
MetaDefender Transfer Guard™
Uncompromising Secure File Transfer with Comprehensive Threat Prevention
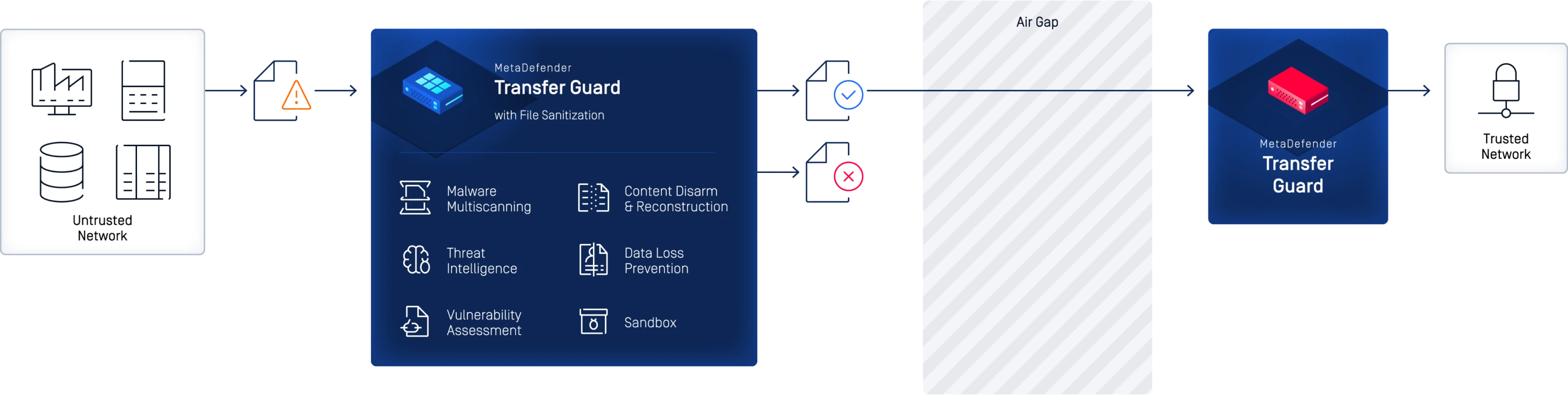
MetaDefender Transfer Guard ensures uncompromising security for file transfers between networks of different security classifications, providing a secure file scanning and transfer solution that delivers unsurpassed performance, reliability, and security; securely transfer files, patches, and software updates into OT and high side networks like never before with the threat prevention technology in MetaDefender Core.
Easy to Deploy
Deploys Quickly and Seamlessly
Reliable Payload Delivery
Comprehensive File Sanitization
High Availability
& Minimize Data Loss
No Return Path
Simple to Operate
Scalable
Transparent to Users
Space-Efficient and Easily Rack-Mounted
- Secure file transfer between networks of different security classifications
- Secure, hardware enforced unidirectional data paths
- True protocol break, non-routable connection
- Assured delivery with no data loss
- Easy deployment and operation
- Isolates OT/ICS assets against cyberattacks
- Prevent malicious C&C communications
- Seamlessly integrates with MetaDefender Kiosk, Core, and Managed File Transfer
- Secures the transfer of software updates and other files to the protected domain

| Configurations | ||
|---|---|---|
| Configurations | Throughput | 100 Mbps, 1 Gbps, or 10 Gbps |
| Electrical | ||
| Electrical | Redundant Power Supply | 250W |
| Voltage | 100-240VAC, auto ranging | |
| Power Consumption | 150W typical | |
| Hardware | ||
| Hardware | Dimensions | 2x 19 x 1.75 x 15.75" (483 x 44 x 400mm) |
| Weight | 2x 27lb (12.2kg) | |
| Operating Temp | 32 – 131°F (0 – 55°C) | |
| MTBF | >50,000 hours | |
| Mounting | 1U rack kit included | |
| Other Specifications | ||
| Other Specifications | Connectivity | 2x USB for connecting provided crypto keys |
| Tested Latency1 | 0.6ms TCP, 0.7ms UDP | |
| Protocol & Certification | ||
| Protocol & Certification | File System | FTP, FTPS, SFTP, Folder and file transfer/copy, Windows File Share, SMB, CIFS, Antivirus updates, Patch (WSUS) updates |
| Streaming | HTTPS, Syslog, TCP, UDP | |
| Certification | Common Criteria EAL 4+2 FCC/CE/UKCA | |
Transfer Guard Deployment
MetaDefender Transfer Guard adds the industry-leading threat prevention technologies found in MetaDefender Core to OPSWAT’s secure data transfer solution.
Talk to One of Our Experts and We’ll Help You Build the MetaDefender Transfer Guard for Your Environment
Scan Before You Send
Easy to Deploy
Preconfigured platform deploys quickly and seamlessly.
Vulnerability Assessment
Uncover vulnerabilities in installers, binaries, or applications before they are installed and plug any security holes.
Threat Intelligence
Detect zero-day malware and more Indicators of Compromise (IOCs) with adaptive threat analysis technology.
Deep Content Disarm and Reconstruction
Recursively sanitize 200+ file types with market leading Deep CDR™ Technology and remove 100% of potential threats.
Proactive Data Loss Prevention
Remove, redact, or watermark sensitive data in files before it enters or leaves your network.
Enables Regulatory Compliance
Meet or exceed Industrial Cybersecurity standards, including NERC CIP, NIST ICS/CSF/800-82/800-53, IEC 62443, NRC 5.71, CFATS, ISO 27001/ 27032 / 27103, ANSSI, IIC SF, and more.
Built with OPSWAT’s #1 Marketing-Leading Technology
OPSWAT’s proven, globally trusted, and award-winning technology prevents removable and peripheral media-borne threats from entering critical IT and OT environments.
Stop Threats That Others Miss
- Supports 200+ file formats
- Recursively sanitize multi-level nested archives
- Regenerate safe and usable files
More Engines Are Better Than One
- Detect nearly 100% of malware
- Scan simultaneously with 30+ leading AV engines
Detect Evasive Malware with Advanced Emulation-Based Sandboxing
- Analyze files in a high-speed
- Anti-evasion sandbox engine extracts IOCs
- Identify zero-day threats
- Enable deep malware classification via API or local integration
Prevent Sensitive Data Loss
- Utilize AI-powered models to locate and classify unstructured text into predefined categories
- Automatically redact identified sensitive information like PII, PHI, PCI in 110+ file types
- Support for Optical Character Recognition (OCR) in images
Enable Instant Detection of a File’s Geographic Source
- Detect the geographic source of uploaded files, including PE, MSI, and SFX (self-extracting archives)
- Automatically analyze digital fingerprints and metadata to identify restricted locations and vendors
Secure Your Software Supply Chain
- Manage risks associated with open-source software (OSS), 3rd party components and dependencies
- Ensure codebase transparency, security, and compliance
Detect Application Vulnerabilities Before They Are Installed
- Check software for known vulnerabilities before installation
- Scan systems for known vulnerabilities when devices are at rest
- Quickly examine running applications and their libraries for vulnerabilities
MetaDefender NetWall vs. Firewall, Router Rules & VLANS
True unidirectional behavior, with no possibility of routable connections to protected zone.
| Feature | MetaDefender NetWall | Networking Solutions |
|---|---|---|
| Routing configuration | ||
| Protocol break, completely removed from TCP/IP connection | ||
| Meets functional requirements of data diodes | ||
| Guaranteed delivery with non-repudiable data movement | ||
| No complex rule-building | ||
| Guaranteed prevention of malware propagation | ||
| No ARP, BGP, TCP/IP handshake |
MetaDefender Optical
Diode Selector
Quickly determine the best-fit diode for secure and compliant unidirectional data flows across critical OT/ICS environments—powered by OPSWAT’s trusted optical and hardware-enforced diode technology.
“OPSWAT's solutions not only protect the critical assets of businesses but also provide the necessary tools and information to improve cybersecurity strategies.”
Technical Documentation
Getting Started
Deployment & Usage
Unlock the Full Potential of Our Products

Looking To Learn More About MetaDefender
Transfer Guard?
Explore documentation, articles, and blogs for more information about the MetaDefender Transfer Guard.







