MetaDefender InSights C2
Stop Cyber Threats at the Source
Detect and disrupt Command and Control (C2) infrastructure in real-time, preventing post-exploit activity and protecting your network from advanced threats.
Proactive Defense Against Hidden Threats: Neutralize C2 Infrastructure in Real-Time
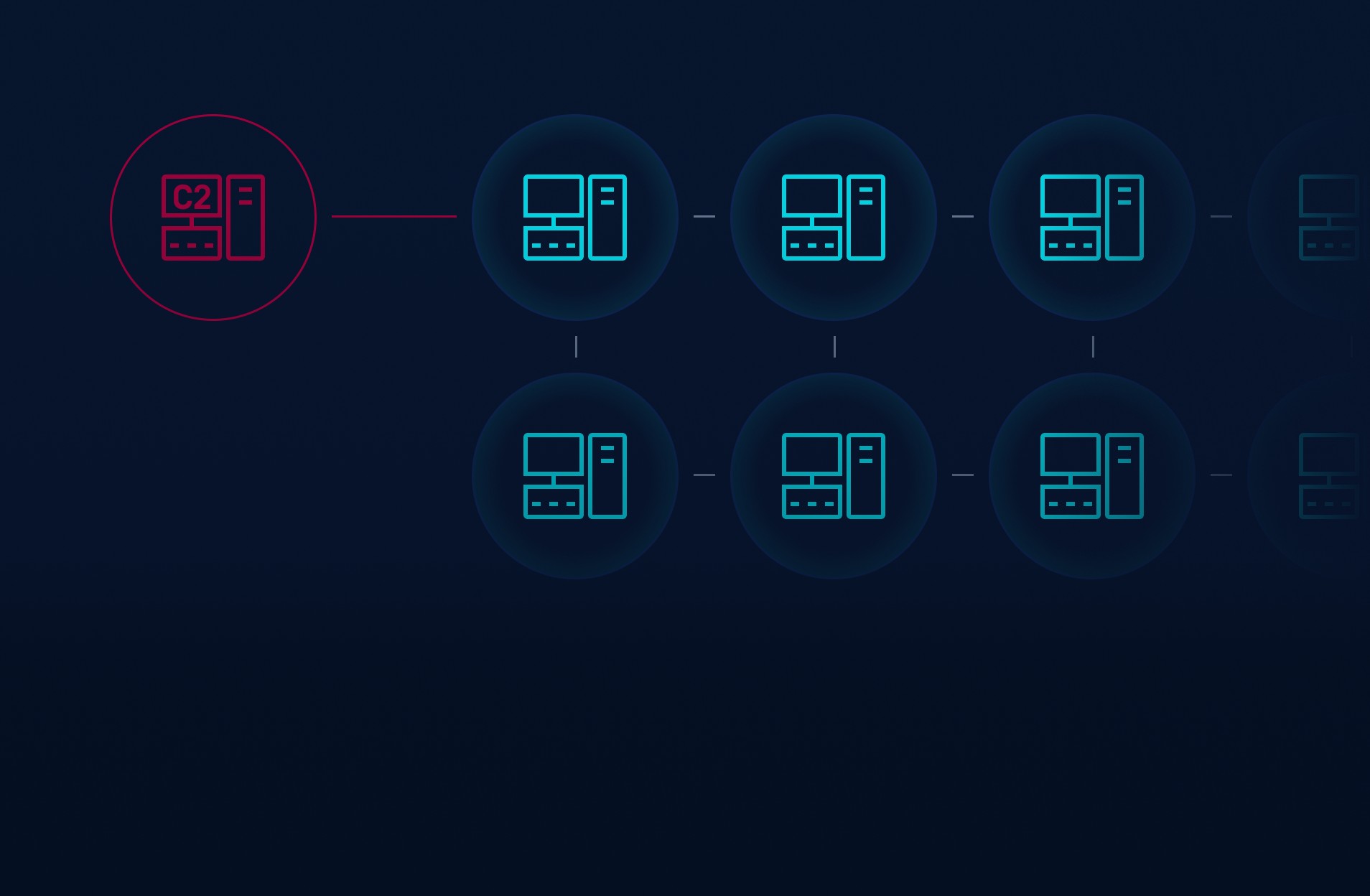
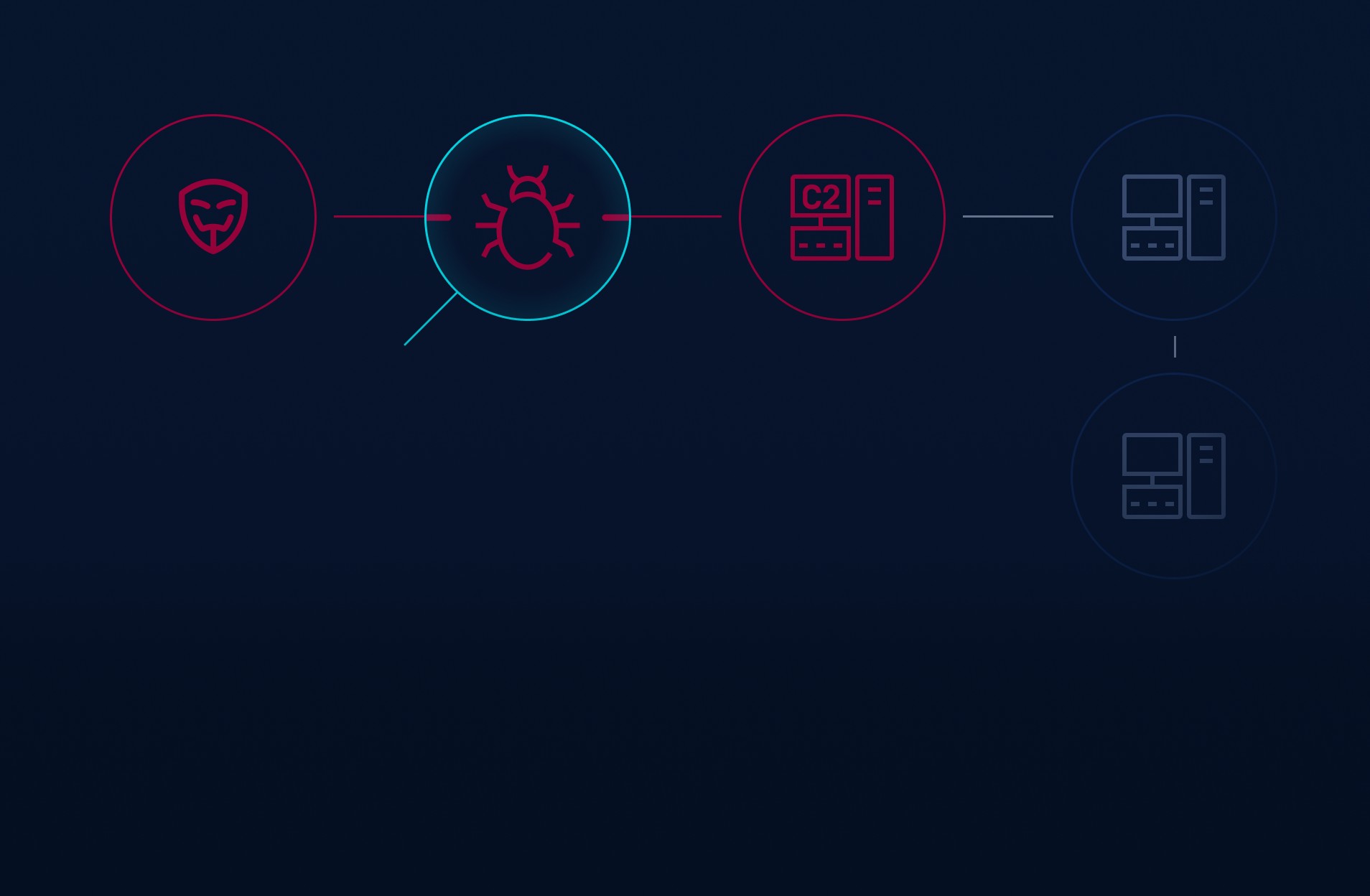
InSights C2 is a specialized threat intelligence solution designed to identify and neutralize adversary Command and Control (C2) infrastructure. Whether you’re defending against targeted attacks or large-scale malware campaigns, InSights C2 ensures that your organization can detect and prevent post-exploitation activity with precision and speed.
MetaDefender InSights C2
Proactive Threat Hunting and Seamless Integration: How InSights C2 Works
InSights C2 delivers near real-time intelligence on adversary C2 infrastructure, seamlessly integrating with your security tools to automatically detect, block, and respond to threats. With proactive threat hunting capabilities and the ability to analyze historical data, InSights C2 empowers your team to stay ahead of emerging threats and ensure comprehensive protection.

Continuously Updated Intelligence
InSights C2 delivers continuously updated data on C2 infrastructure based on proprietary research and partnerships.
Seamless Integration
InSights C2 integrates effortlessly with SIEM, SOAR, XDR, and other platforms.

Proactive Threat Hunting
Leveraging InSights C2 to proactively hunt for adversary C2 nodes.
Historical Data Analysis
InSights C2 enables retrospective analysis of network traffic and logs.
Maximize Threat Detection and Mitigation
InSights C2 provides advanced features that enable organizations to detect, analyze, and respond to threats with precision. Benefit from C2 detection, automated blocking, and in-depth threat analysis, all designed to improve your response times and safeguard your critical assets.
Timely Detection of C2 Infrastructure
Continuously monitor for emerging C2 nodes and malicious communications to stop threats before they can escalate.
Automated C2 Blocking
Integrate with your existing security tools to automatically block malicious IPs, domains, and C2 callbacks, minimizing manual intervention and improving response times.
Comprehensive C2 Intelligence
Access a wide dataset enriched with proprietary intelligence on attacker infrastructure, ensuring precise and actionable detection.
Early Warning of C2 Activity
Benefit from unmatched lead times on C2 nodes, giving your security team the earliest possible warnings of impending threats.
Seamless Integration
InSights C2 integrates with key platforms like SIEM, SOAR, XDR, and TIPs, providing your team with enriched threat intelligence that enhances your security workflows.
Historical Threat Hunting
Use historical threat intelligence to retroactively analyze past network traffic and logs, uncovering hidden C2 activity and ensuring full incident remediation.
Purpose-Built for Every Sector
MetaDefender InSights empowers organizations with industry-focused threat intelligence, ensuring proactive defense and compliance across critical sectors.
Technical Documentation
Getting Started
Deployment & Usage
Unlock the Full Potential of Our Products

Recommended Resources
Take Control of Your Cyber Defense
Get ahead of evolving threats with InSights C2. Request a demo today to see how real-time intelligence and proactive defense can strengthen your security operations.