Creating a list of the most destructive, dangerous, or impactful malware is a difficult endeavor. Much of the challenge is that there is not a universal benchmark for what “most destructive malware” means. If we are talking about the destruction of hardware, it’s a short list. If “destructive” includes factors such as data loss, financial loss, bankruptcy, harm to brand reputation, etc. the list is quite large. The next challenge is choosing whether damage is measured by financial impact, the number of computers infected, etc. What about malware that inspires new types of attacks? Due to the subjective nature of a top ten list, we will mix and match a number of criteria. Let’s start with a trip down memory lane and include some “blasts-from-the-past.” How many of these famous threats do you remember?
1. The Morris Internet Worm – 1988
Guess what? The worm only ran on UNIX, but so did most of the internet. The worm exploited multiple vulnerabilities for which there were patches, as well as exploiting weak passwords. Have we learned nothing since 1988? The author, Robert Morris, did not intend for the worm to be as destructive as it was, but he underestimated the power of his replication algorithm. The worm infected at least 2,000 computers in 15 hours and disinfection could take up to a couple of days. It is estimated that the worm infected 10% of all internet connected computers. Robert Morris became the first person to be convicted of a felony under the 1986 Computer Fraud and Abuse Act, but worst of all for Morris, his dad who was a cryptographer working for the NSA, found out. Ouch!
2. Concept Macro Virus - 1995
Concept is the first in-the-wild macro virus. After trying to warn Microsoft that macro viruses could be written for Microsoft Word, the author, presumed to be working at Microsoft, wrote the virus. Upon infection, Concept displayed “1” in a message box. A remark in the code reads “That’s enough to prove my point.” Concept went viral, so to speak, when Microsoft distributed it on CDs that were shipped around the world. Concept ushered in the age of macro mayhem. According to Virus Bulletin’s May 1999 virus prevalence report, macro viruses accounted for 90% of all reported infections. One such infected document came to me in an invoice from an antivirus company!
3. CIH Virus - 1998
The CIH virus, also known as the "Chernobyl virus", was named after the initials of the author of the worm, Chen Ing Hau. When the media realized the detonation date of CIH coincided with the anniversary of the Chernobyl disaster, they seized the opportunity to sensationalize its name.
CIH was the first in-the-wild virus to actually damage hardware. On some computers CIH would overwrite the BIOS. In many cases the entire motherboard had to be replaced. For computers that did not have a vulnerable BIOS, the virus still overwrote the first megabyte of the boot drive, resulting in data loss and rendering the computer unbootable. CIH became part of a supply chain attack as thousands of IBM Aptiva computers shipped with CIH pre-installed, as did software from a number of sources. Estimates place the cost of the damage inflicted as high as $1B USD, with an estimated 600,000 infections in South Korea and Turkey alone. Chen Ing Hau never faced criminal charges, however for his ability to destroy computers across the globe a now defunct Taiwanese company hugged Chen and then gave him a job.

4. Melissa Macro Virus/Worm - 1999
Due to Melissa’s ability to spread through infected documents and through email, Melissa was both a virus and a worm. Written by David Lee Smith, who would later go to jail for his work, Melissa became the most rapidly spreading viruses of the time and inspired future mass-mailing malware. Causing an estimated $80M USD, Melissa was a data stealing virus as well. Melissa infected normal.dot which then resulted in the infection of every document that was subsequently opened. Upon opening an infected document, Melissa sent that document to the first 50 entries in the Outlook address book. Should a distribution list be one of the entries, Melissa could easily be sent to hundreds or even thousands of people at once. An off-spring of the Concept macro virus, Melissa was a trend-setter in her own right. Trivia: Melissa was reportedly named after a stripper in Florida. Given the fact that Melissa first surfaced on the Usenet alt.sex forum, it’s plausible that it was.
5. Code Red Worm - 2001
There are scores of macro viruses that deserve honorable mention, but let’s give other types of threats their due credit. Code Red was a computer worm that exploited a buffer overflow vulnerability in Microsoft IIS web servers. The worm infected well over 360,000 computers in one day alone. The worm was first discovered by two eEye Digital Security employees and was named for the Code Red Mountain Dew they were drinking when they discovered it. The estimated $2.6B of damage Code Red caused in 2001 was equal to approximately $4B in purchasing power in 2017. WannaCry is estimated to have inflicted less than $4B damage in 2017.
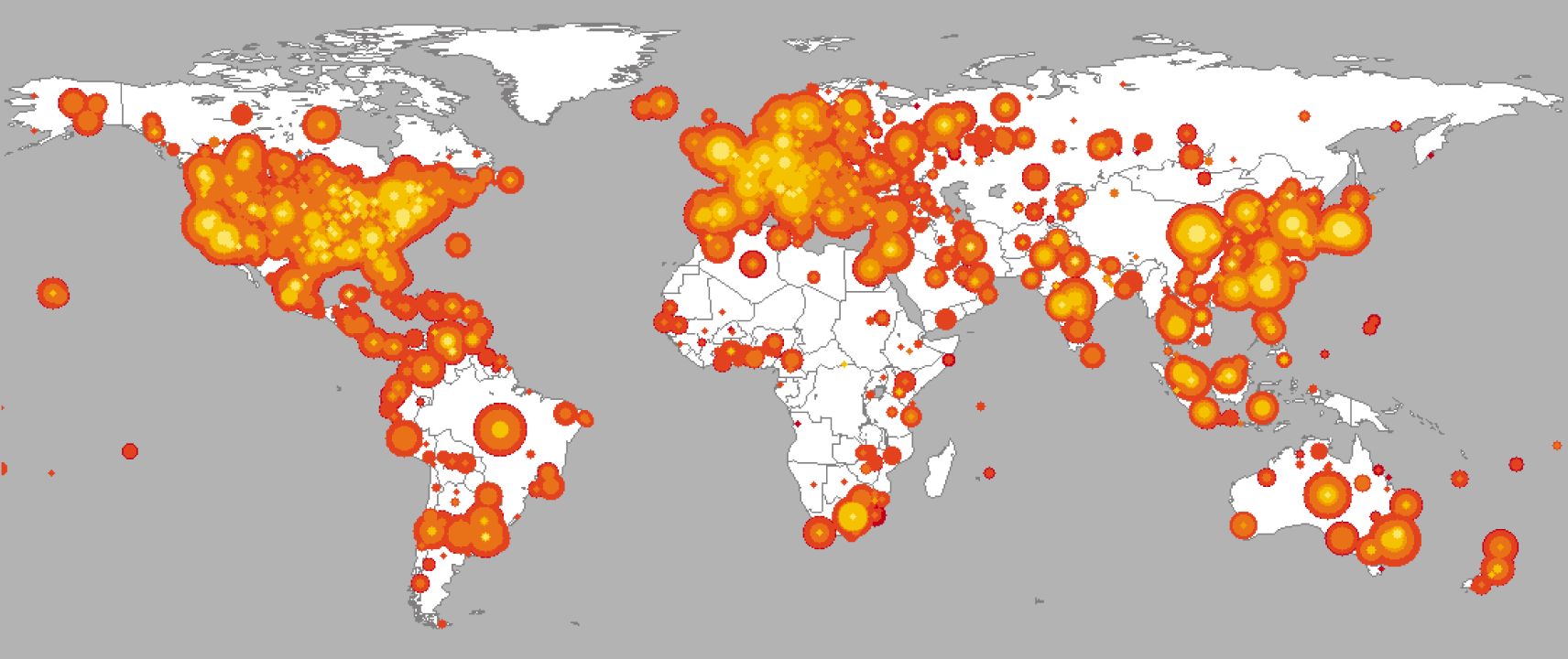
Spread of the Code Red worm from Caida
6. Slammer Worm - 2003
In January of 2003, the Slammer worm struck 75,000 users with a DoS attack. The worm targeted a vulnerability found in Microsoft SQL and spread rapidly. Owen Maresh of Akamai is credited with being the first person to discover the destructive worm from Akamai's Network Operations Control Center. At its height, the Slammer Worm sent 55 million database requests across the globe and is said to have spread within just 15 minutes, surpassing the speed of the Code Red Worm from 2001.
7. SoBig.F Worm - 2003
The SoBig.F Worm was a piece of malware that appeared only a few weeks before the Slammer worm mentioned above. The SoBig.F worm entered a device via email, which if opened could search the infected computer for additional email addresses and then send messages to those contacts. The worm caused $37.1 Billion in damages and is credited with bringing down freight and computer traffic in Washington D.C, as well as Air Canada. Email subject lines used to entice users included, "Your details, Thank you!”, "Re: My details" and various others. The speed at which the worm spread is said to surpass that of the ILOVEYOU virus and Anna Kournikova worm, both of which also spread via email. The worm's creator still remains unknown.
8. MyDoom Worm - 2004
The MyDoom worm, known as one of the fastest spreading pieces of malware in history, passed both the ILOVEYOU bug and SoBig worm in speed. It was transmitted via email and usually contained a variety of subject lines including, "Error", "Mail Delivery System", "Test" or "Mail Transaction Failed". Though its creator still remains unknown, some speculate that it originated in Russia. The worm was first discovered and named by an employee at McAfee for the line, "mydoom" that appeared in its code. MyDoom remains active in the wild.
9. Conficker Worm 2008
Conficker, still alive and well today, may very well be the most persistent threat of all time. Conficker spread through removable media on systems that had autorun enabled (virtually every Windows computer did), and/or by exploiting a Windows vulnerability, and by exploiting weak passwords to spread across networked computers. Conficker found its way into military and manufacturing systems, as well as the healthcare industry. In 2016 Conficker found its way into a German Nuclear facility. A 2016 report by TrapX details targeted attacks against three hospitals. Conficker variants have been used to target networked medical devices in order to perform lateral movement across networks. TrapX was still seeing Conficker infections in 2019. According to Trend Micro Conficker accounted for 41% of all detections in 2017. In 2028 the world will celebrate Conficker’s 20th birthday and no doubt the worm will be an uninvited guest at somebody’s party.
Conficker prompted the creation of the Conficker working group (CWG), a consortium of companies including Microsoft, Facebook, Cisco, IBM, Verisign, and several anti-malware companies, to try to contain the botnet. In order to do so the CWG had to proactively register 50,000 domains each day. In 2011 the CWG released a 50-page report of lessons learned from Conficker. Although the CWG website is no longer live, the document is still available through archive.org.
10. WannaCry NotPetya - 2017
WannaCry didn’t stay on the list very long. The discovery of a “kill-switch” cut its life short, and the damage caused by NotPetya eclipsed WannaCry. NotPetya pretended to be ransomware, however in reality it wiped files by encrypting the MBR. There was no decryption key, and money is not believed to be a motive for the malware. Believed to be a Russian attack against the Ukraine, NotPetya quickly went global. When shipping giant Maersk fell victim to NotPetya, close to one fifth of the worlds shipping capacity was halted. While the estimated cost $300,000,000 to Maersk was painful, the estimated cost of NotPetya to pharmaceutical giant Merck is estimated at $870,000,000. Striking everything from critical infrastructure to candy manufacturer Mondelez, NotPetya is estimated to have caused $10 billion of damage and is often touted as the most destructive malware of all time.
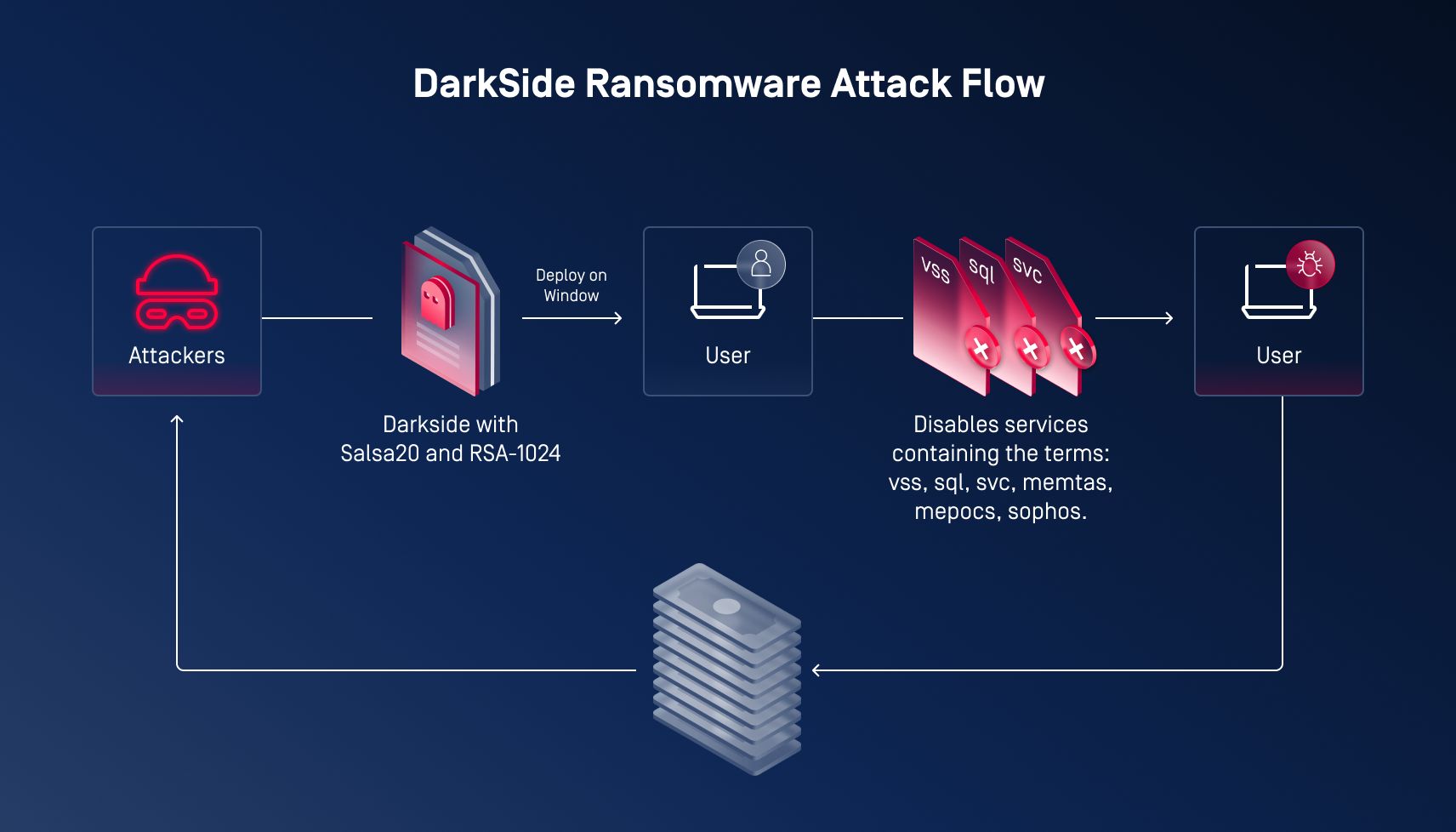
11. DarkSide Ransomware - 2021
DarkSide is a ransomware threat that emerged in August 2020 and gained notoriety for its role in the Colonial Pipeline cyberattack, which caused a significant fuel disruption along the U.S. East Coast. Operated as a ransomware-as-a-service (RaaS), DarkSide employs double extortion tactics, combining file encryption with data theft to pressure victims into paying ransoms. The group, believed to have ties to Russian cybercriminals and former REvil affiliates, initially ran its own attacks before franchising its ransomware to other cybercriminals via underground forums. Despite branding itself as an ethical ransomware group that avoids targeting certain organizations, evidence suggests that DarkSide’s claims are deceptive, as they have pressured schools and engaged in high-profile extortion attempts.
DarkSide affiliates infiltrate networks using stolen credentials, exploiting vulnerabilities in remote access software, and leveraging penetration testing tools for lateral movement. Once inside, they disable backups, escalate privileges, exfiltrate sensitive data, and deploy ransomware in a coordinated attack. The malware uses strong encryption techniques and avoids systems in former Soviet Bloc countries. With features designed to attract affiliates—including Linux compatibility, built-in victim communication tools, and even DDoS capabilities—DarkSide has proven to be a formidable and sophisticated ransomware operation. However, its claims of ethical considerations and charitable donations remain unverified and are widely viewed as attempts to manipulate public perception.
12. Honorable Mentions
Perhaps you feel that an entry didn’t belong on the list. Everyone has valid reasons for disagreeing with entries in any top ten list, and that is to be expected. Top ten lists are among the top ten causes of disagreement.
That said, here are a few honorable mentions that didn’t make the list this time.
Mirai
Mirai malware infects Internet of Things (IoT) devices, is widespread, and is capable of launching highly disruptive distributed denial of service attacks. Were it not for the inclusion of historical malware, Mirai would make the list without even trying. Mirai has demonstrated the all-encompassing insecurity of the IoT. Note: The majority of secure IoT devices are owned by unicorns.
Emotet
Emotet is a potent banking Trojan that has evolved to OEM other malware as well. Emotet could arguably have been on the top ten list. Again, the inclusion of historical malware leaves no room on the list for some deserving malware.
Wannacry
Wannacry was a huge wake-up call for the healthcare industry, especially in the UK. The lessons taught by WannaCry may have been responsible for many companies avoiding infection by NotPetya. Unfortunately, some companies slept through the lesson and remained blissfully unaware of the danger, until NotPetya woke them up.
Stuxnet
Stuxnet was highly destructive… if you were Iran. Stuxnet caused catastrophic hardware damage to Iran’s nuclear program, but Stuxnet had safety mechanisms coded into it to assure that its payload was only for Iran’s SCADA systems. Although capable of spreading to Windows computers across the globe, Stuxnet was only dangerous to a handful of computers in the world. The reason that Stuxnet makes some top ten lists, and honorable mention here, is that it was a high-profile harbinger of cyber weapons to come.
13. How to Prevent Malware: The OPSWAT Solution
OPSWAT’s Metascan™ Multiscanning solution utilizes over 30 different antivirus engines to provide comprehensive scanning that can achieve over 99% detection. Deep CDR™ Technology disarms suspicious or out-of-policy content in over 180 file types and regenerates new, safe-to-use files. It goes beyond traditional CDR solutions by recursively sanitizing archive file formats, like Microsoft Office documents and PDFs.
For the best all-in-one platform containing all of OPSWAT’s file security solutions and technologies, check out MetaDefender Core.