File-Based Vulnerability Assessment
Detect Application Vulnerabilities Before They Are Installed
Our File-Based Vulnerability Assessment technology detects application and file based vulnerabilities before they are installed. We use our patented technology (U.S. 9749349 B1) to correlate vulnerabilities to software components, product installers, firmware packages and many other types of binary files, which are collected from a vast community of users and enterprise customers.
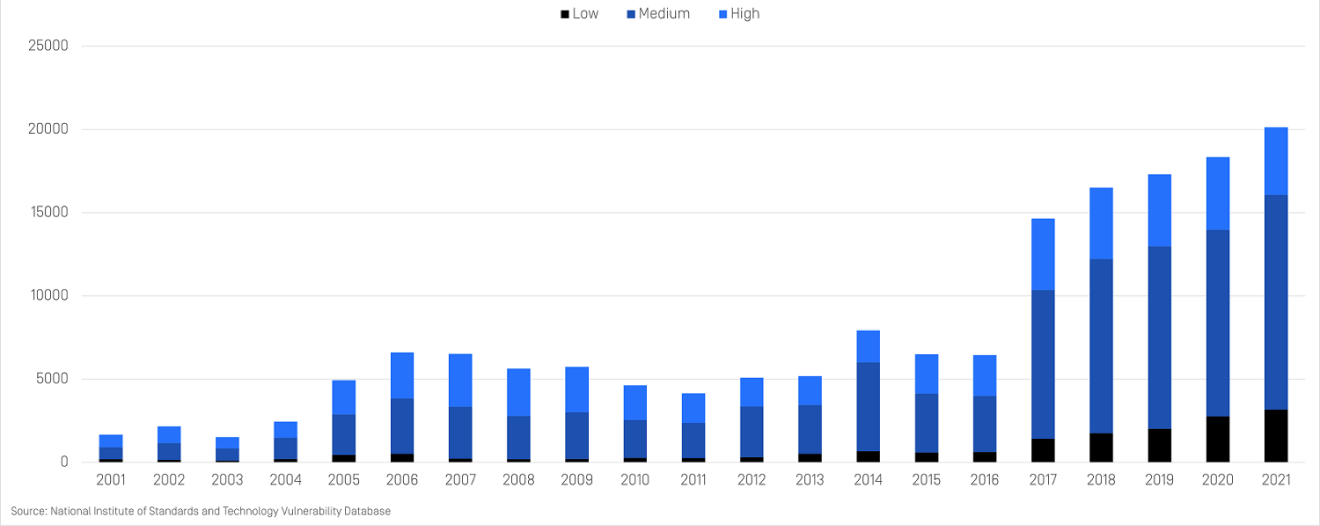
Growth of Software Vulnerabilities Proliferates
As software becomes more complex, the number of application vulnerabilities increases. Every year a new record is set for the number of known vulnerabilities, including not only operating system and application vulnerabilities, but also binary components, Internet of Things (IoT) firmware, and other file based vulnerabilities.
18,400
13.62%
Rapid Growth of File-Based Vulnerabilities
File-based vulnerabilities is one of the fastest growing categories of vulnerability types in recent years.
Application and File-Based Vulnerability Assessment
IOT Software and Firmware Vulnerabilities
Vulnerabilities in IoT software and firmware vulnerabilities are growing in importance. IoT devices are usually designed for specific functions and lack security precautions. Preventing vulnerable firmware from being deployed on IoT devices is a critical security measure given the rapid growth of IoT devices. Our vulnerability scanning technology is capable of detecting software vulnerabilities before installation and deployment.
Over a Billion Data Points
Vulnerabilities associated with specific binary components are hard to detect with traditional vulnerability-scanning technology. Our innovative technology has collected and analyzes over one billion (and growing) vulnerable software data points from in-the-wild devices and uses this data as a foundation for assessing vulnerabilities based on software components.
Detecting Vulnerable Installers
Millions of users are exposed to attacks that leverage vulnerabilities. Detecting and preventing installation programs from getting into your network and being used to propagate vulnerabilities is one of the top cybersecurity best practices.
Assess Vulnerabilities Before They Are Deployed
Most vulnerability scanning solutions identify vulnerabilities after applications are already installed, which creates a detection window that can be exploited. OPSWAT’s patented Computer Security File-Based Vulnerability Assessment (U.S. 9749349 B1) technology assesses and identifies vulnerabilities through binary files that are associated with vulnerable components or specific application versions. It gives IT administrators the ability to:
- Check certain types of software for known vulnerabilities before installation
- Scan systems for known vulnerabilities when devices are at rest
- Quickly examine running applications and their loaded libraries for vulnerabilities
