Prevent. Detect. Neutralize.
Total File Protection in the Cloud.
Stop known, unknown and AI-generated threats from disrupting business processes
across cloud-native and hybrid environments in milliseconds.
- Comprehensive File Security
- Seamless Cloud Integration
- Simplified Compliance Automation
OPSWAT is Trusted by
What We’re Up Against


Weaponized File Uploads
Threat actors can use file uploads to insert ransomware, viruses, and other malware into systems. Organizations need to scan all files – even those coming from trusted resources – for any malicious content. Multiscanning is recommended, as multiple engines increase detection rates.


Complex Compliance Laws
Organizations must comply with regulatory mandates (like SOC 2, GDPR, ISO 27001, HIPAA, PCI, FISMA, FINRA) or face severe financial and legal consequences. As a result, companies need to select partners that support compliance efforts.

Zero-Day Attacks
Detection-based cybersecurity can identify known threats but is ineffective against zero-day attacks. These attacks exploit previously unknown vulnerabilities and cannot be detected by traditional antivirus engines, since no signatures exist for the new exploits. To mitigate Zero-Days, organizations need to go beyond detection, and completely disarm files from any suspicious content.

Unsecured File Downloads
Files must be analyzed at every point of download, regardless of where or how they are downloaded, or whether the source is known or unknown. Balancing security with employee access to resources remains a significant issue.

Distributed Work Vulnerability
In enterprise-level companies, employees work across various locations, time zones, and unmanaged devices, making it more difficult for organizations to monitor and control file-based threats and to ensure that files are processed only within desired regions.
A Unified Approach for Enterprise File Security
MetaDefender Cloud delivers complete file protection across cloud-native, SaaS, and hybrid infrastructures.
It stops known, unknown, and AI-generated threats while helping organizations simplify compliance and maintain business continuity.
Complete File Security Across
All Cloud Workflows
File Uploads
File Downloads
Secure enterprise browsers from threats coming from unfamiliar websites downloads.
File Sharing & Collaboration
Protect the safety and confidentiality of your shared data and keep compliant with data protection laws, without compromising speed or performance.
File Storage
Protect your organization from data breaches, eliminate downtime, and ensure compliance with data protection laws.
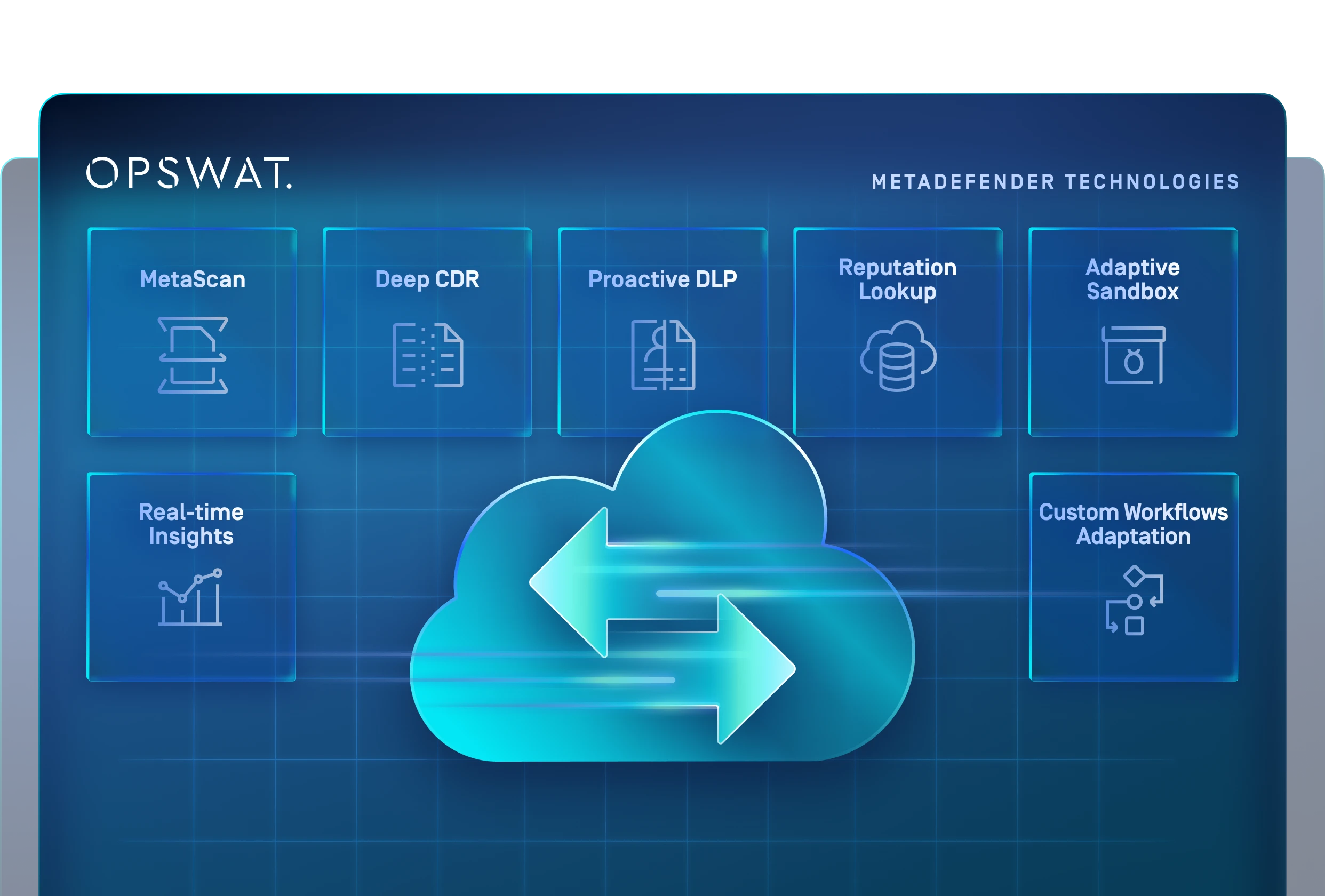
Multi-Layered Defense Powered
by MetaDefender Cloud
Seamless integrations, meant to secure files across the entire workflow; from upload to download, sharing, collaboration, and storage.
100%
Protection
Deep CDR Test

Works Where You Work
20+ Engines
Detection Rates
Plug and Play
Compliance with global standards
Trusted by top banks & insurance companies worldwide
#1 Market Leader
Complete File Protection with
Market-Leading Technologies
Stop Threats That Others Miss
- Supports 200+ file formats
- Recursively sanitize multi-level nested archives
- Regenerate safe and usable files
More Engines Are Better Than One
- Detect nearly 100% of malware
- Scan simultaneously with 20+ leading AV engines
Detect Evasive Malware with Advanced Emulation-Based Sandboxing
- Analyze files in a high-speed
- Anti-evasion sandbox engine extracts IOCs
- Identify zero-day threats
- Enable deep malware classification via API or local integration
Prevent Sensitive Data Loss
- Utilize AI-powered models to locate and classify unstructured text into predefined categories
- Automatically redact identified sensitive information like PII, PHI, PCI in 110+ file types
- Support for Optical Character Recognition (OCR) in images

Reputation Lookup
- Check IP addresses, domains, file hashes, and URLs for malicious behavior using multiple IP & URL reputation sources.
- Identify threats like botnets that would not be found through traditional scanning
Zero-day Attacks Detection
Detect Zero-Day Attacks with the Adaptive Sandbox technology
Real-time Insights
Get real-time scanning reports and usage insights
Custom Workflows Adaptation
Custom workflows adapting to specific user needs
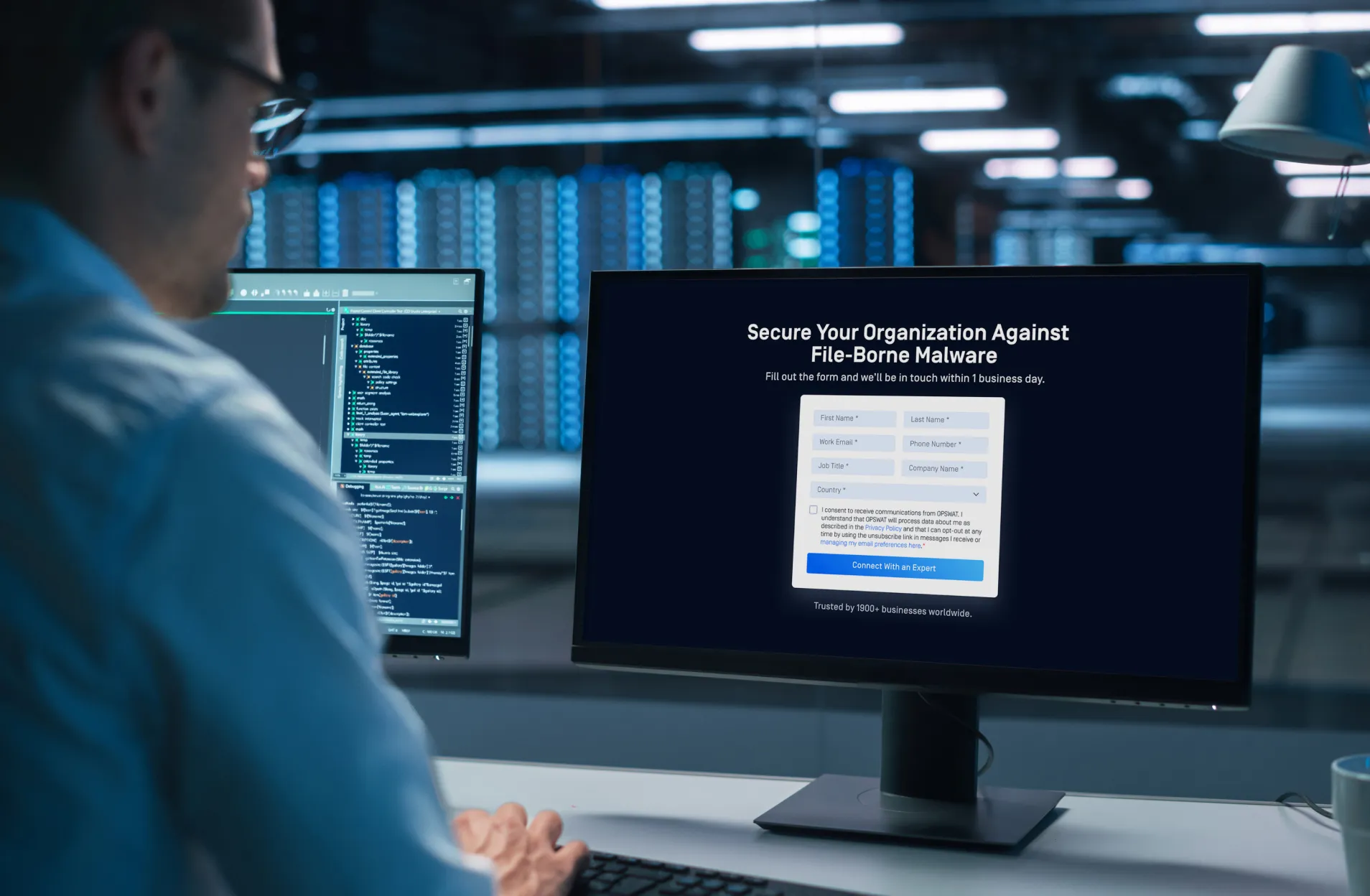
3 Easy Steps to Secure Your Organization Against File-Borne Malware
Trusted by Market-Leading Banking and Insurance Companies Worldwide
A Single Platform Protects
Your Entire Cloud Stack
Seamless integrations, meant to secure files across the entire workflow; from upload to download, sharing, collaboration, and storage.
Support Compliance with
Regulatory Requirements
MetaDefender Cloud Global Infrastructure
We value the experience and privacy of our users. Our service is provided by servers located in the following locations
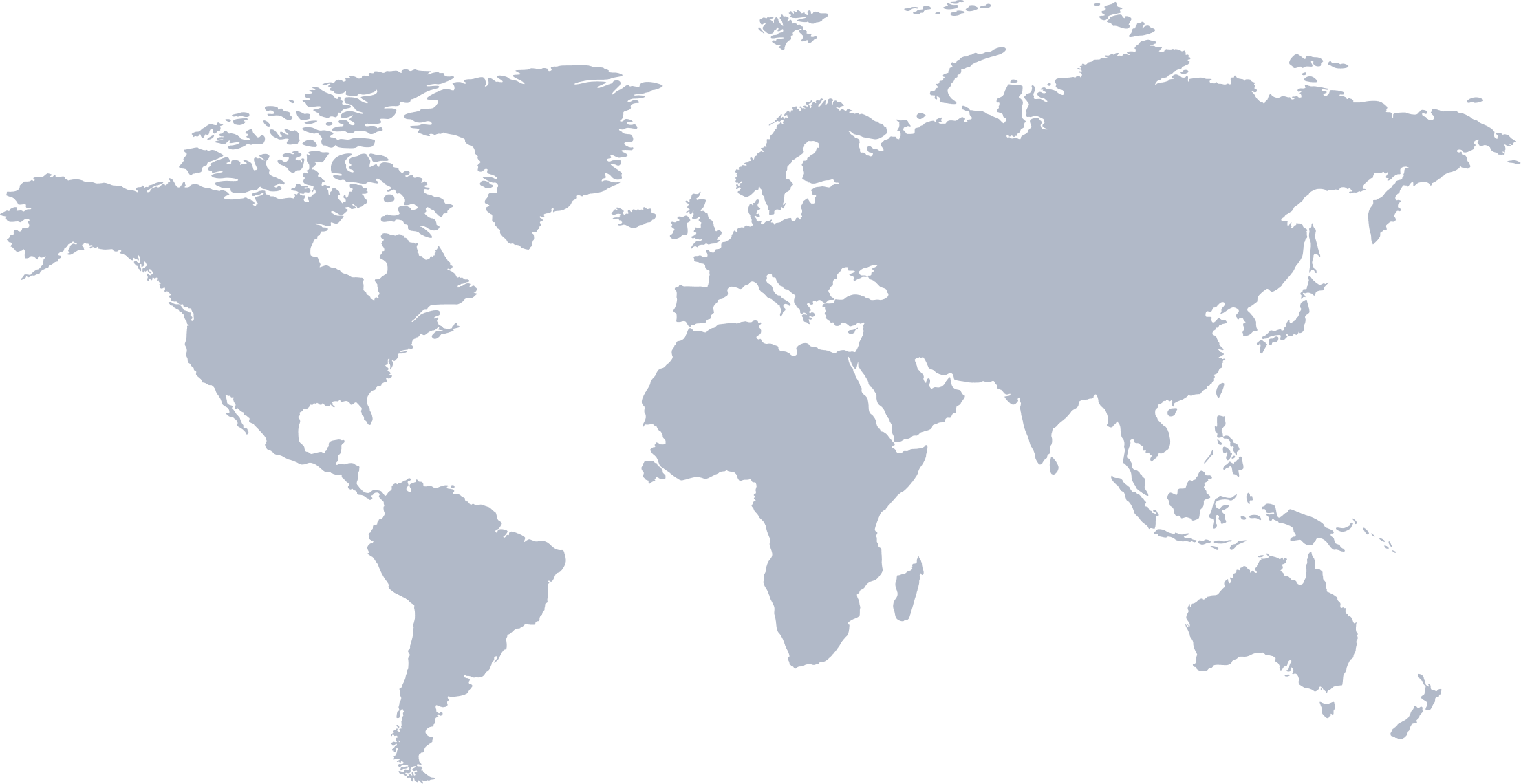
- North America Location: United States, West Coast
- Canada Location: Montreal
- Europe Central Location: Germany
- India Location: Mumbai
- Singapore Location: Singapore
- Japan Location: Tokyo
- Australia Location: Sydney
Built to Protect the World’s
Critical Infrastructure
Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.