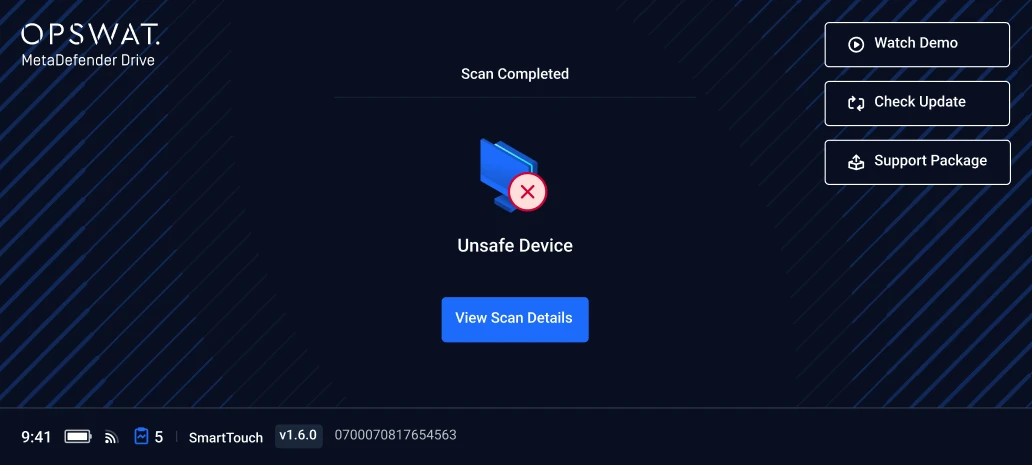
Portable Malware and Compliance Scanning
Scan laptops, desktops, and servers before they power on or are received, even in air-gapped environments
- Pre and Post Boot Threat Scanning
- Scan with 7 Anti-Malware Engines
- Country of Origin Compliance





2,000+
Portable Malware Scanning for All Devices
TAA & FIPS 140-2
17 Offices Worldwide
#1 Market Leader
3 Category Winner

What We’re Up Against

Zero-Day & Boot Sector Viruses
Traditional antivirus solutions often miss deeply embedded threats such as rootkits or malware hidden in the MBR (Master Boot Record) or partition boot sector. MetaDefender Drive scans at the hardware level to detect and neutralize these threats.


Transient Device Protection
Perform comprehensive bare metal scans at the hardware level to detect and neutralize threats, ensuring that all transient devices are secure and safe to use.


Compliance Requirements
Meeting strict cybersecurity mandates, such as ISO/IEC 27001 and NIST SP 800-53, can be challenging. MetaDefender Drive helps organizations comply with these regulations by assessing the security of devices before they are introduced into secure environments.


Cross-Platform Compatibility
In OT and critical infrastructure, many devices run on outdated or legacy operating systems, alongside newer IT assets. The aging systems could not support modern endpoint security, leaving critical assets exposed. MetaDefender Drive scan the most recent and legacy devices across all major operating systems to close this gap and ensure network integrity.


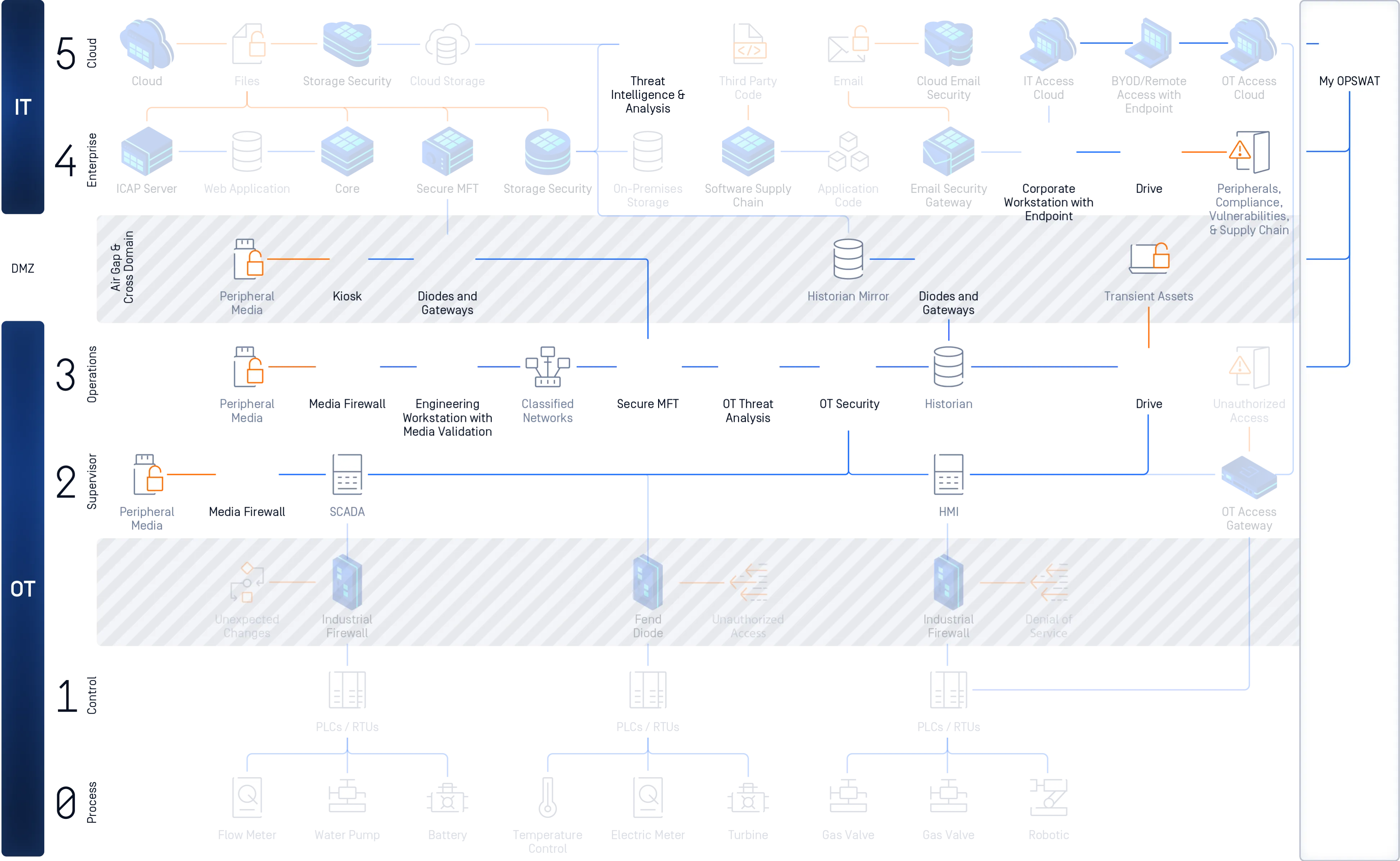
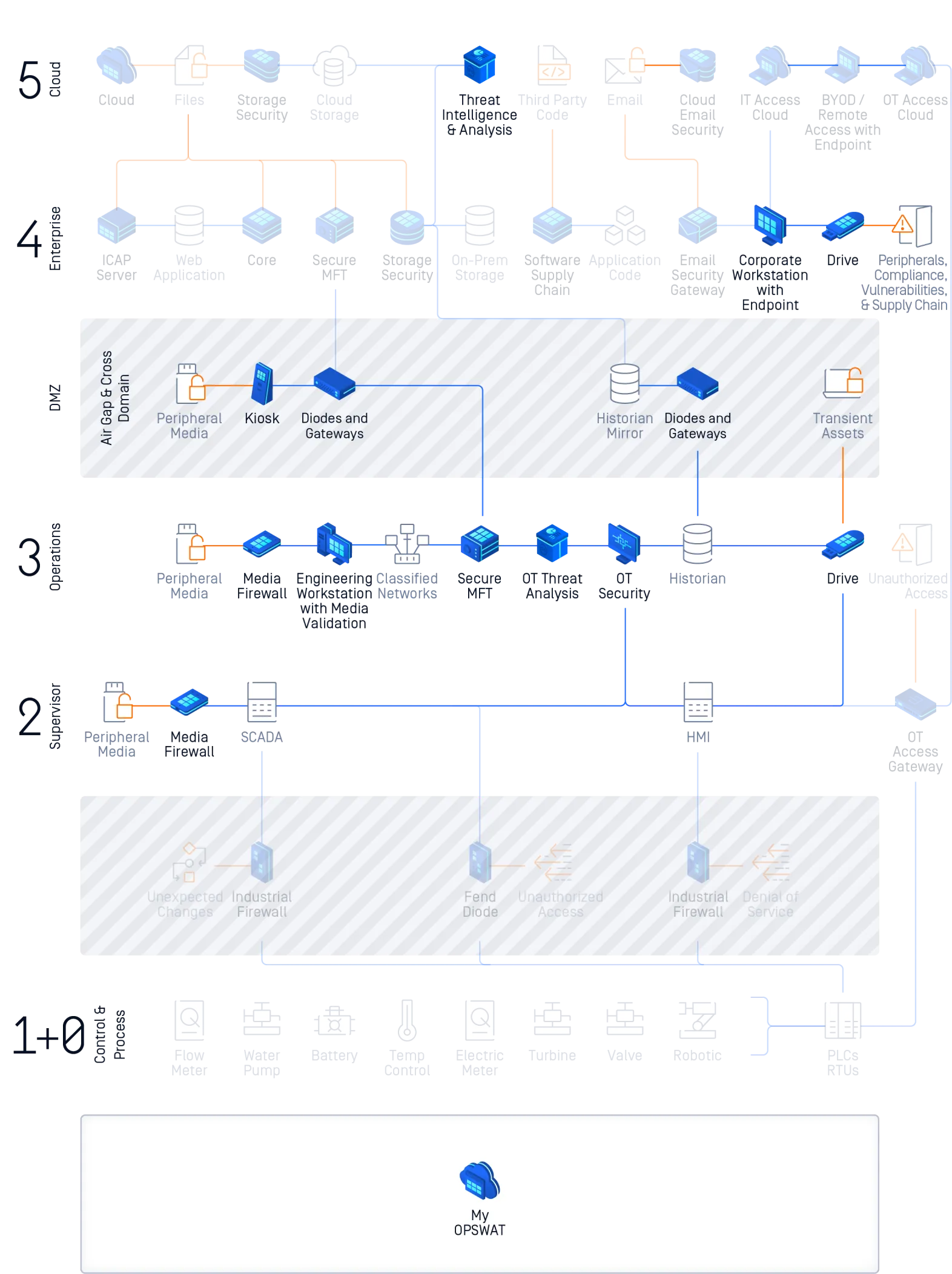
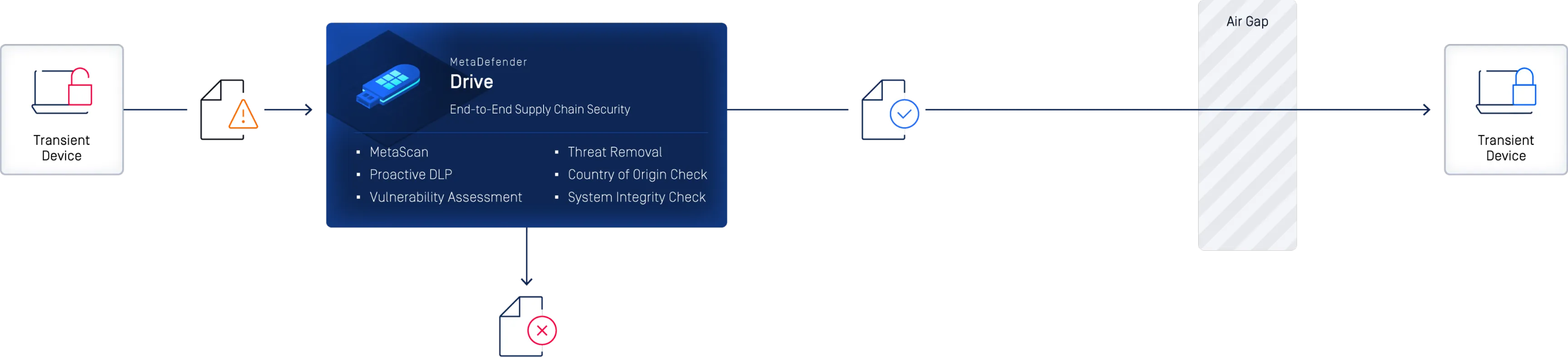
End-to-End Portable Malware Scanning
The risks associated with vendor and contractor devices connecting to critical networks require rigorous inspection. MetaDefender Drive scans laptops, desktops, and servers before power-on — even in air-gapped environments — to ensure every device entering your environment is safe from tampering, infection, or hidden threats.
End-to-End Portable Malware Scanning
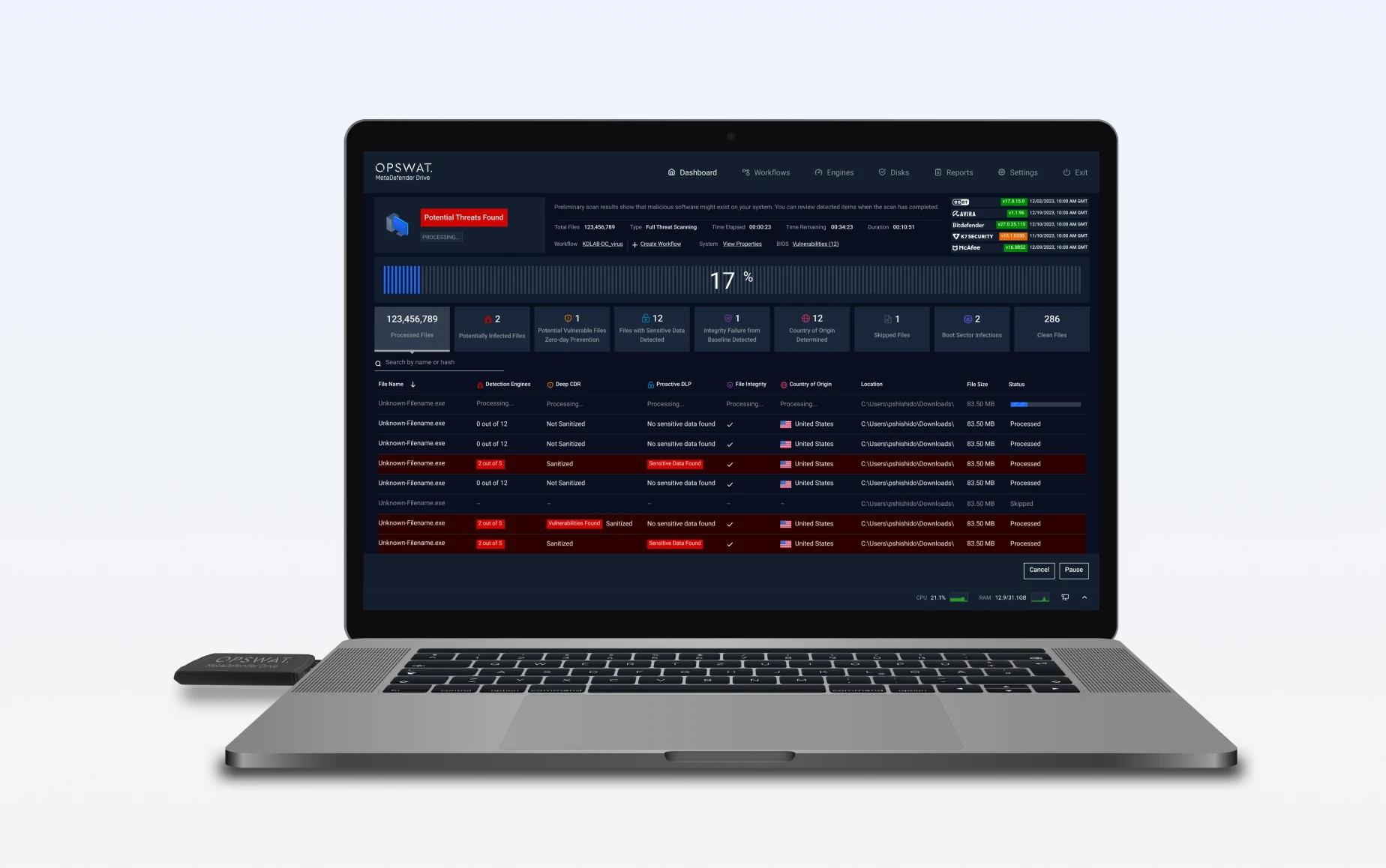
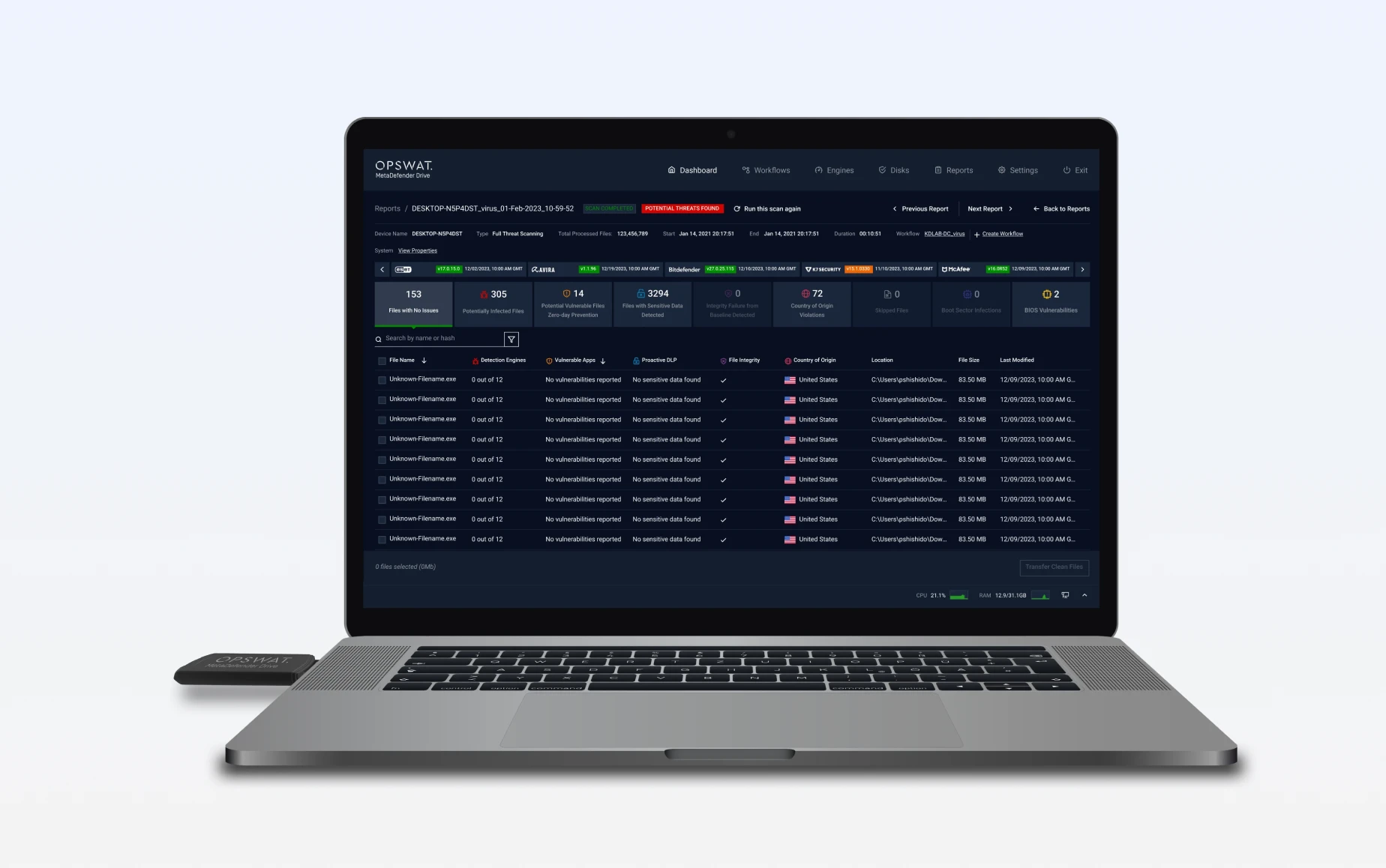
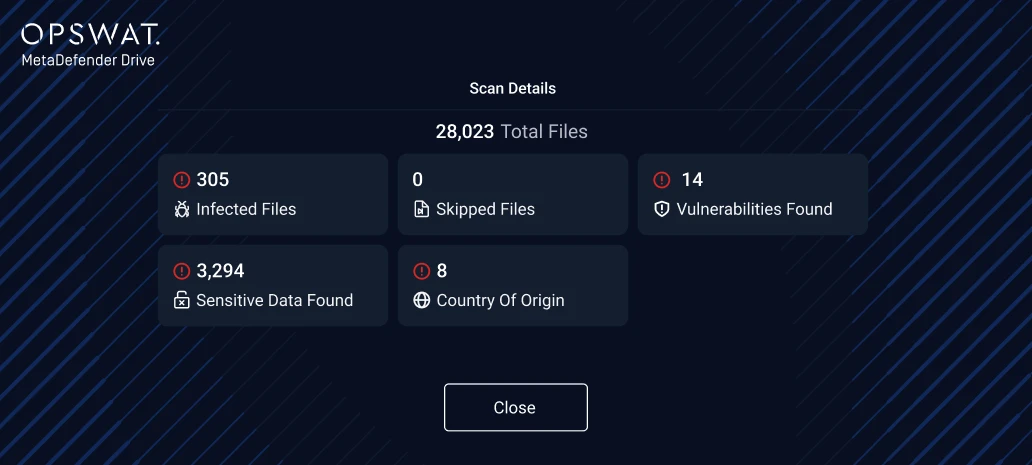
MetaDefender Drive secure boots from a built-in OS, independent of the device's primary operating system. It performs an offline, bare-metal scan, targeting the device's hardware components, including the Master Boot Record and partition sectors, to detect and remove malicious code. Scan reports instantly show threats, vulnerabilities, and system risks, providing immediate security feedback and highlighting what needs remediation.
MetaDefender Drive
and Stationary Devices
MetaDefender Drive with Smart Touch
Touch of a Finger
What Solution is Right for You?
MetaDefender Drive 2
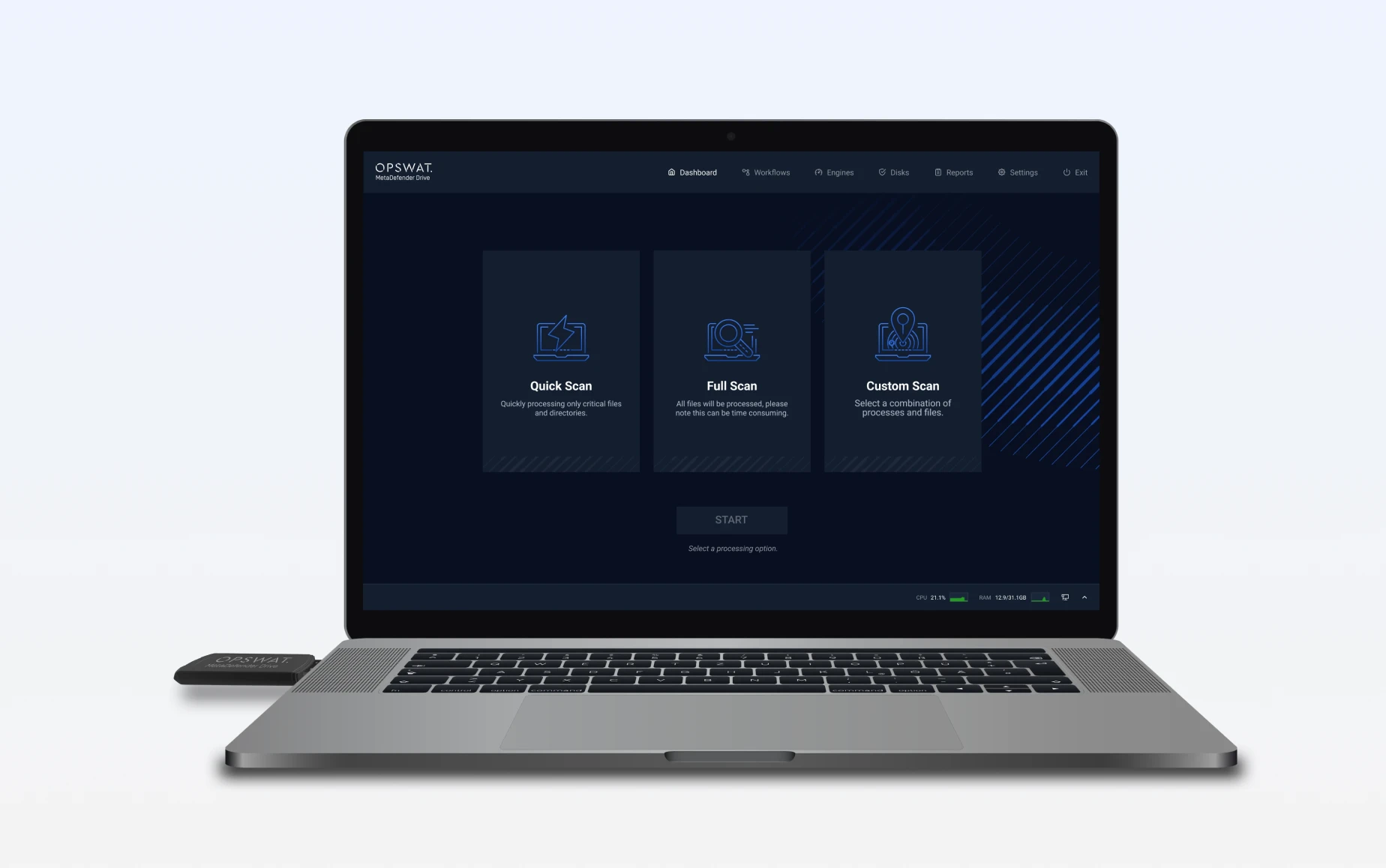
MetaDefender Drive creates a portable perimeter, anywhere maintaining an airgap is critical. Perform a secure boot, bare-metal boot scan on computers and servers before they access critical networks.
- No Software Installation on Asset Required
- End-to-End Portable Malware Security
- 1TB Storage Offering Expanded Archive Capacity and Improved Performance
- Support for UEFI, GPT, Legacy BIOS
- TAA and FIPS 140-2 Compliant
- Localization Support in 12 Languages, including English, French, and Japanese
Security Compliance Ready
Self-Checking Secure Firmware
Made in the U.S.A.
MetaDefender Drive with Smart Touch
MetaDefender Drive with Smart Touch scans and ensures all hardware, from new servers to vendor laptops, is safe to use before entering your environment.
- Multiscanning up to 7 Trusted Engines
- Physical Network Kill Switches
- Zero Risk of Network Compromise During Operation
- Enterprise Central Management
- Sync Reports, Update Engines, and Applications over Wireless
- No Software Installation Required
Touchscreen Display
No Software Install Required
Wi-Fi & Cellular Connectivity
Made in the U.S.A. (Select Model)
Scan and Verify Devices Before They Power On
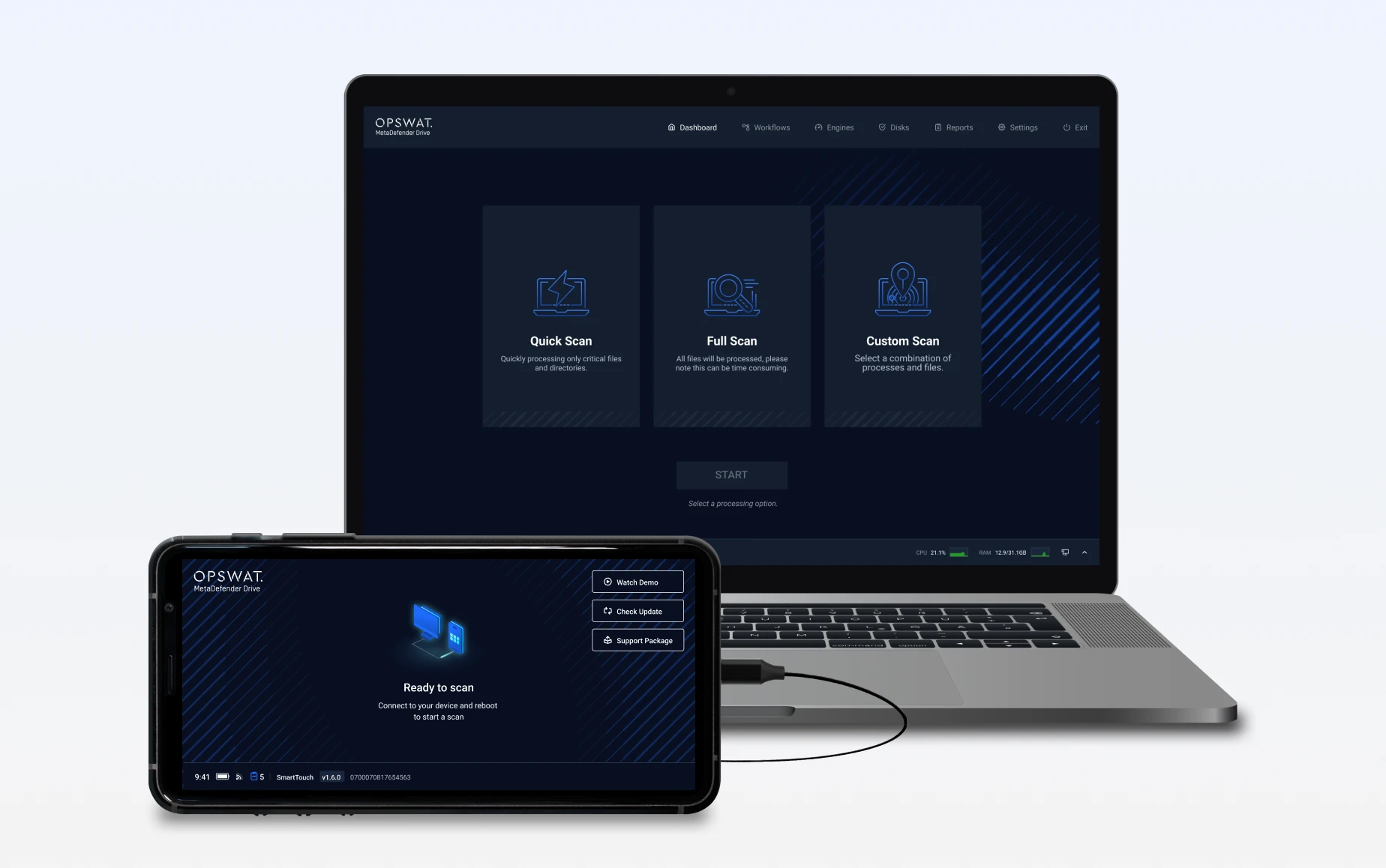
Plug It In
Secure boot target device directly from MetaDefender Drive
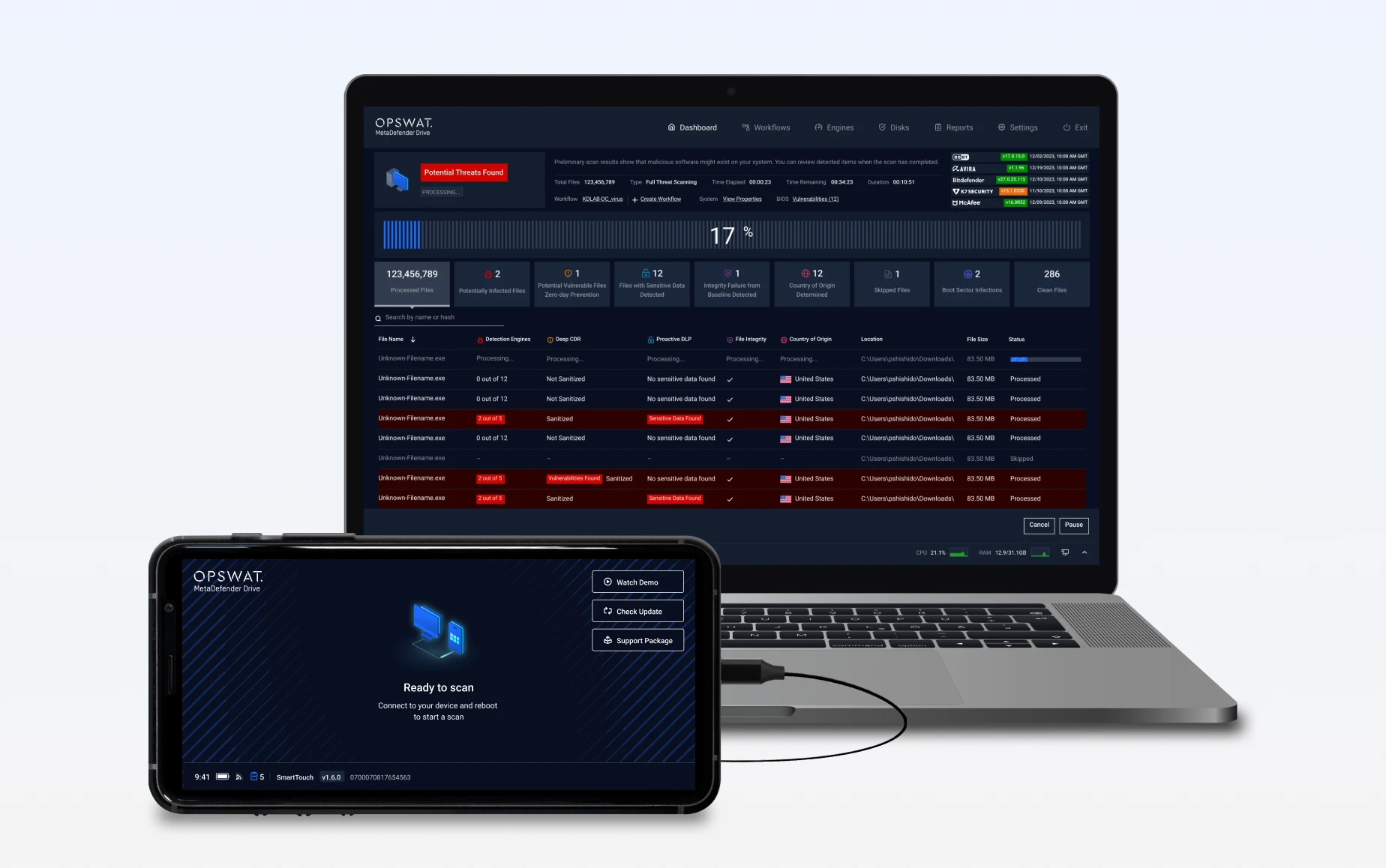
Run Scan
MetaDefender Drive performs bare metal Multiscanning with up to 7 engines







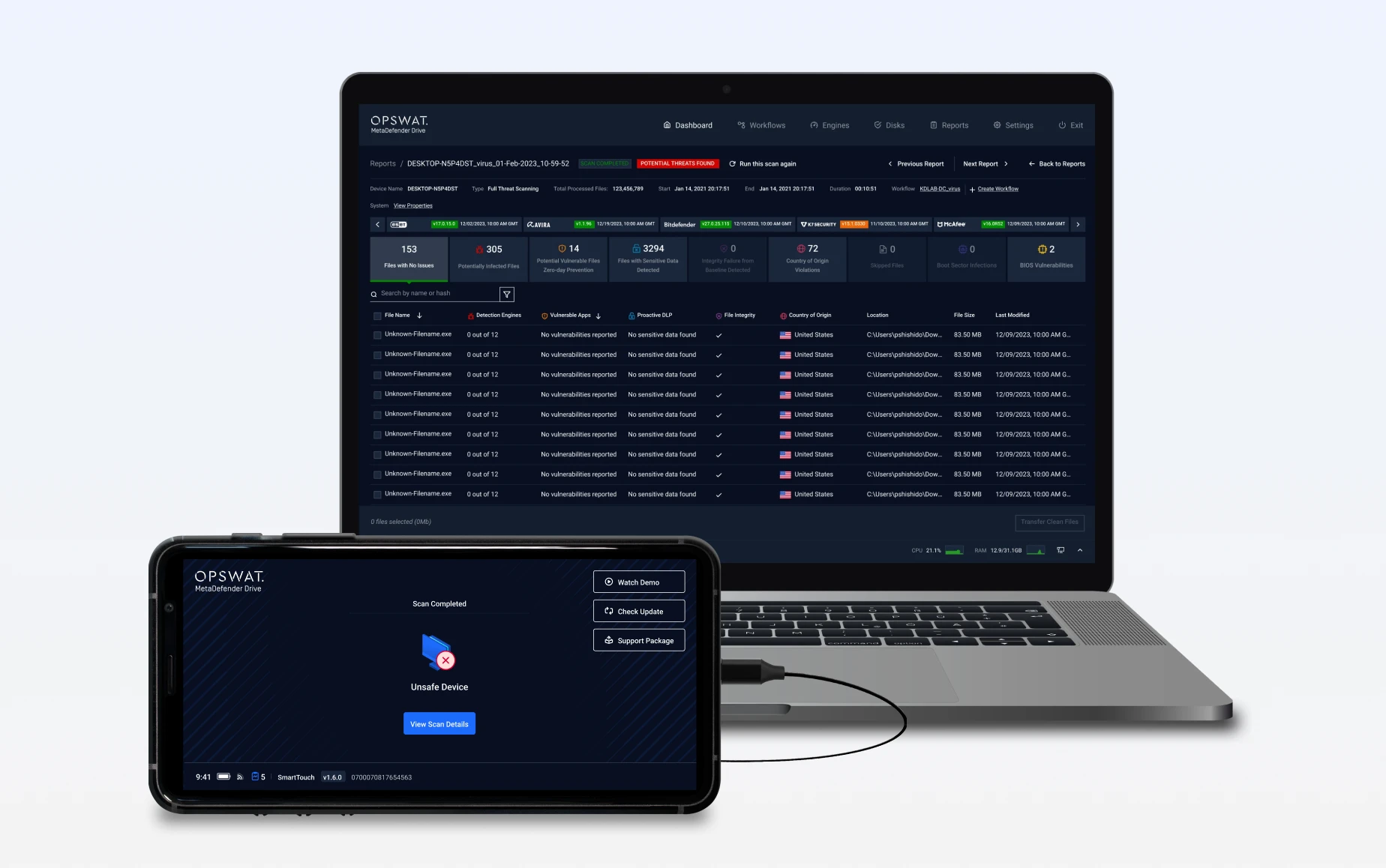
View Reports
Review scan results to identify exactly what requires remediation
Connect and Boot
Use Wi-Fi or cellular to update engines and security on MetaDefender Drive with Smart Touch, then connect to the target device and securely boot from the Drive.
Run Scan
With physical kill switches for air-gapped environments, securely boot your device directly from the Smart Touch for a full bare metal multiscanning with up to 7 engines. Includes 1TB of Storage for large archive scanning.







View Reports
- 5.7” screen to view the results of scans, directly on the Smart Touch interface.
- Streamlined, automated report syncing with My OPSWAT Central Management.
End-to-End Hardware Protection
MetaDefender Drive ensures unverified devices are safe before they connect. By scanning transient laptops, desktops, and servers outside the operating system, Drive detects and removes malware, vulnerabilities, and integrity risks. Threats are eliminated, clean files are verified, and only trusted devices are allowed into secure or air-gapped environments.
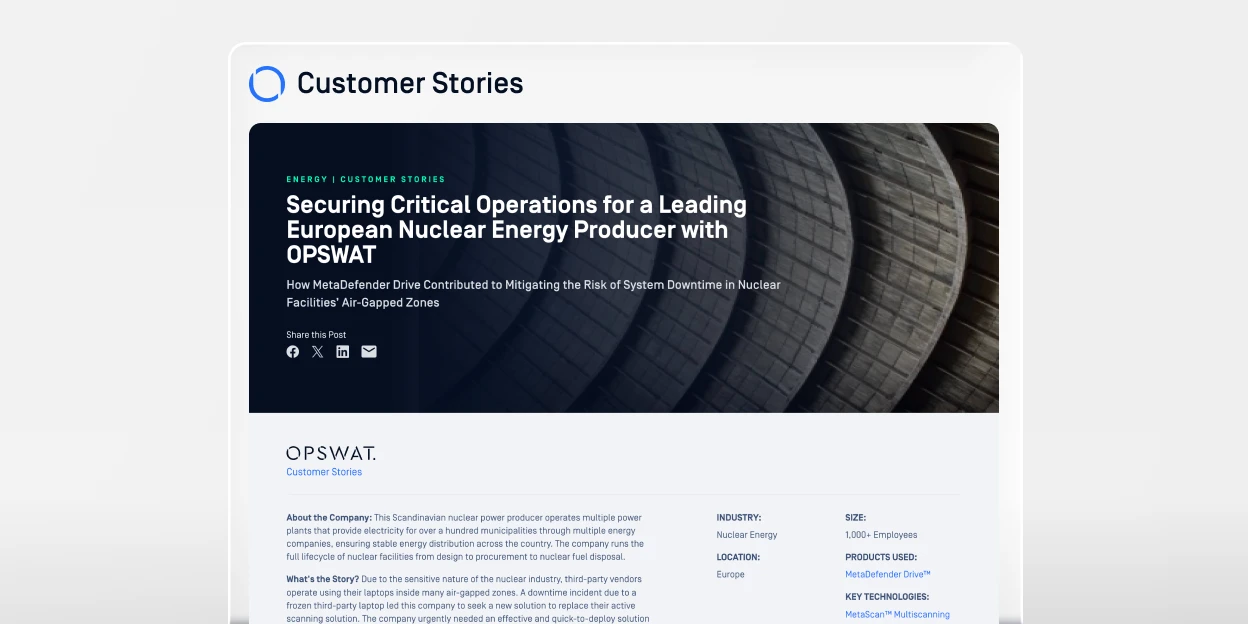
“OPSWAT and MetaDefender Drive helps us control that, showing that anything that comes into our environment is clean.”
Nuclear Restoration Services
Built with OPSWAT’s #1 Market-Leading Technology
OPSWAT’s proven, globally trusted, and award-winning technology prevents threats to the hardware supply chain.
More Engines Are Better Than One
- Detect nearly 100% of malware
- Scan simultaneously with 30+ leading AV engines
Prevent Sensitive Data Loss
- Utilize AI-powered models to locate and classify unstructured text into predefined categories
- Automatically redact identified sensitive information like PII, PHI, PCI in 110+ file types
- Support for Optical Character Recognition (OCR) in images
Enable Instant Detection of a File’s Geographic Source
- Detect the geographic source of uploaded files, including PE, MSI, and SFX (self-extracting archives)
- Automatically analyze digital fingerprints and metadata to identify restricted locations and vendors
Detect Application Vulnerabilities Before They Are Installed
- Check software for known vulnerabilities before installation
- Scan systems for known vulnerabilities when devices are at rest
- Quickly examine running applications and their libraries for vulnerabilities
Portable Malware Scanning That Helps You Stay Compliant
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure. Failure to comply with these regulations put your organization at financial, reputational, and even physical risk. Portable Malware Scanning is critical to verifying devices before power-on and maintaining compliance with key global regulations.
Purpose-Built Supply Chain Security
Critical Protection for Critical Environments
Critical Expertise for Critical Enviroments
OPSWAT offers purpose-built, innovative solutions to face the evolving cybersecurity challenges faced by our customers. Our team of subject matter experts bring years of experience in cybersecurity and risk mitigation to make sure you get the most out of those solutions.