What is Centralized Security Management?
Centralized security management is a strategy that consolidates control of security tools, policies, and monitoring into one platform for greater consistency and visibility. It enables consistent policy enforcement, unified visibility, and streamlined threat response across an organization’s IT infrastructure. This approach replaces fragmented, siloed security tools with a unified security platform that provides comprehensive oversight and control.
- How Does a Centralized Security System Work?
- How Does Centralized Security Management Work?
- What are the Benefits of Centralized Security Management?
- Centralized vs. Decentralized Security Management
- How to Implement Centralized Security Management: Best Practices
- What’s Next for Centralized Security Management?
How Does a Centralized Security System Work?
A centralized security system operates on the principle of unified control and visibility. Unlike decentralized approaches where security decisions are made independently across different departments or systems, centralized network security management establishes consistent standards and protocols organization wide.
Centralized models offer stronger oversight and consistency, while decentralized models enable faster, team-level autonomy. Key differences include control, scalability, policy enforcement, user experience, and compliance readiness.
This system integrates multiple security functions including threat detection, incident response, compliance management, and policy enforcement under one umbrella. The result is a more coordinated and effective defense strategy that adapts quickly to emerging threats.
Key Components and Functionalities
Single-Pane-of-Glass Monitoring
Provides administrators with comprehensive visibility across all security tools and systems. This unified view eliminates blind spots and enables faster threat identification and response.
Policy Enforcement
Ensures consistent application of security standards across all endpoints, networks, and cloud environments. Centralized policy management eliminates configuration drift and maintains security integrity.
RBAC (Role-Based Access Control)
Implements granular permission systems that align with organizational hierarchies and responsibilities. This approach minimizes security risks while maintaining operational efficiency.
Unified Visibility
Extends beyond monitoring to provide contextual intelligence about security events, and system performance across the entire infrastructure.
How Does Centralized Security Management Work?
Instead of managing a patchwork of disconnected firewalls, antivirus software, and intrusion detection systems, a centralized model provides a unified view and control point.
- Integration with Existing Infrastructure: A powerful centralized management system can pull data from and push policies to a wide range of security tools, from endpoint protection to network firewalls. This eliminates security silos and creates a more robust defense.
- Automation and Orchestration: Once all tools are connected, the system can automate routine tasks and orchestrate complex responses to threats. For example, if a vulnerability is detected on one device, the system can automatically quarantine it and restrict the entire network access via NAC policies.
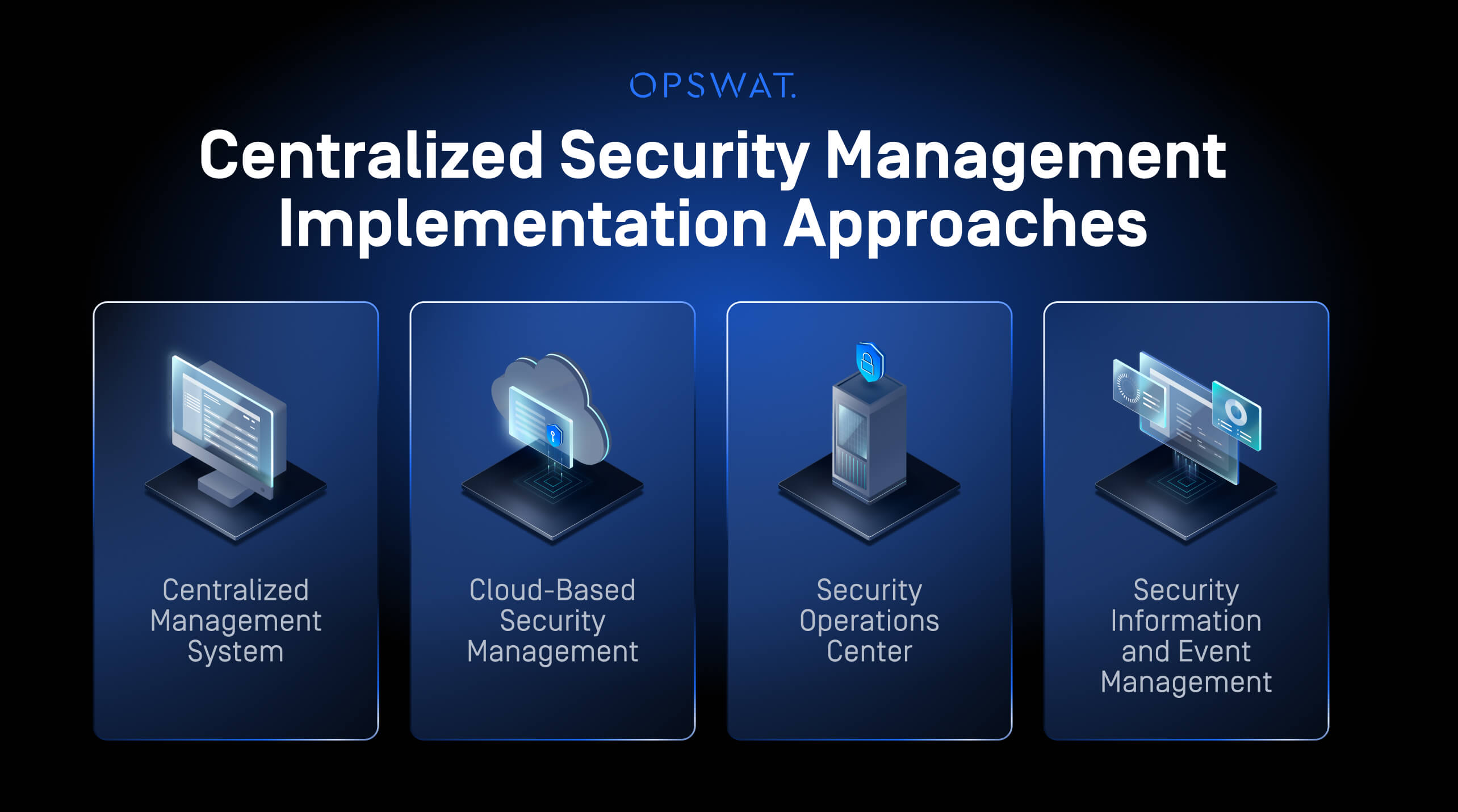
Implementation Approaches
Centralized security management can be implemented through a variety of systems and tools. Each approach serves a slightly different function but contributes to the overall goal of a unified security posture.
- CMS (Centralized Management System): This is the core of the strategy. A CMS provides a dashboard for monitoring and managing security devices and policies from a central location. It's the "brain" that connects and controls all other security components. A powerful CMS can pull data from and push policies to a wide range of security tools, from endpoint protection to centralized firewall management across network segments.
- Cloud-Based Security Management: This approach leverages scalable infrastructure to provide centralized oversight across distributed environments. This approach is particularly effective for organizations with remote workforces or multi-cloud deployments, offering secure data handling.
- SOC (Security Operations Center): An SOC is a dedicated team or facility that monitors and analyzes an organization's security posture. While a CMS provides the technology, the SOC provides the human expertise to interpret data, respond to incidents, and fine-tune policies.
- SIEM (Security Information and Event Management): A SIEM solution aggregates and analyzes security data from various sources to provide a real-time view of threats. It's a critical component for detecting anomalies and generating alerts that inform the SOC's response.
Unified Security Platforms
As data and infrastructure become more distributed across the globe, a centralized security management solution is the only way to ensure consistent security and control. By moving away from multiple, standalone solutions, organizations can avoid higher maintenance costs and operational complexity, and invest in a more efficient, resource-optimized system.
However, modern unified security platforms do more than consolidate tools; they deliver comprehensive, multi-layered protection across every attack vector. These platforms integrate with real-time threat intelligence feeds and advanced threat intelligence integration capabilities to defend against zero-day exploits, ransomware, and targeted attacks while extending protection from endpoints and file transfers to hardware supply chains, removable media, and file-based attack vectors.
Advanced platforms employ CDR (Content Disarm and Reconstruction) and multi-engine scanning to neutralize file-borne threats without disrupting workflows, while enforcing zero-trust access and compliance policies. Through centralized management, administrators deploy consistent rules across cloud, on-premises, dramatically reducing misconfigurations and systematically closing attack vectors before they can compromise critical infrastructure.
What are the Benefits of Centralized Security Management?
Centralized security management delivers measurable improvements in security effectiveness, operational efficiency, and regulatory compliance. Organizations implementing these systems typically see significant reductions in security incidents, faster threat response times, and improved compliance posture.
- Consistent policy enforcement: Ensures rules and access controls apply uniformly across all systems.
- Improved threat detection and response: Aggregated monitoring shortens detection times and speeds up containment.
- Streamlined compliance management: Centralized reporting simplifies audits and regulatory reviews.
- Enhanced security posture: Provides a stronger, more resilient defense by reducing blind spots.
Policy Enforcement and Access Control
Effective centralized access control systems implement sophisticated permission structures that balance security requirements with operational needs. These systems support complex organizational structures while maintaining strict security boundaries. Integrated Access Control mechanisms coordinate permissions across multiple systems and applications.
With RBAC, organizations can define roles once and apply them consistently across all systems, reducing administrative overhead and security risks. This approach minimizes security risks while maintaining operational efficiency, particularly when managing diverse endpoint environments across the organization.
Unified Monitoring and Incident Response
Centralized monitoring capabilities transform how organizations detect and respond to security threats. By aggregating data from multiple sources, these systems identify patterns and anomalies that might be missed by isolated monitoring tools.
Automated Incident Response workflows reduce response times and ensure consistent handling of security events. These systems can automatically isolate affected systems, collect forensic data, and initiate recovery procedures.
Integration with Defense in Depth strategies provides multiple layers of coordinated protection. Centralized management ensures that all security layers work together effectively rather than operating in isolation.
Centralized vs. Decentralized Security Management
Organizations face a fundamental choice in how they structure their security operations. This decision significantly impacts everything from operational efficiency and compliance posture to response times and resource allocation.
Centralized vs. Decentralized
Aspect | Centralized Management | Decentralized Management |
|---|---|---|
Policy Consistency | High | Variable |
Response Speed | Moderate - requires coordination | Fast - local decisions |
Resource Efficiency | High - shared resources and expertise | Lower - duplicated resources |
Scalability | Excellent - centralized infrastructure | Limited - depends on local resources |
Compliance Management | Simplified - centralized reporting | Complex - multiple compliance points |
Implementation Cost | Higher initial investment | Lower per-unit initial cost |
Visibility | Comprehensive across organization | Limited to local scope |
Flexibility | Lower - standardized approaches | Higher - customized solutions |
How to Implement Centralized Security Management: Best Practices
Successful implementation of centralized security management requires careful planning, stakeholder engagement, and phased deployment strategies. Organizations should begin with clear objectives, comprehensive asset inventories, and realistic timelines.
- Assess current tools and environments.
- Choose a platform that integrates with existing infrastructure.
- Define policies and automate enforcement where possible.
- Train staff on new workflows and access controls.
Organizations across industries have successfully implemented these practices, including leading game developers who secured proprietary code access through a centralized management system.
Policy Management and Automation
Effective security policy management balances security requirements with operational efficiency. Automated policy updates ensure consistent enforcement while reducing administrative overhead.
Automating Security Policy Updates enables organizations to respond quickly to new threats and regulatory changes. Automated systems can deploy policy updates across the entire infrastructure simultaneously.
Ensuring Consistent Enforcement across different environments requires careful attention to configuration management and policy translation. Centralized systems must account for environmental differences while maintaining security standards.
Integration with Compliance Standards
- Regulatory alignment: Delivers a comprehensive overview of all managed endpoints, highlighting alignment with key industry standards such as NIST, GDPR, CISA, HIPAA, and ISO 27001
- Streamlined reporting: Use centralized dashboards to generate audit-ready reports instantly.
What's Next for Centralized Security Management?
The future of centralized security management lies in increased automation, artificial intelligence integration, and adaptive security architectures. 61% of cybersecurity and IT professionals plan AI and machine learning adoption for security in the next 12 months, while global cybersecurity spending will grow 12.2% in 2025 and cross $377 billion by 2028. These investments reflect the urgent need for more sophisticated threat detection and response capabilities that reduce the burden on security personnel.
If your organization is ready to simplify operations, strengthen defenses, and stay ahead of compliance, explore how My OPSWAT Central Management can deliver secure, unified, and future-ready protection. Organizations seeking on-premises deployment benefits will find additional value in centralized control architectures.
Frequently Asked Questions (FAQs)
What is centralized security management?
Centralized security management is the practice of unifying control of security tools, policies, and monitoring under one platform. This improves visibility, policy consistency, and response time across IT environments.
What is a centralized security system?
A centralized security system is an integrated platform that manages firewalls, access controls, and monitoring tools from a single console. It enables unified oversight and coordinated threat response.
What are examples of centralized management?
Examples of centralized management include enterprise firewalls, SIEM platforms, and unified threat management systems. These tools centralize control, simplify administration, and improve overall security posture.
What tools are essential for effective centralized security management?
Essential tools include firewalls, SIEM and SOAR platforms, RBAC systems, and centralized compliance dashboards. These enable unified monitoring, access control, threat response, and policy enforcement.
What are the core principles of security management that can guide my organization?
Core principles include consistency, least privilege, automation, and defense in depth. These ensure strong, scalable security across diverse systems.
How can I stabilize, standardize, and optimize security management practices?
Adopt a centralized security platform, automate policy updates, and integrate compliance frameworks. This reduces risk and streamlines operations.
How do I implement a centralized security management system effectively?
Start by assessing current tools and infrastructure, then select an integrated platform. Automate policies and train staff to ensure smooth adoption.
What are the best practices for managing security across different business functions?
Use role-based access controls, automate updates, and monitor activity from a centralized dashboard. This ensures consistency and reduces errors.
How can we enhance security compliance and risk management within our organization?
Centralize reporting, align with industry frameworks, and run continuous audits. These steps improve compliance and reduce risk exposure.
What guidance is available for developing a strong security policy?
Follow established frameworks like NIST and ISO, tailor controls to your industry, and enforce policies consistently through centralized management.
How can we improve our incident response and recovery in security management?
Automate response playbooks, centralize threat monitoring, and coordinate actions across layers using defense-in-depth strategies.
What are effective strategies for managing security roles in a growing organization?
Implement RBAC, automate access provisioning, and review user privileges regularly. This reduces insider threats and access mismanagement.
How do security frameworks relate to regulatory and compliance requirements?
Security frameworks like NIST, CIS, and ISO map directly to regulatory controls, helping streamline audits and demonstrate compliance readiness.
Why choose My OPSWAT for centralized security management?
My OPSWAT offers a unified platform that integrates advanced threat detection, streamlines compliance, and simplifies security operations across hybrid environments.

