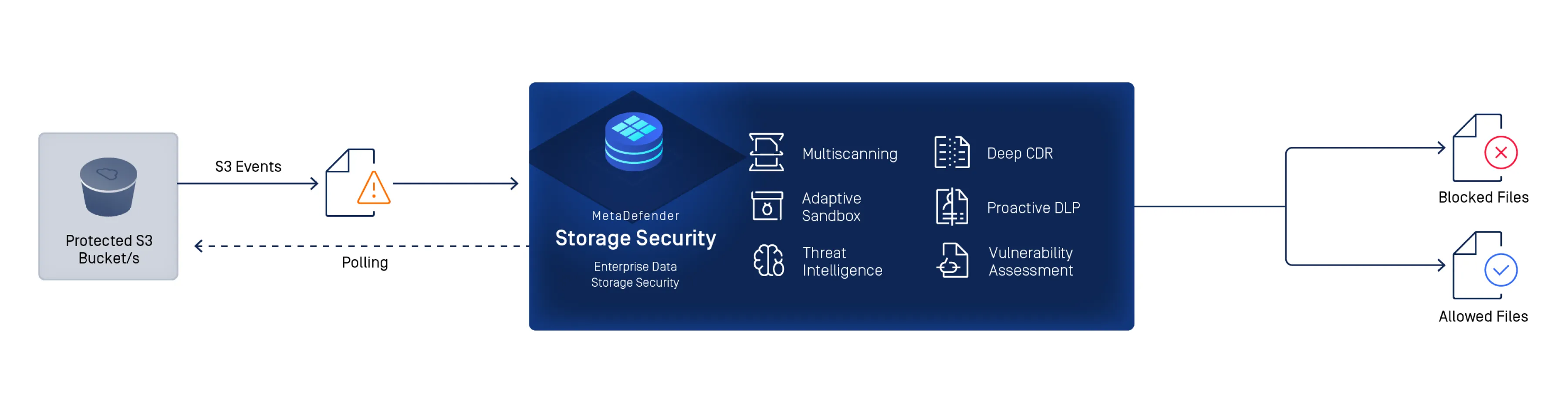
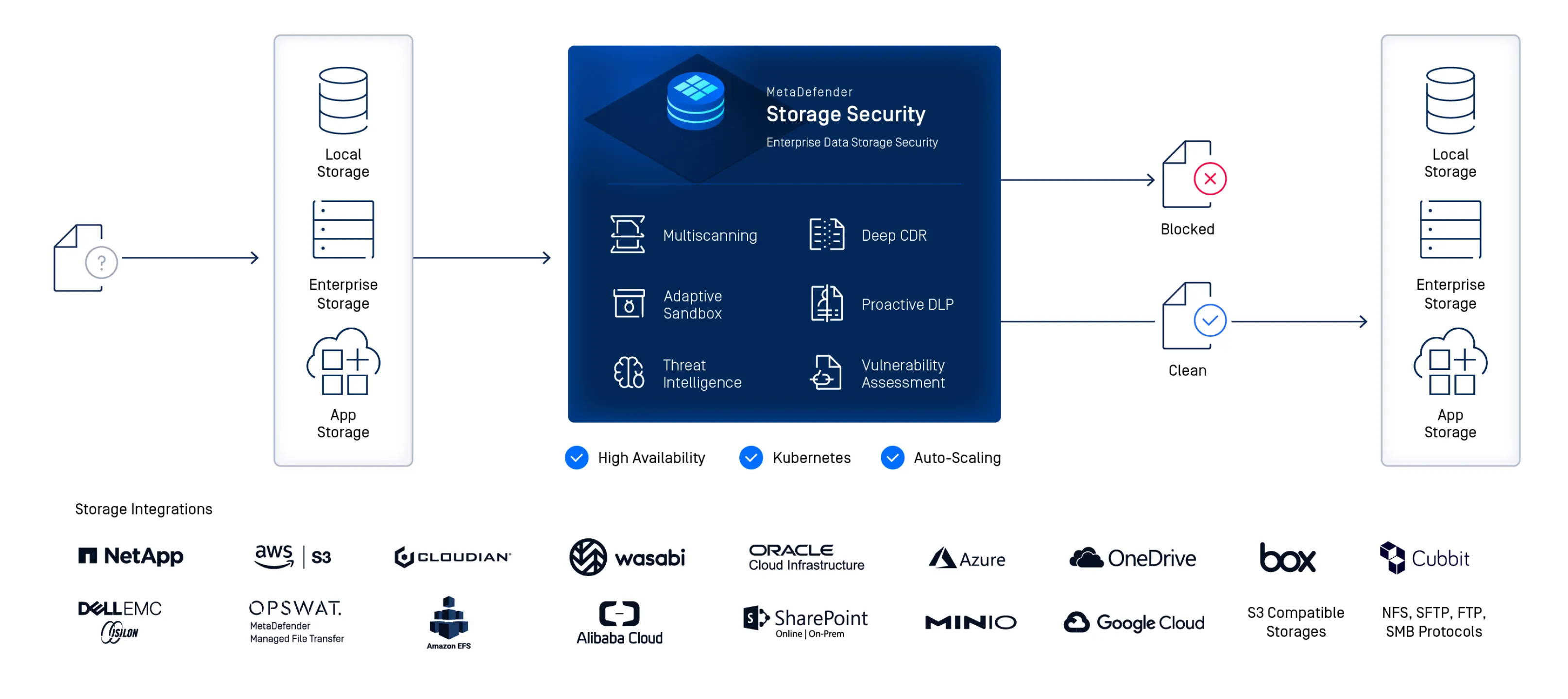
Gain real-time and on-demand threat detection and prevention with multi-layered enterprise data storage. MetaDefender Storage Security combines Metascan™ Multiscanning, Deep CDR™, Proactive DLP™, Vulnerability Assessment, and Adaptive Sandbox for seamless protection across on-premises, hybrid and cloud environments—all in a single, easy-to-deploy platform.
Enable Secure Collaboration Across Storage Environments
Enable seamless and secure collaboration across on-premises, hybrid, and cloud-native storage. MetaDefender Storage Security enables seamless and secure collaboration between users and organizations, regardless of their storage environments.
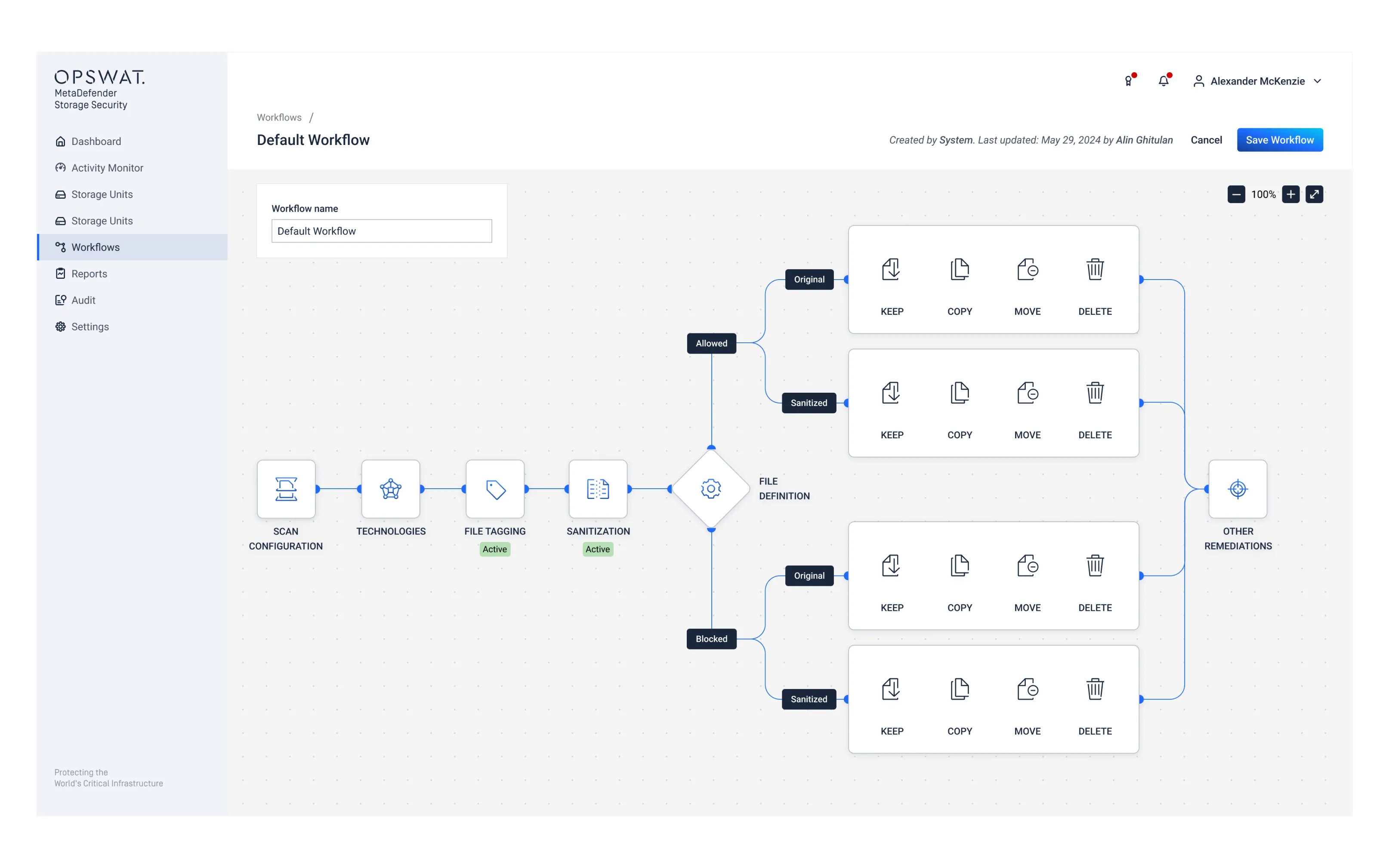
Automated Compliance and File Privacy Controls
Provide you with complete control over your security policies. Custom file processing workflows tailored to your organization's specific needs without additional API development.
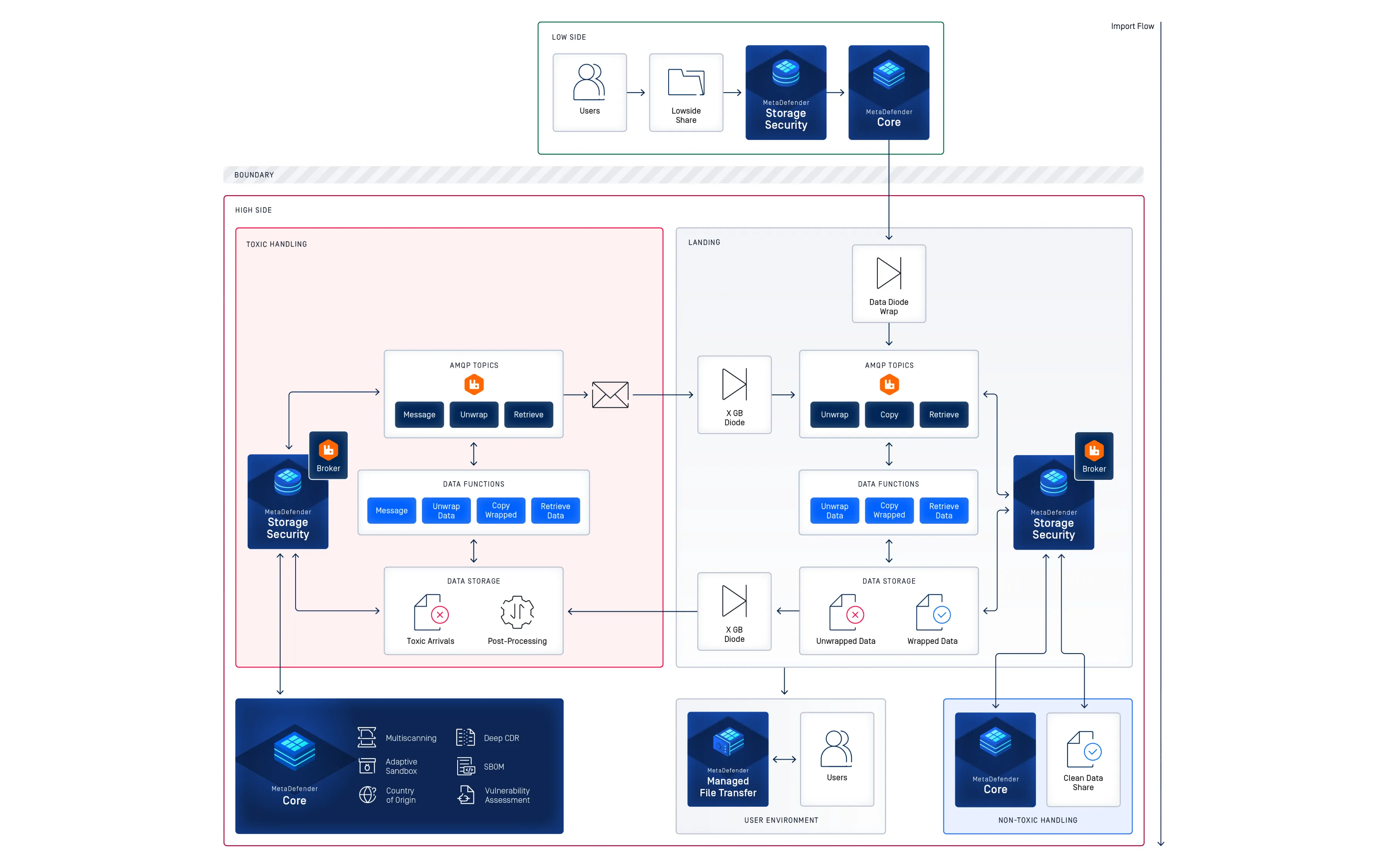
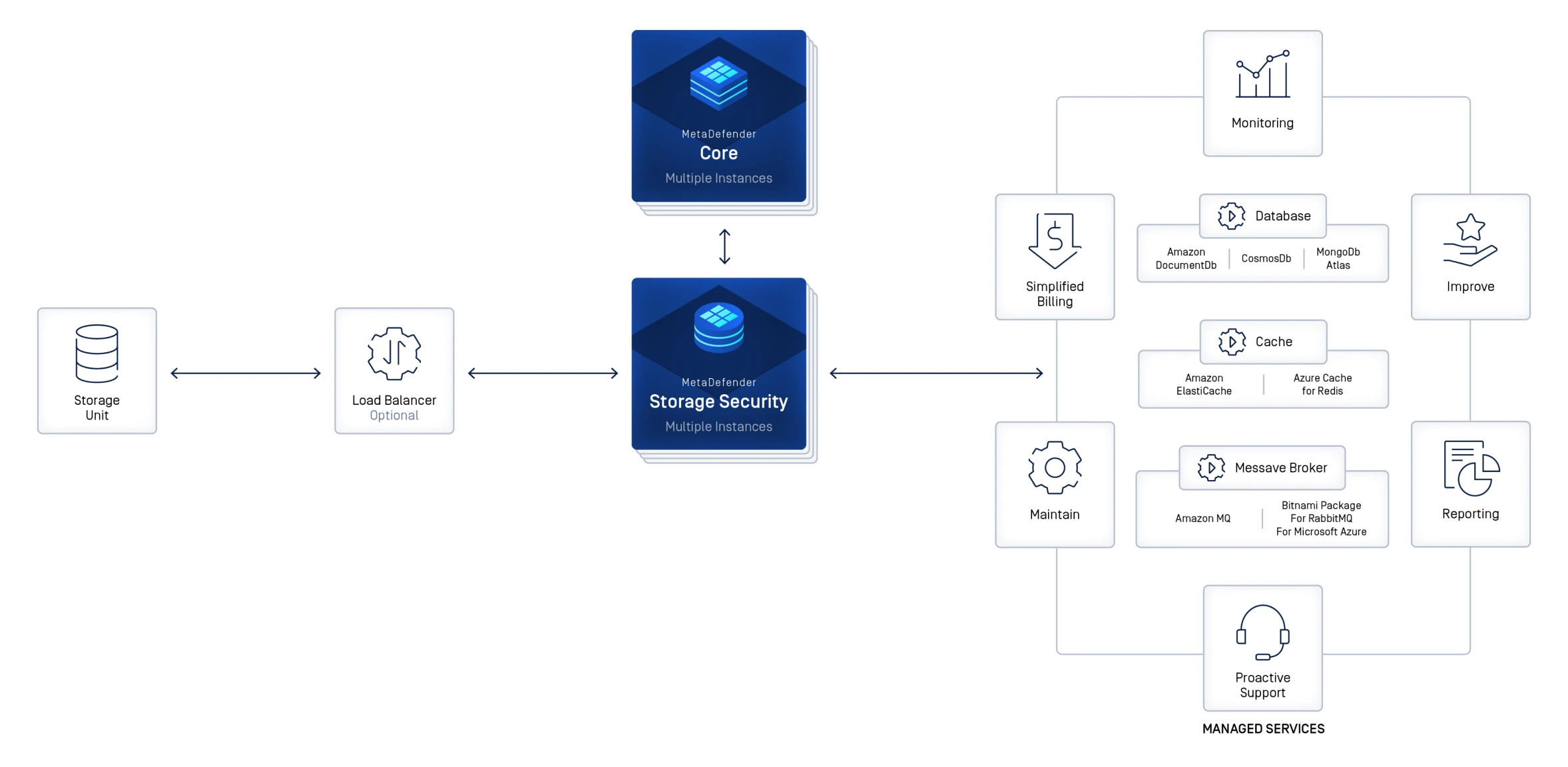
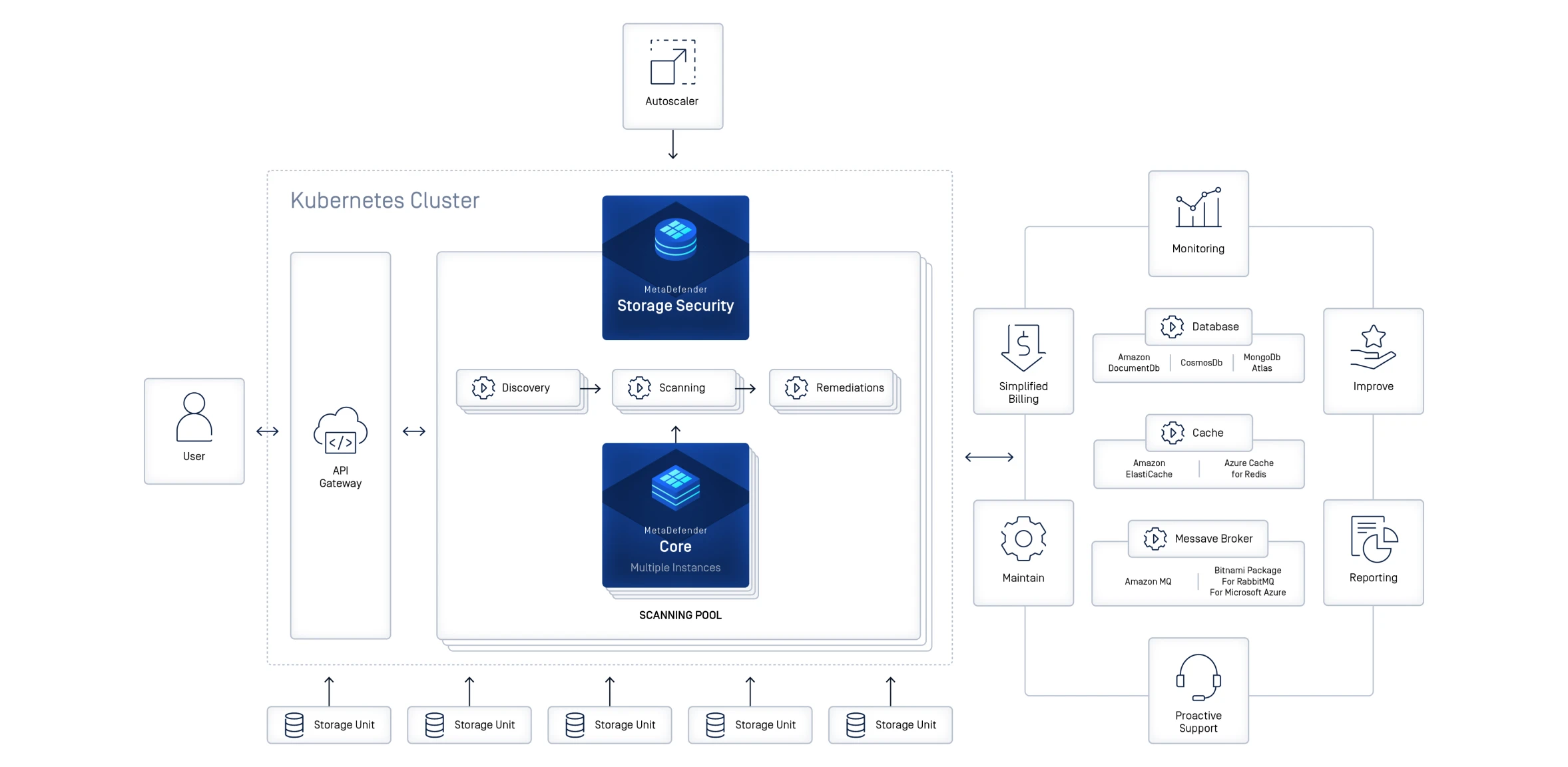
Flexible Deployment and High Availability for Enterprise Storage
Deploy MetaDefender Storage Security across local, hybrid, or cloud-native storage environments for scalable protection. Benefit from continuous security with redundant and distributed architectures that minimize downtime and maintain service reliability.
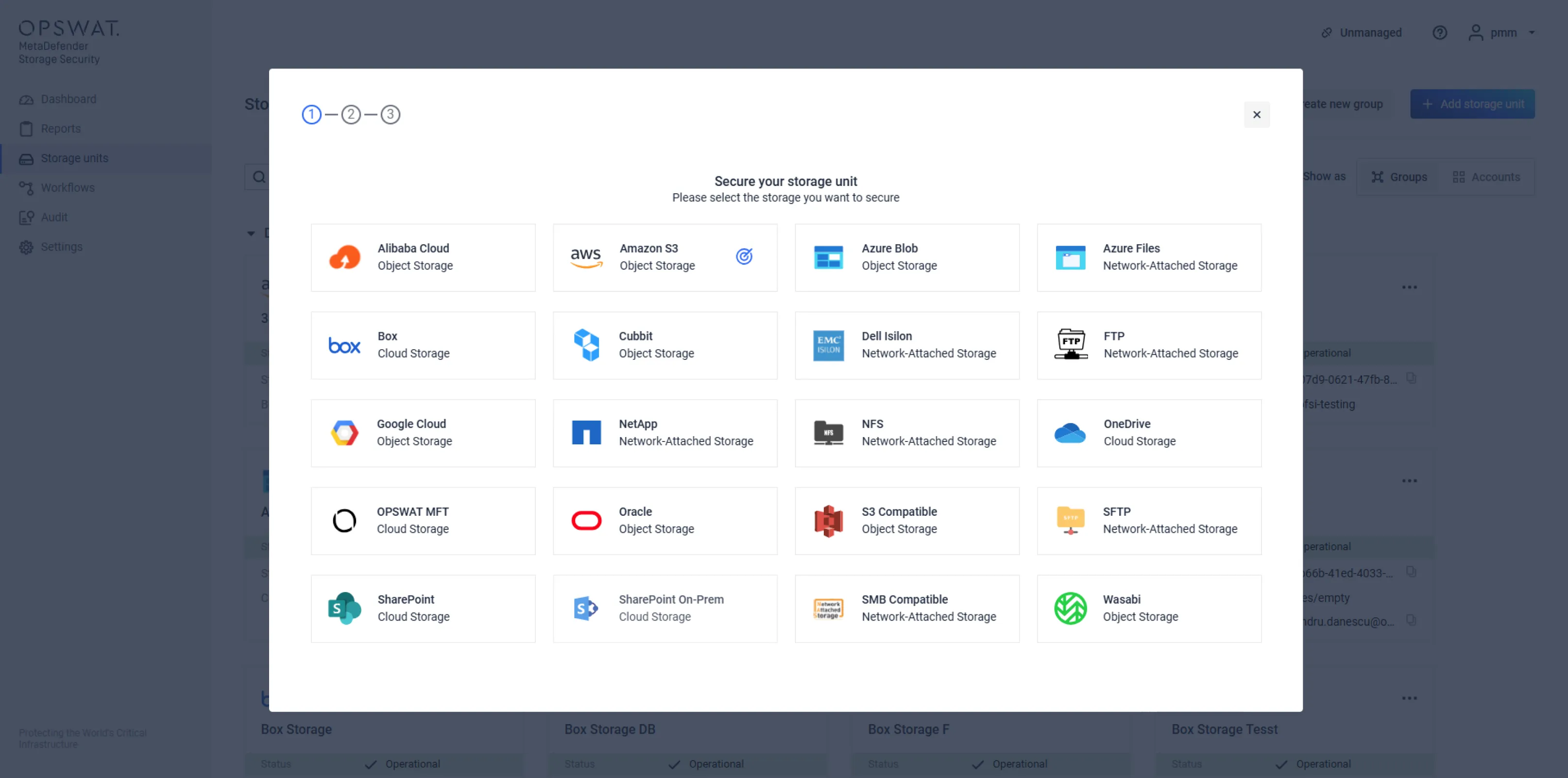
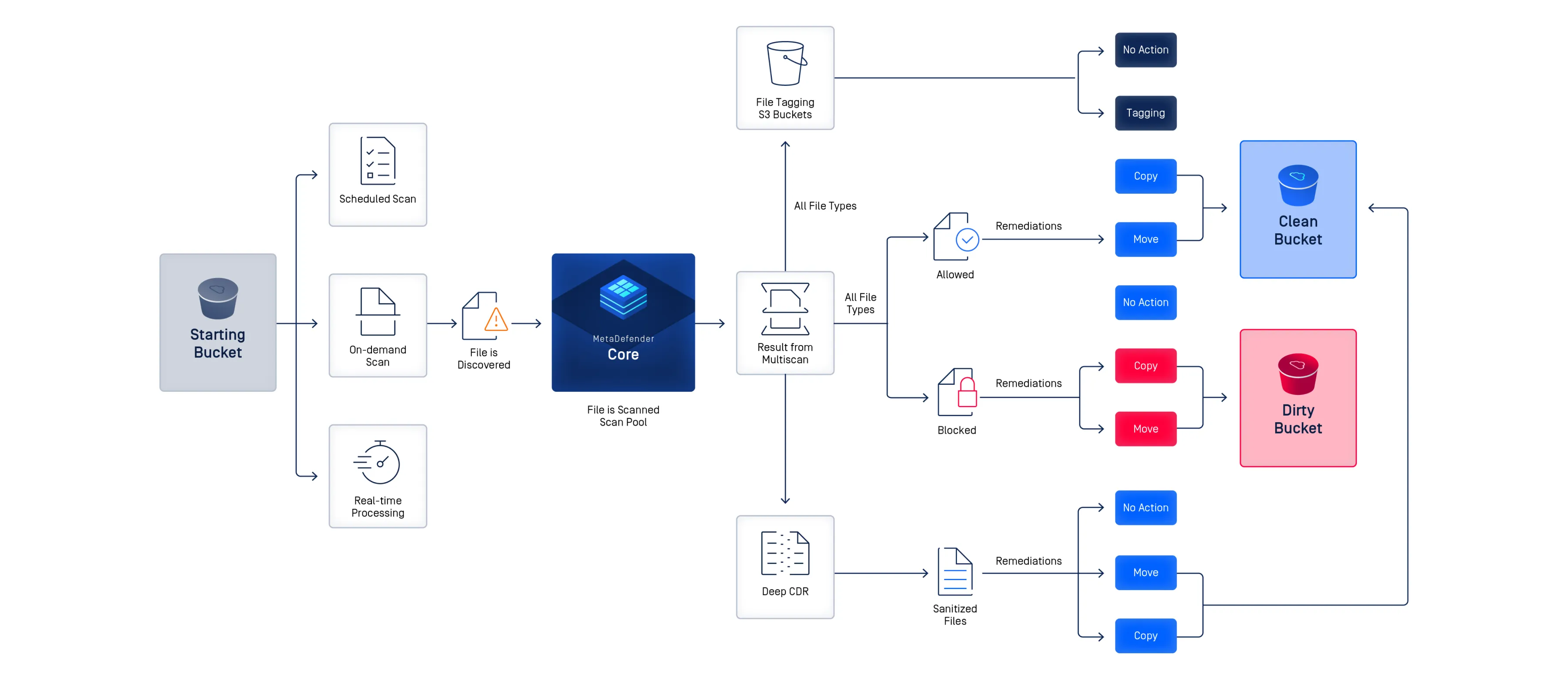
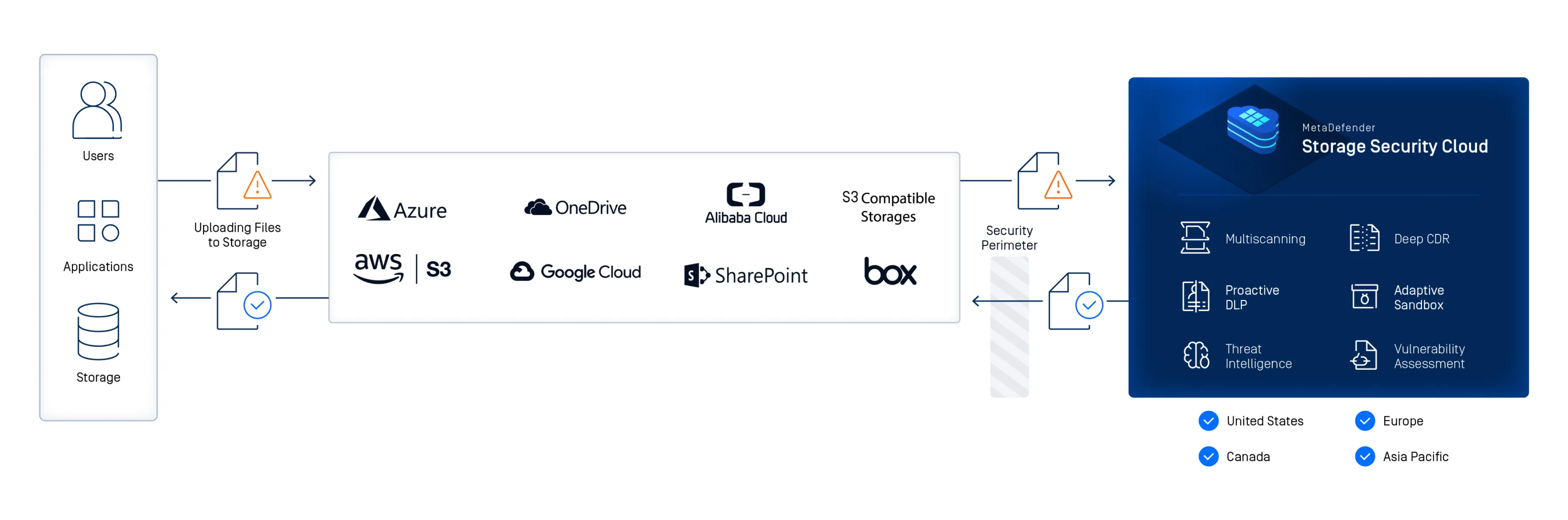
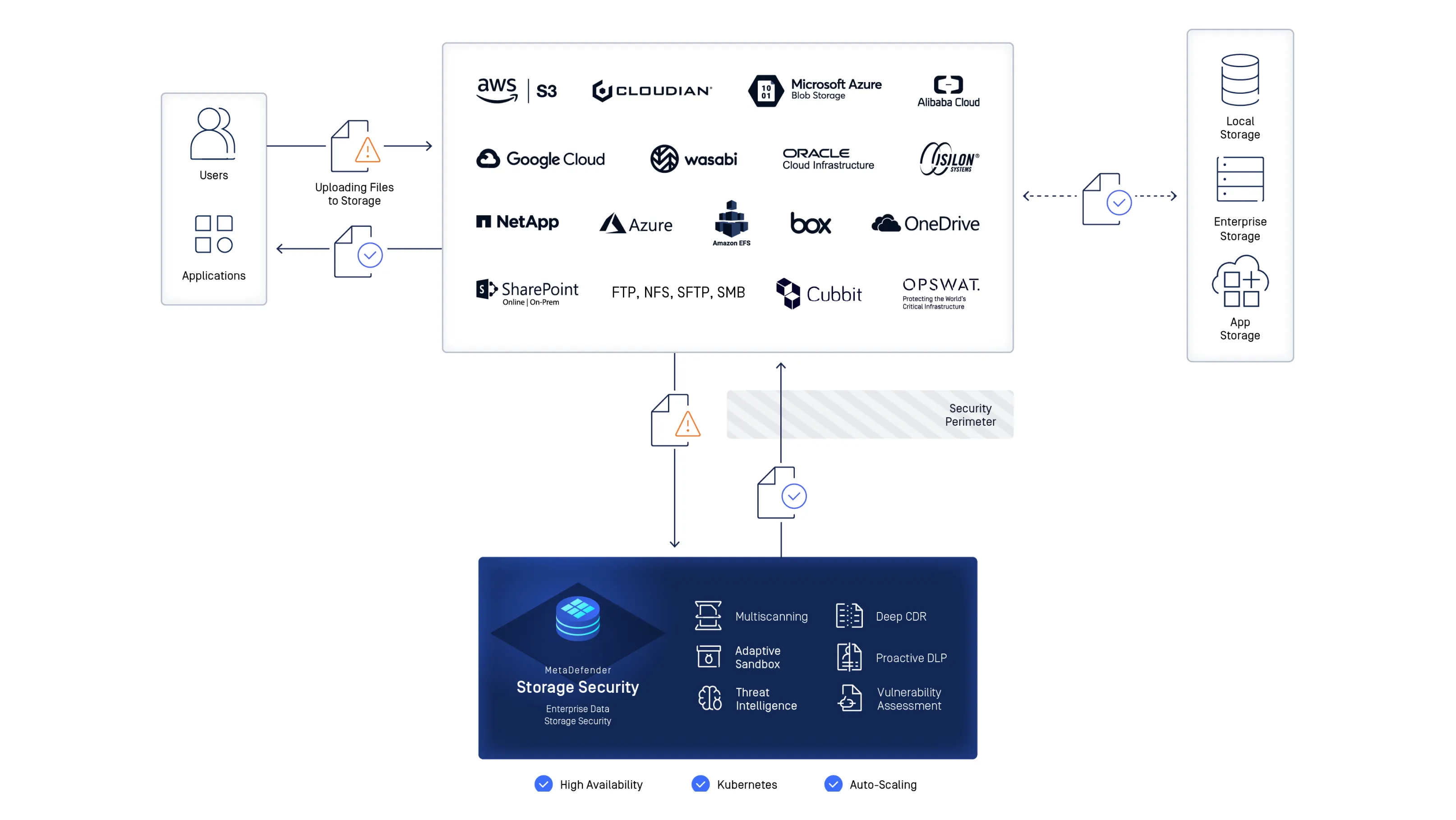
Real-Time Scanning Across Hybrid and Cloud Storage Platforms
[storage-security-integrations]
Scan files in real time or on demand across on-premises, hybrid, and cloud-native storage platforms. MetaDefender Storage Security integrates with Amazon S3, Microsoft Azure, NetApp, Wasabi, Dell EMC, SharePoint, Box, and any SMB/NFS/SFTP or S3-compatible storage for seamless workflow protection.
Storage Type | Storage Name | Integration Type |
|---|---|---|
Cloud Object Storages | AWS S3 | Native |
| Wasabi | S3 Compatible | |
| Cloudian | S3 Compatible | |
| Oracle | S3 Compatible | |
| MinIO | S3 Compatible | |
| Azure Blog Storage | Native | |
| Google Cloud | Native | |
| Alibaba Cloud | Native | |
| Cubbit | S3 Compatible | |
File Storages | Azure Files | Native |
| Sharepoint Online | Native | |
| SharePoint On-premises | Native | |
| OneDrive | Native | |
| Box | Native | |
| OPSWAT MetaDefender Managed File Transfer (MFT) | Native | |
| Network Attached Storages (NAS) | NetApp ONTAP | SMB/NFS |
| AWS EFS | NFS | |
| Dell EMC Isilon | SMB/NFS | |
| SMB | NFS/Native | |
| NFS | Native | |
| SFTP | Native | |
| FTP | Native |
Deployment Options for Any Enterprise Storage Architecture
Whether you require the rapid scalability of the cloud, the control of on-premises infrastructure, or the simplicity of SaaS, MetaDefender Storage Security ensures seamless integration and robust protection across all platforms.
Optimize On-Premises and Hybrid Deployments with Virtual Machines
Gain enhanced control and customization for on-premises and hybrid storage. MetaDefender Storage Security supports medium to large workloads, processing over 100,000 files per hour with scalable, reliable performance.
Embrace Modern Architecture with Kubernetes Deployment
Deploy at scale for distributed applications in containers across on-premises and hybrid cloud environments. Benefit from efficient workload management, cost optimization, and support for Helm on Kubernetes services such as OpenShift, EKS, AKS, and GKE.
Simplify Security with IaaS and SaaS Solutions
Simplify security with a cloud-native solution that requires no dedicated IT staff or hardware. Integrate seamlessly with cloud and on-premises systems, benefit from pay-as-you-go flexibility, and maintain built-in security for regulatory compliance.
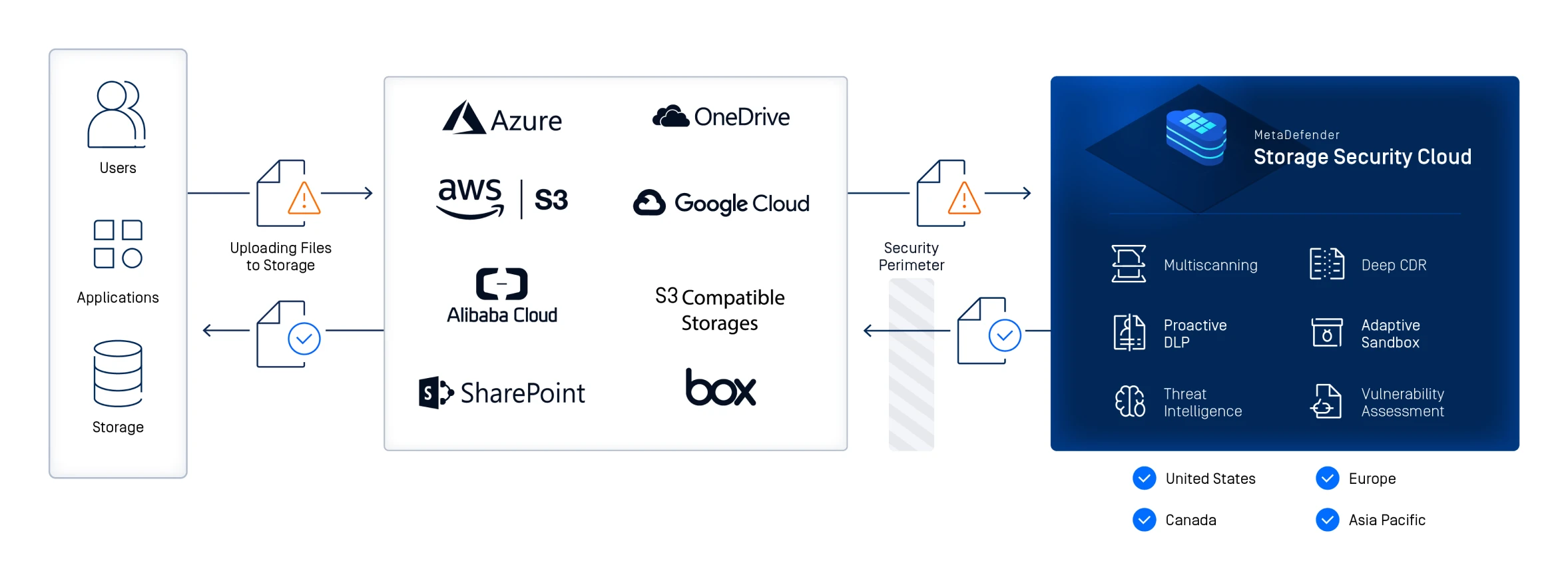
Defense in Depth with OPSWAT Technologies
MetaDefender Storage Security leverages a multi-layered security approach to ensuring all stored data is safe to use across all storage types with high-efficacy detection and prevention technologies.
Detect Malware with Metascan™ Multiscanning
Detect over 99.2% of threats with 30+ commercial anti-malware engines, machine learning, and heuristics.
- Reduce exposure time with faster detection mechanisms from various vendors.
- Avoiding reliance on a single vendor’s malware detection capabilities.
- Reduce TCO (total cost of ownership) with optimized, single-license multiscanning engine packages.
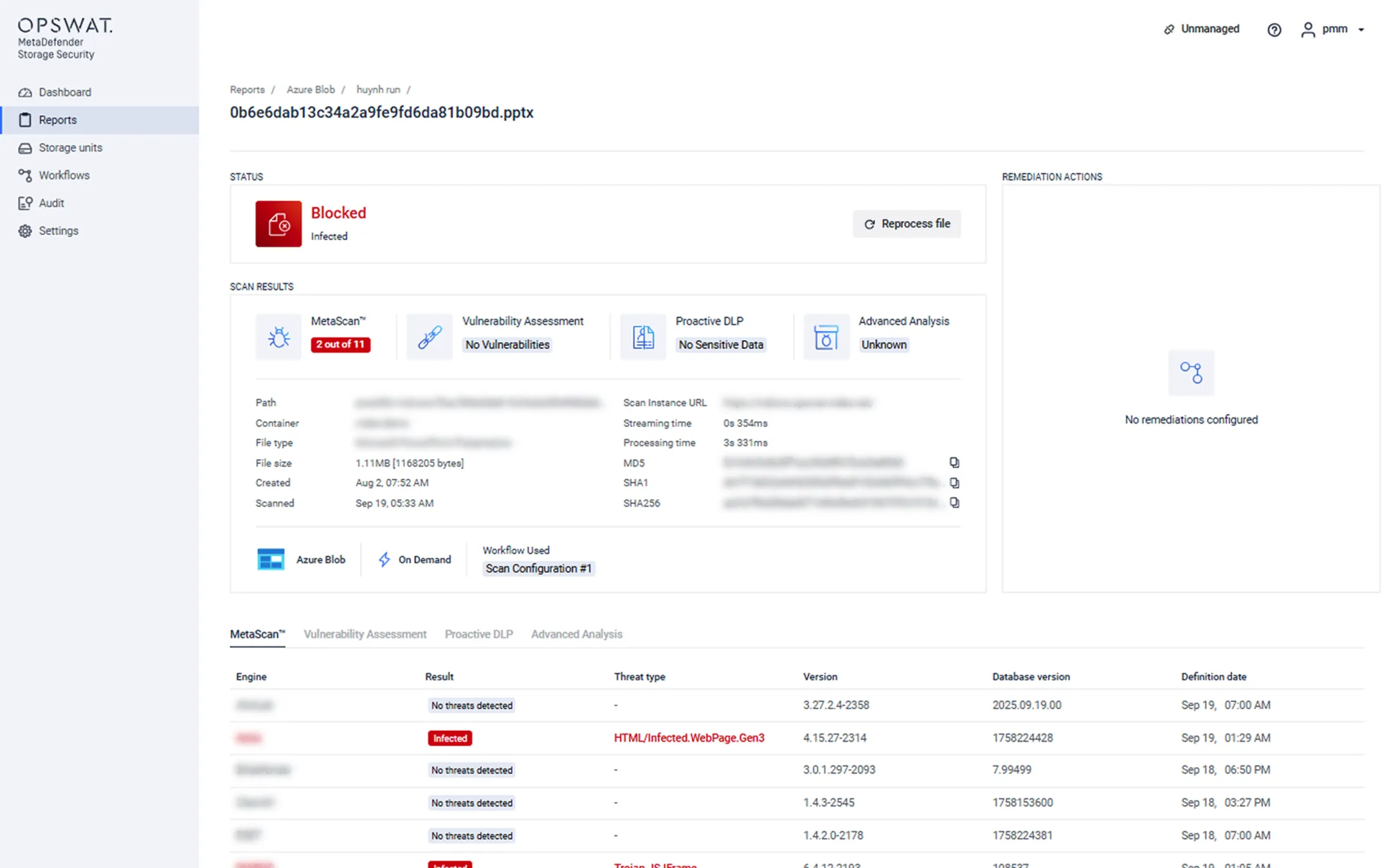
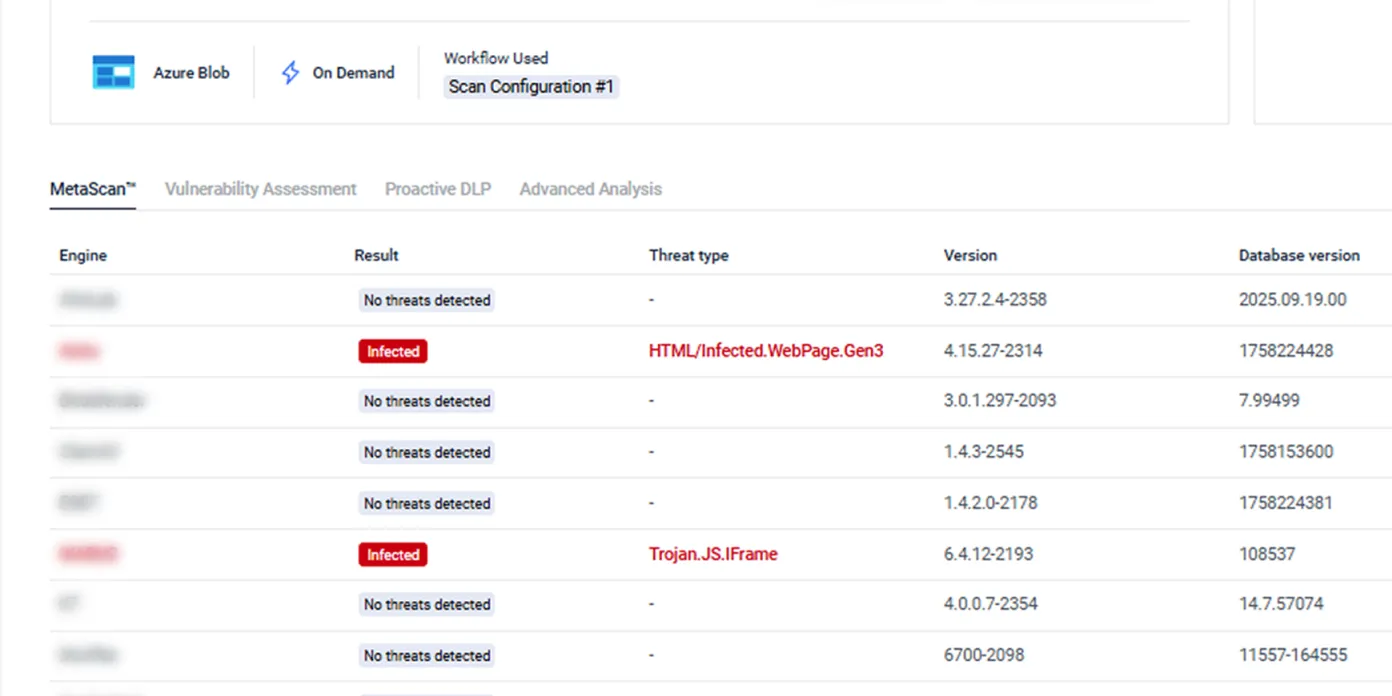
Sanitize Files with Deep CDR™
Remove potentially harmful and out-of-policy objects in files and regenerate new, safe-to-use files.
- Process over 200+ file types, including nested archives, for versatility and security across different environments.
- Recursively sanitize files to remove potentially malicious content like embedded scripts and macros.
- Enhance security without affecting efficiency by integrating with various file processing workflows and file upload platforms.
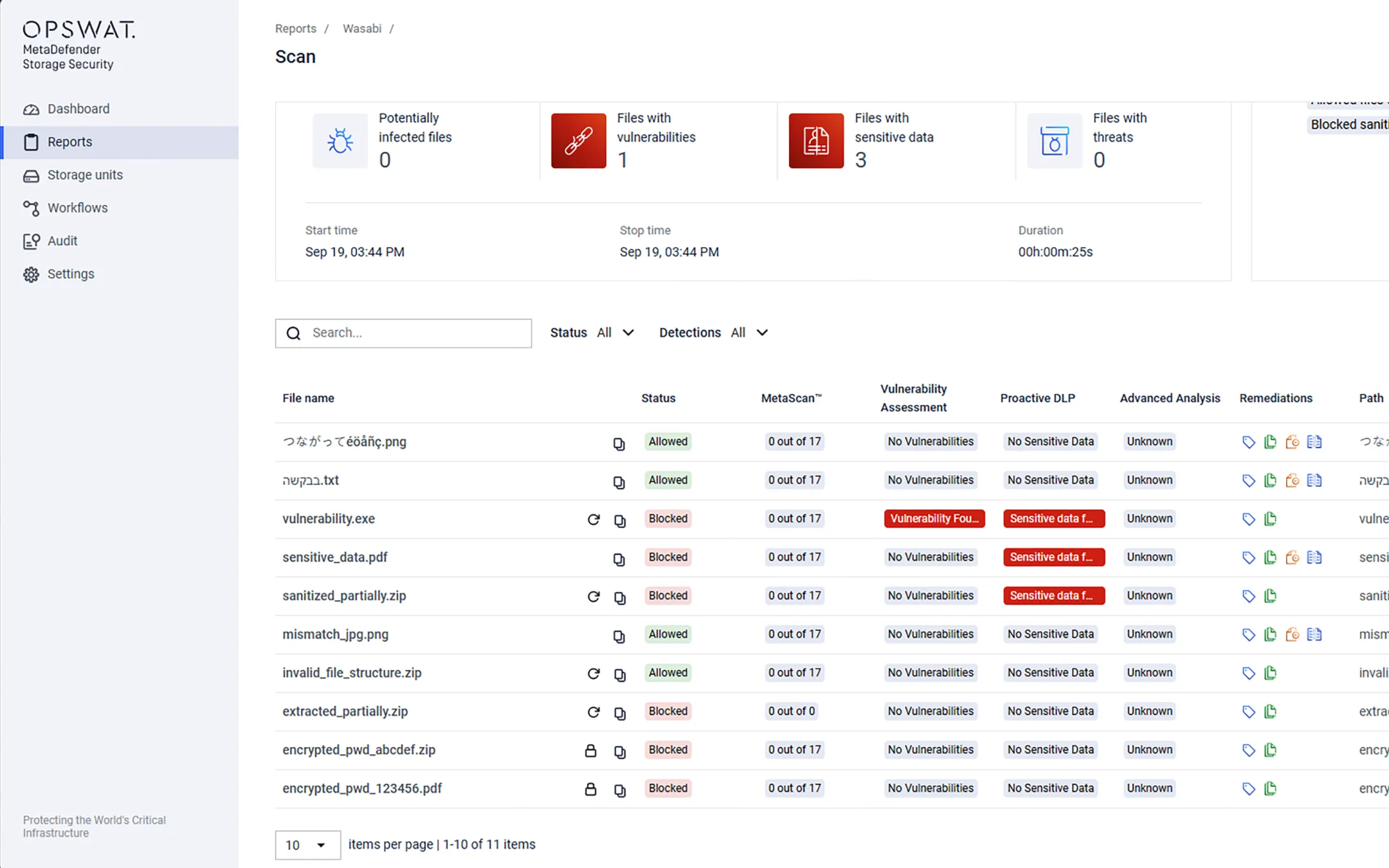
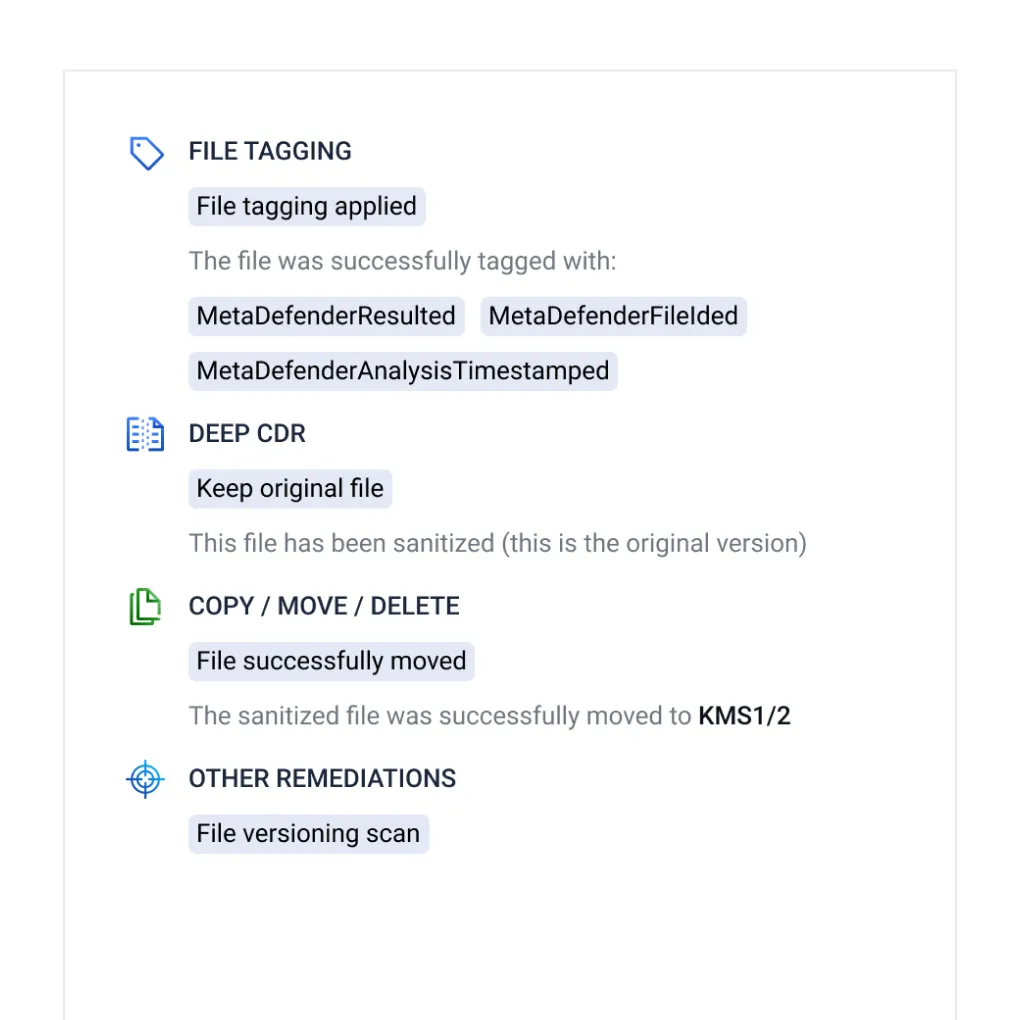
Secure Sensitive Data with Proactive DLP™
Help prevent data breaches and regulatory compliance violations by detecting and blocking sensitive, out-of-policy, and confidential data in files.
- Detect NSFW content with AI-powered document classification.
- Establish custom policies to meet your specific policy requirements.
- Use AI to locate and classify unstructured text into predefined categories.
- Aid compliance with regulations like PCI, HIPAA, Gramm-Leach-Bliley, and FINRA.
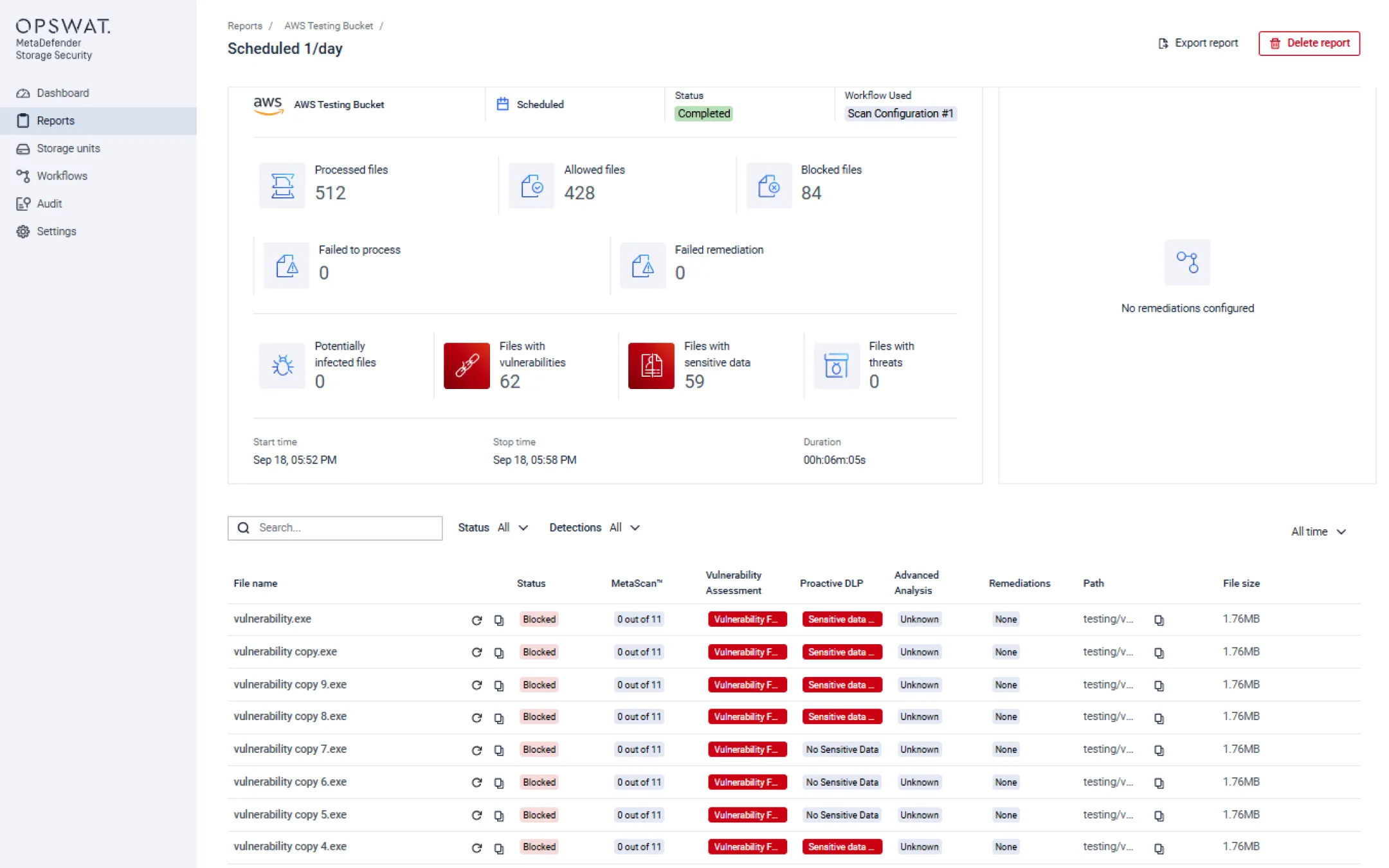
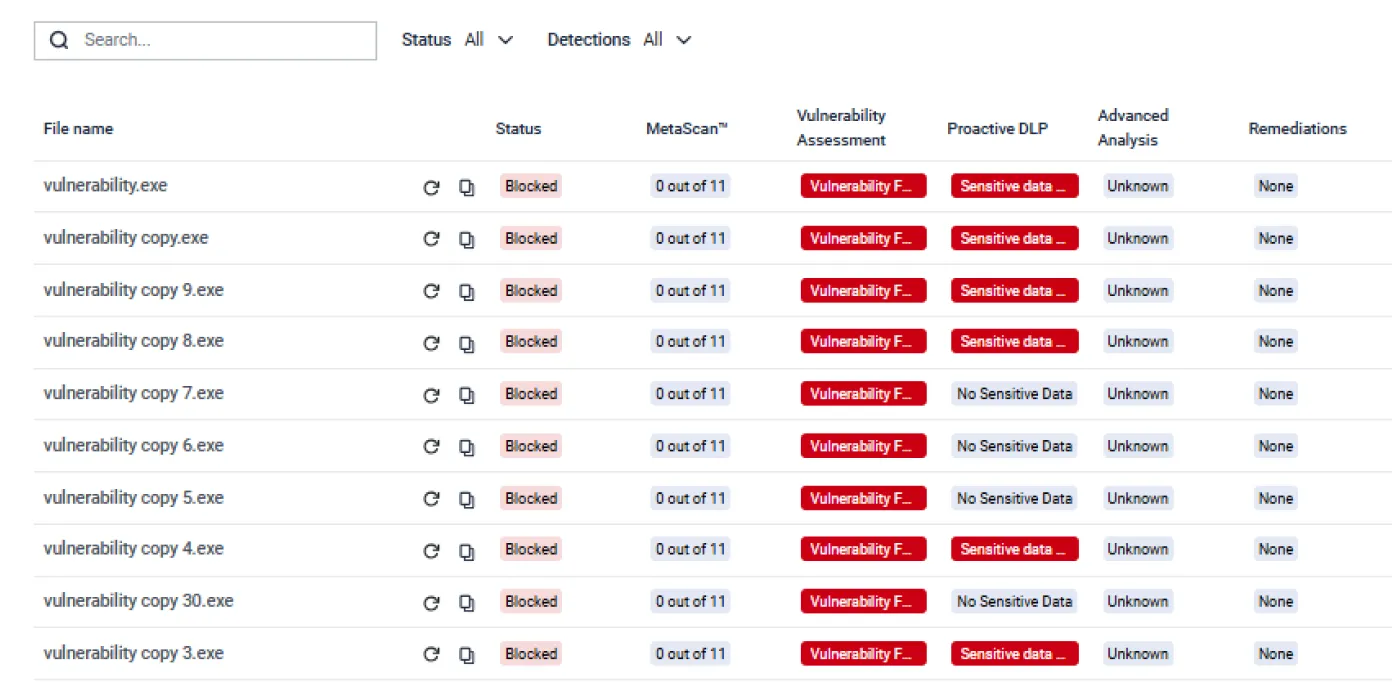
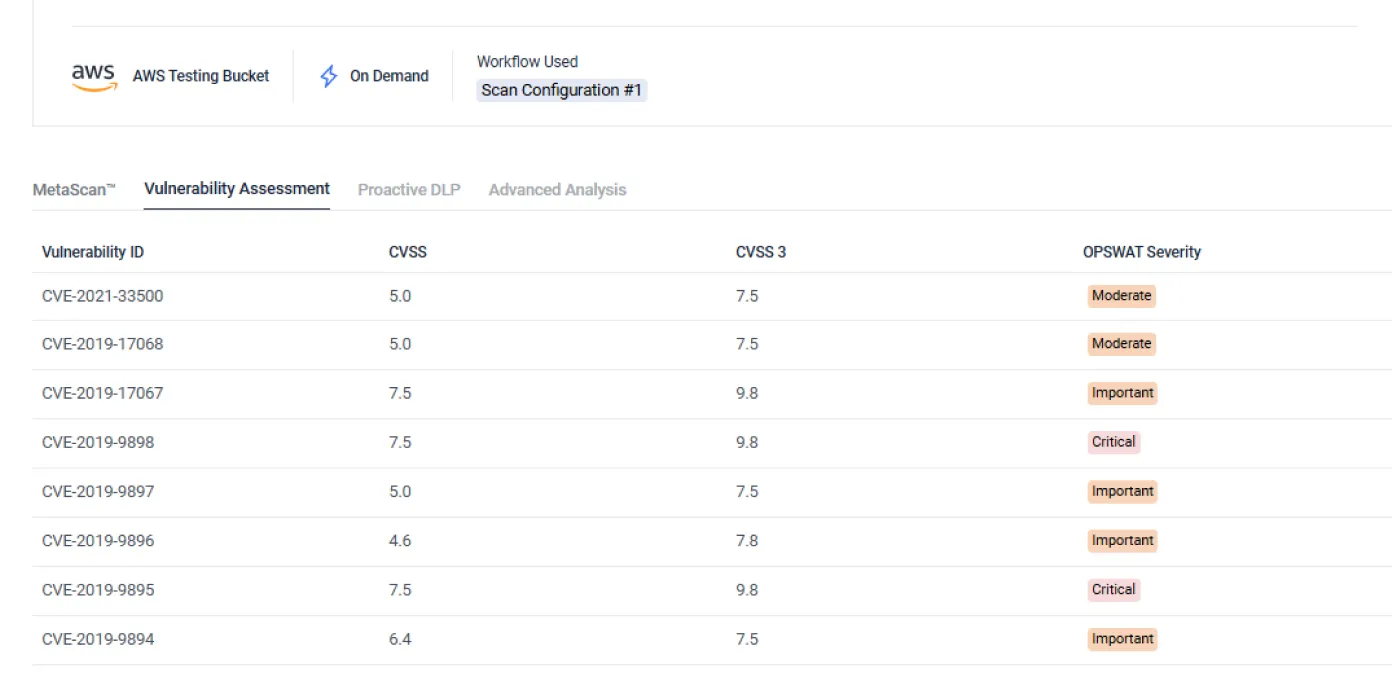
File-Based Vulnerability Assessment
Detect application and file-based vulnerabilities, empowering your security team to patch and remediate before they are installed.
- Check certain types of software for known vulnerabilities before installation.
- Scan systems for known vulnerabilities when devices are at rest.
- Quickly examine running applications and their loaded libraries for vulnerabilities.
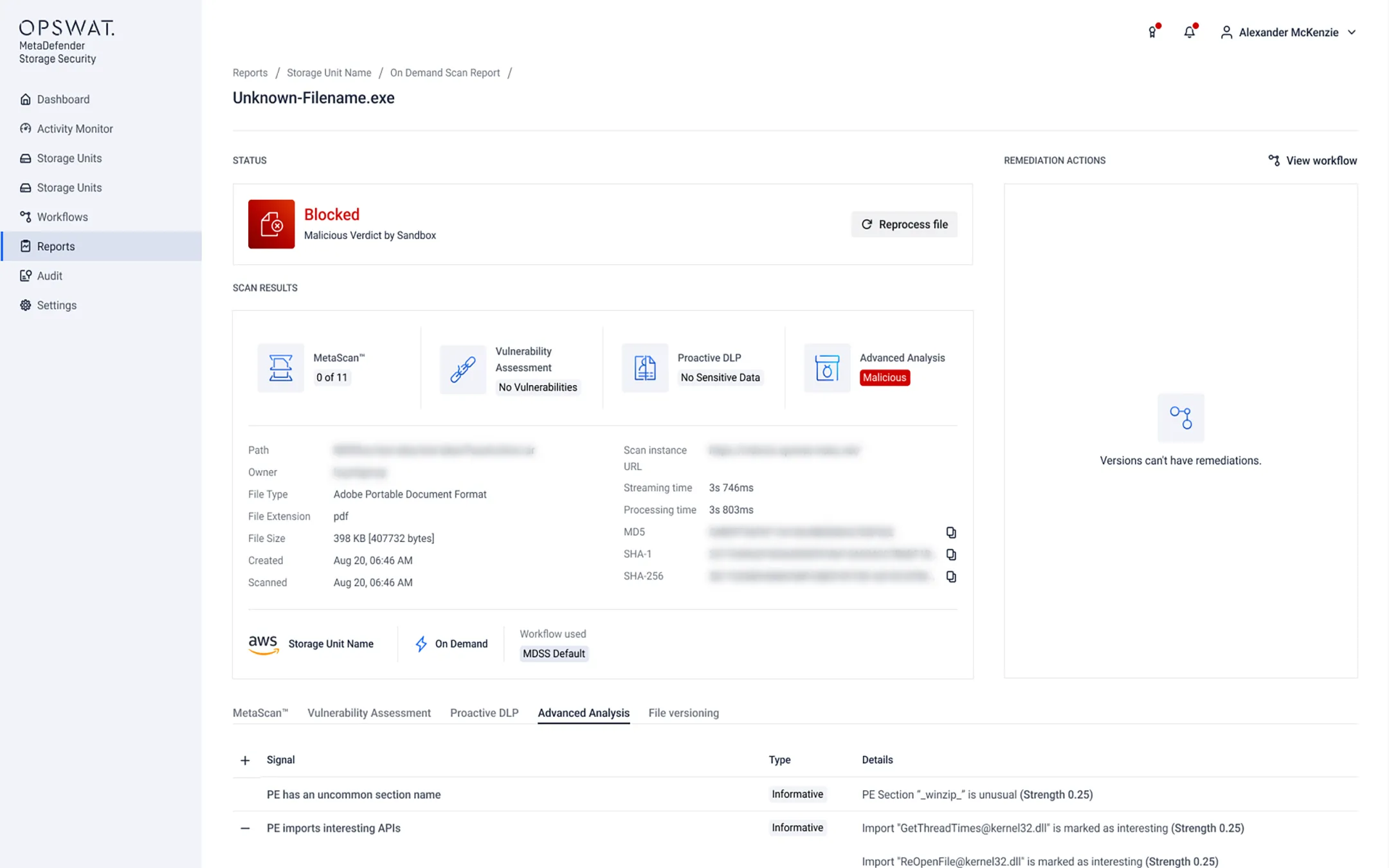
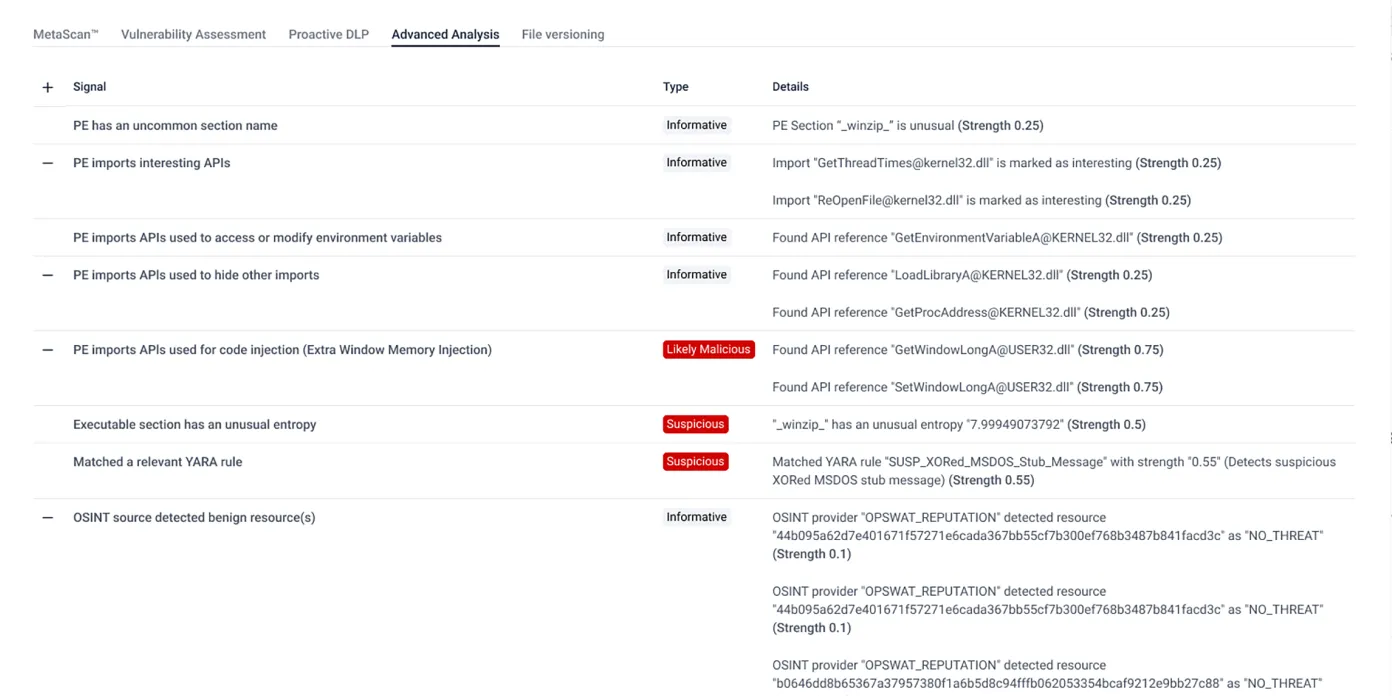
Adaptive Sandbox
Adaptive Sandbox enables zero-day malware detection and extracts valuable IOCs (indicators of compromise) with its advanced, emulation-based approach that operates 10x faster and 100x more efficiently than traditional sandboxes
- AI-Powered URL Threat Detection
- Defeats anti-VM, anti-debug, and time-based evasion—no manual tuning required
- Auto-Generates YARA Rules & IoCs in Real-time
- Supports Any Environment - On-Prem, Air-Gapped, Hybrid
- Deep Insights with MITRE ATT&CK Mapping & Visual Graphs
Trusted Protection for Files at Rest Across Enterprise Storage
Join 2,000+ organizations worldwide that securely share, transfer, and store files with OPSWAT, protecting critical infrastructure at every step.

“MetaDefender Storage Security was so easy to deploy in our cloud environment and that was a very important factor.”
Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.