
Latest Articles

Jan 22, 2026 | Endpoint Management
How MetaDefender Endpoint™ Supports Your Cyber Essentials Compliance Journey
Over the last six months, malware complexity has jumped by 127%, according to OPSWAT’s 2025 Threat Landscape Report.



Oct 18, 2024 | Endpoint Management
Remediating the CVE-2024-0517 Vulnerability in Google Chrome


Sep 26, 2024 | Endpoint Management
Fortifying Endpoint Security for Omnissa Access™ with OPSWAT MetaDefender® IT Access
Discover Critical Infrastructure Protection at One of OPSWAT’s Global Experience Labs
Explore More


Aug 30, 2024 | Endpoint Management
The Security Advantages of OPSWAT MetaDefender Endpoint for Critical Infrastructure


Sep 5, 2023 | Endpoint Management
How the Zero-Trust Principle Terminates the Terminator Antimalware Killer

Aug 24, 2023 | Endpoint Management
New Geofencing Capabilities for MetaDefender Access: A Powerful Tool for Endpoint Compliance
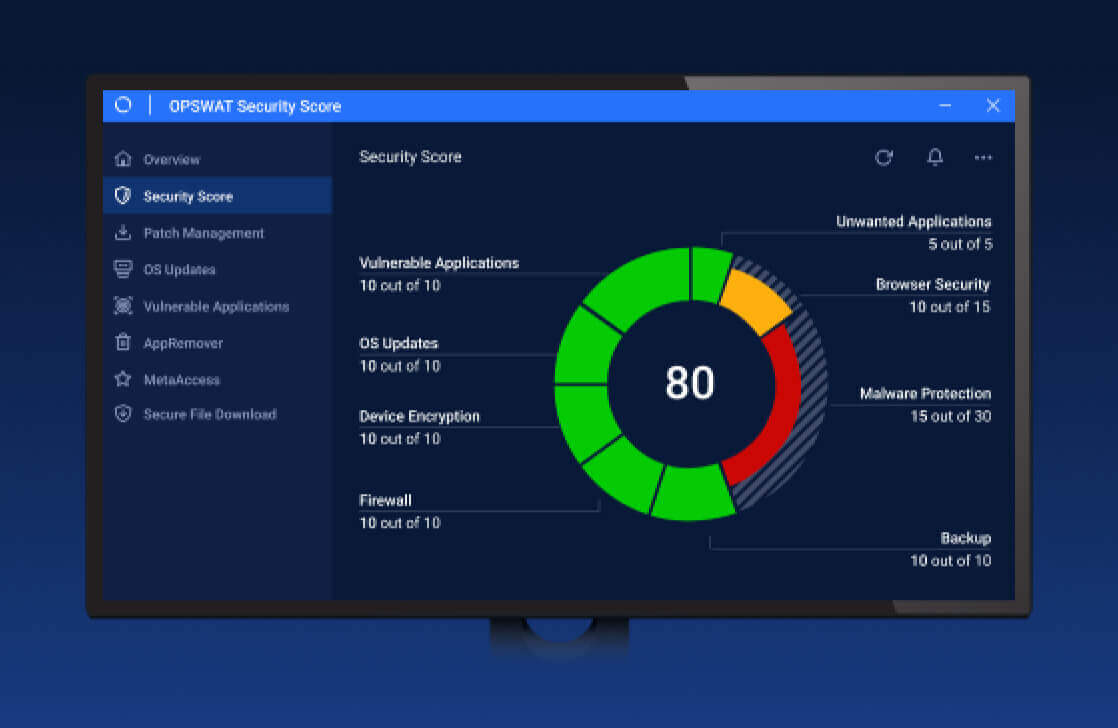
Aug 22, 2023 | Endpoint Management
Enterprise-Level Cybersecurity for All: Reintroducing OPSWAT Security Score

