Technology and convenience often go hand in hand, but that means that something as commonplace as a USB drive can be a gateway for cybercriminals. Recent reports from The Hacker News have brought attention to a sophisticated attack targeting Italian businesses across sectors like healthcare, transportation, construction, and logistics. The culprit behind these attacks is believed to be UNC4990, a financially motivated threat actor group that has honed its skills in deploying USB-based attacks to steal sensitive data.
The Attack
The attack on Italian businesses reportedly involved the use of weaponized USB drives, a tactic that underscores the persistent vulnerability of endpoint devices. These malicious USB drives are suspected of carrying malware capable of stealing critical and sensitive information, including credit card and social security numbers. Once plugged into a device, the malware can quickly spread through an organization's network, compromising data and potentially causing significant financial damage.
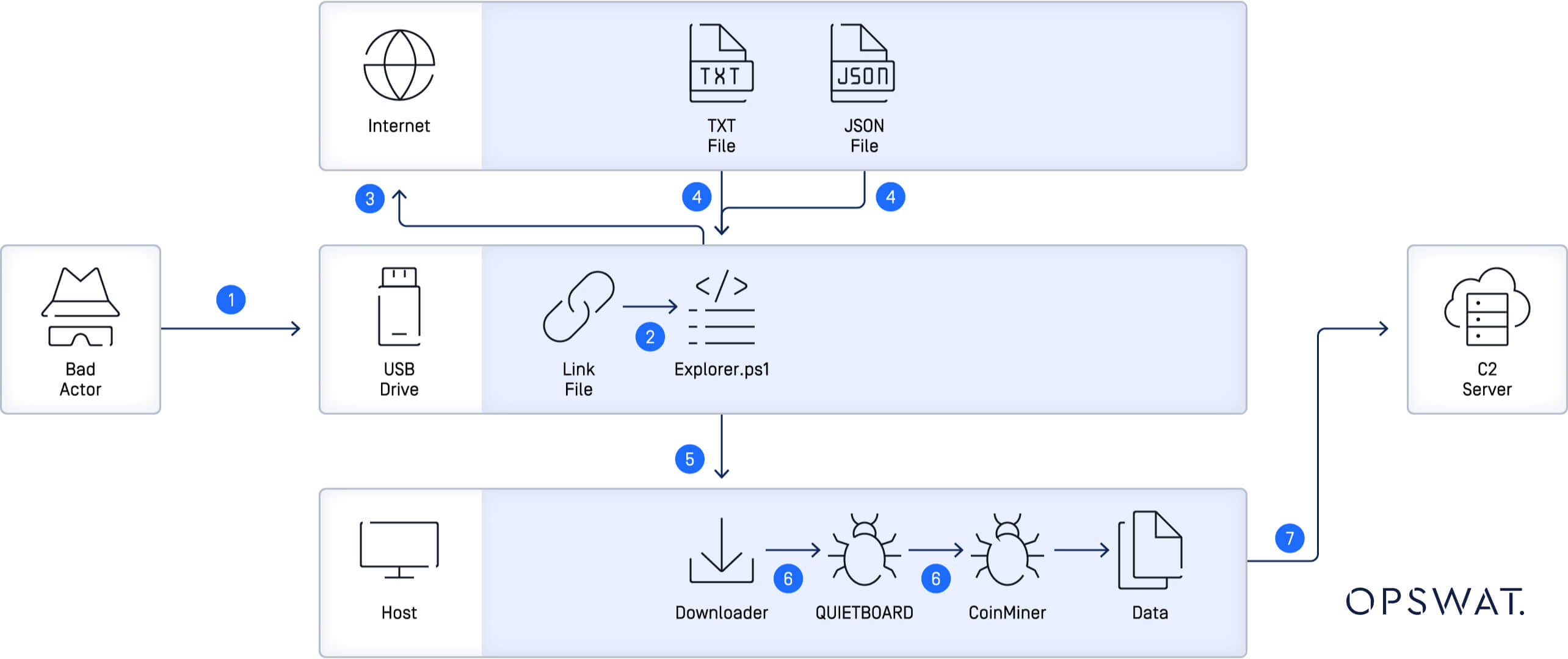
The use of USB drives in these attacks is not new, but the precision and sophistication with which UNC4990 operates signals an evolution in tactics. By using USB devices as the initial infection vector, UNC4990 exploits the often-overlooked security gaps in endpoint protection. Their modus operandi includes using encoded text files hosted on legitimate platforms like GitHub and Vimeo to deliver malicious payloads, making detection and mitigation more challenging.
UNC4990
UNC4990 has been active since at least 2020, primarily targeting users in Italy. Over time, they have refined their approach, leveraging advanced backdoors like QUIETBOARD and EMPTYSPACE to infiltrate and persist within targeted networks. This group’s focus on industries like healthcare and transportation, where disruption can have widespread consequences, highlights that comprehensive cybersecurity measures are more critical than ever.
The use of USB devices as an infection vector is particularly concerning because it bypasses many traditional security measures. UNC4990’s ability to adapt and utilize everyday tools like USB drives as weapons speaks to their sophistication and the evolving nature of cyberthreats.
Mitigating USB-Borne Threats with MetaDefender Endpoint
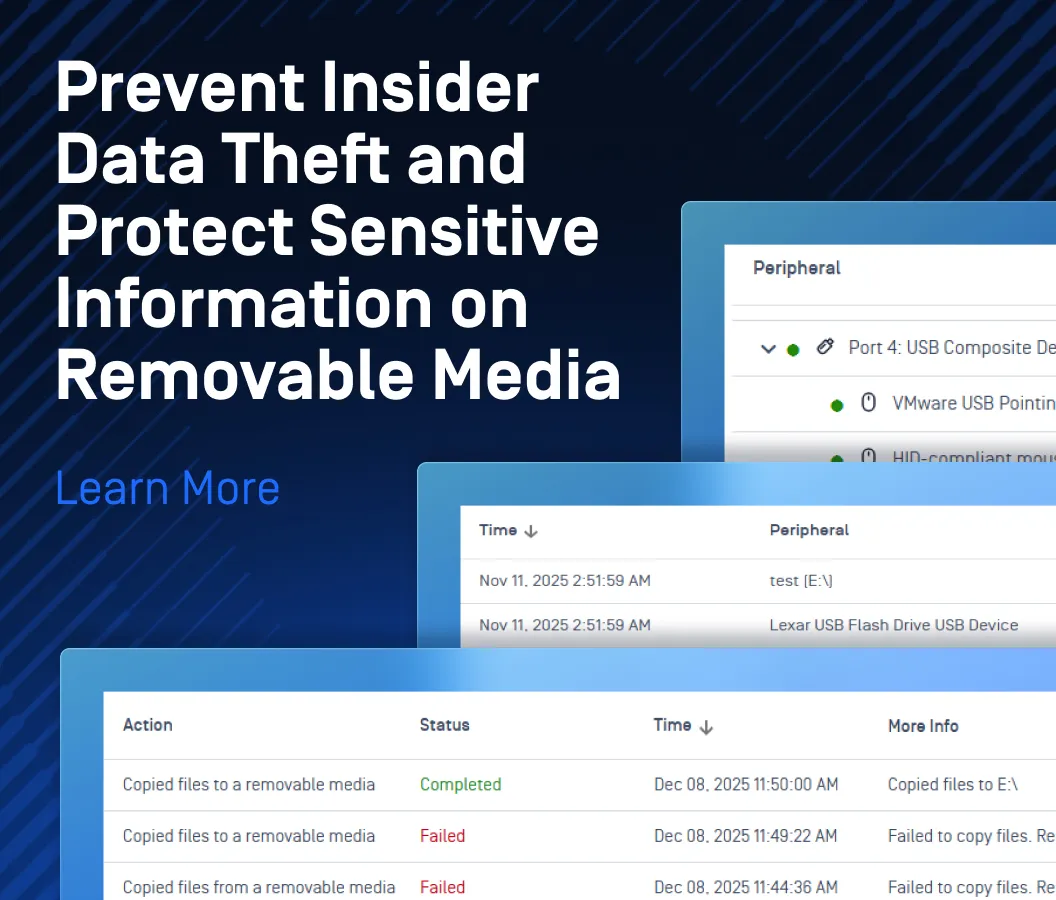
Protection from USB-Borne threats isn't important—it’s essential. OPSWAT’s MetaDefender Endpoint client offers a powerful defense against USB-borne threats, ensuring that malicious content on peripheral devices is detected and neutralized before it can compromise an organization’s systems.
MetaDefender Endpoint stops threats that traditional cybersecurity methods miss, providing comprehensive threat prevention by scanning and sanitizing USB devices in real-time, blocking potentially harmful files before they can be accessed.
Powered by industry-leading technology like Deep CDR™ TechnologyTM, Sandbox, and Multiscanning with up to 30 leading antivirus engines to stop known and unknown threats, this proactive and multifaceted approach is critical in environments where the use of external devices is unavoidable. By implementing MetaDefender Endpoint, businesses can significantly reduce their risk of falling victim to attacks like those perpetrated by UNC4990.
Preventing Future Attacks
The recent USB-based attacks on Italian businesses are a stark reminder of the vulnerabilities that exist at the endpoint level. As threat actors like UNC4990 continue to refine their tactics, the need for comprehensive and proactive security measures becomes continuously more urgent. By leveraging solutions like OPSWAT’s MetaDefender Endpoint, organizations can protect themselves from the growing threat of USB-borne malware and ensure their critical data remains secure.
MetaDefender Endpoint is just a piece of OPSWAT’s larger peripheral media protection strategy—talk to an expert today for a free demo and discover the critical advantage in the fights against cyberthreats.