The Story Behind OPSWAT’s Leading Malware Analysis Solution
The Need for Smarter Sandboxes
As cyberthreats become more sophisticated, traditional security measures like antivirus solutions have increasingly struggled to keep pace. Malware authors have adapted, using advanced obfuscation techniques, anti-sandboxing measures, and fileless malware tactics that are designed to evade detection. Early malware analysis systems relied on basic API hooking or kernel monitoring to capture behaviors, but these approaches were often detectable by sophisticated malware, allowing it to hide its true nature.
With the rise of ransomware, zero-day exploits, and APTs (advanced persistent threats), organizations need far more comprehensive solutions to detect, analyze, and mitigate these threats before they wreak havoc on their environments. This is where sandboxing—the process of running suspicious files or programs in isolated environments to observe their behavior—plays a critical role in automated malware analysis.
But as threats have evolved, so too have sandboxing technologies. From simple API hooking to virtualization, hybrid analysis, and now emulation, sandboxes have grown into essential tools for modern malware detection. Let's explore the major milestones in the evolution of sandboxing technologies and explain how modern sandboxes address today’s increasingly evasive threats.
What is a Sandbox?
A sandbox is a secure, isolated environment used to test suspicious files through dynamic analysis (observing the behavior of programs in real-time by running or simulating them) to identify potential threats. This allows security professionals to detect any harmful actions the file may attempt, such as unauthorized data access, spreading to other parts of the system, or exploiting vulnerabilities.
By simulating various real-world scenarios within the sandbox—such as typical network communications or user interactions—security teams can gain insights into how malware might act in a live environment. This isolation ensures that even if the software is malicious, it remains contained within the sandbox environment, keeping the broader system and network safe from infection.
Modern sandboxes use a combination of dynamic and static analysis (examining the code structure without execution) to better identify malware, including new or previously unseen threats. They are especially effective for identifying polymorphic malware that changes its appearance to avoid detection or for threats that employ delayed execution tactics. Sandboxes are commonly integrated into advanced cybersecurity solutions, such as next-generation firewalls, secure email gateways, and endpoint protection platforms, providing an additional layer of security against sophisticated threats.
How Sandboxing Has Evolved Over Time
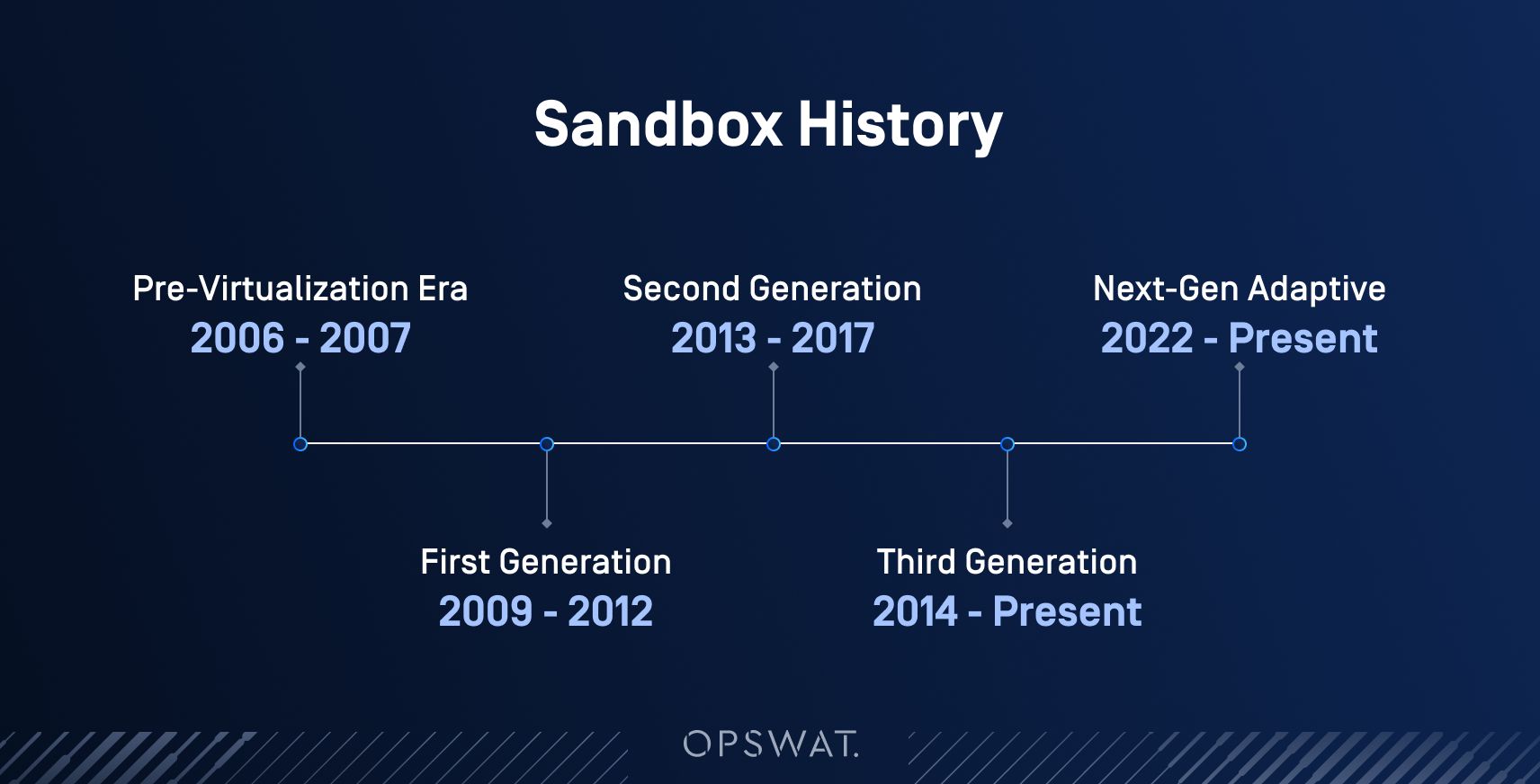
2006: Early API Hooking Sandboxes
- Technology: Introduced user-mode API hooking to capture malware behavior directly on the host system. However, these sandboxes lacked proper isolation, leaving the endpoint vulnerable.
2007: Early Academic Sandbox Projects
- Technology: Similar to API-hooking sandboxes, these projects focused on academic research but lacked isolation, making them susceptible to malware bypass.
Noteworthy Vendors:
Sunbelt Software, Academic Projects
2009: Introduction of Virtualization-Based Sandboxes
- Technology: This era introduced full system virtualization, enabling malware to be executed in isolated virtual machines. This provided safer analysis by fully containing the malware.
2010: Commercial Virtualization-Based Sandboxes
- Technology: Introduced multi-stage execution environments using virtualization to detect advanced persistent threats (APTs), going beyond traditional detection mechanisms.
Noteworthy Vendors:
Cuckoo Foundation, FireEye
2012: Appliance-Based Virtualization Sandboxes
- Technology: Focused on on-premise appliance-based sandboxes for high-security environments, offering full isolation and rich behavioral analysis, ideal for air-gapped networks.
2013: Hybrid Analysis
- Technology: Combined static code analysis with dynamic execution, incorporating memory dumps to provide deeper forensic insights, especially for evasive malware.
Noteworthy Vendors:
FireEye, Joe Security, Payload Security (later acquired by CrowdStrike)
2014: Hypervisor-Based Sandboxing
- Technology: These sandboxes analyzed malware at the hypervisor level, avoiding API hooking and providing kernel-level visibility while enhancing stealth against anti-sandboxing techniques.
2017–2022: Cross-Platform and Cloud-Native Sandboxing
- Technology: Introduced cross-platform support (e.g., Windows, macOS, Linux) and cloud-native deployments, integrating API-driven workflows for large-scale malware detection.
Noteworthy Vendors:
VMRay, Joe Security, CrowdStrike
2022: Next-Gen Adaptive Sandboxing
- Technology: Emerging sandboxes are evolving into comprehensive threat detection platforms that merge AI-driven insights, static and dynamic analysis, and reputation engines. These platforms include their own orchestration pipelines, delivering end-to-end threat detection and response capabilities.
- Capabilities: Supporting multi-cloud deployments, they combine high throughput with SOAR (Security Orchestration, Automation, and Response) functionality to automate the entire detection lifecycle.
Noteworthy Vendors:
OPSWAT
The Rise of Hybrid Analysis and Emulation
As malware authors evolved their techniques, it became clear that static analysis alone wasn't enough to detect modern threats. Sandboxes needed to adapt to these evolving tactics, and the introduction of hybrid analysis was a significant step forward.
Both VxStream Sandbox and Joe Sandbox led the way, combining dynamic execution with static memory analysis. This hybrid approach allowed for deeper analysis of malware that attempted to cloak its true behavior using techniques like encryption or obfuscation. By examining memory dumps, security teams could uncover malicious intent that wouldn’t be apparent during normal execution.
The latest trend in sandboxing is the incorporation of emulation, where malware is run in a fully synthetic environment designed to mirror real-world systems as closely as possible. OPSWAT’s MetaDefender Adaptive Sandbox and other advanced platforms are using emulation alongside hybrid analysis to handle fileless malware, memory-resident threats, and malware that specifically targets endpoint defenses.
Where We Are Today: An Overview of Modern Sandboxing Solutions
| Sandbox Type | Technology | Deployment | Key Features | Ideal Use Case |
| Cloud-Based Threat Detection Platform | Hybrid analysis, AI and TI | Cloud-native | API-driven, hybrid analysis with integration into existing platforms | Enterprise endpoint protection, large-scale detection |
| Appliance-Based Sandbox | Multi-stage APT detection | On-premises | Full isolation, multi-stage malware analysis | Air-gapped or high-security environments |
| Hypervisor-Based Sandbox | Hypervisor-level monitoring | Cloud/On-premises | Stealthy monitoring, resistant to sandbox evasion | Evasive malware detection, targeted or advanced threats |
| Emulation-Based Sandbox | Emulation | Cloud/On-premises/td> | High throughput, offline/air-gap support (e.g., URL reputation engine) | Large-scale enterprise detection, critical infrastructure, high-security |
Use Case Examples
| Use Case | Description |
| Critical Infrastructure / Air-Gapped | Offline analysis for isolated, secure environments in utilities, healthcare, and defense. |
| Large-Scale Automated Analysis | High-volume, scalable malware processing with fast turnaround times. |
| Advanced Threat Detection & Targeted Attacks | Identifying sophisticated, long-term threats and custom attacks aimed at high-value targets. |
| Enterprise Endpoint Protection | Continuous monitoring and malware detection across distributed endpoints. |
| Forensic Malware Research | Detailed reverse engineering and in-depth malware analysis for security research. |
| Cloud-Native Threat Detection | Seamless cloud integration for automated, large-scale threat detection. |
Key Takeaways
For organizations looking to implement comprehensive malware analysis, the choice of sandbox will depend on their specific needs, whether it’s the scalability of cloud-native solutions, the security of appliance-based tools, or the stealth of hypervisor-based detection. Regardless, sandboxing remains a vital tool for both immediate malware detection and deeper forensic analysis. The race to outsmart malware continues, and sandboxes are leading the charge.
Sandboxing has evolved to combat increasingly evasive malware
Early sandboxing relied on basic API hooking and kernel monitoring, which proved ineffective against sophisticated malware. Modern sandboxes incorporate hybrid analysis and emulation to detect even highly obfuscated threats.
Adaptive and hybrid sandboxes are essential for advanced threat detection
By combining static and dynamic analysis, along with emulation and AI-driven insights, today’s sandboxes can analyze complex threats such as ransomware, zero-day exploits, and advanced persistent threats more effectively.
Sandboxing solutions vary by deployment needs
From on-premises appliance-based sandboxes for air-gapped environments to cloud-native, API-driven platforms for large-scale threat detection, organizations should select sandboxing technologies that align with their specific security requirements.
The Future of Sandboxing
Modern sandboxing technologies have evolved far beyond their initial iterations, combining virtualization, hybrid analysis, and emulation to handle increasingly sophisticated threats. As malware authors continue to refine their tactics, the next step in sandbox evolution will likely involve even more AI-powered detection and adaptive learning systems to stay ahead of the curve.
Experience this technology for free on its community site: www.filescan.io
Jan Miller is a cybersecurity expert with over a decade of experience in malware analysis, sandboxing technologies, and hybrid threat detection methods. He is the founder of Payload Security, the company behind VxStream Sandbox, which was later acquired by CrowdStrike and evolved into Falcon Sandbox. Jan’s innovative work in hybrid analysis has set the standard for modern sandboxing, combining both static and dynamic approaches to malware detection.
Currently, he works at OPSWAT as a Chief Technology Officer, where he focuses on advancing sandboxing technologies for critical infrastructure and high-security environments.

