SMB Compatible NAS Storage Security
How do you ensure enterprise data storage security for any high-volume NAS platform?
It is now possible to integrate MetaDefender Storage Security with any SMB-Compatible storage to provide multi-AV scanning, data sanitization, and other advanced vulnerability assessment and threat prevention benefits. Advanced encryption support is also available via SMB v3.1.1.
This allows you to employ the following best practices for SMB compatible NAS
Run periodic scans on your entire storage by scheduling automated processes.
Typically, it takes 6-9 months for organizations to even detect a data breach [1]- as demonstrated very dramatically in the famous 2020 Sunburst attack on SolarWinds and it’s 18,000 Orion customers.
Hackers do not make their presence known right away. Once they find a loophole to bypass your security perimeter, they will try to infiltrate further and gain more privileged access to collect more data and information.
Malicious code is often introduced via legitimate scripts (for example in Office Documents or productivity files) that reach out later to Command & Control servers to download malware.
Malware that employs timing-based evasive tactics bypasses even the most sophisticated sandboxes.
By periodically processing your entire SMB compatible NAS storage, you can catch any latent outbreaks early and limit damage.
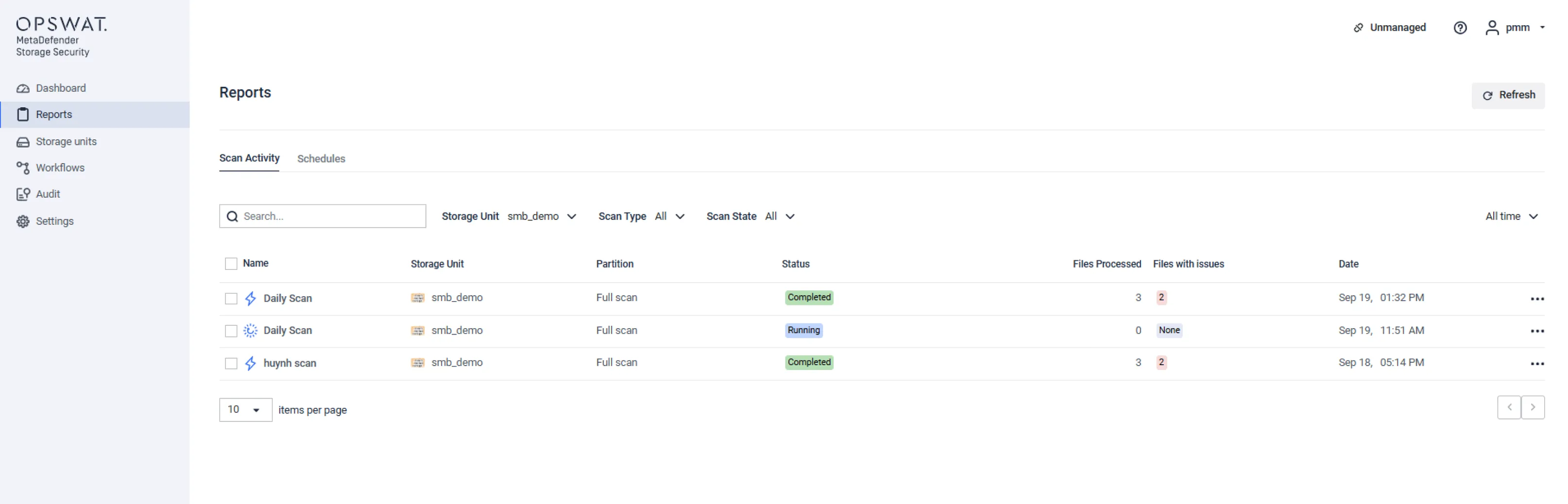
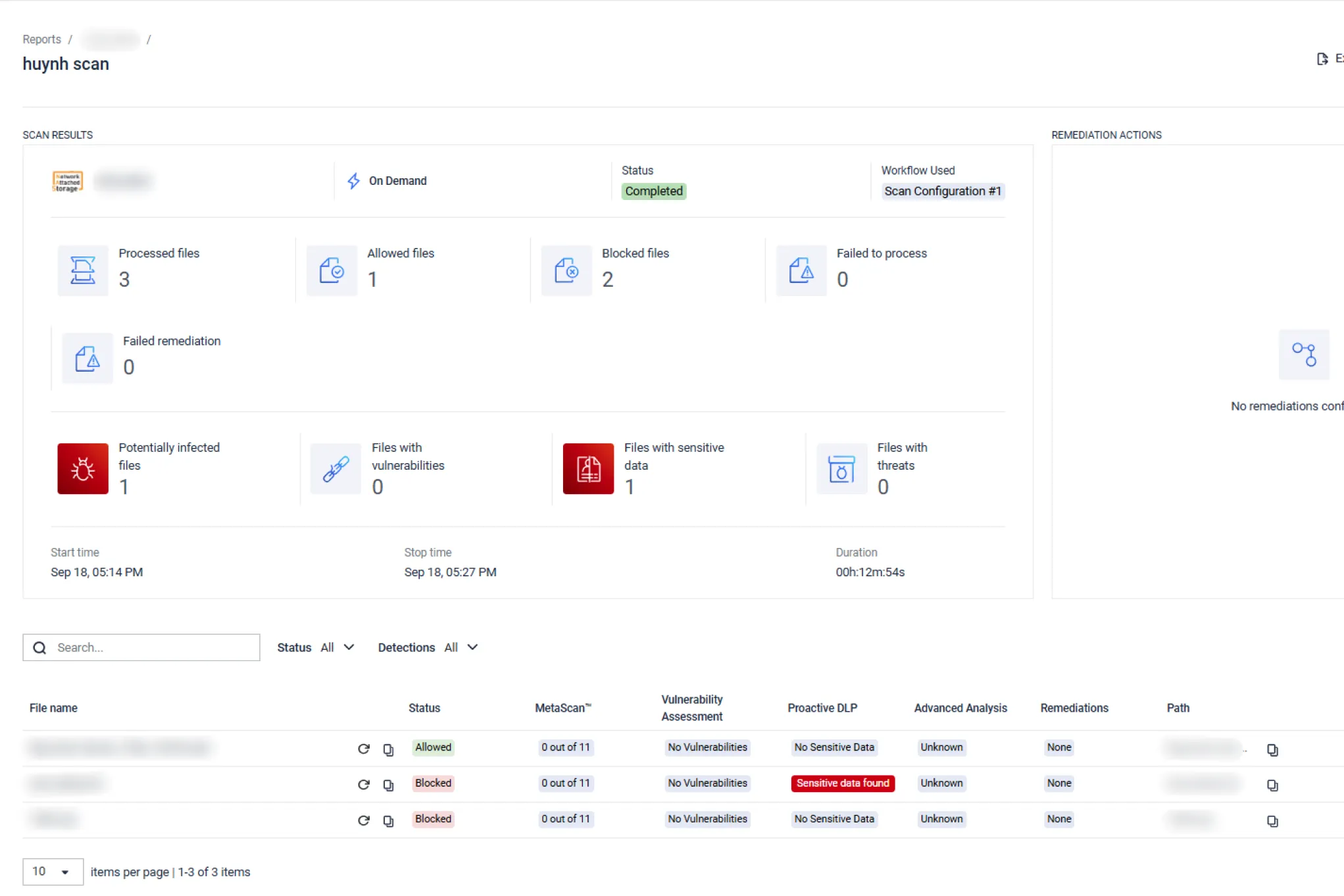
Instant Scan for suspected infections.
If you suspect your storage might have been compromised, kick off instant processing right away. In case there was a breach - the sooner you respond, the more money you can save [2]. In case there wasn’t – the sooner you know, the sooner you can go back to normal operations and minimize productivity loss for your workforce.
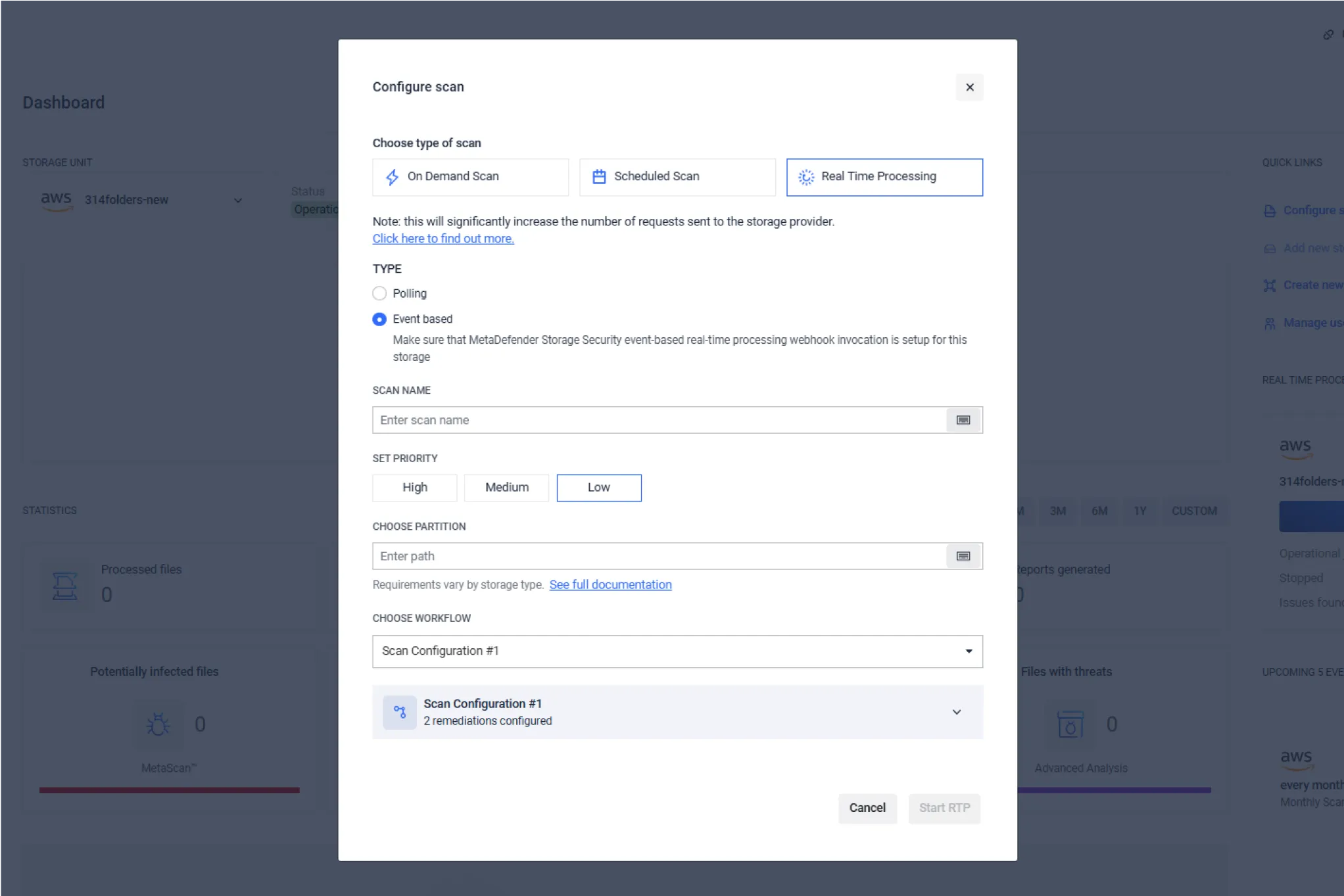
Scan real-time for new and modified files.
Users uploading files could have been hacked or might be using a system that is compromised. Often, attackers maintain persistence on machines with the intent to use them to come back to networks [3].
To ensure newly uploaded files do not introduce a threat inside your secured storage, make sure you process any new file as soon as it is uploaded by enabling real time processing.
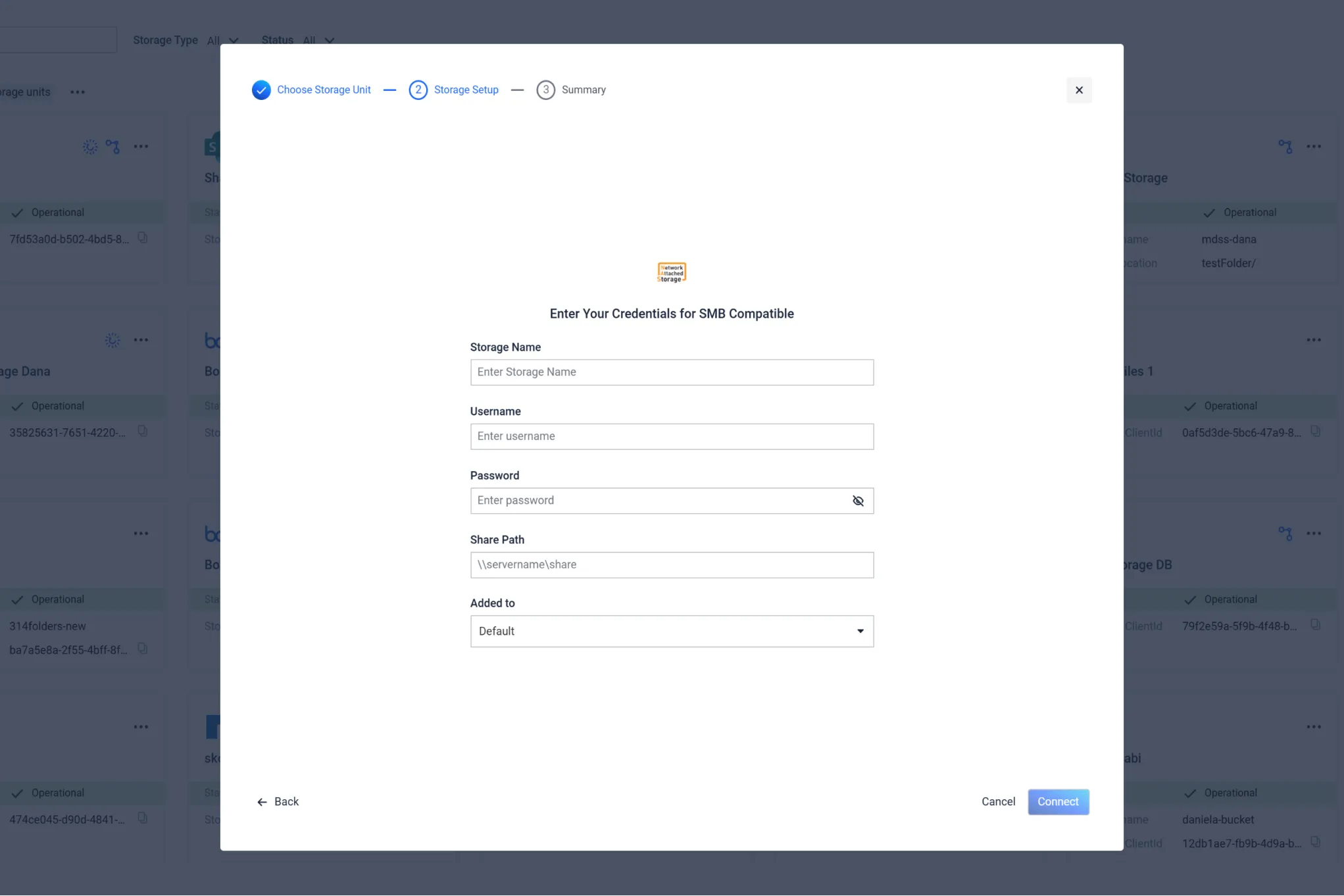
Adding a storage instance to MetaDefender Storage Security
It is easy to integrate your SMB Compatible Storage with MetaDefender Storage Security to monitor and manage all your Storage instances and units (regardless of vendor) in one view - whether in the cloud or on-premises.
Recommended Resources

MetaDefender Storage Security Datasheet
MetaDefender Storage Security Documentation