Import (Low→High)
- Prevents malware from entering classified networks.
- Combines Multiscanning, Adaptive Sandbox Analysis, Deep CDR™ Technology, unidirectional control and protocol breaks.
Enable mission-critical collaboration with OPSWAT’s modular, purpose-built solutions.


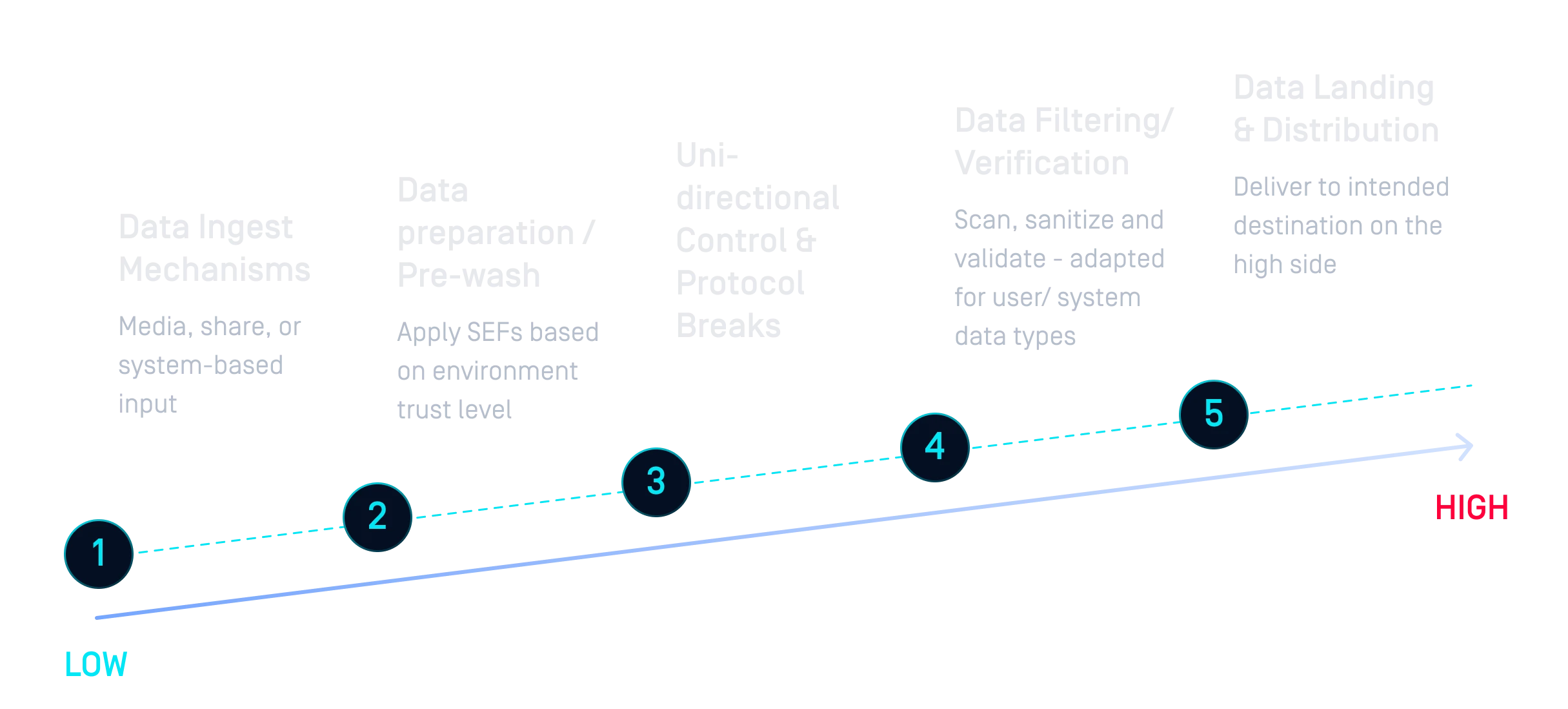
Data moving across domains now comes in high volumes and diverse formats, from everyday user files to geospatial data, installers, and application updates. Legacy and hardware-only systems struggle to process this variety and cannot scale to deliver the Security Enforcing Functions (SEFs) needed in a flexible, expandable way.


Systems must withstand highly resourceful attackers, including nation-state threats. Data transfers between security levels expose vulnerabilities that traditional defenses can’t address, while AI-driven attacks demand modern, adaptive protection.


Permanently isolating data no longer meets cross-territorial collaboration needs. Modern CDS systems must adapt to business demands, supporting diverse volumes, data types, and applications while enabling seamless API-to-API and cloud-to-on-prem transfers.
OPSWAT provides a modular, software-led approach that adds to existing processes,
with market-leading technologies.
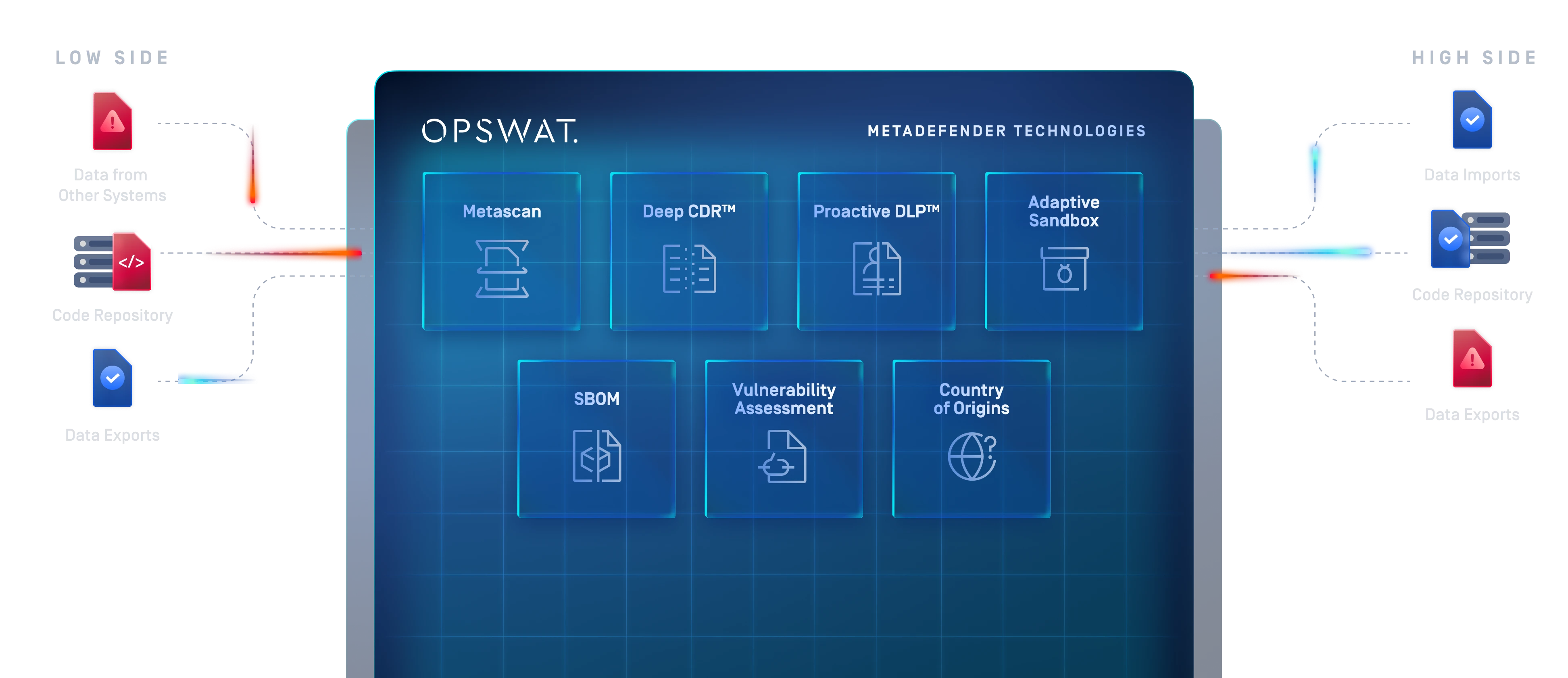
With market-leading technologies and plug-in/plug-out capabilities, OPSWAT’s modular approach is a more efficient way to build CDS solutions.
With the emulation sandbox, organizations can look at IOCs in complex data types such as OS patches or applications and eliminate potential threat vectors.
Proactive DLP can help ensure that data transferred from higher to lower classifications (such as reports shared with partners) does not contain sensitive information, not meant for release, by detecting and blocking it within files.
With the MetaDefender Kiosk, data coming from Removable Media can go through the security enforcement mechanisms that are appropriate based on your organization's risk posture.
One main advantage is that using MD Core in conjunction with tools like MFT allows for a full audit trail, enabling organizations to trace back and see which role or persona tried to exfiltrate the data.
Unlike traditional air-gapped approaches that isolate data and make collaboration difficult, OPSWAT’s solutions integrate into cross-domain architectures and enforce security policies. The hybrid hardware-software approach supports multiple communities of interest while ensuring sensitive data is properly controlled, monitored, and audited.
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure.