What is Ransomware?
Ransomware is a type of malicious software (malware) designed to permanently block access to computer resources or encrypt data until a ransom is paid to the attacker.
Some of the most common types of ransomware include:
- Crypto Ransomware: Also known as encryption malware, it is the most common type of ransomware. Crypto ransomware encrypts data and files on a computer system and demands ransoms for the decryption key.
- Locker Ransomware: Locker ransomware doesn’t use encryption. Instead, it disables basic computer functions to block the user from using the device until the ransom is paid.
- Scareware: While not always grouped in the ransomware category, scareware frightens users into believing that their computer is infected with a virus, then urges them to purchase cleaning software with the objective of making money or compromising the system.
- Doxware (or Leakware): Doxware encrypts, exfiltrates, and threatens to publish confidential or personal information unless a ransom is paid.
Ransomware attacks can cause severe damage to critical infrastructure organizations such as manufacturers, businesses, health institutions, and schools, which must maintain consistent operation and protect important data.
Ransom payments, if paid, can range from thousands to millions of dollars per incident. Organizations falling victim to attacks also endure irrevocable reputational damage and remediation costs, including system downtime, data recovery, and the provision of new hardware or software.
Moreover, organizations’ data is at stake, as there is no guarantee that attackers will hand over the decryption key after the ransom is paid. Even when the data is decrypted by the key, it is often corrupted and requires regeneration by the organizations, if possible.
How Ransomware Works
The increased digitization of organizational infrastructure has introduced multiple attack vectors for ransomware. The most common method is phishing emails, which impersonate legitimate senders and contain malicious links or attachments. Attackers also spread ransomware through dubious websites and applications, which can automatically download malware without the user’s knowledge.
Vulnerabilities in system infrastructure may be targeted for ransomware attacks. For instance, attackers can remotely infiltrate and infect corporate networks with ransomware through inadequately secured RDP (Remote Desktop Protocols).
Once attackers gain access, ransomware executes on the victim’s system, scanning the network for target files and seeking higher privileges to spread further. It then encrypts valuable files, such as documents and records. Most ransoms use asymmetric encryption, that means that ransomware encrypts the aforementioned data with a public key, which will be only decrypted by the private key (stored in the attacker's side).
Upon losing access to files and data, victims will encounter a ransom note demanding payments to recover their encrypted or stolen assets.
Unique Challenges in IT/OT Environments
Ransomware can affect IT/OT environments in distinct ways:
- In IT environments, ransomware typically causes data loss or access blockage. In OT environments, ransomware can cause malfunction, physical damage, and safety hazards. Recently, a steel mill in Germany suffered severe damage to its blast furnace when a cyberattack, initiated through phishing, exploited unknown vulnerabilities, and bypassed the standard shutdown procedure.
- Because of the interconnected nature of networks between IT and OT environments, OT components can be compromised even if the ransomware originates in IT, and vice versa. This necessitates a comprehensive defense line across all possible attack surfaces.
- Critical infrastructure OT systems must maintain real-time operation with minimal latency, such as in power grids, water treatment facilities, or manufacturing lines. This complicates ransomware attack response efforts, as delayed shutdowns or isolation of infected components can lead to further ransomware spread and damage.
- The possible impact of ransomware on interconnected IT and OT environments is significant. A ransomware attack on critical infrastructure, such as petroleum supply chains, can disrupt gasoline production and distribution, causing widespread disruption to civilian and industrial activities.
12 Expert Strategies to Prevent Ransomware Attacks
Drawing on more than 20 years of protecting critical infrastructure and being trusted by over 1,700 organizations globally, we know what it takes to get between ransomware attacks and your business continuity. Here are 12 proven strategies to combat ransomware threats.
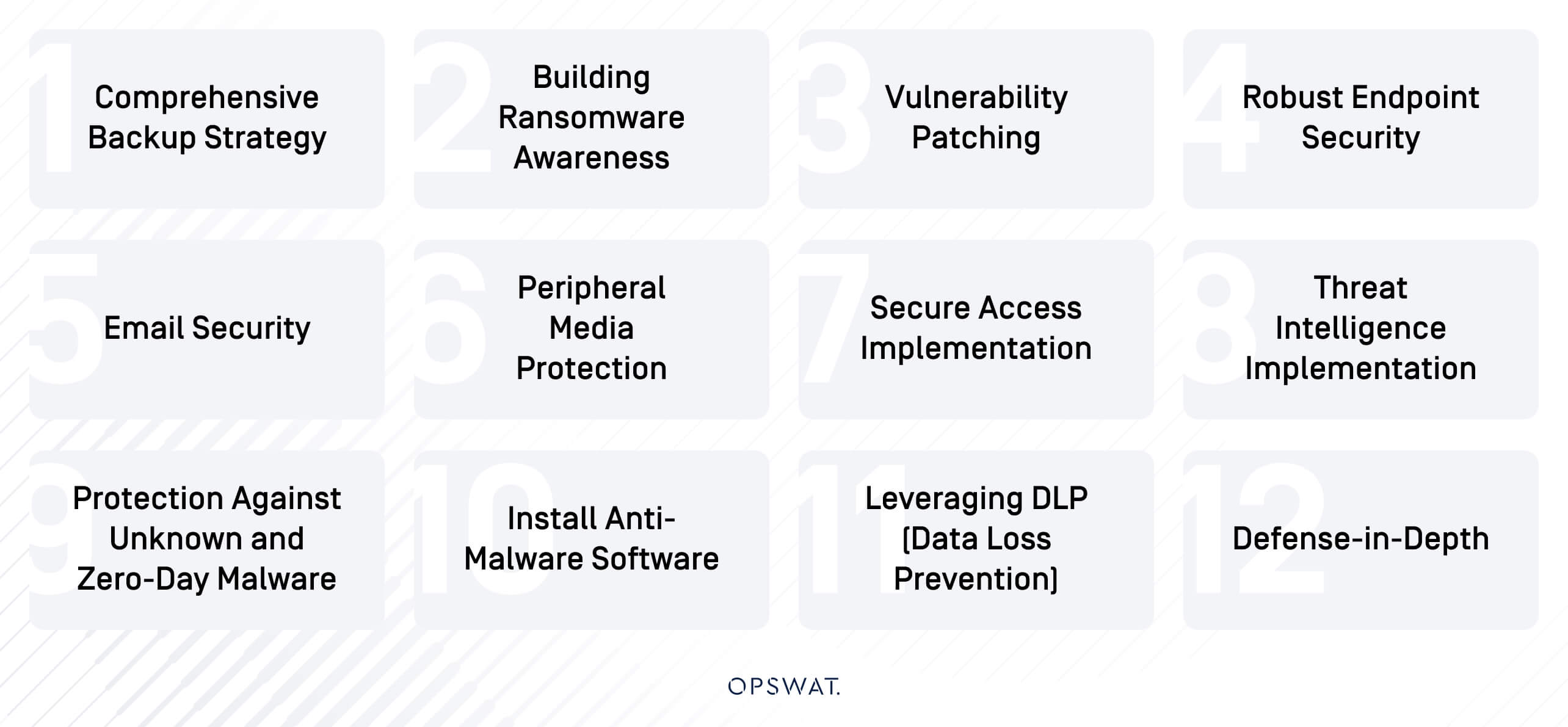

Comprehensive Backup Strategy
The first and foremost preventative defense strategy against ransomware is to regularly back up critical data to protect against loss or damage. Backup repositories can be stored securely offline or in a separate, vaulted network, allowing data to be recovered without paying the ransom in case of an attack. This essential process can be secured with the use of a one-way security gateway solution, like MetaDefender Optical Diode.

Building Ransomware Awareness
Any cybersecurity strategy must secure the weakest link in the security chain: the human factor. Mandatory training courses, knowledge bases, phishing tests, and regular assessment are effective methods to build strong awareness against social engineering tactics from ransomware attackers. OPSWAT Academy offers professional training courses and resources that equip learners with comprehensive cybersecurity knowledge, skills, and expertise.

Vulnerability Patching
Systems and infrastructure get more complex as organizations mature. It is crucial to keep them continually patched with the latest security updates and versions to reduce vulnerabilities that ransomware attackers can exploit. MetaDefender’s Patch Management module can identify the latest updates available to endpoint applications and patch them automatically.

Robust Endpoint Security
As organizations embrace remote, or more decentralized working options, they also need to protect and secure endpoint devices. MetaDefender’s Deep Endpoint Compliance enforces comprehensive, beyond standard endpoint policies such as OS level checks, security software, malware scanning, vulnerability management, and disk encryption.

Email Security
Ransomware can also be attached to emails, sent by attackers as a spear phishing or scamming method. Sophisticated email attacks can resemble legitimate senders and create a sense of urgency to open or download attached files. Enterprise email systems must integrate effective anti-malware capabilities, such as MetaDefender Email Security, preventing zero-day phishing, on-click URL, credential and CC harvesting, data leakage, and more.

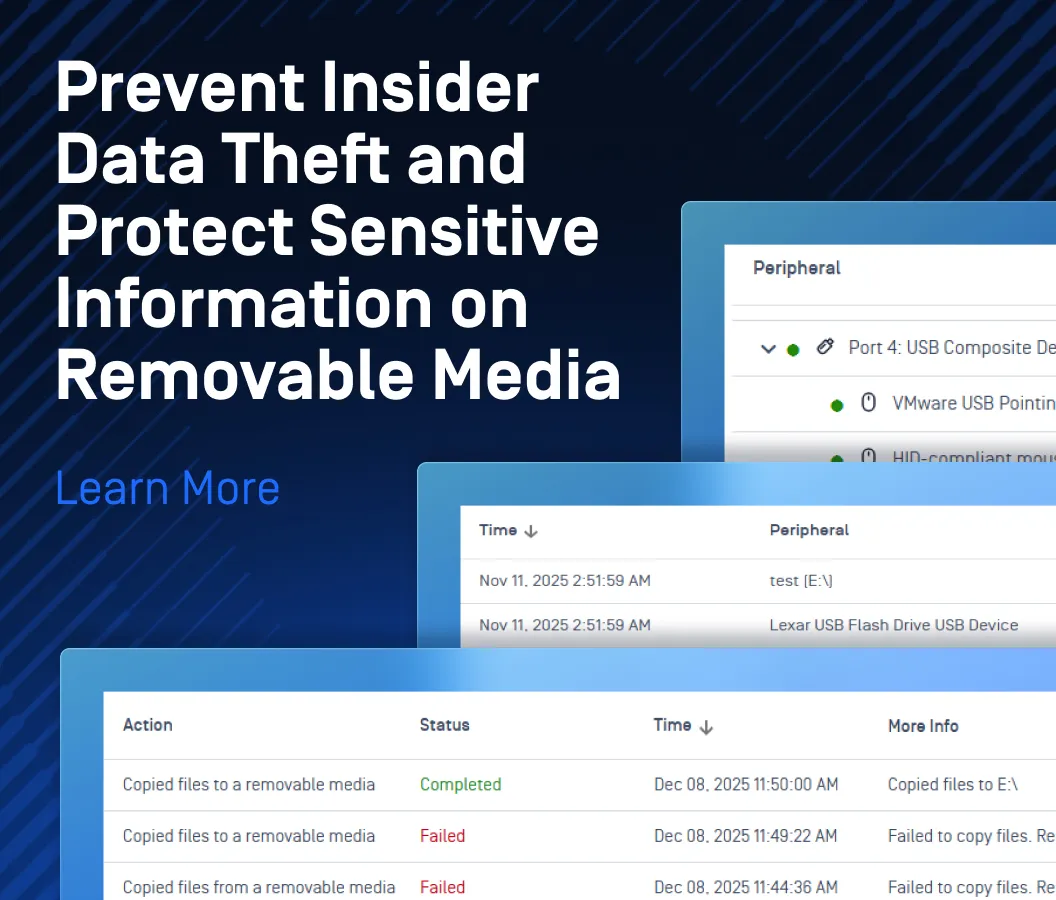
Peripheral Media Security
Organizations need to also protect themselves from file-borne threats from peripheral and removable media like USB flash drives and other portable storage devices. Any incoming media must be scanned and sanitized to prevent any malicious content from entering organizations’ infrastructure. OPSWAT’s Peripheral Media Protection solutions can scan most media types, achieving a 99.2% detection rate, and ensuring files and boot sectors are sanitized and safe prior to use.
Secure Access Implementation
Secure Access involves monitoring and controlling network entry points, ensuring every device or connection is visible in real-time. MetaDefender Access provides a consolidated view of the security posture of all connection nodes, enabling the enforcement of security compliance when necessary.
Threat Intelligence Implementation
Increase threat detection operations efficacy by adopting and integrating high quality Threat Intelligence feeds. MetaDefender Threat Intelligence can provide key detection and contextualization across security controls it is integrated with to drive detection and blocking of Ransomware and other malicious cyberthreats.
Protection Against Unknown and Zero-Day Malware
Unknown and zero-day malware exploit undiscovered vulnerabilities, allowing attackers to bypass traditional solutions. MetaDefender Sandbox integrates advanced anti-malware solutions that utilize adaptive threat analysis to detect zero-day malware and successfully analyzes evasive and sophisticated threats that can leave systems vulnerable to ransomware.
Install Anti-Malware Software
A trusted anti-malware solution with strong, effective engines is essential for any ransomware prevention strategy. Organizations should adopt anti-malware solutions that combine multiple AV engines that can detect and isolate malicious files and activities in real time. OPSWAT's reputable Multiscanning technology incorporates 30+ leading anti-malware engines, detecting nearly 100% of known threats. Moreover, efficiently manage multiscanning instances and results with MetaDefender Endpoint.
Leveraging DLP (Data Loss Prevention) Against Double Extortion Ransomware
Many ransomware attacks now involve double extortion, where attackers not only encrypt data but also steal it, threatening to leak it unless a ransom is paid. OPSWAT’s Proactive DLP helps prevent this by detecting and blocking the unauthorized transfer of sensitive data—like PII (personal identifiable information), financial records, and intellectual property—before it leaves the network. With real-time content-checking of files and emails, AI-powered classification, and OCR for images, DLP solutions reduce the risk of exfiltration and ensure compliance with standards like PCI, HIPAA, and GDPR.
Defense-in-Depth
A multi-layered defense strategy is highly effective when applied across possible attack surfaces of IT/OT infrastructure. Defense-in-depth is an approach that layers numerous defensive measures to become a fortification around information and data. If one line of defense fails, others remain to prevent attackers from penetrating and causing harm. Leveraging the broad array of effective technologies and solutions from OPSWAT’s MetaDefender Platform organizations can build a robust defense that comprehensively protects all attack surfaces, preventing ransomware attacks at various stages.
Staying Vigilant Against Future Threats
Ransomware remains an imminent cyberthreat due to significant financial gains for attackers. As a result, ransomware criminals are always devising more tactics and methods to target any vulnerable components in the system. It is crucial to safeguard critical resources in case of attacks through data backup, network segmentation, and access control. More importantly, organizations must always assess and monitor their infrastructure to remain prescient and defend against pervasive attack vectors.