Rapid Zero-Day Detection
Detect 99.9% of Zero-day File-Based Attacks with Dynamic Analysis & Built-in Threat Intelligence.
- 99.9% Zero-Day Efficacy
- 20x Faster than Traditional Tools
- 25K+ Analyzes Per Day
OPSWAT is Trusted by
Unified Zero-Day Detection

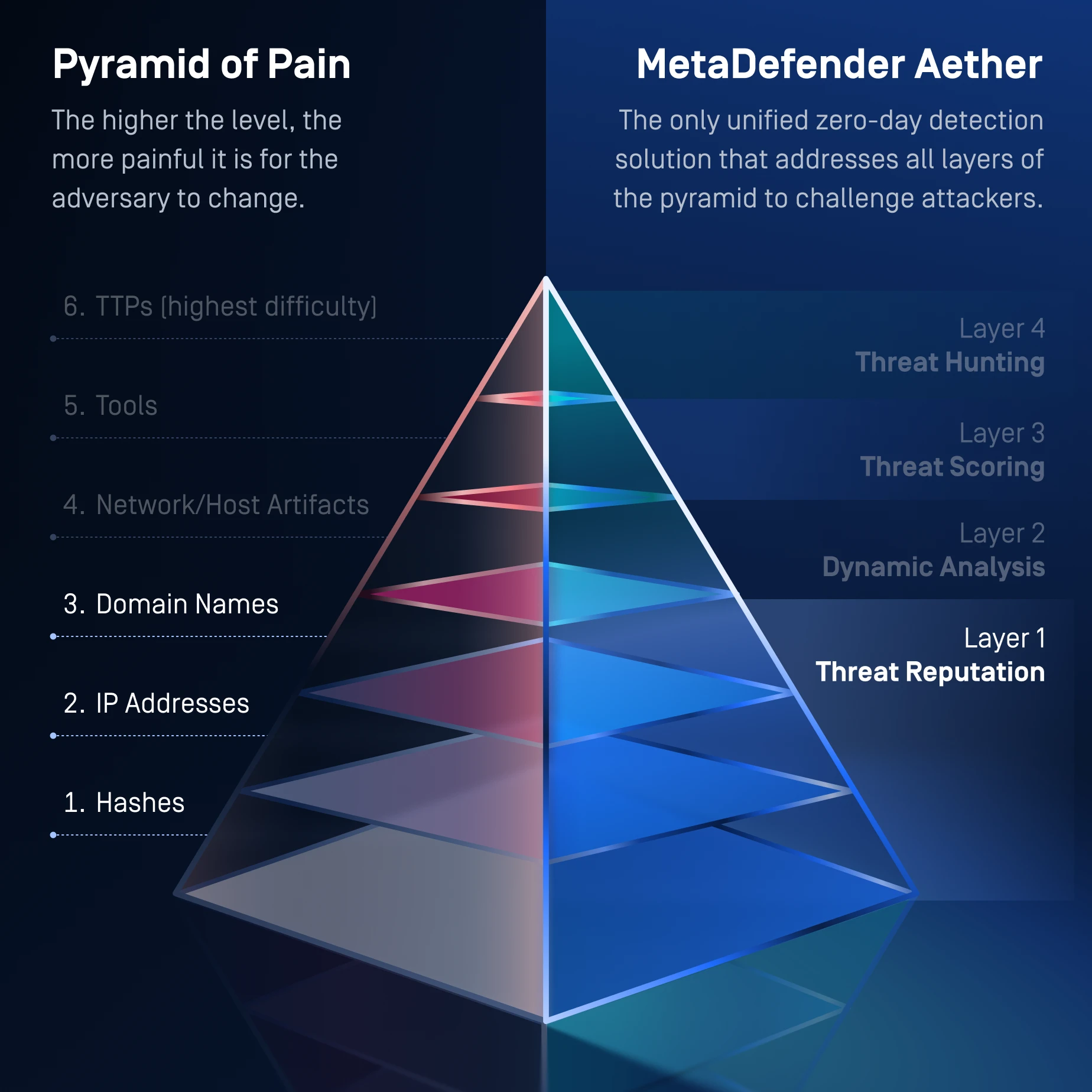
Layer 1: Threat Reputation
Expose Known
Threats Fast
Stop the flood of known threats.
Checks URLs, IPs, & domains in real time or offline to detect malware, phishing, & botnets.
Blocks reused infrastructure & commodity malware and forces attackers to rotate basic indicators.
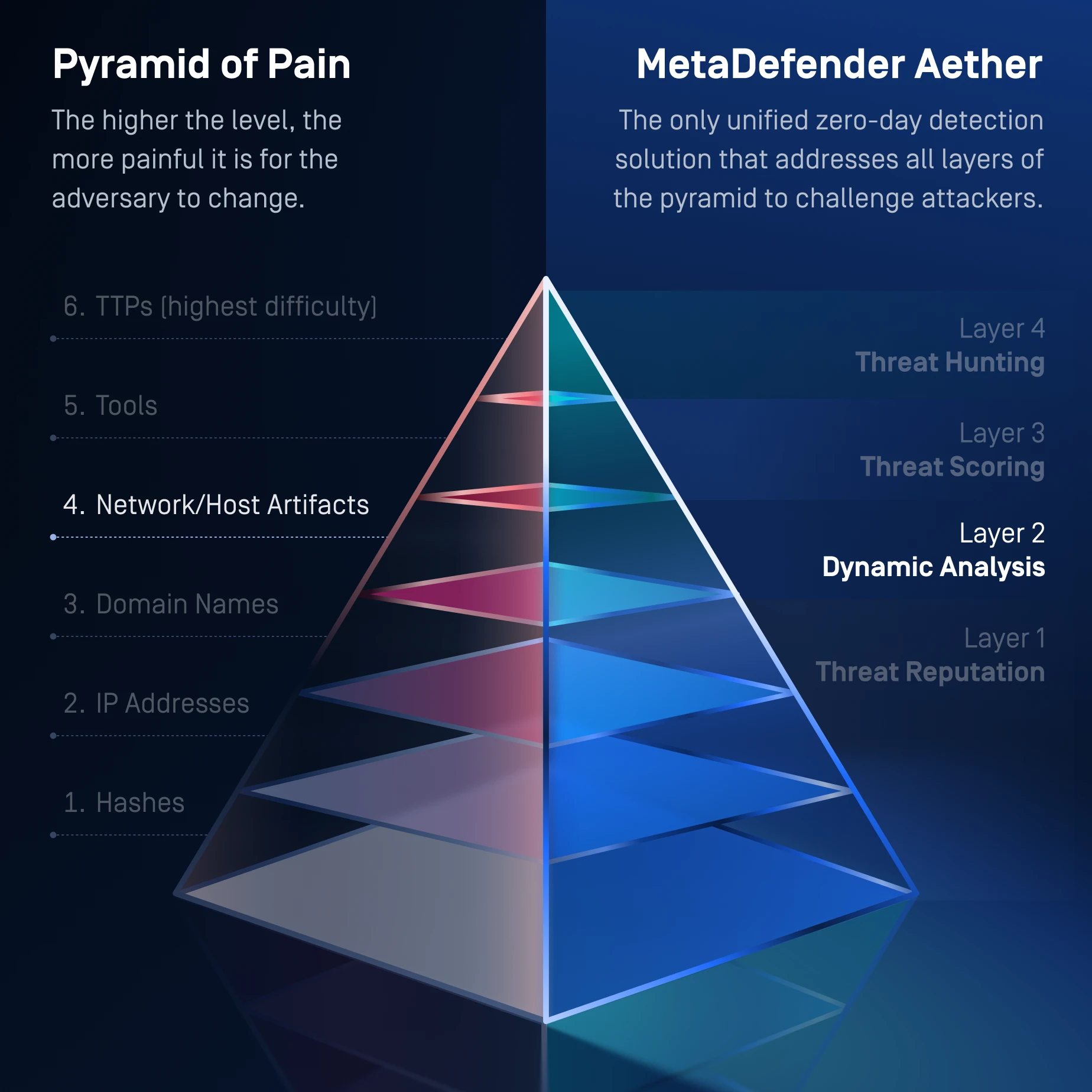
Layer 2: Dynamic Analysis
Uncover Unknown
Threats
Detects evasive malware hiding from traditional sandboxes.
An emulation-based sandbox analyzes files to detect hidden threats like ransomware.
Exposes artifacts, loader chains, script logic and evasion tactics.
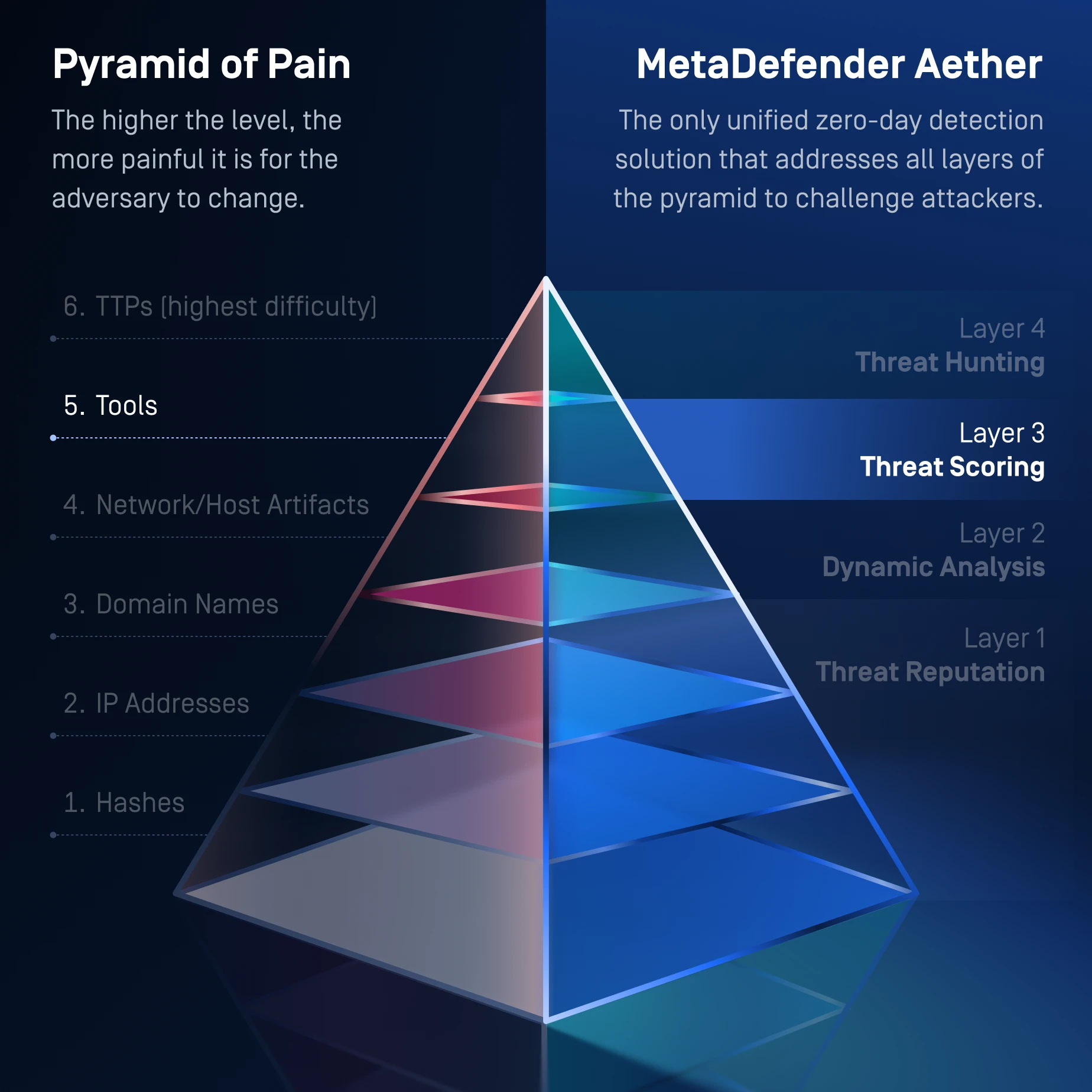
Layer 3: Threat Scoring
Prioritize Threats
Reduce alert fatigue.
Threat risk levels are ranked to quickly highlight priority threats in real-time.
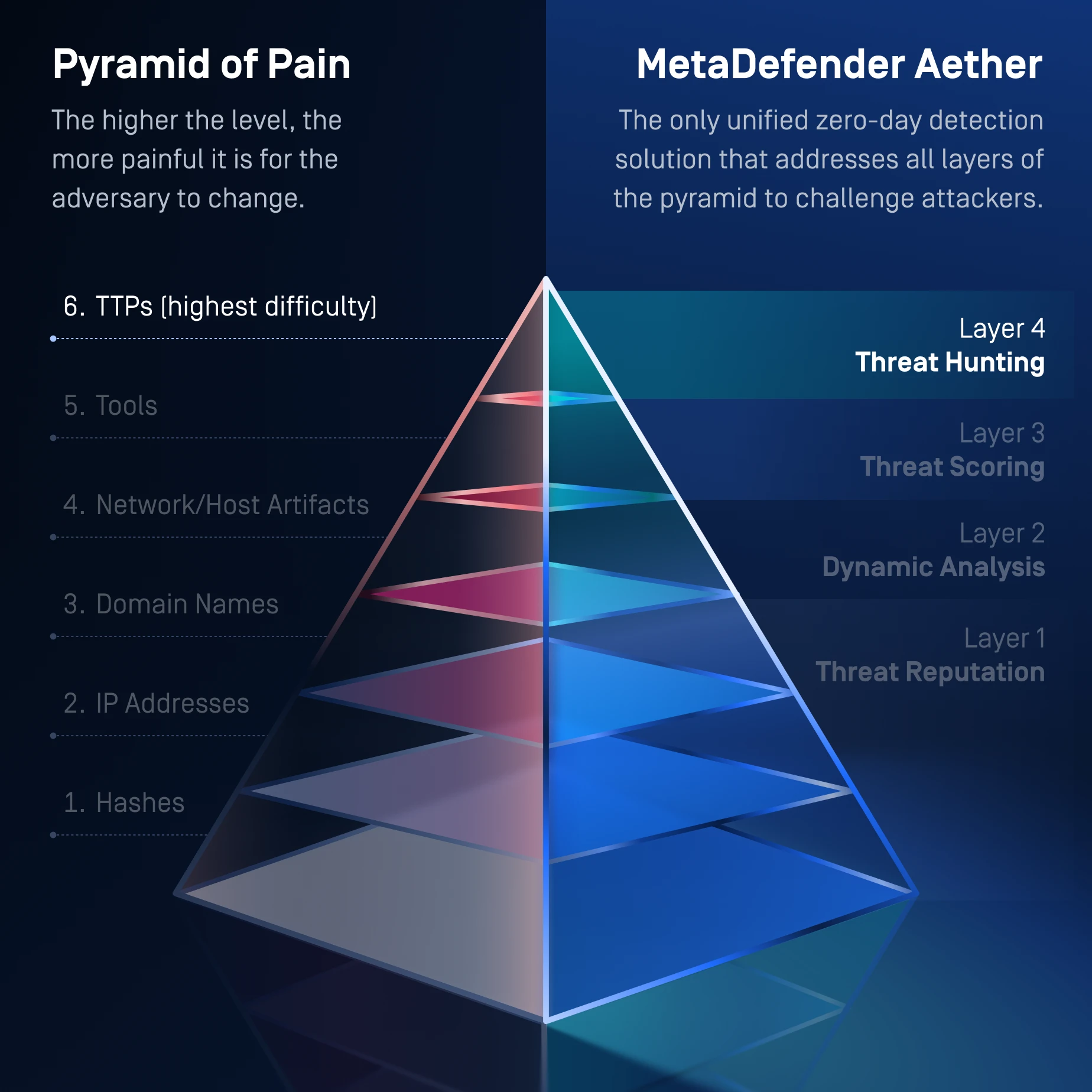
Layer 4: Threat Hunting
Identify Malware
Campaigns
Machine-Learning Similarity Search
Threat Pattern Correlation matches unknown threats to known malware, tactics, infrastructure and more.
Uncovers malware families and campaigns, forcing attackers to overhaul tactics and infrastructure.
Product Overview
Learn how MetaDefender Aether uses AI-powered adaptive sandboxing to detect and stop zero-day attacks
that traditional security tools miss.
One Solution for the Entire Pyramid of Pain
MetaDefender Aether addresses the whole Pyramid of Pain, from commodity indicators at Level 1 to advanced TTP disruption at Level 6, forcing attackers to continually rewrite their infrastructure, tools, & behaviors in order to evade detection.
- Pyramid Levels 1,2,3
Hashes, IPs, Domains (bottom 3 levels of pyramid)
- Hash lookups → detect reused malware binaries
- URL/domain/IP reputation → blocks known infrastructure
- Brands, ML URL classification → block phishing infra
- Offline and online reputation → stops commodity threats
- How It Applies Pressure to Attackers
- Forces attackers to rotate infrastructure
- Makes reused malware indicators worthless
- Breaks automated phishing & botnet distribution workflows
- Forces attackers to rotate infrastructure
- Pyramid Level 4
Artifacts + Tools
- CPU-level emulation reveals runtime artifacts:
- Behavior logs
- Registry edits
- File drops
- Process injections
- C2 callbacks
- Loader behavior
- Memory-only payload exposure
- Unpacks packers, stagers, droppers
- CPU-level emulation reveals runtime artifacts:
- How It Applies Pressure to Attackers
- Forces attackers to redesign payloads
- Exposes loader chains & second-stage artifacts
- Bypasses evasion → attacker must rewrite anti-sandbox logic
- Reveals artifacts that traditional sandboxes miss
- Pyramid Level 5
Tools + TTPs
- Uses context + behavior to detect:
- Malicious execution flow
- Loader patterns
- Script obfuscation signatures
- Malware family behaviors
- Persistence techniques
- 900+ behavioral indicators
- MITRE ATT&CK tactic alignment
- Uses context + behavior to detect:
- How It Applies Pressure to Attackers
- Attackers now must modify how their tools behave
- Not just the payload, but the behavior pattern must change
- More expensive for attackers to pivot
- Pyramid Layers: TTPs
Top Tier – Most painful for adversaries - Level 6 on Pyramid
- ML-based similarity search correlates:
- Malware families
- Recompiled variants
- Infrastructure clusters
- Polymorphic mutations
- Shared code sections
- Bridges gaps between different artifacts from shared operations
- Behavioral + code similarity → detects unknown variants
- Campaign-level clustering
- ML-based similarity search correlates:
- How It Applies Maximum Pressure
- Hackers must completely change their tactics, tools, infrastructure, AND behavior
- Detects campaigns even when payloads rotate
- Top-tier pain point: attackers must rewrite their entire toolkit
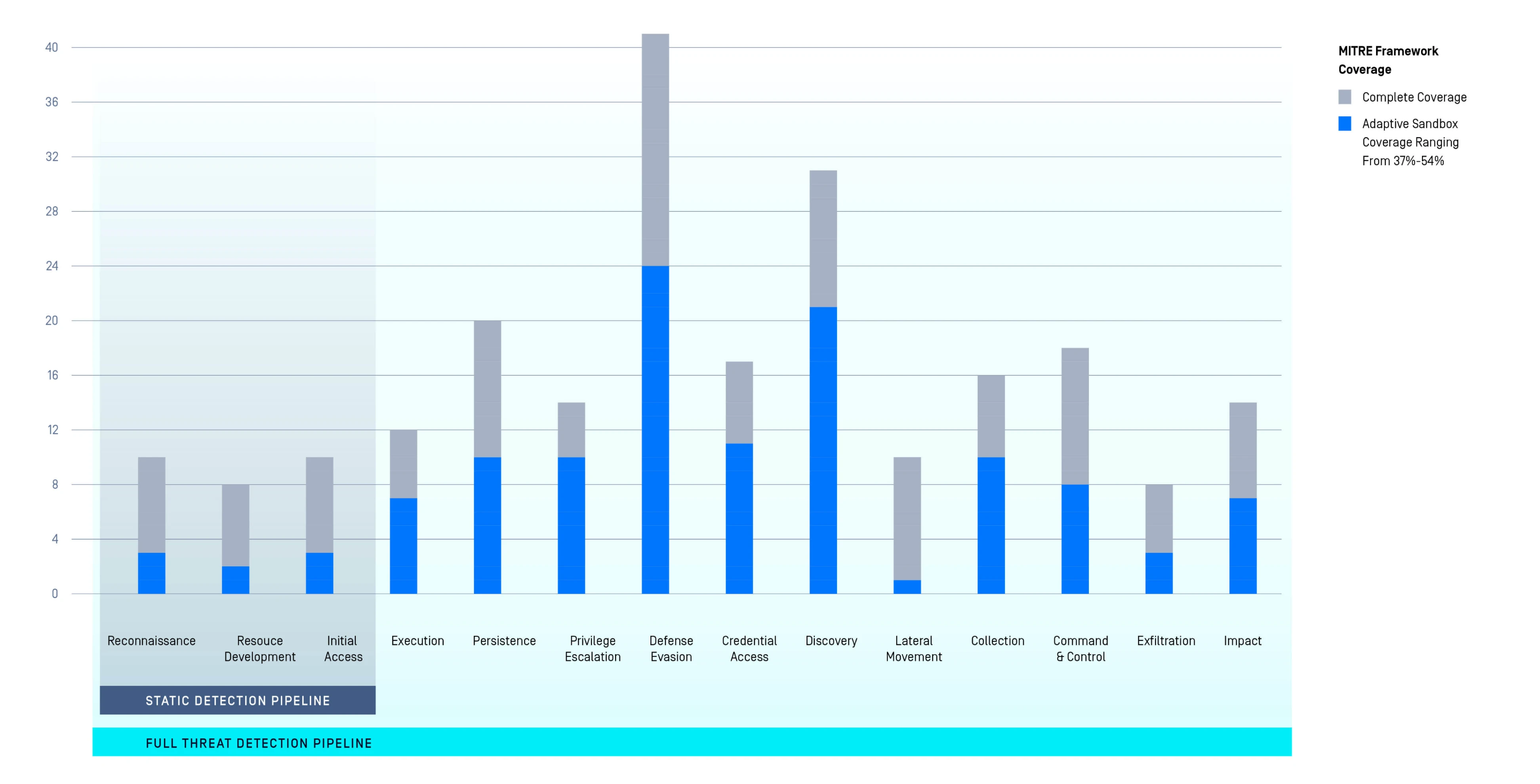
MetaDefender Aether's Impact on
the MITRE ATT&CK Framework
- Layered visibility across the entire attack chain.
- Pre-execution (static) & runtime (dynamic analysis) detection mapped to MITRE Tactics.
- +60% additional detection coverage.
“Fastest Speed We’ve
Ever Tested.”
Venak Security
330+
Detectable Brands
for ML-Based
Phishing Detection
50+
File Types
Extract artifacts,
images, & more
100x
Higher Volume
Integrate Easily
We stop attackers from leveraging
your own files against you
20x
Faster than Traditional Solutions
MetaDefender Aether Features
The table below highlights the core capabilities of the MetaDefender Aether engine.
To explore how these features work together in real-world deployments, contact us to schedule a technical presentation.
MetaDefender Aether Integrations
| Implementation | Appliance | |
|---|---|---|
| Integration | API & Web Interface Integration |
|
| Email Integrations & Format Support |
| |
| Security Orchestration, Automation, and Response (SOAR) Integrations |
| |
| SIEM Integrations | Common Event Format (CEF) Syslog Feedback | |
| Deployment | OPSWAT Threat Detection & Prevention Platform |
|
| Report Format/ Data Export | Report Formats |
|
| Scripting & Automation Tools | Python |
|
MetaDefender Aether Reports
Overview of our cybersecurity software's capabilities, including sample analysis, malware family decoding, disassembly unpacking, similarity search, and more.
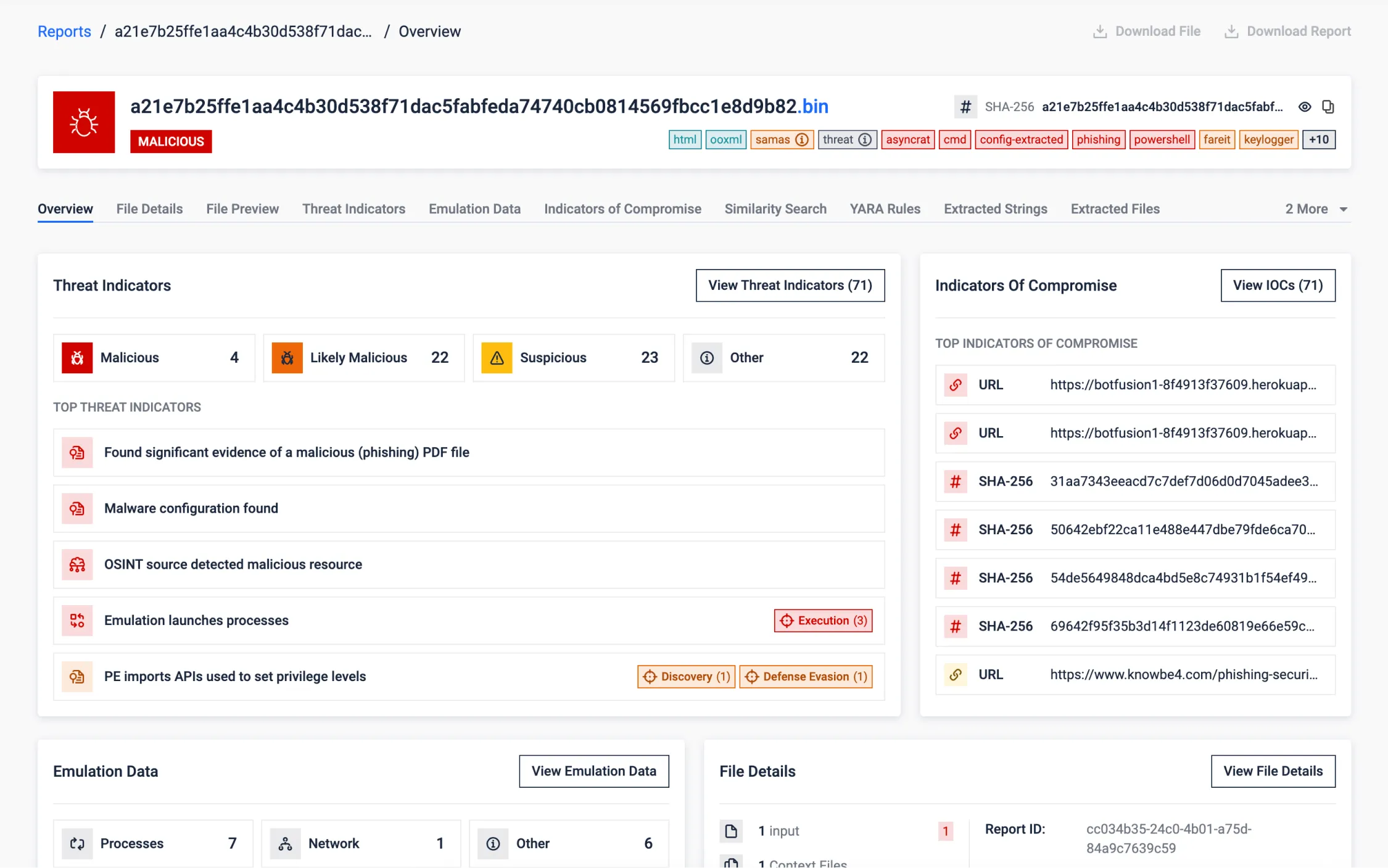
Synthetic (Fabricated) Sample
This sample stands as a purpose-built example to highlight the diverse capabilities of MetaDefender Aether (previously known as OPSWAT Filescan Sandbox).
Crafted to show-off real-world cyber threats, embedding multiple files and file-types into each other. This effectively demonstrates our solution's prowess in adaptive threat analysis, behavioral analysis, and advanced security measures.
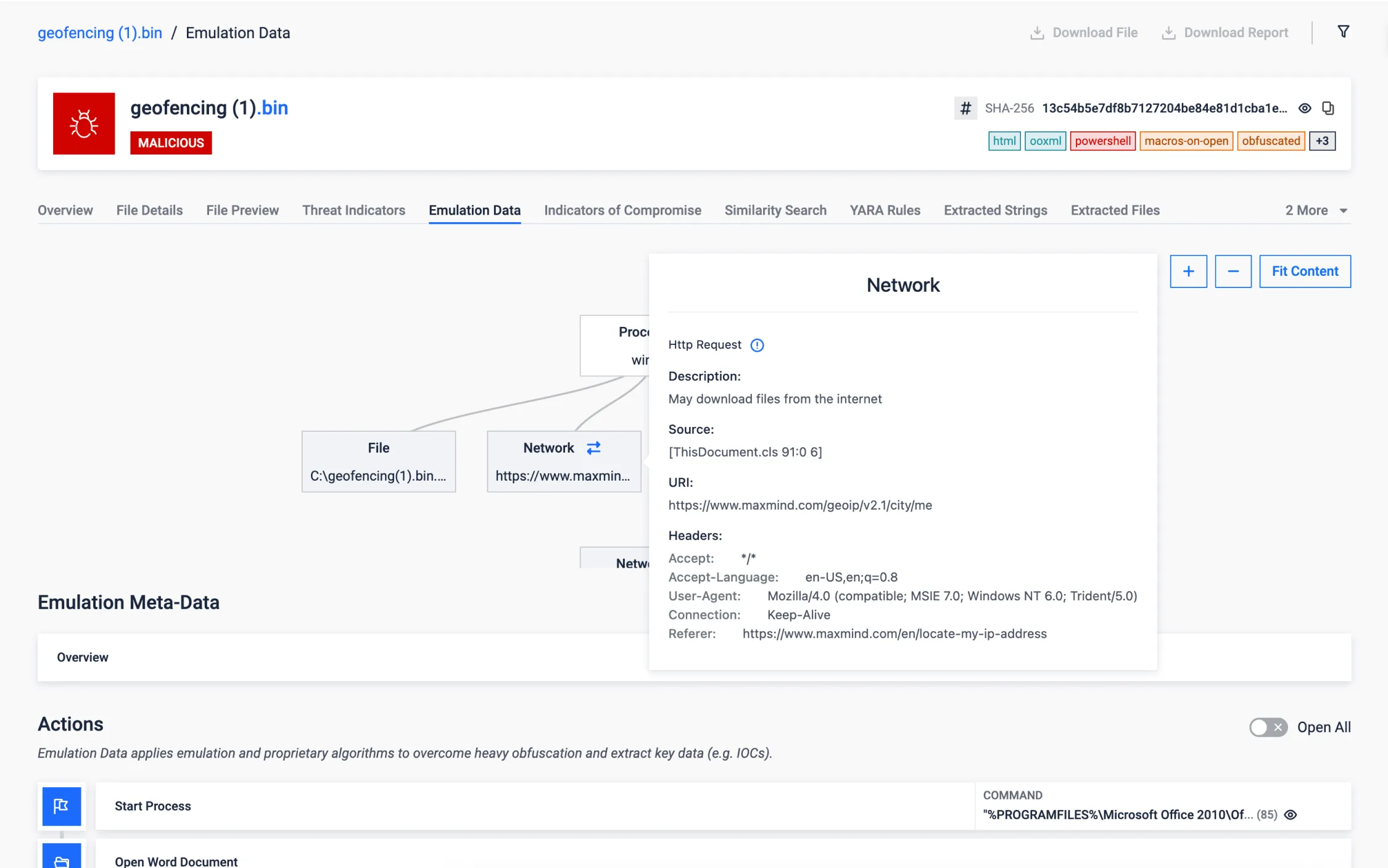
Geofencing
Malware documents employing geofencing have become a significant threat to cybersecurity. These malicious files often employ location-based triggers, making detection and mitigation a challenging task. However, Adaptive Threat Analysis stands out from traditional approaches by offering the capability to accurately emulate and falsify the expected geolocation values, effectively neutralizing the tactics employed by malware, thus enhancing our ability to protect against such threats.
In the sample provided below, we can observe a geofencing malware attempting to execute exclusively within a specific country. However, our innovative solution successfully bypasses this restriction, as previously mentioned, by emulating the desired geolocation values, demonstrating our superior capability in countering such geofencing-based threats.
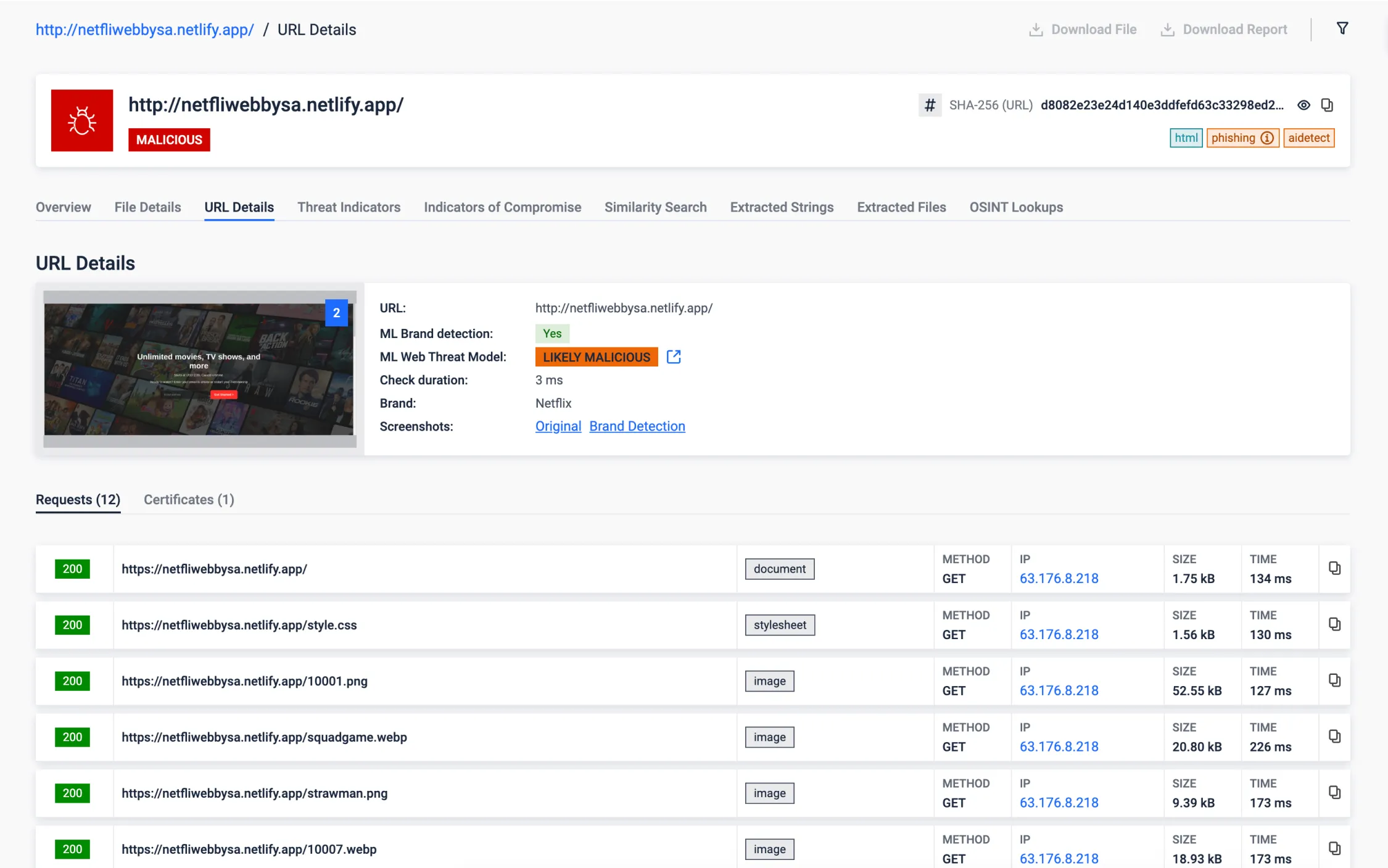
Phishing Detection
- Brand Detection: By rendering suspicious websites and subjecting them to our advanced machine learning engine we're capable of identifying nearly 300 brands. In the example provided below, you can witness a website masquerading as a streaming company known as Netflix. Our solution excels in comparing the site's content to the genuine URL, swiftly identifying such fraudulent attempts to safeguard your digital assets and personal information. Learn more.
- AI-driven analysis: We have an AI-driven solution analyzing the network traffic, structural and textual content of the rendered page. Verdict of the joint model outcome can be seen after 'ML Web Threat Model'.
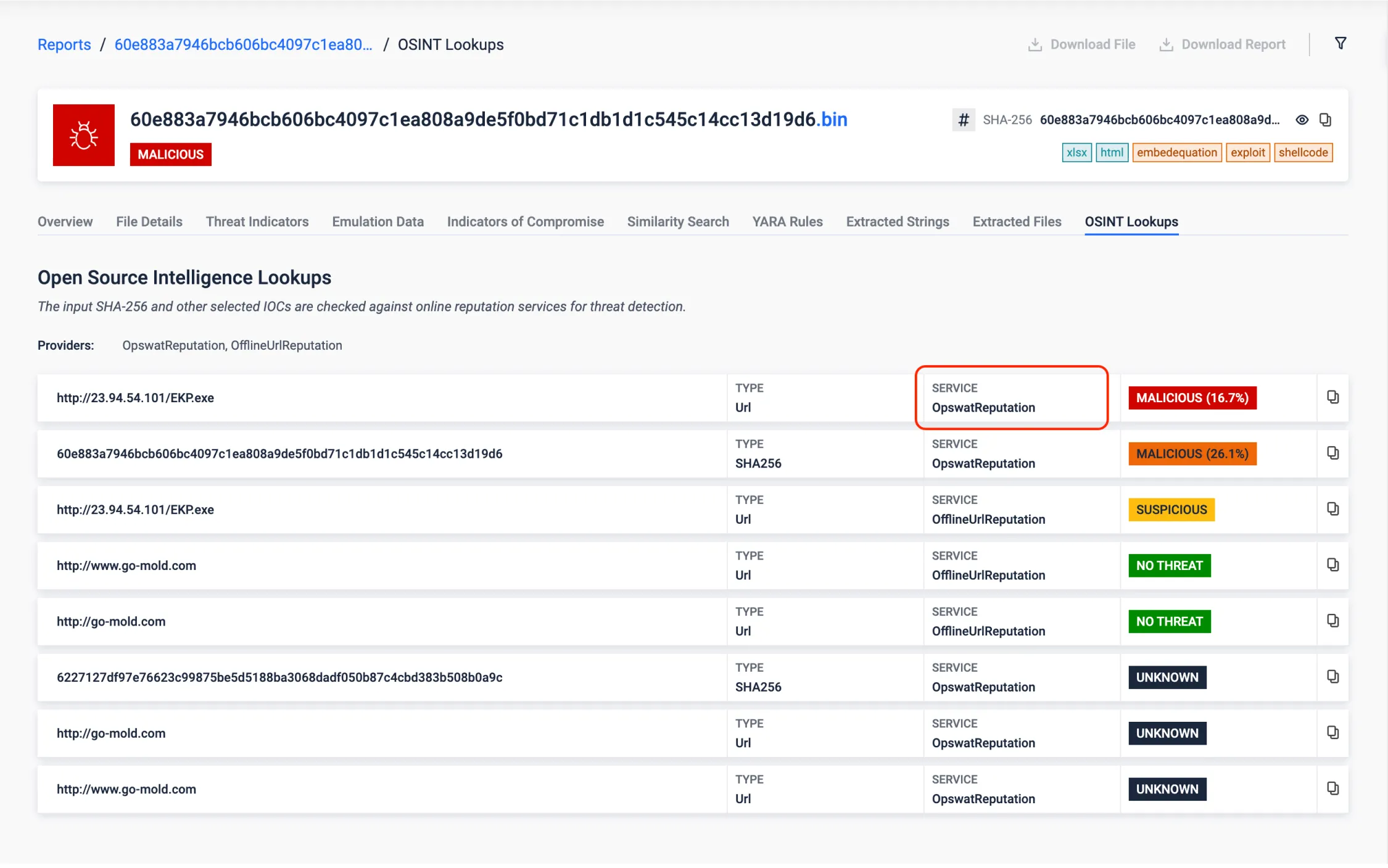
Offline URL Reputation
The offline URL detector ML model provides a new layer of defense by effectively detecting suspicious URLs, offering a robust means to identify and mitigate threats posed by malicious links. It leverages a dataset containing hundreds of thousands of URLs, meticulously labeled as either no threat or malicious by reputable vendors, to assess the feasibility of accurately detecting suspicious URLs through machine learning techniques.
It is important to note that this feature is particularly useful in air-gapped environments where online reputation lookups are not available.
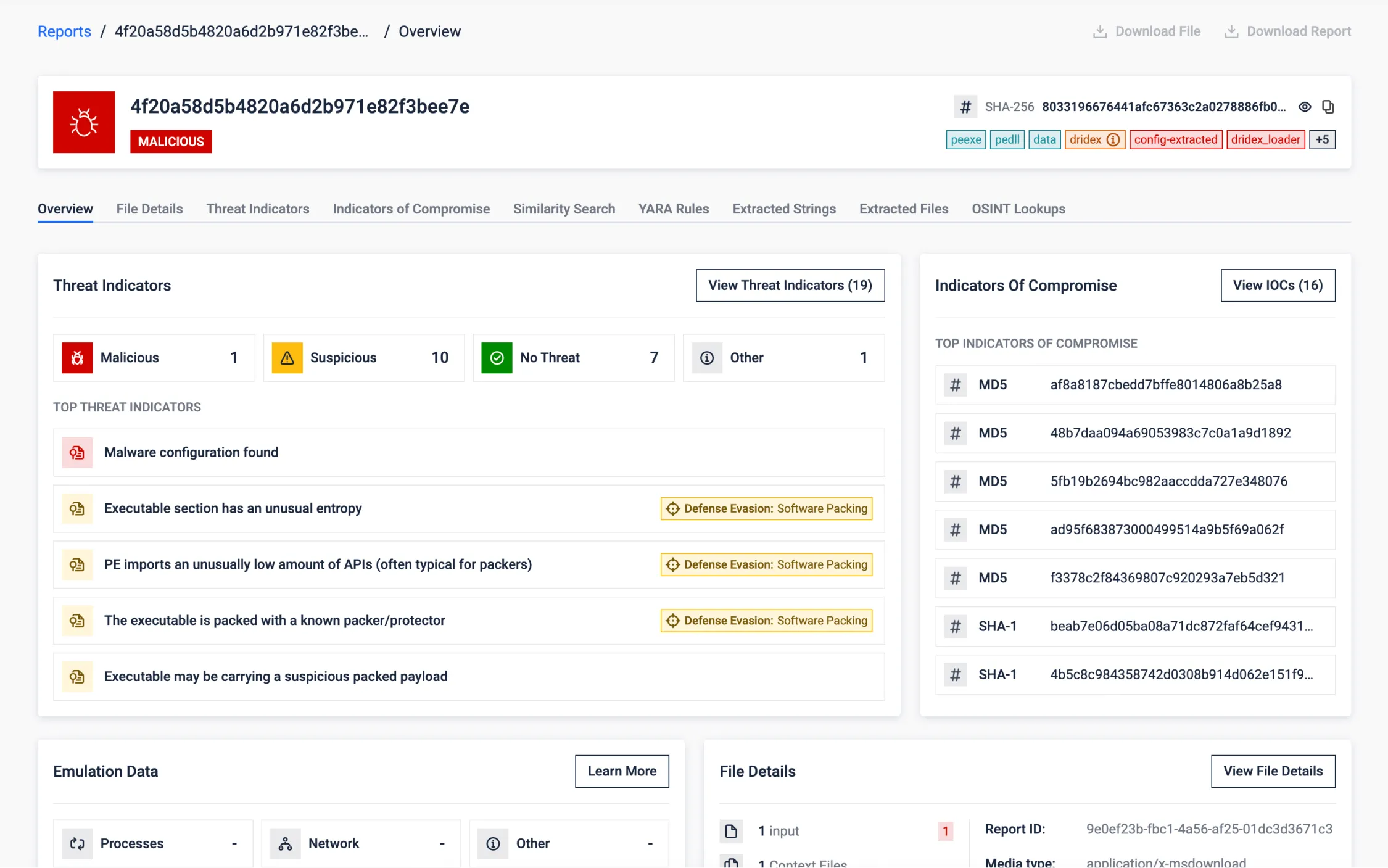
Malware Config Extraction of a Packed Sample
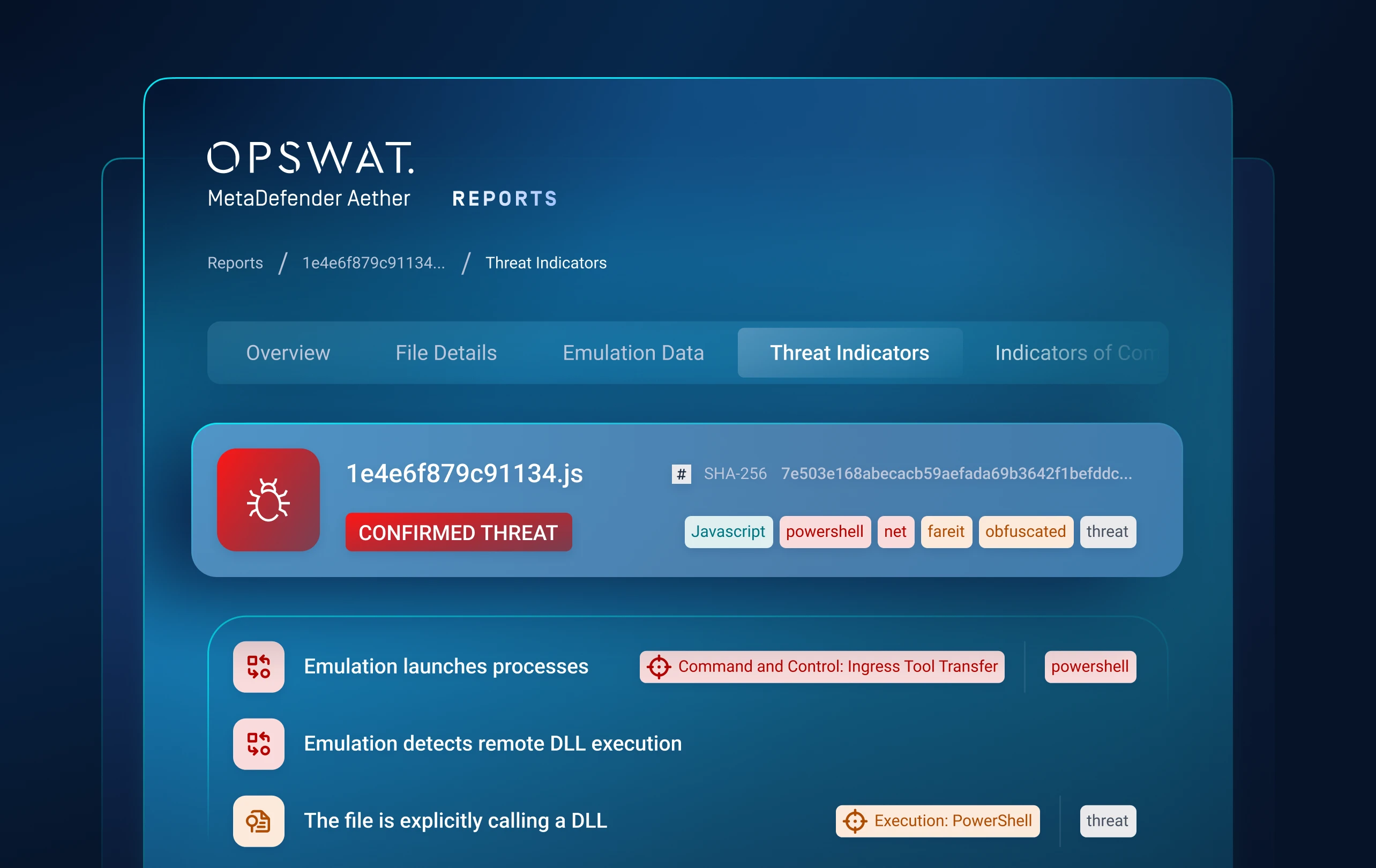
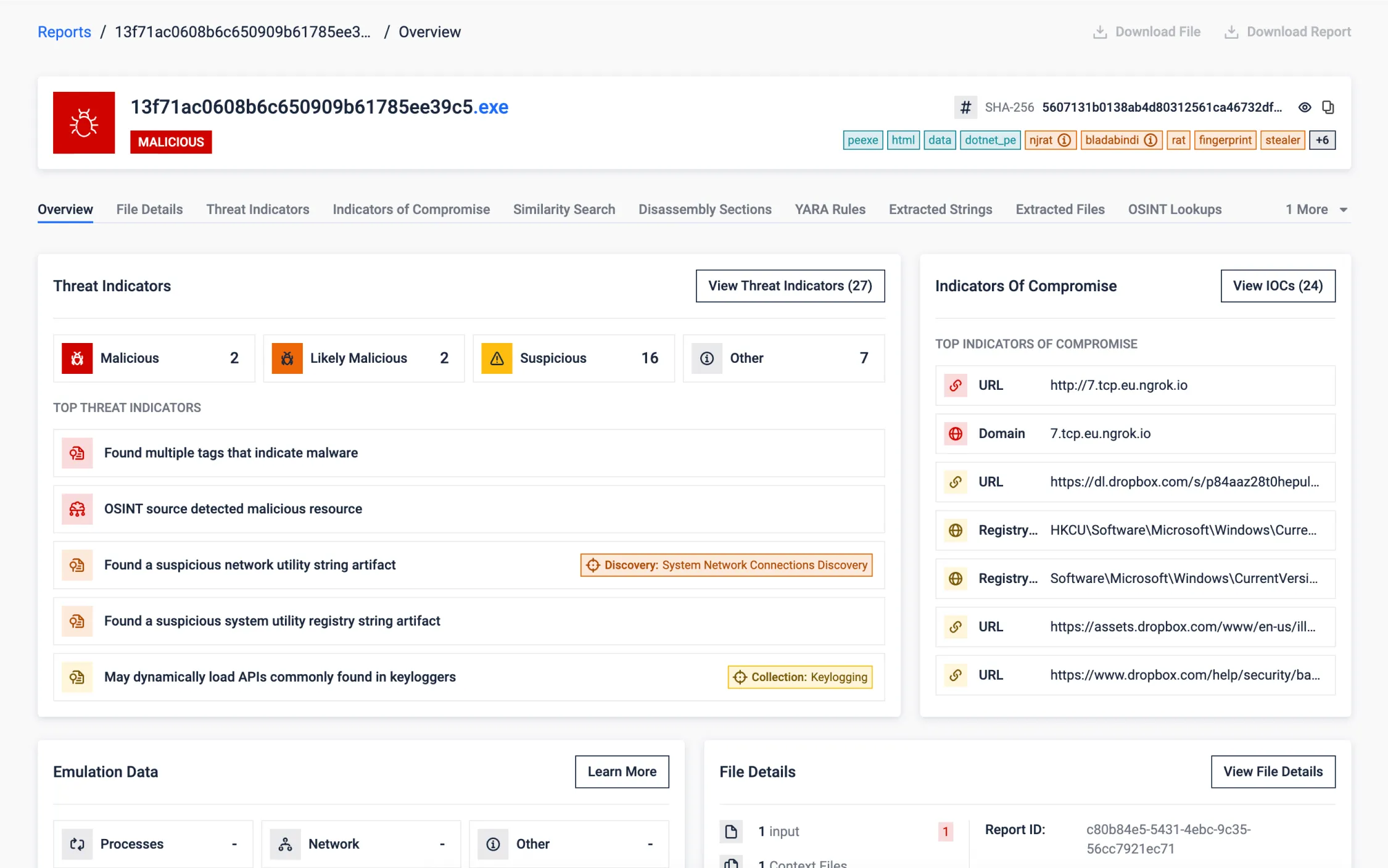
The sample below reveals a malware that was packed using the UPX packing technique. Despite its attempt to evade detection and defenses, our analysis successfully unpacked the payload, exposing its true identity as a Dridex Trojan. We were able to uncover the malware configuration, shedding light on the malicious intent behind this threat, extracting valuable IOCs.
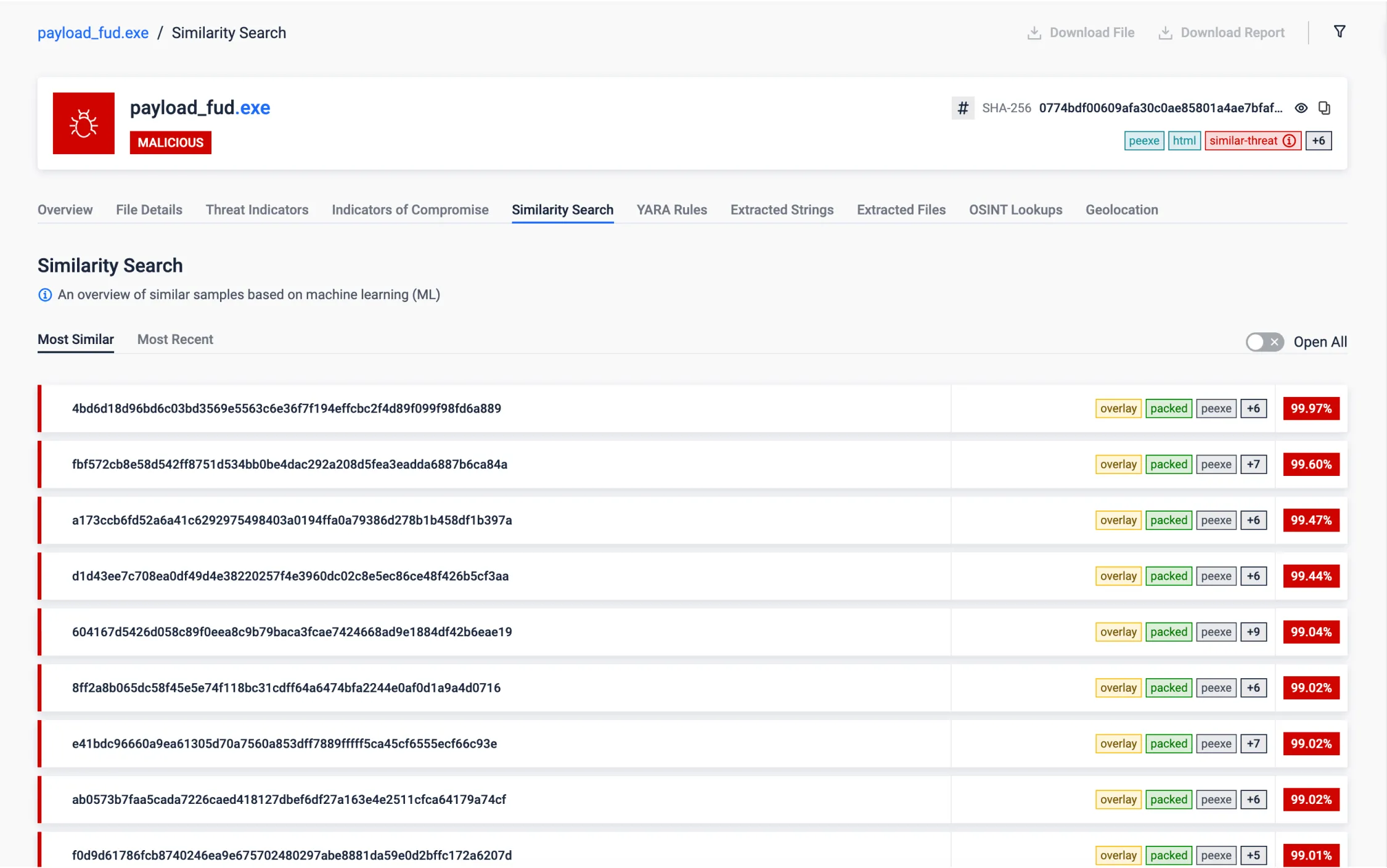
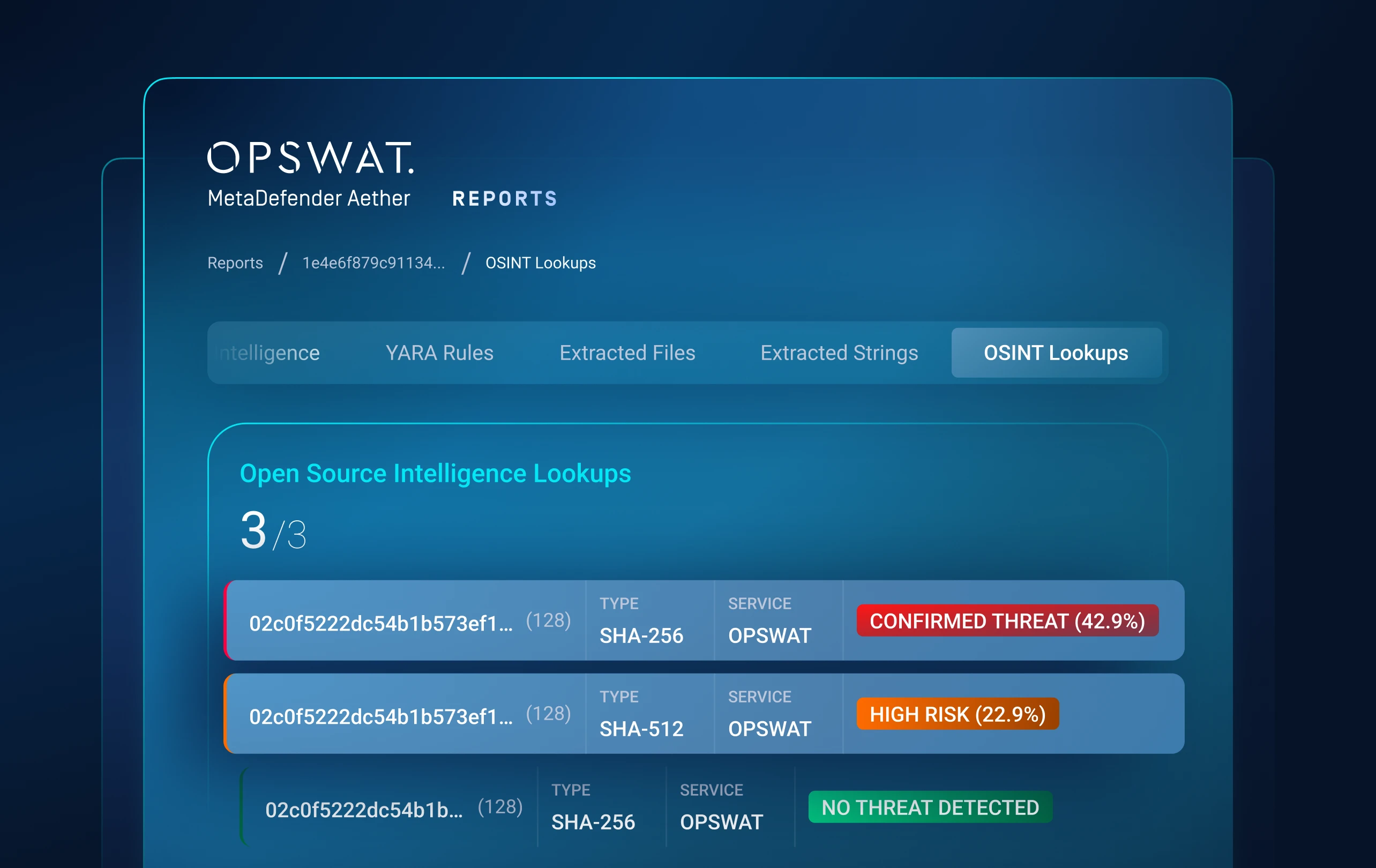
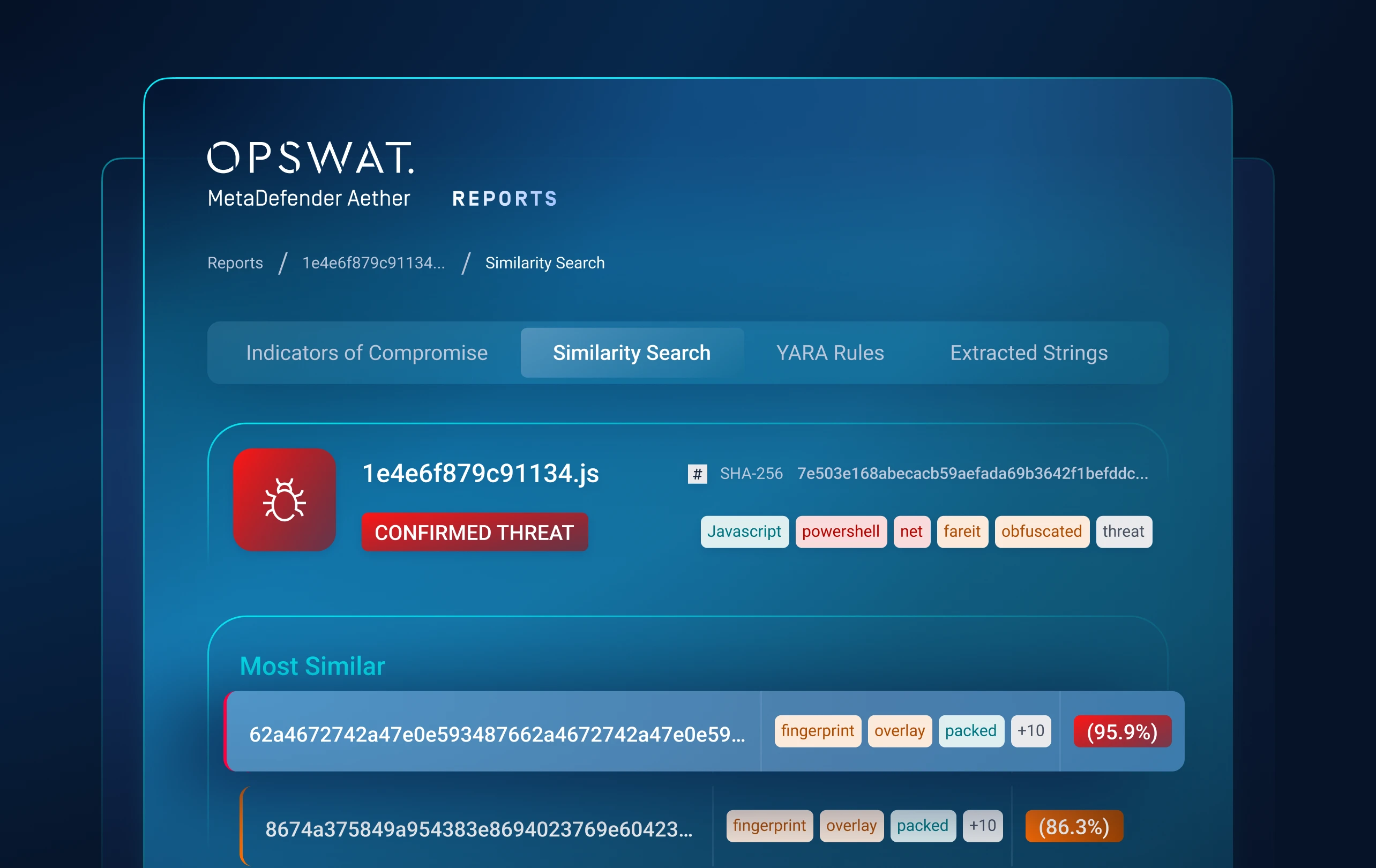
Similarity Search
Employing Similarity Search functionality, sandbox has detected a file remarkably resembling a known malware. Notably, this file had been previously marked as non-malicious, revealing the potential for false negatives in our security assessments. This discovery empowers us to specifically target and rectify these overlooked threats.
It is important to highlight that Similarity Search is highly valuable for threat research and hunting, as it can help uncover samples from the same malware family or campaign, providing additional IOCs or relevant information about specific threat activities.
Native Executable
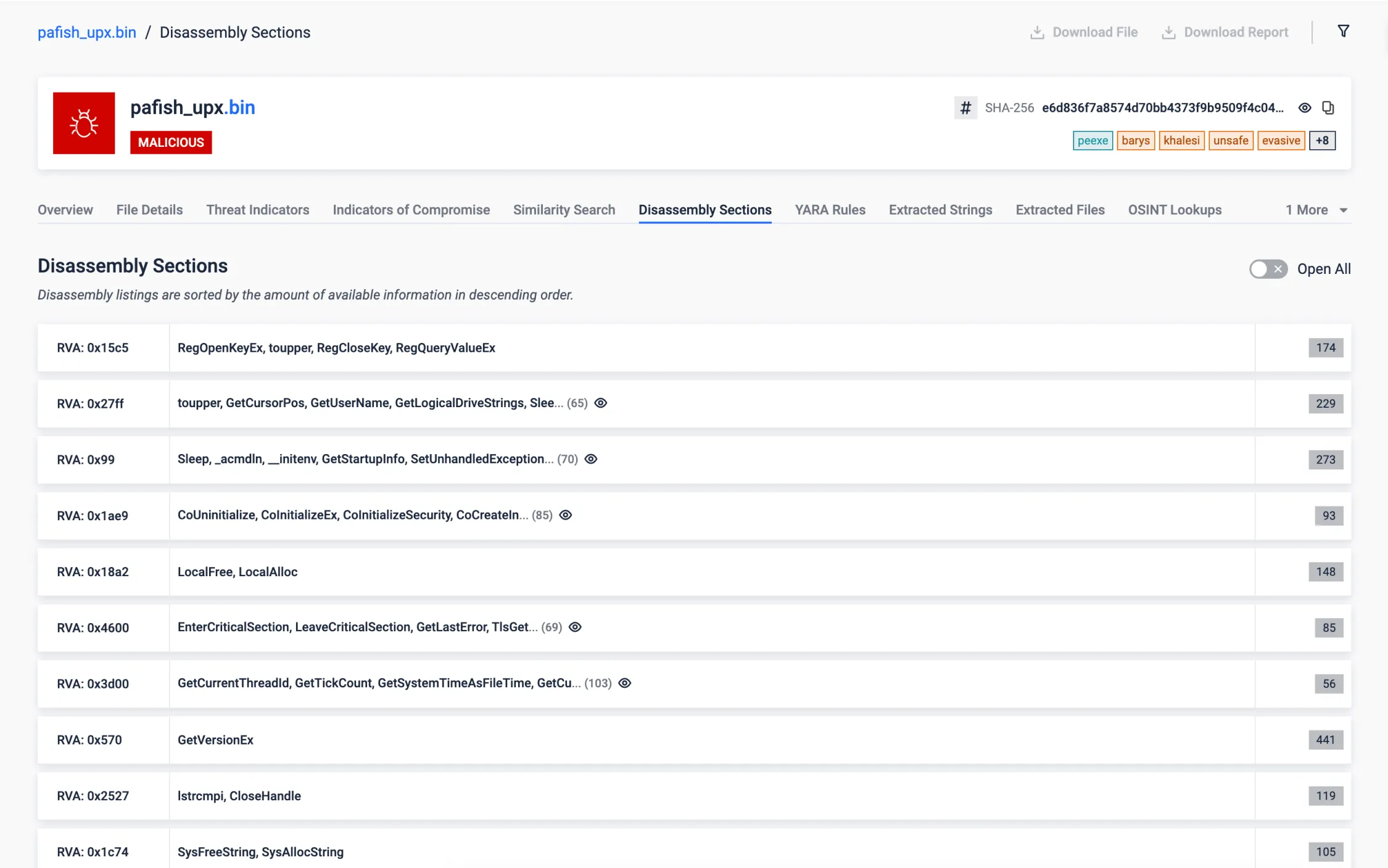
Our disassembling engine revealed intriguing findings within the target sample. Surprisingly, this sample monitors the system time using the uncommon <rdtsc> instruction and accesses an internal, undocumented structure in Windows, commonly used for different malicious tricks. These unusual actions raise questions about its purpose and underscore the need for further investigation to assess potential risks to the system.
.NET Executable
The sample under examination was built using .NET framework. While we refrain from displaying the actual CIL, our decompilation process extracts and presents noteworthy information, including strings, registry artifacts, and API calls.
Besides that, we parse the .NET metadata to identify .NET-specific functions and resources. This process allows to extract detailed information about the assembly, such as methods, classes, and embedded resources, which is critical for analyzing the behavior and structure of .NET applications.
Shellcode Emulation
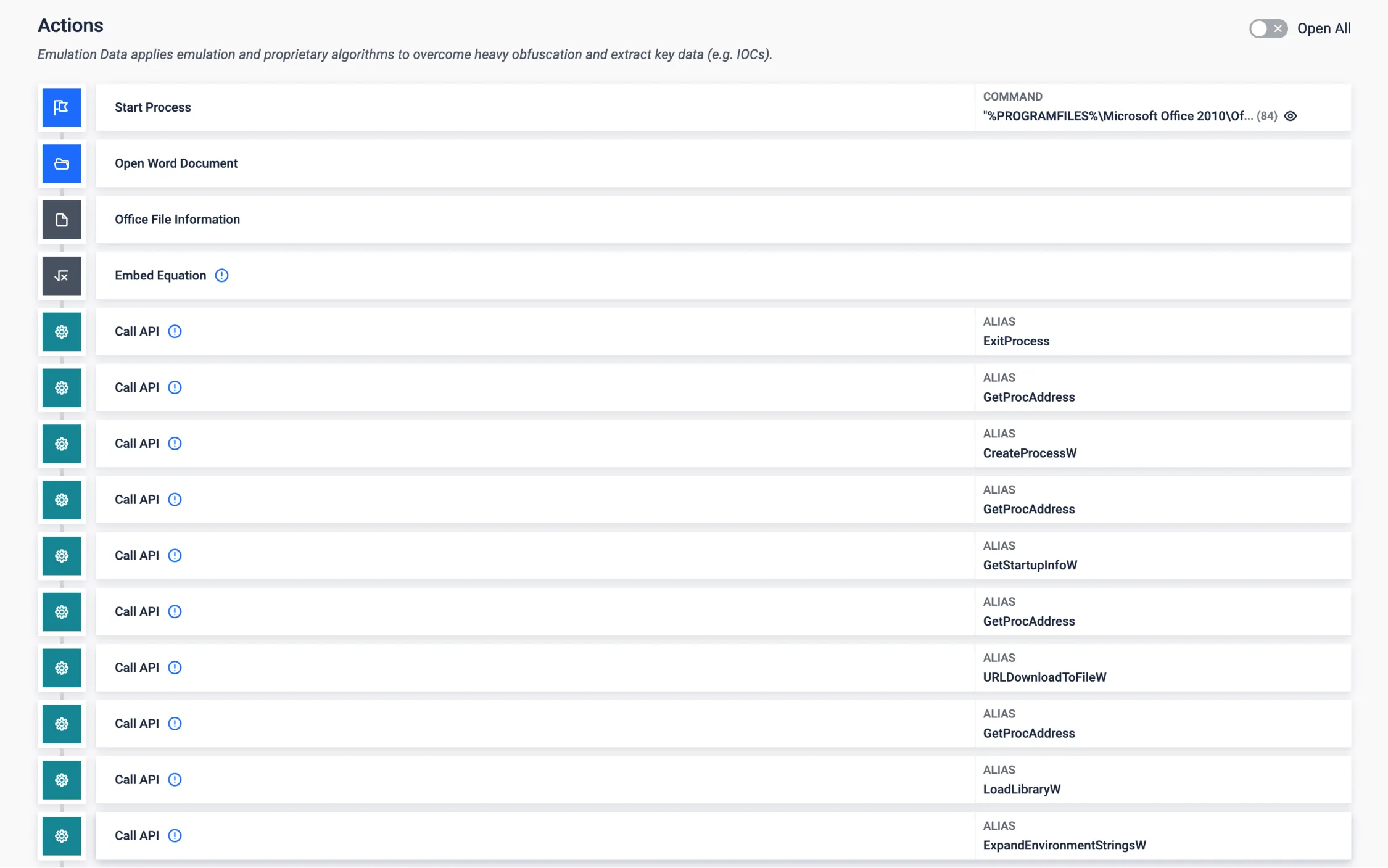
Many application exploits bring their final payload in raw binary format (shellcode), which might be an obstacle when parsing the payload. With our shellcode emulation we are able to discover and analyse the behaviour of the final payload, in this example for a widely leveraged Office vulnerability in the equation editor. Hence opening the door to gathering the relevant IOCs.
Highly Obfuscated VBA Macro
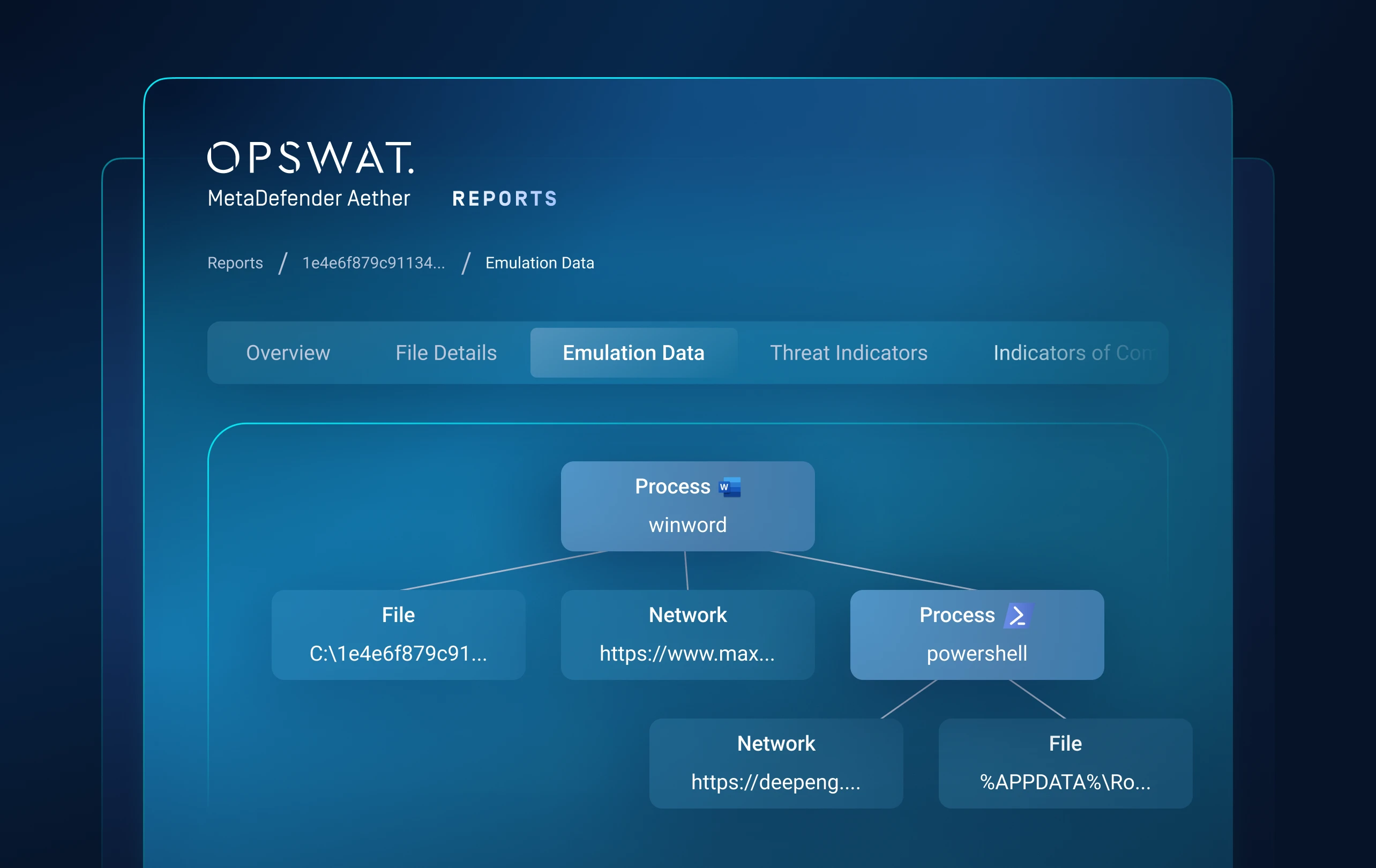
Obfuscated VBA macros present a significant challenge to deliver a reasonable response time of active threats. This unclear code makes the analysis and understanding of threats a high complex task that demands a lot of time and efforts. Our cutting-edge VBA emulation technology is able to overcome these challenges and provides a comprehensive analysis of obfuscated VBA macro together with clear insights into its functionality in seconds.
The analyzed sample is an Excel document with highly obfuscated VBA code that drops and runs a .NET DLL file, together with a LNK file in charge of continuing the malware execution chain. After VBA emulation, MetaDefender Aether identifies launched processes and the main deobfuscating function, automatically extracts obfuscated strings and saves dropped files (previously hardcoded and encrypted in the VBA code). This rapidly show the main purpose of the malware and give us the possibility of a further analysis of this threat.
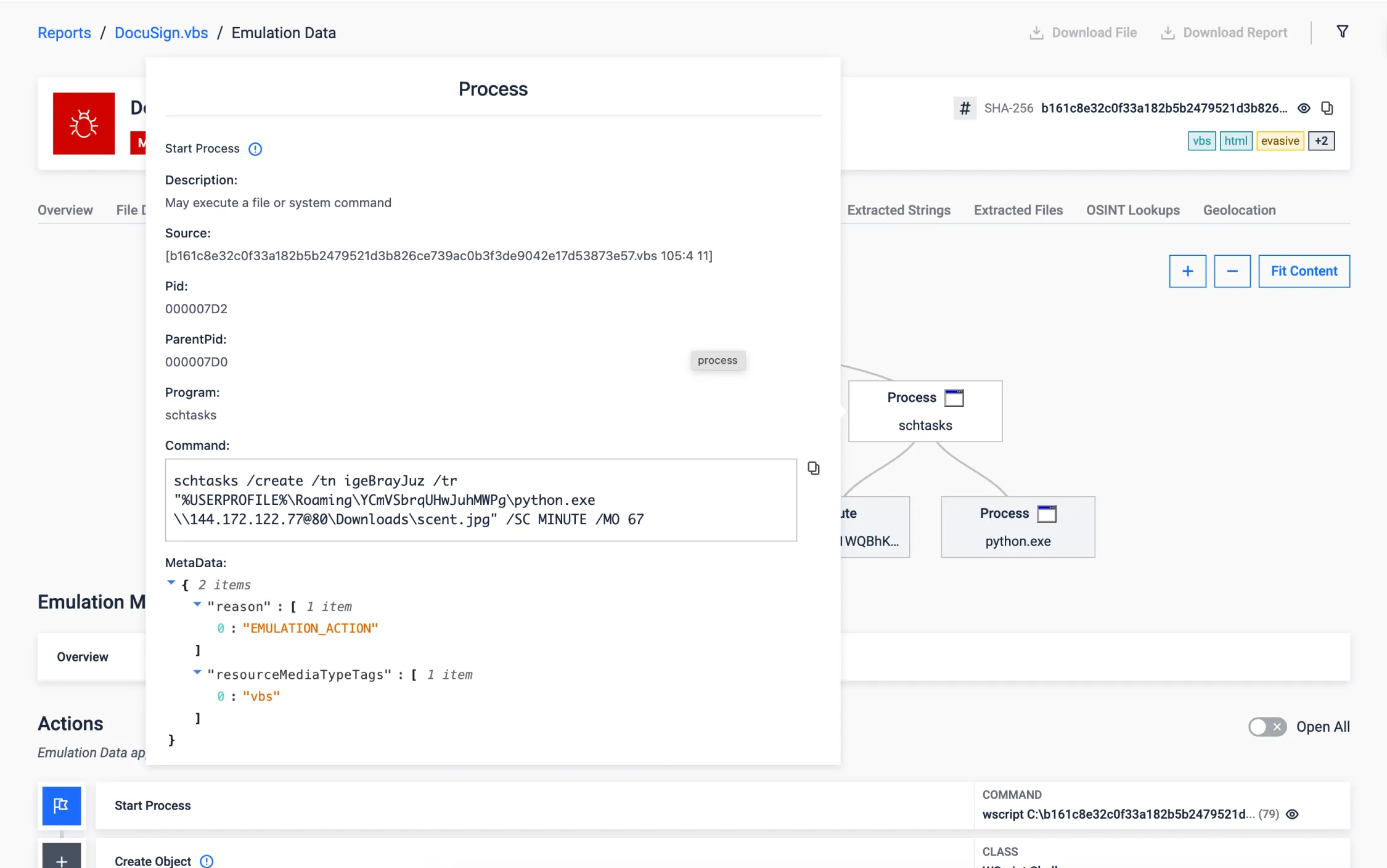
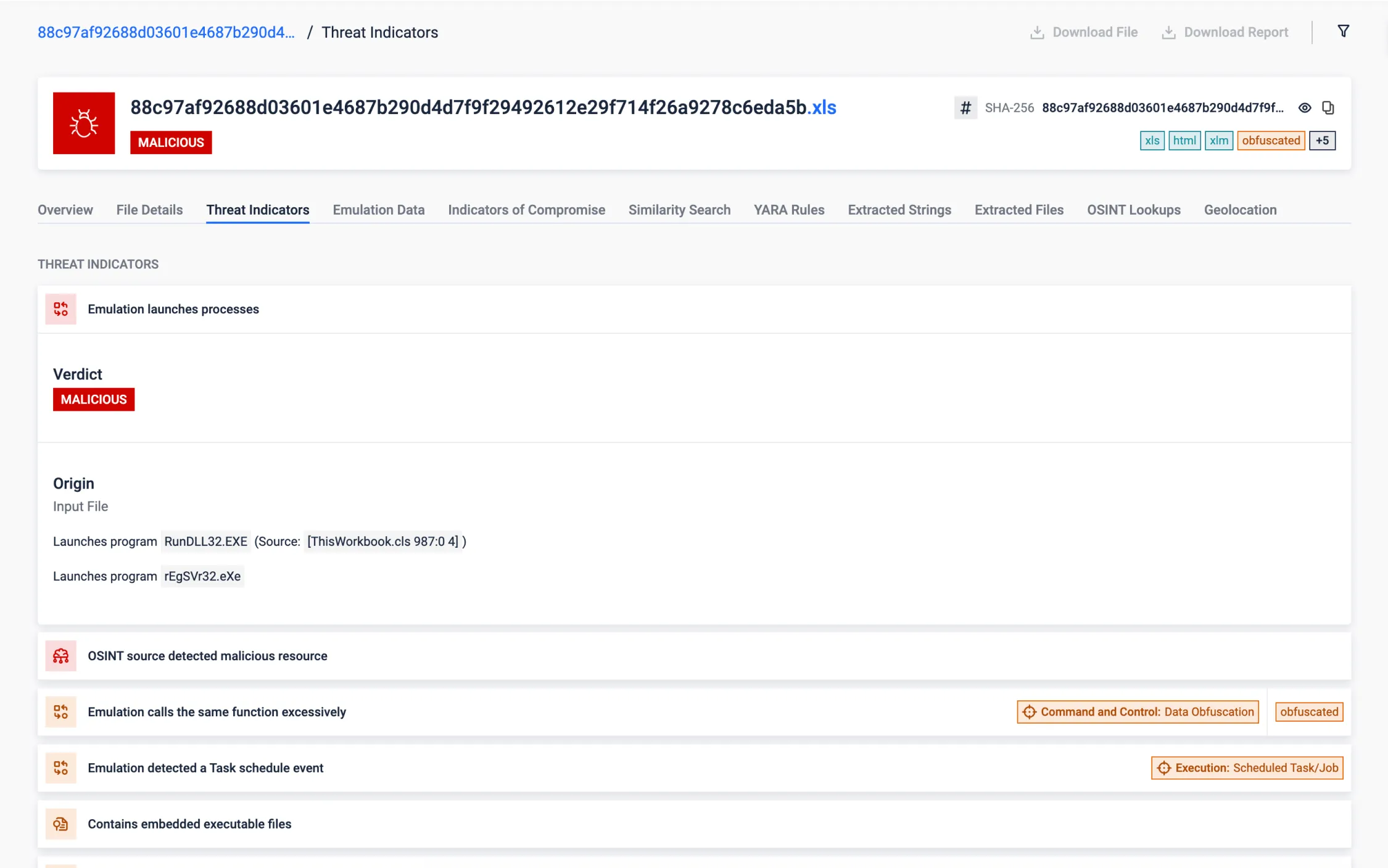
Sandbox Evasion via Task Scheduler
Using Windows Task Scheduler to execute malicious payloads at a later time is a stealthy technique to evade sandbox environments seen in recent threats. It exploits the delay in execution to effectively bypass the short analysis window typical of sandboxes.
The following sample is an obfuscated VBScript that downloads the malicious payload and creates a scheduled task to run it 67 minutes later. Traditional sandboxes maintain the execution for only a few minutes and the malicious behavior would be never exposed. In the other hand, our VBScript emulator is able to detect and overcomes this evasion technique (T1497), adapting the execution environment to continue with further analysis, and getting the full report in 12 seconds.
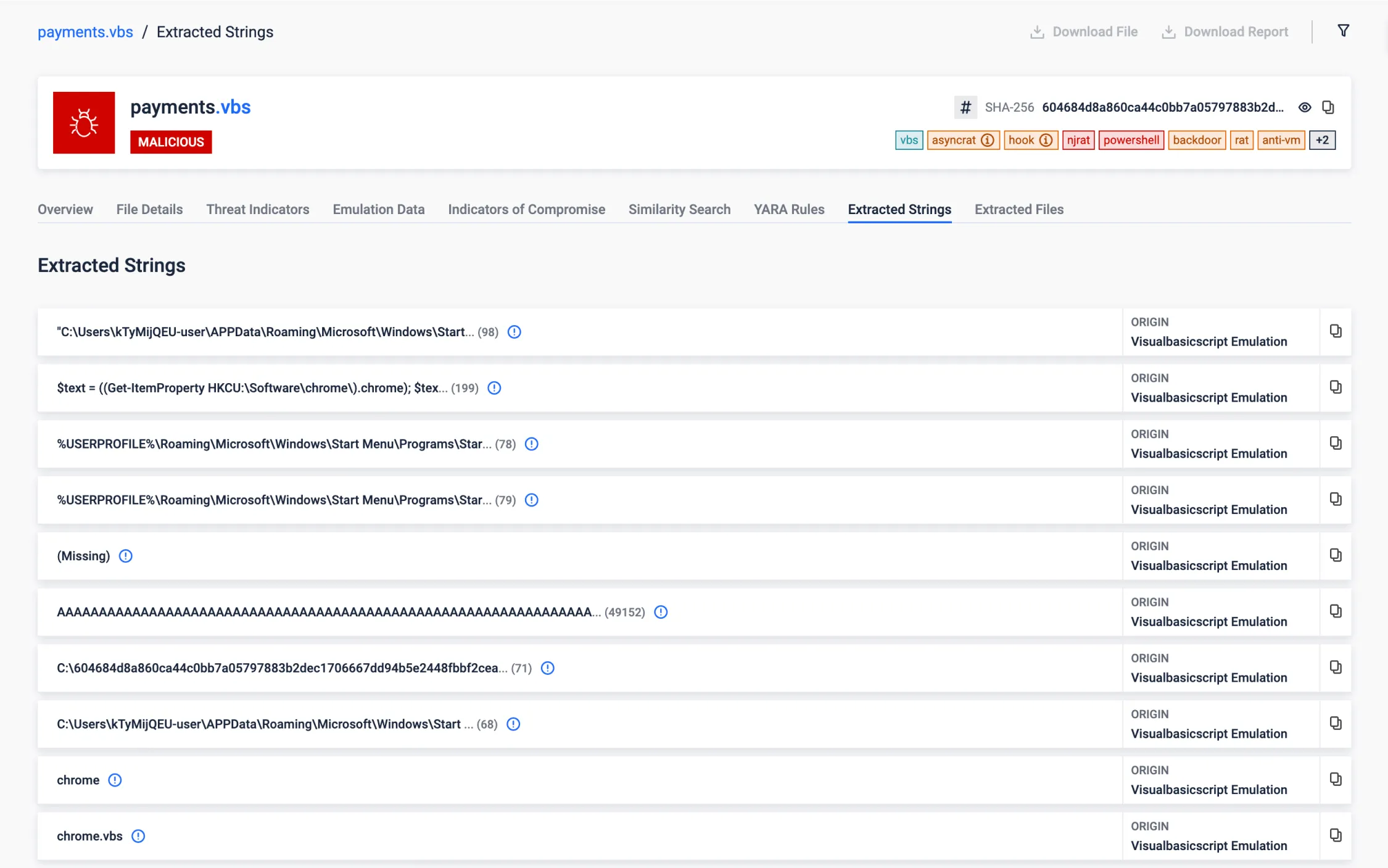
.NET Reflection
NET Reflection is a powerful feature provided by the .NET framework that allows programs to inspect and manipulate a .NET file structure and behavior at runtime. It enables the examination of assemblies, modules, and types, as well as the ability to dynamically create instances of types, invoke methods, and access fields and properties.
Malware can use reflection to dynamically load and execute code from assemblies that are not referenced at compile time, allowing to fetch additional payloads from remote servers (or hidden in the current file) and execute them without writing them to disk, reducing the risk of detection.
In this case, we can see how the analysed VBScript loads and runs a .NET assembly into memory directly from bytes stored in a Windows register.
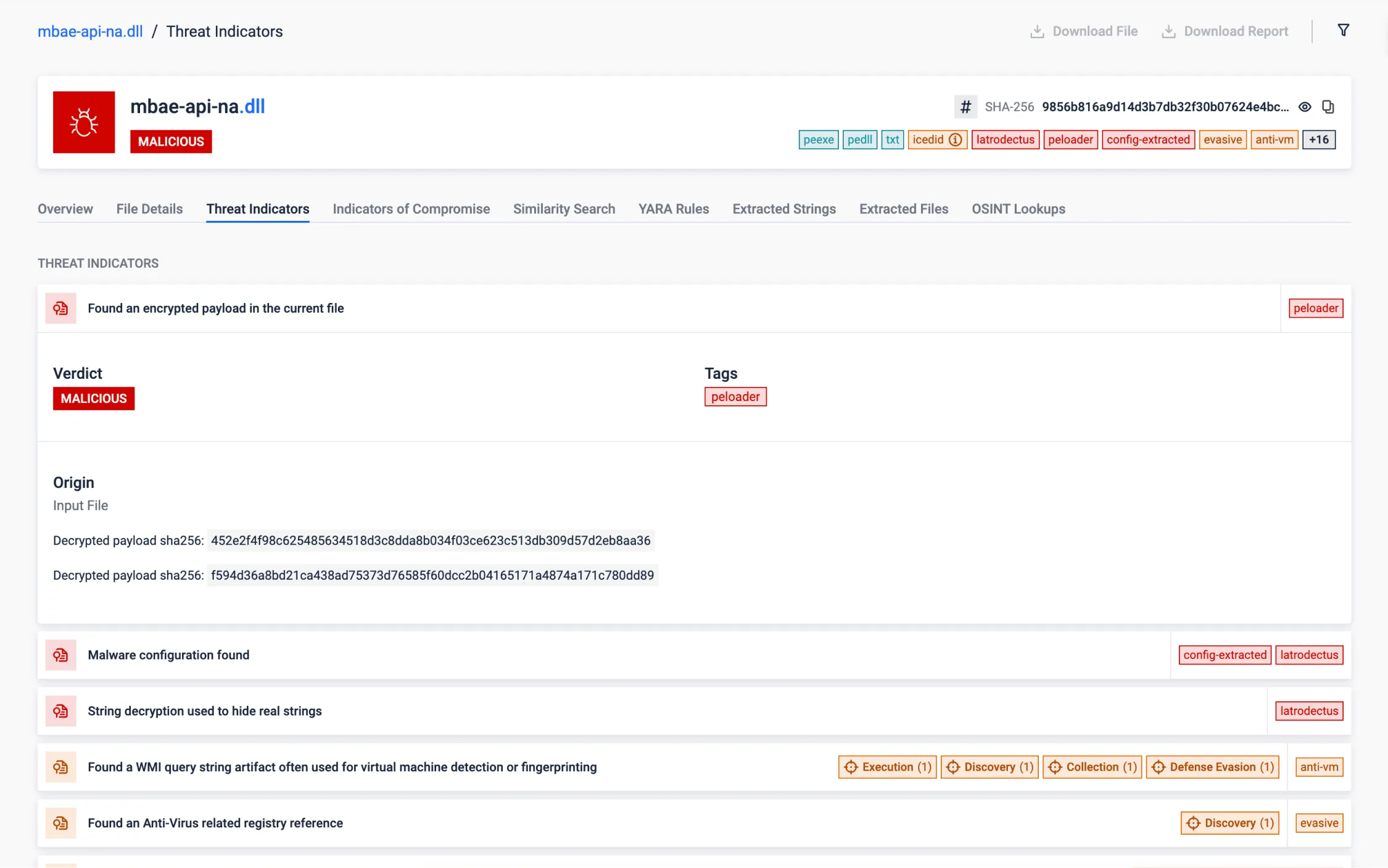
XOR Decrypting Payload Stored in PE Resource
This feature enables to reveal hidden artifacts encrypted within PE resources. Malicious artifacts are often encrypted to evade detection and obscure the true intent of the sample. Uncovering these artifacts is essential, as they typically contain critical data (as C2 information) or payloads. By extracting them, the sandbox can deliver a deeper scan, with higher chance of identifying the most valuable IOCs.
This sample stores that encrypted artifacts using the XOR algorithm, simple but efficient to evade detection. By analyzing patterns in the encrypted data, the encryption key can be guessed, allowing to decrypt the hidden.
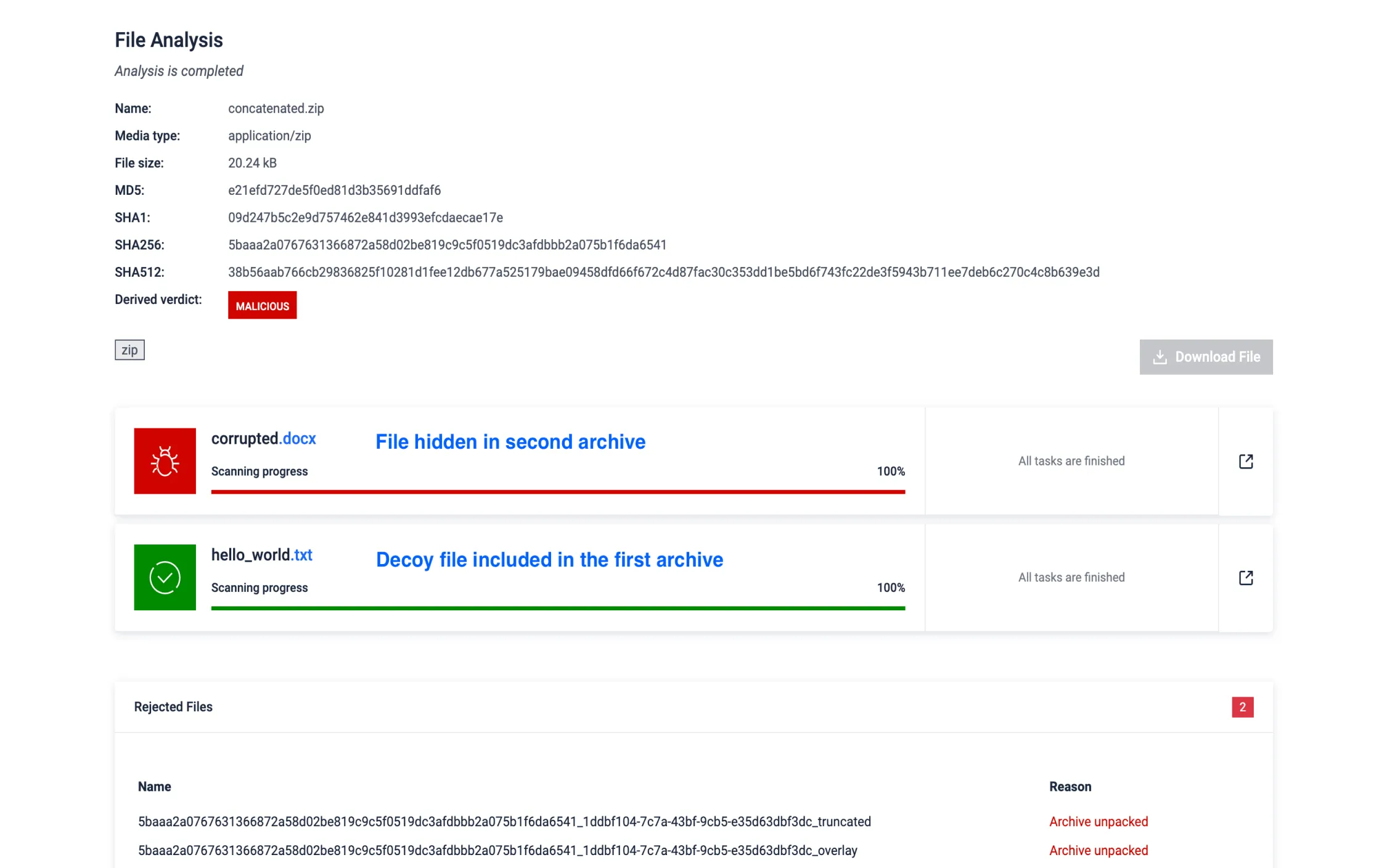
Evasive Archive Concentration
Attackers use archive concatenation to hide malware by appending multiple archives into a single file, exploiting how different tools process them. This technique creates multiple central directories - key structural elements used by archive managers - causing discrepancies during extraction and enabling the bypass of detection for malicious content hidden in overlooked parts of the archive.
MD Sandbox detects and extracts content from all concatenated archives, ensuring no file is missed and effectively neutralizing this evasive technique.
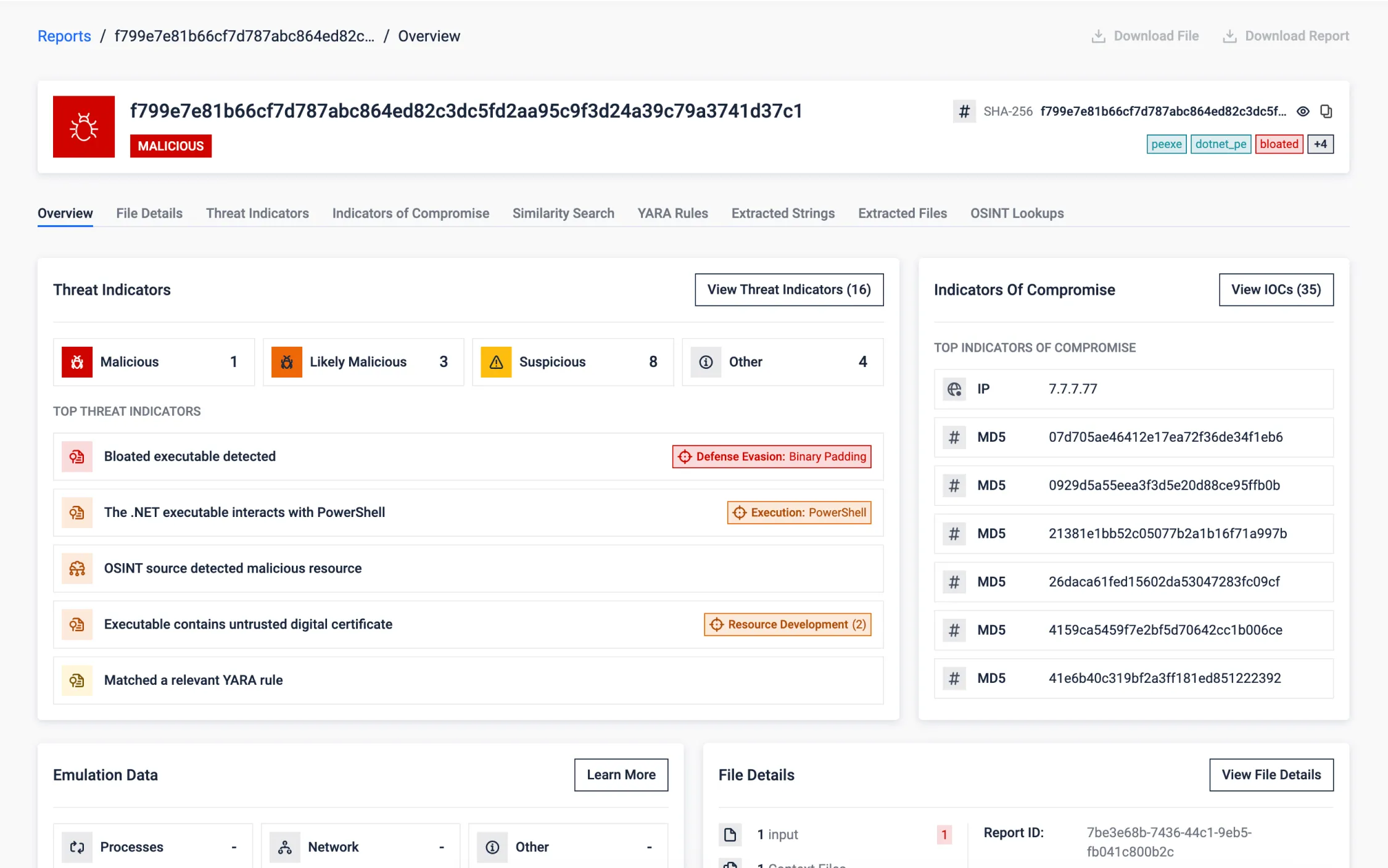
Mitigating Bloated Executables
Threat actors bloat intentionally executables with junk data to evade detection by exploiting resource limitations and analysis time constraints in sandboxes. This evasion technique looks to overwhelm tools or bypass scans by exceeding time limits.
MD sandbox detects bloated executables early, removes junk data, and processes a smaller file for efficient analysis. This debloating process targets various methods, including junk in overlays, PE sections, and certificates, ensuring accurate detection while conserving original resources.
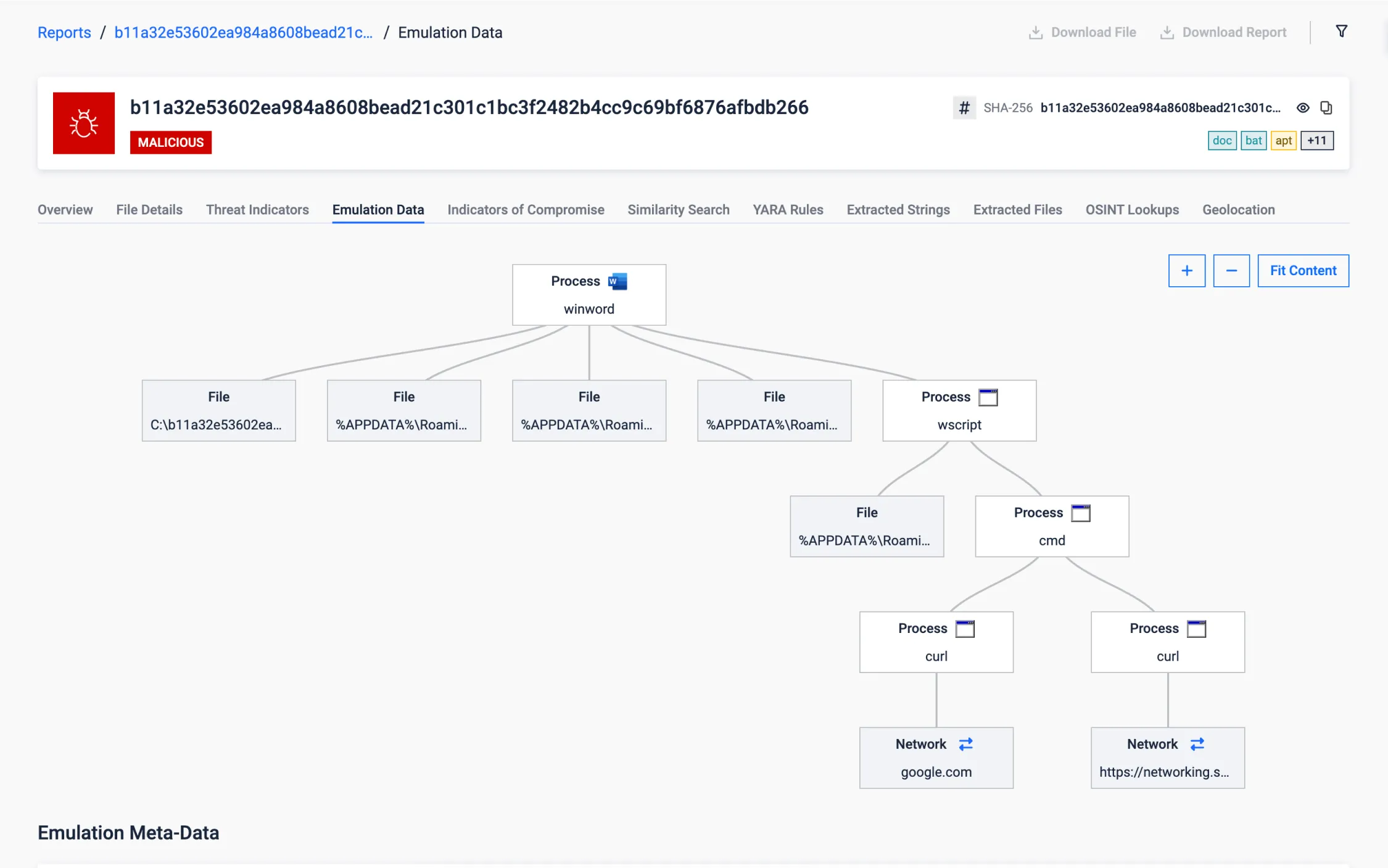
Document Targeting Critical Infrastructures
This Office document targets critical infrastructure in Iran (with content in Persian) to steal sensitive information, such as credentials and documents, and periodically takes screenshots, potentially for espionage purposes.
After establishing persistence, it performs a stealthy initial internet connectivity check (against a trusted domain like google.com) to ensure a reliable connection, delaying further actions until network conditions allow the attack to proceed. This is a tactic commonly observed in attacks on critical infrastructure, environments where internet access may be intermittent or restricted.
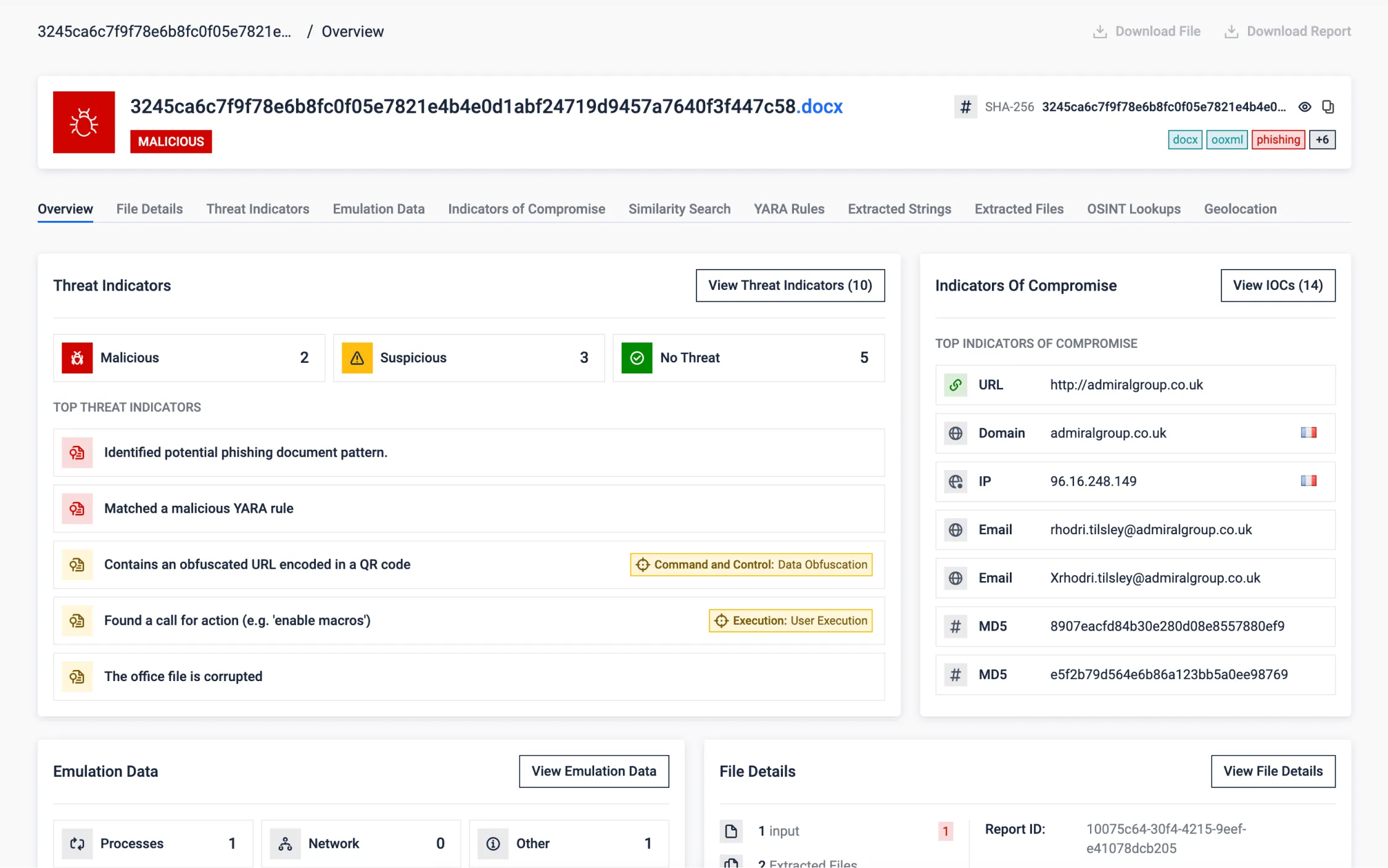
Evasion Through Corrupted OOXML (Office) Documents
Researchers discovered intentionally corrupted OOXML documents (modern office documents). By modifying the binary content near the internal file headers, the purposely broken files may be misdetected as ZIP files by automatic scans which will attempt to extract compressed files.
Document viewers will automatically repair the document upon opening. At this point, despite the document containing phishing content, it may have effectively bypassed defenses. Automated analysis will not be able to read its content and therefore miss the relevant indicators.
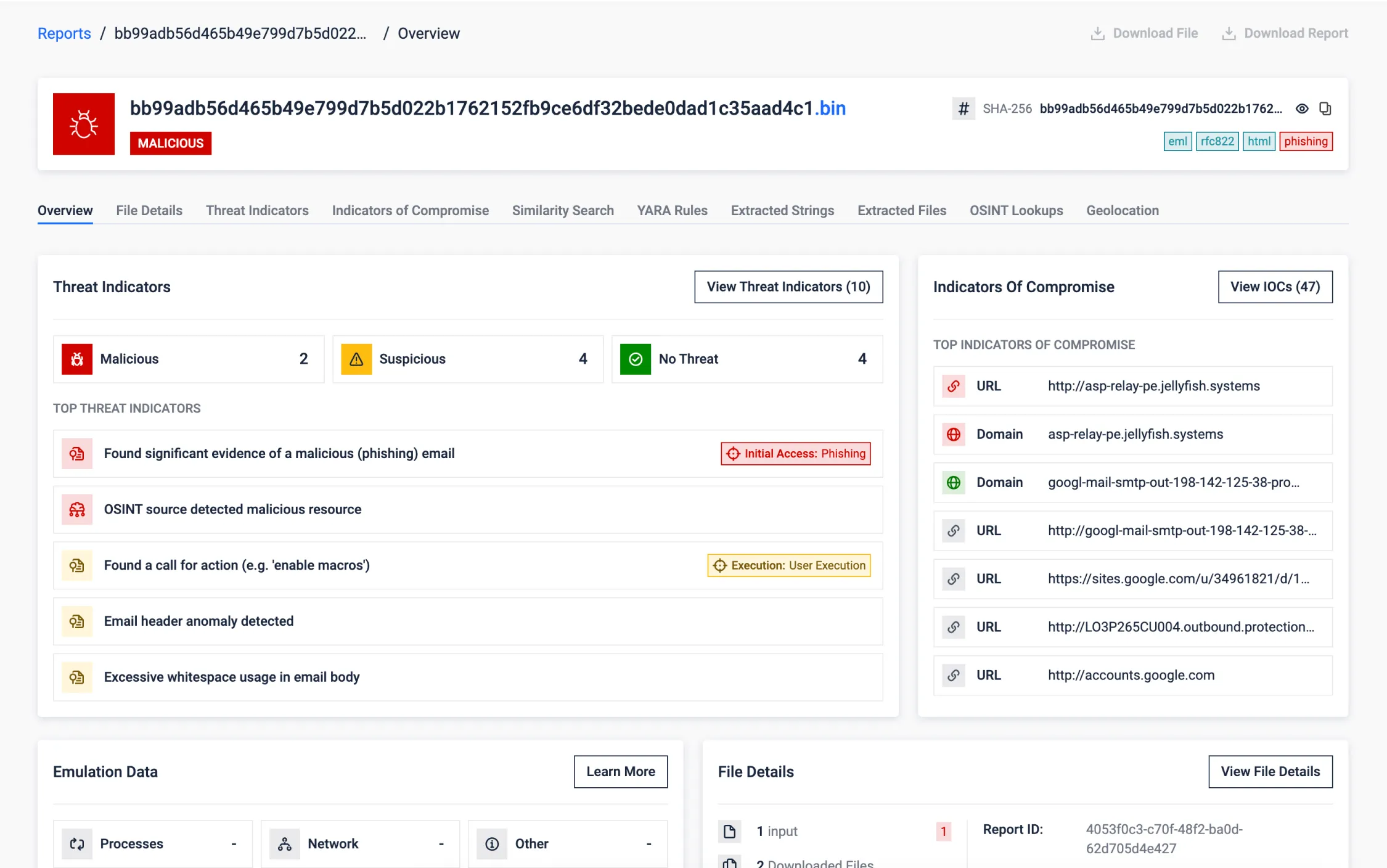
Google DKIM Replay Attack Detection
Email authentication mechanisms like SPF, DKIM, and DMARC are essential, but sophisticated attackers can sometimes bypass them. This example showcases a scenario where an email, despite being authentically signed by Google and passing standard checks, was identified as malicious by MetaDefender Aether.
MetaDefender Aether detected several anomalies along with other indicators:
- DKIM Boundary Violation: Identified content added beyond the scope of the DKIM signature.
- Obfuscation Techniques: Detected excessive whitespace used to hide malicious intent.
- Phishing Patterns: Recognized urgent calls-to-action characteristic of phishing attempts.
- Header Analysis: Flagged anomalies in email headers associated with OAuth application abuse.
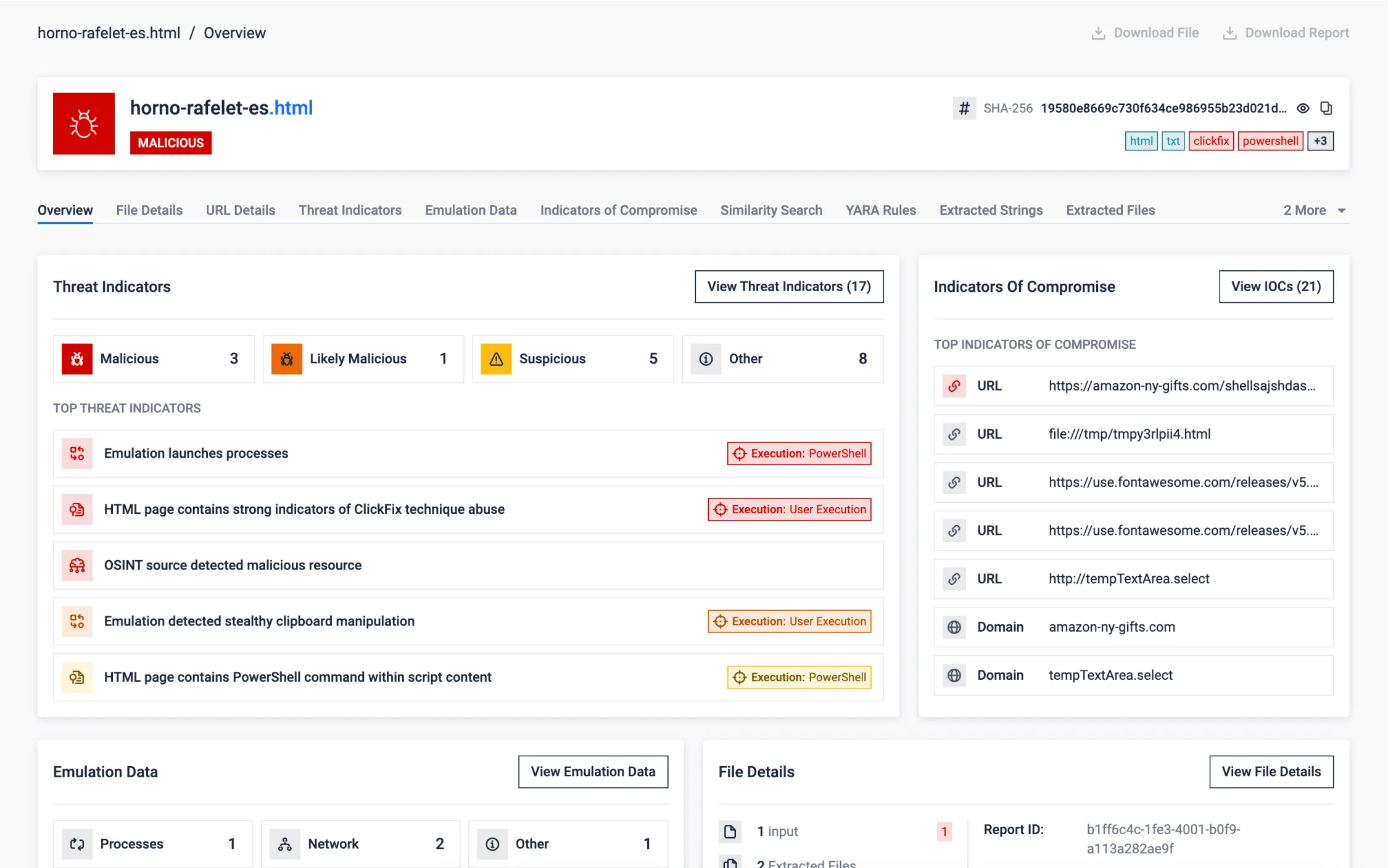
ClickFix, a Trending Social Engineering Technique
ClickFix is an emerging web-based threat that leverages social engineering to silently trick users into executing malicious commands. Unlike traditional phishing, ClickFix operates through deceptive UX elements and clipboard manipulation rather than file downloads or credential theft.
The ClickFix website presents a fake reCAPTCHA or "bot protection" screen to appear legitimate. The user is then asked to verify themselves—often through a harmless-looking interaction—while, in the background, obfuscated JavaScript code silently runs. This script dynamically decodes a malicious command and copies it directly to the system clipboard. Next, the user is presented with misleading instructions and guide to execute the malware, unaware of the danger.
ClickFix highlights how simple web techniques, combined with user deception, can effectively bypass traditional security layers—making sandbox analysis critical for uncovering stealthy, low-footprint attacks like this one.
MetaDefender Aether analyses this threat end-to-end. The sandbox begins by rendering the malicious URL and applying phishing detection models to identify suspicious content. It then extracts and emulates the JavaScript, simulating user actions to reach the critical moment when the clipboard is modified. Once the hidden command is captured, it is emulated, allowing the sandbox to fully trace the malicious execution flow. This not only exposes the clipboard-based tactic but also reveals the payload’s behavior and infection chain.
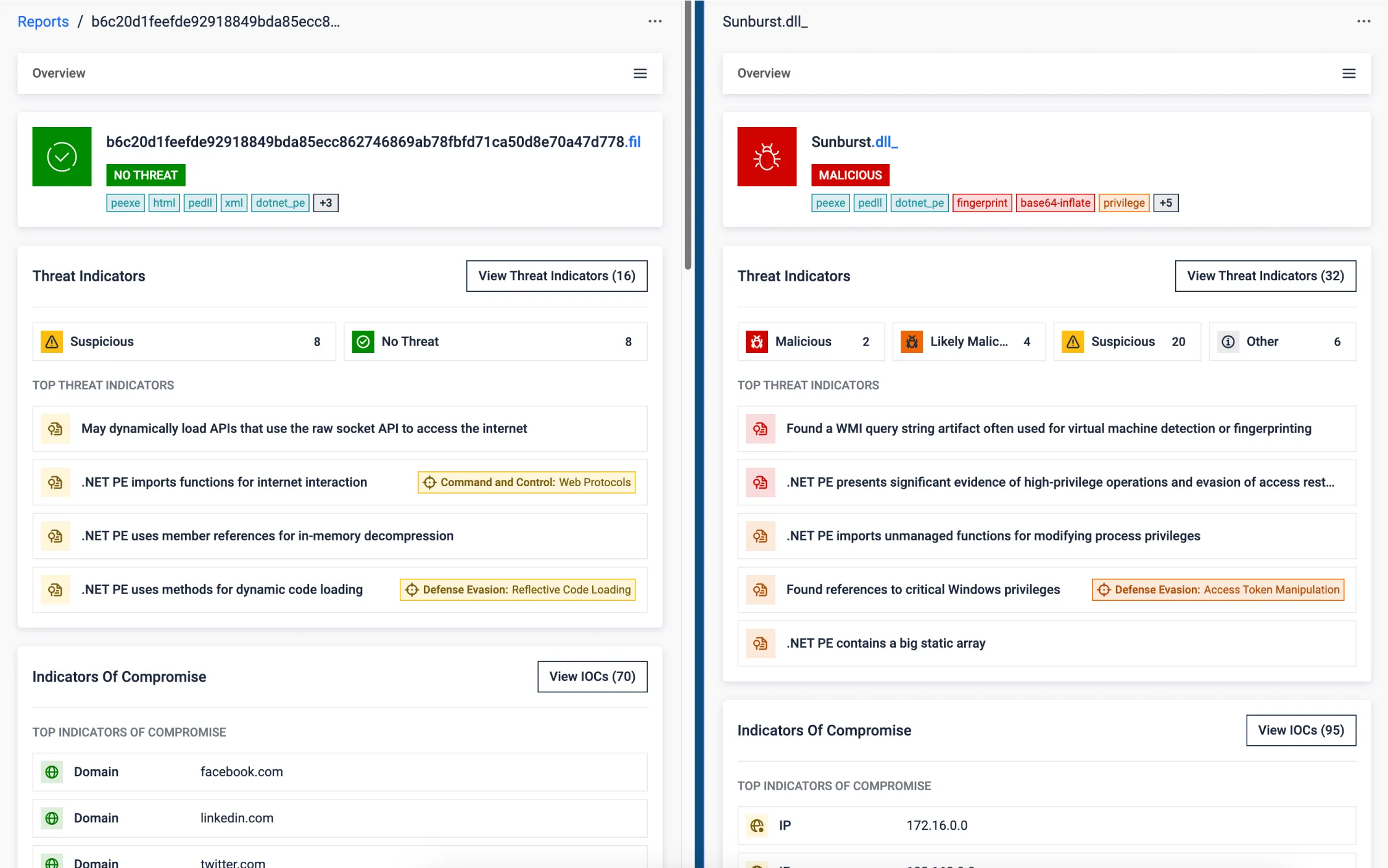
Supply Chain Attack
The SolarWinds supply chain attack exemplifies how minimal code changes in trusted software can enable massive breaches while bypassing traditional security defenses. Threat actors injected a stealthy backdoor into a legitimate DLL, embedding malicious logic while preserving original functionality. The payload ran silently in a parallel thread mimicking legitimate components. With a valid digital signature and seamless behavior, the DLL evaded detection and granted covert access to thousands of high-profile victims. The compromise of the build pipeline turned trusted updates into a vehicle for global intrusion.
While a 4,000-line backdoor might seem significant, in the context of a large enterprise source code, it’s easily overlooked. This is where MetaDefender Aether excels: it doesn’t just inspect the code, it observes what the software does. It flags deviations from normal behavior, guiding analysts to what really matters—cutting through the noise to spotlight threats that traditional reviews would likely miss.
Detonator - The Endless Quest
for Zero-Day Detection
The Story Behind OPSWAT’s Industry-Leading Dynamic Analysis Technology
Trusted Globally to Defend What's Critical
OPSWAT is trusted by over 1,900 organizations worldwide to protect their critical data, assets, and networks from
device and file-borne threats.
FileScan.io Community
Uncover hidden threats with insightful malware analysis
powered by OPSWAT’s MetaDefender Aether
technology—try it free.
Support Compliance
with Regulatory Requirements
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are
implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure.
Get Started in 3 Simple Steps
Recommended Resources

MetaDefender Aether for Core

SANS Detection & Response Survey

2025 OPSWAT Threat Landscape Report
FAQs
Aether is the unified zero-day detection solution combining - emulation sandboxing + threat reputation + ML similarity search + rich Threat Intelligence - in a single, analyst-friendly UI/API.
It uses CPU-level emulation (not fingerprintable VMs) to force malware to execute its real logic, unpack memory-only payloads, and expose evasions (sleep loops, geofencing, .NET loaders, steganography) at speed and scale.
Aether builds on the same emulation-based sandboxing engine used in Adaptive Sandbox but extends it with intelligence correlation, automated enrichment, and threat hunting.
- Sandbox = analysis engine.
- Aether = full Zero-Day Detection solution built around that engine.
Aether uses CPU-level emulation instead of full virtual machines. This means seconds instead of minutes per analysis, with higher throughput, stronger evasion resistance, and easier scalability across deployments.
Clear verdict + threat score, live behaviors and MITRE mapping, unpacked payloads/configs, network/C2 indicators, and exportable IOCs (MISP/STIX) ready for blocking and hunts-plus ML similarity to cluster related campaigns.
Deploy it on-prem (including fully air-gapped), in your cloud, or consume via API. It's ops-light: decoupled detection updates ship continuously, and you can integrate with SSO (SAML 2.0) and your ticketing/SOAR.
Point a pilot at a real workflow (e.g., email attachments or inbound MFT files) and mirror suspicious traffic to Aether for 2-4 weeks; measure new detections, triage time saved, and IOC yield to build the ROI case.































