Zero-Day Detection
for MetaDefender Core
Enable dynamic file analysis and behavioral threat detection
directly within your Core environment — no new infrastructure required.
- Install in Minutes
- No Extra Integration Needed
- Uses Your Existing Policies
Unified Zero-Day Detection

Layer 1: Threat Reputation
Expose Known
Threats Fast
Stop the flood of known threats.
Checks URLs, IPs, & domains in real time or offline to detect malware, phishing, & botnets.
Blocks reused infrastructure & commodity malware and forces attackers to rotate basic indicators.
Layer 2: Dynamic Analysis
Uncover Unknown
Threats
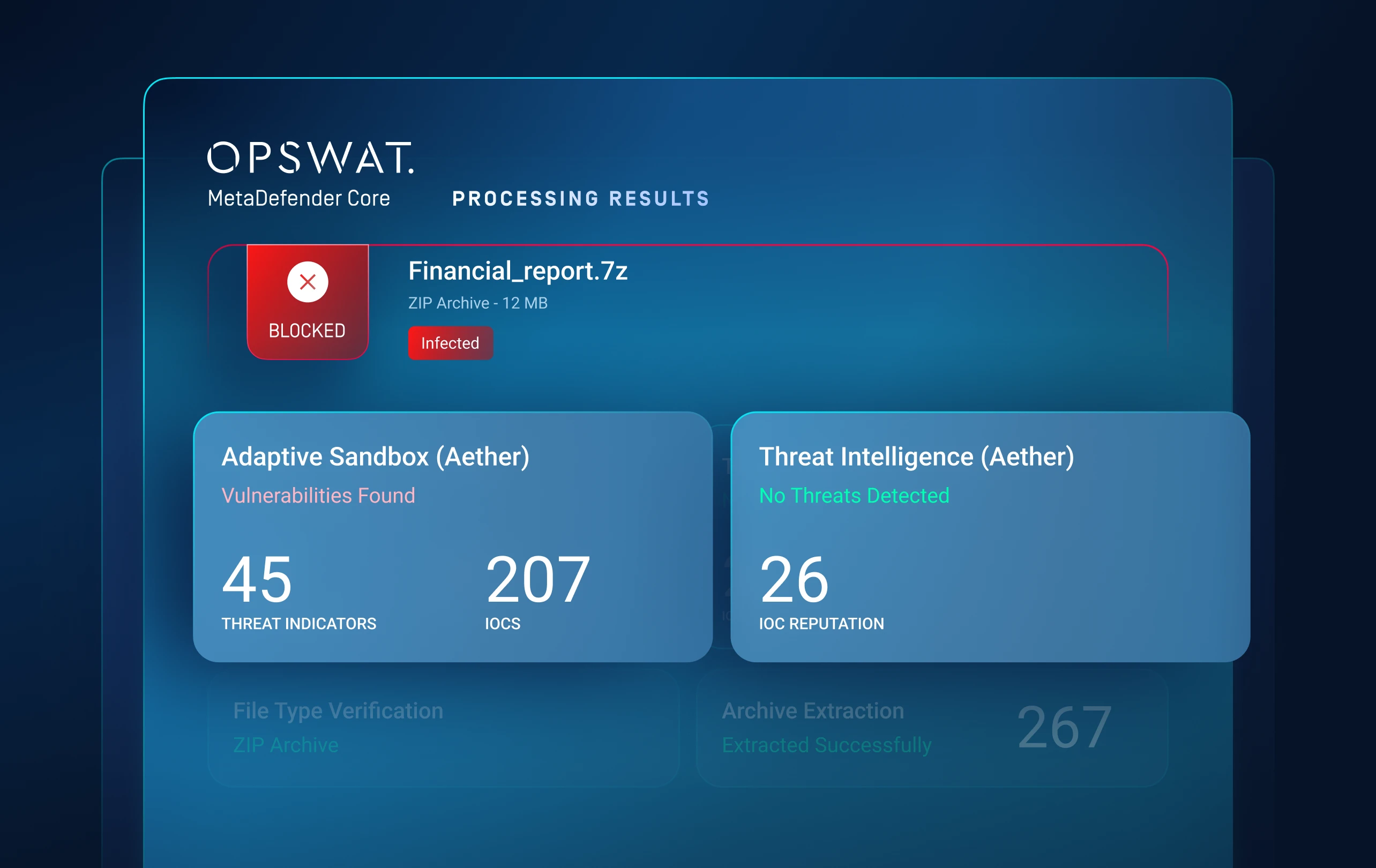
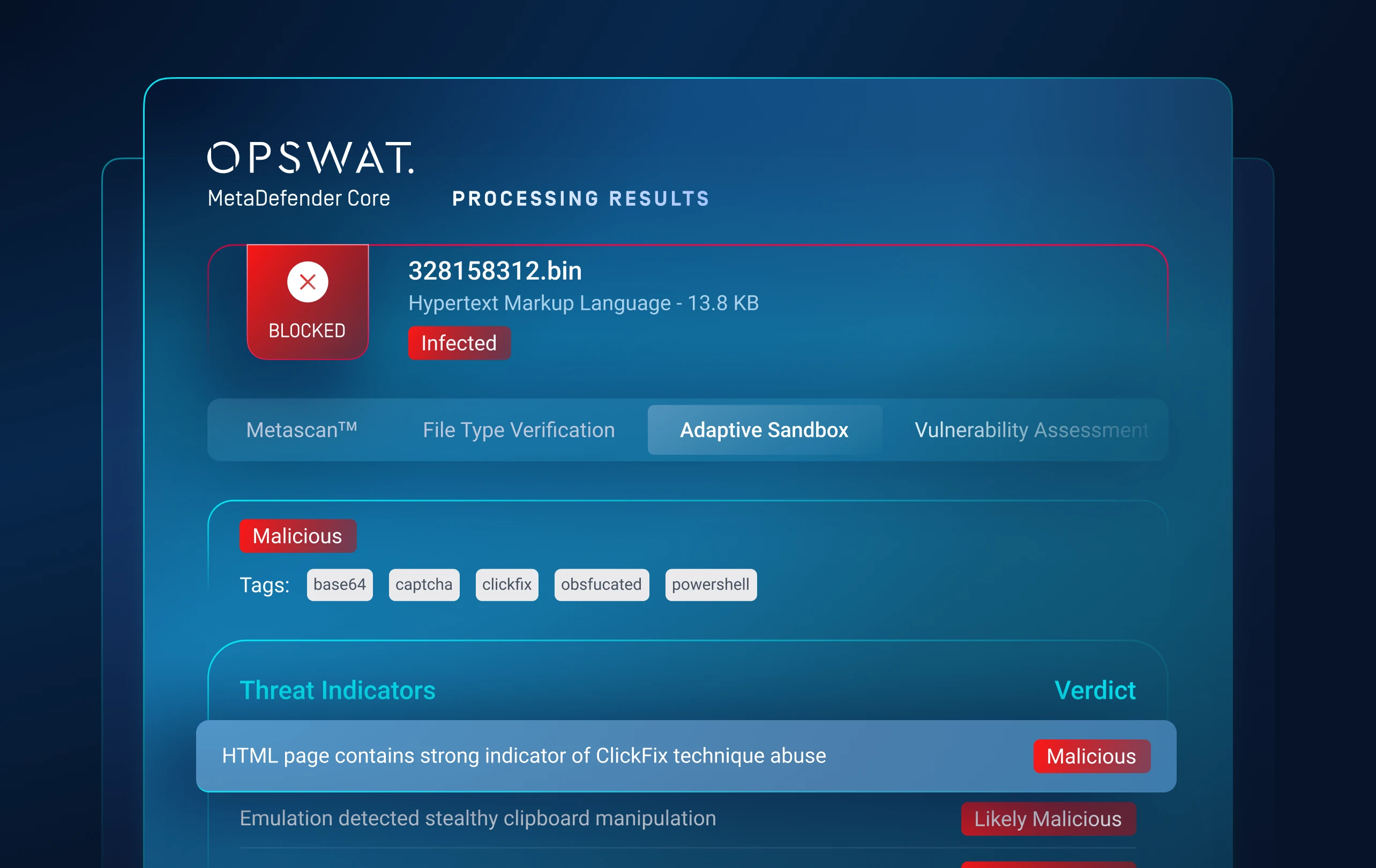
Detects evasive malware hiding from traditional sandboxes.
An emulation-based sandbox analyzes files to detect hidden threats like ransomware.
Exposes artifacts, loader chains, script logic and evasion tactics.
Layer 3: Threat Scoring
Prioritize Threats
Reduce alert fatigue.
Threat risk levels are ranked to quickly highlight priority threats in real-time.
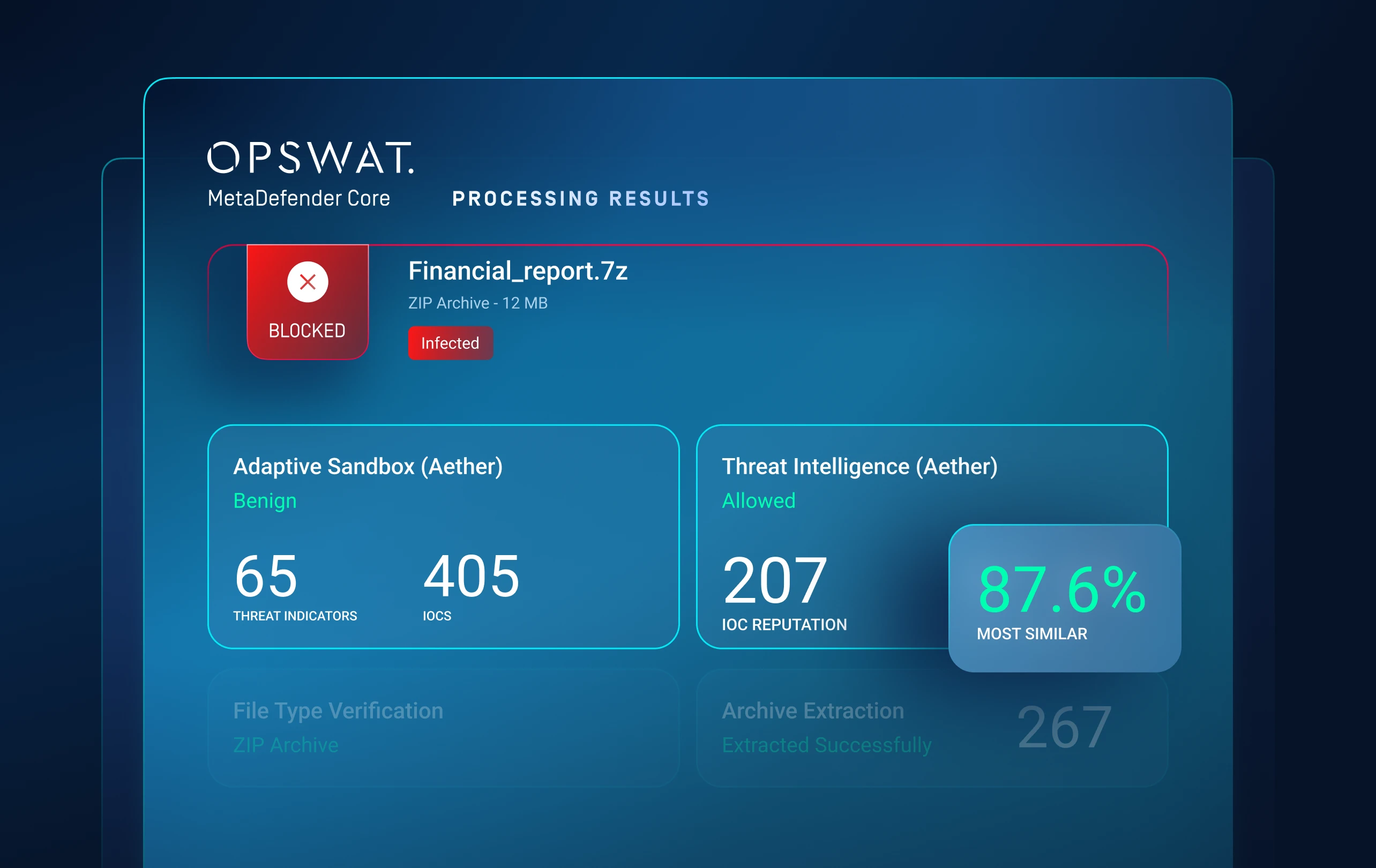
Layer 4: Threat Hunting
Identify Malware
Campaigns
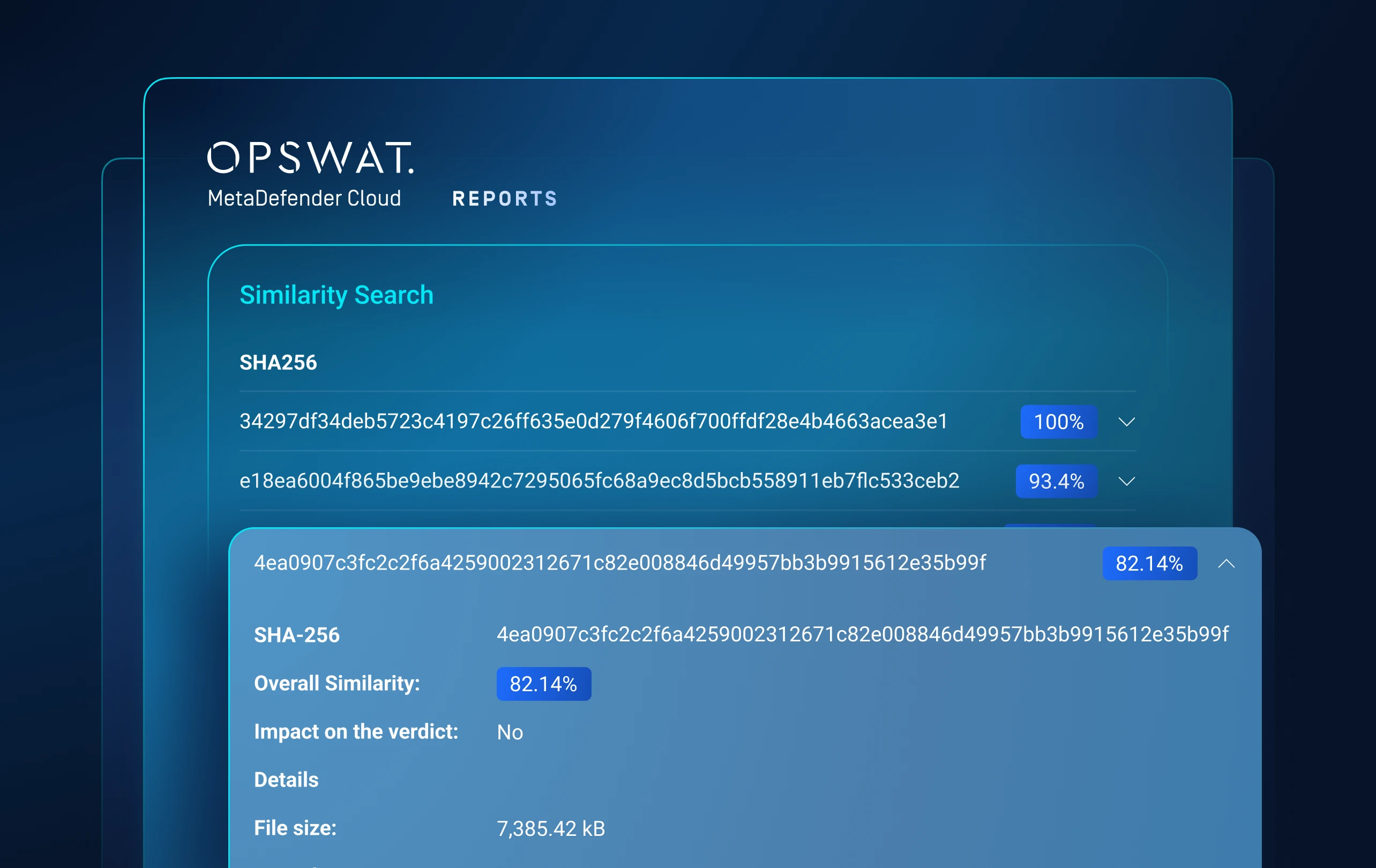
Machine-Learning Similarity Search
Threat Pattern Correlation matches unknown threats to known malware, tactics, infrastructure and more.
Uncovers malware families and campaigns, forcing attackers to overhaul tactics and infrastructure.
Get Started in 3 Simple Steps
Activate Your Integration
Add your API key to enable the Adaptive Sandbox with built-In Threat Intelligence.
Configure Policies
Select which file types or risk categories will be automatically sent for dynamic analysis.
View Results
View sandbox verdicts, threat scores, & IOCs directly within your Core dashboard.
- Step 1
- Step 2
- Step 3
Embedded & Remote
Adaptive Sandbox Engine Features
The following table outlines Adaptive Sandbox remote and embedded engine feature set. It doesn’t include platform features, such as the API coverage, configurable ACL (Access Control List), OAuth integration, CEF (Common Event Format) syslog feedback, etc.
Please contact us to book a technical presentation and get a run-through of all platform features and capabilities.
Support Compliance
with Regulatory Requirements
As cyberattacks and the threat actors that carry them out become more sophisticated, governing bodies around the world are
implementing regulations to ensure critical infrastructure is doing what’s necessary to stay secure.
Recommended Resources

MetaDefender Aether for Core

SANS Detection & Response Survey

2025 OPSWAT Threat Landscape Report
FAQs
It's the embedded sandbox module inside MetaDefender Core-ideal when you want zero-day analysis tightly coupled to your existing Core pipelines (ICAP, kiosks, email, MFT), especially in regulated or air-gapped sites. Choose Aether if you want the full standalone analysis UI and broader TI workflows.
Use Core policy/CDR triggers (macros, scripts, embedded objects, active content) to auto-route just the risky 2-3% for emulation-maintaining throughput without missing stealthy stage-one vectors. This can also be used manually to analyze the behavior of a file.
Independent detection-logic updates (faster coverage), offline certificate validation for air-gapped ops, expanded filetype/installer coverage, and double-Base64 decoding so you keep pace with evasions without full upgrades.
Yes-Linux server (RHEL/Rocky) on-prem, no outbound dependency in offline mode, minimal egress options, and simple REST connection to existing Core. Designed for OT/ICS and classified networks.
Sharper triage (fewer escalations), faster root cause (decoded scripts/unpacked loaders), and ready-to-action IOCs that enrich your SIEM rules and playbooks.