- The Problem Behind the Noise
- When Sandboxing Becomes the Bottleneck
- Smarter Sandboxing: Emulation, Not Emulation of Effort
- The Four Layers of Smarter Detection
- Threat Reputation - The Great Filter
- Dynamic Analysis - The Emulation Advantage
- Threat Scoring - Context That Cuts Through the Clutter
- Threat Hunting - From Detection to Insight
- Breaking the Alert Fatigue Cycle
- Lessons from the Field
- The Human Element: Empowering Analysts, Not Replacing Them
- Beyond the SOC: Scaling Without Losing Control
- Why This Matters Now
- The Takeaway
If you've ever sat through a night shift in the SOC, eyes burning from dashboards that never stop blinking, you know the drill. Hundreds of alerts pour in. You triage one, two, a dozen, then another hundred replace them. You silence what you can, escalate what you must, and hope none of the ones you ignored were the one.
Welcome to the modern SOC bottleneck: an ecosystem drowning in data but starved for clarity.
The Problem Behind the Noise
Most teams don't suffer from a lack of visibility. If anything, we're oversaturated with it. AV engines, EDRs, SIEMs, email gateways, all shouting for attention. But detection alone isn't the issue. It's confidence. The key questions to answer are:
- Which of these alerts are false positives?
- Which are real?
- And which are quietly hiding something new, something our tools don't yet recognize?
That last category, the evasive, never-before-seen malware, is the one that keeps analysts awake.
When incident response teams trace post-breach forensics, they often find that the malicious file had already touched the environment days or weeks earlier. It wasn't flagged as malicious because, at the time, no one knew it was. That's the zero-day gap, the blind spot between what's known and what's actually dangerous.
Traditional sandboxes were supposed to solve this. But as anyone who's managed them knows, most of those systems quickly became part of the bottleneck themselves.
When Sandboxing Becomes the Bottleneck
In theory, sandboxing is simple: detonate suspicious files in a safe environment, watch what they do, and decide if they're malicious.
In practice, many SOCs discovered a different story:
- Performance hits - VM-based sandboxes take minutes per file and eat compute like candy. Multiply that by tens of thousands of daily submissions, and throughput collapses.
- Evasion tactics - Modern malware knows when it's being watched, checking system locales, timing loops, and virtualized CPU artifacts to stay dormant.
- Operational drag - Managing multiple virtual images, patching environments, and chasing false negatives creates more admin work than security value.
As one analyst joked, "By the time my sandbox finishes detonating a sample, the attacker's already on LinkedIn bragging about it."
This is where the smarter approach in the form of emulation-based sandboxing starts changing the game.

Smarter Sandboxing: Emulation, Not Emulation of Effort
Instead of relying solely on virtual machines, emulation runs files at the instruction level-mimicking the CPU and operating system directly.
That subtle difference changes everything.
Because there's no full VM to spin up, analysis is lightning fast, in seconds, not minutes. As malware can't fingerprint the environment, it behaves naturally. And because the sandbox dynamically adapts to what it sees, you get real behavioral intelligence rather than just static verdicts.
The best part? This approach doesn't just stop at one layer of analysis. It feeds into an intelligent multi-layer detection pipeline, a framework that works more like an analyst's brain than a machine's script.
The Four Layers of Smarter Detection
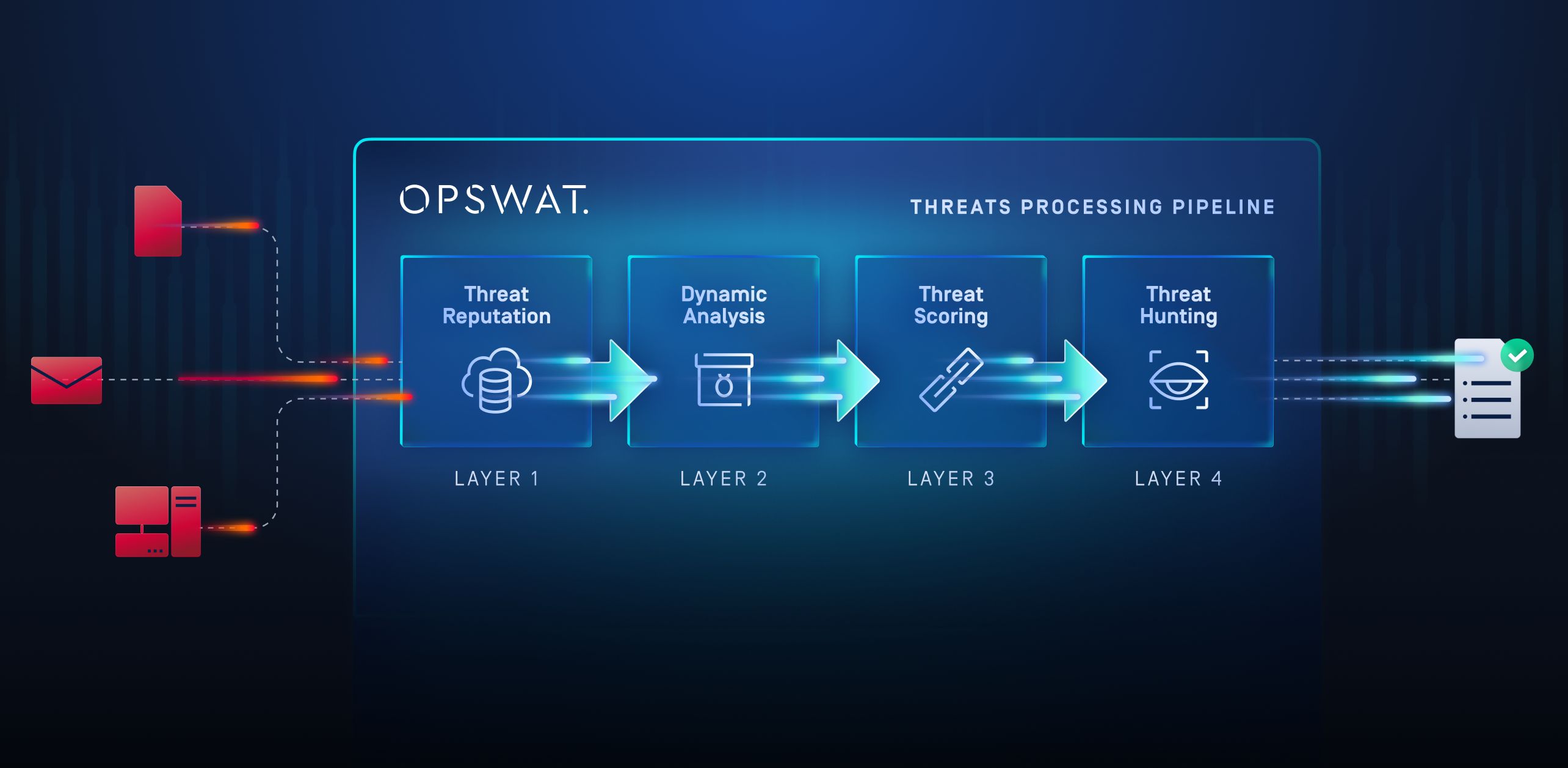
1. Threat Reputation - The Great Filter
Every SOC starts with triage. Reputation services play that same role at scale.
Instead of detonating everything, the system first checks URLs, IPs, and file hashes against global intelligence feeds. Billions of indicators are correlated in real time, allowing 99 percent of common, known threats to be filtered out instantly.
That's your noise reduction layer, the digital equivalent of a seasoned Tier 1 analyst who says, "Don't bother, we've seen that one before."
Only the suspicious, unknown, or borderline cases move on to deeper scrutiny.
2. Dynamic Analysis - The Emulation Advantage
This is where the magic happens.
Once filtered, files enter a dynamic analysis stage powered by instruction-level emulation, not virtualization. The sandbox can simulate different OS locales, bypass geofencing checks, and force malware to execute behaviors it would otherwise hide.
Every instruction is observed: registry writes, process spawns, memory injections, network calls. The result is not a guess or a signature match; it's direct behavioral evidence.
It's the digital equivalent of watching a suspect's hands instead of just checking their ID.
For the SOC, this means fewer missed threats and faster verdicts without throttling performance. A single high-performance sandbox server can process tens of thousands of samples per day, no server farm required.
3. Threat Scoring - Context That Cuts Through the Clutter
Raw detections alone don't help an overwhelmed analyst. What matters is priority.
This layer uses adaptive threat scoring to assign meaningful severity based on behavior and context.
- Did the file drop a PowerShell script?
- Attempt C2 communication?
- Inject into explorer.exe?
Each behavior adjusts the score dynamically.
By blending sandbox results with reputation and intelligence data, SOC teams gain triage clarity. Now you can focus on the handful of high-risk alerts that truly deserve investigation, reducing alert fatigue without sacrificing visibility.
Threat scoring transforms "thousands of alerts" into a digestible to-do list. The noise becomes narrative.
4. Threat Hunting - From Detection to Insight
Once you know what's dangerous, the question becomes: Where else does it live?
Here, machine learning comes into play through threat similarity search. The system compares new samples to known malicious families, even if code, structure, or packing differ. It's pattern recognition at scale: spotting relationships, variants, and shared TTPs that traditional tools miss.
For threat hunters, this is gold. A single sandbox detection can trigger retro-hunts across terabytes of historical data, uncovering other infected assets or related campaigns. Suddenly, detection turns into proactive defense.
Breaking the Alert Fatigue Cycle
Most SOCs don't lack data, they lack correlation.
The smarter sandbox model integrates all four layers into one continuous flow, where each stage refines the next. Reputation reduces volume, emulation reveals behavior, scoring adds context, and hunting turns that context into action.
This layered approach does more than accelerate response times-it changes the daily rhythm of the SOC.
Instead of chasing false positives, analysts spend time understanding genuine threats. Instead of endless triage, they can trace attack chains, map MITRE ATT&CK techniques, and feed those insights back into their SIEM or SOAR platforms.
The result: fewer pings, richer signals, and a team that can finally breathe between alerts.

Lessons from the Field
In practice, I've seen three consistent outcomes when SOCs deploy this smarter model:
- Detection Accuracy Climbs. Behavioral analysis catches what static defenses miss, especially obfuscated scripts and weaponized documents.
- Investigation Time Shrinks. Automated context and scoring reduce "time-to-verdict" by up to 10× compared to legacy VM sandboxes.
- Operational Load Drops. A single emulation node can process 25,000+ analyses per day with 100× less resource overhead, meaning fewer bottlenecks and lower cost per sample.
For one financial institution, integrating this model into their email and file transfer gateways turned previously manual triage into automated confidence. Suspicious attachments were detonated, scored, and logged with clear verdicts in minutes. Their SOC no longer needed to babysit every incident queue, the data spoke for itself.
The Human Element: Empowering Analysts, Not Replacing Them
Technology alone doesn't fix alert fatigue, context does.
When your sandboxing system provides explainable results, "this document launches a hidden VBA macro that downloads an executable from a C2 in Poland", it empowers analysts to make faster, better decisions.
It's not about automation for automation's sake. It's about giving Tier 1 the power of Tier 3 insight.
With detailed behavioral reports, MITRE ATT&CK mapping, and extractable IOCs, every detection becomes an investigation accelerator. Analysts can pivot through incidents, enrich SIEM data, or export structured indicators to MISP or STIX. The sandbox becomes part of the workflow, not another silo.
And that's how you actually break the bottleneck: not by adding another tool, but by making the existing ones smarter together.
Beyond the SOC: Scaling Without Losing Control
Modern security teams operate across hybrid, cloud, and air-gapped environments. Smarter sandboxing adapts accordingly.
On-premises or air-gapped deployments keep critical data isolated but still benefit from the same emulation and scoring logic.
Cloud-based deployments scale dynamically, processing thousands of submissions per minute with global threat intelligence correlation.
Hybrid configurations sync results across both, sharing verdicts, reputations, and IOCs so insights travel faster than the threats do.
No matter the architecture, the goal remains the same: consistent detection fidelity across every file, every workflow, every perimeter.
Why This Matters Now
Evasive malware isn't slowing down. In the past year alone, 2025 OPSWAT Threat Landscape Report data from over a million scans showed a 127 percent increase in malware complexity, and 1 in 14 files labeled "safe" by OSINT turned out malicious within 24 hours.
That's the reality of the modern SOC. The threats evolve hourly; the tooling must evolve faster.
Smarter sandboxing closes that window, shifting zero-day detection from reactive forensics to proactive prevention.
It's the bridge between detection and intelligence, between the avalanche of alerts and the handful that truly matter.
The Takeaway
Alert fatigue isn't a people problem, it's a process problem.
By moving from isolated detection engines to an integrated, four-layer threat analysis pipeline, SOCs can reclaim focus, precision, and time.
The combination of fast reputation filtering, undetectable emulation, contextual scoring, and intelligent hunting transforms the sandbox from a performance drain into the SOC's sharpest instrument.
When that happens, the blinking dashboard stops feeling like noise and starts telling a story worth listening to.

