MetaDefender™
Advanced Threat Prevention Platform
MetaDefender layers an array of market-leading technologies to protect critical IT and OT environments, shrinking the overall attack surface by detecting and preventing sophisticated known and unknown file-borne threats like advanced evasive malware, zero-day attacks, APTs (advanced persistent threats), and more.
MetaDefender
MetaDefender easily integrates with existing cybersecurity solutions at every layer of your organization’s infrastructure. With flexible deployment options purpose-built for your specific use case, MetaDefender ensures files entering, being stored on, and exiting your environment are safe—from the plant floor to the cloud. This solution uses a range of technologies to help your organization develop a comprehensive threat prevention strategy.
Advanced Malware Threat Prevention
MetaDefender protects organizations from advanced cybersecurity threats in data that originates from a variety of sources, such as web, email, portable media devices, and endpoints.
The MetaDefender philosophy is:
- Any file could be infected
- Any file could be attempting to exploit a vulnerability to compromise a network
- Single anti-malware engines, next-gen firewalls, sandboxes, machine learning, IPSec, and proxy anti-malware solutions do not provide adequate cybersecurity threat protection on their own
Digitally connected organizations are exposed to a wide variety of cyberattack vectors making it difficult for them to track and secure against threats, especially large enterprises with thousands of employees and contractors. Data transfer channels, such as file uploads, portable media devices, and email attachments, all have the potential to carry targeted attacks that can damage an organization’s reputation, financial standing, customer relationships, and for critical infrastructure, sensitive equipment and the facility itself.
Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.
Don’t Just Take Our Word for It.
OPSWAT is trusted by over 1,800 organizations worldwide to protect their critical data, assets, and networks from device and file-borne threats.
Analyze. Detect. Prevent.
Prevent Zero-Day Attacks and Evasive Malware
Most cybersecurity solutions rely upon threat detection as their core protective function. Deep CDR™ does not rely on detection. It assumes all files are threats and rebuilds their content using a secure and efficient reconstruction process. Deep CDR supports 200+ file types and outputs safe and usable files. Deep CDR is extremely effective at preventing targeted attacks, emerging threats, ransomware, known threats, and unknown malware.
Fast and Accurate Threat Detection with Multiscanning
Metascan™ Multiscanning uses multiple anti-malware engines to achieve fast, accurate threat detection. It combines the advanced threat prevention capabilities of more than 30 anti-malware engines. Utilizing signature and heuristic scanning, machine learning capabilities, and global threat intelligence feeds to increase response capabilities and accuracy.
Detect Vulnerable Software Before Installation
All applications contain exploitable vulnerabilities of varying severity. Our File-Based Vulnerability Assessment improves endpoint security. It detects binaries and installers with known vulnerabilities in files, applications, and software before they are installed on endpoint devices, including IoT devices. It supports vulnerability detection for over 1 million files and over 20,000 applications.
Detect Sensitive Data in Files and Emails
Proactive DLP™ helps prevent potential data breaches and regulatory compliance violations by detecting and blocking sensitive data in files and emails. Proactive DLP handles various data, including credit card and social security numbers. Proactive DLP supports multiple file types, including Microsoft Office and PDF. AI-powered Document Classification detects adult content in images and offensive language in text.
Detect and Respond to Threats in Near Real-Time
MetaDefender InSights Threat Intelligence detects known malicious domains and IP addresses in documents and enables real-time blocking of files based on malicious indicator detections. It applies high-quality, curated threat intelligence to extracted IOCs (indicators of compromise), aggregating data from hundreds of sources to ensure the highest quality threat detection and response capabilities.
Flexible Deployment in the Cloud or in Local Environments
Customers can implement our industry-leading Deep CDR, Metascan Multiscanning, and File-Based Vulnerability Assessment technology through either our MetaDefender Cloud service or by deploying MetaDefender advanced threat prevention solutions in their own environment, including air-gapped networks.
Next-Generation Sandbox Built on Adaptive Threat Analysis
MetaDefender Sandbox's unique adaptive threat analysis technology enables zero-day malware detection and more IOC extraction. Our proprietary Rapid Dynamic Analysis engine detects targeted attacks, bypassing anti-analysis tricks (e.g. geofencing).
Secure the Software Supply Chain
Identify known vulnerabilities, validate licenses, and generate component inventory for OSS (open-source software), third-party dependencies, and containers. OPSWAT SBOM supports 10+ programming languages, over 5 million third-party libraries, and utilizes an extensive database of 17K+ vulnerabilities sourced from the National Vulnerability Database (NVD) and GitHub (GHSA).
Faster False Positive Remediation with Reputation Match
Our reputation engine inspects the reputation of files by matching their hashes against a database of known malicious or safe files and identifying them as “known good”, “known bad” or “unknown”. OPSWAT Reputation engine leverages advanced analyses to reduce and remediate false positives faster.
Streamline Security and Compliance with Country of Origin
Detect the geographical origin of uploaded files including PE, MSI, and Self-extract. Country of Origin engine analyzes digital fingerprints and metadata to identify restricted locations and vendors automatically. This enables precise filtering that blocks unauthorized access to sensitive data based on its origin while ensuring compliance with data regulations across regions.
OPSWAT Advanced Threat Prevention
Advanced threat prevention with MetaDefender offers essential benefits to your organization.
Enhanced Visibility
Many organizations operate within increasingly complex infrastructures that make visibility a challenge. Understanding what's happening throughout your organization is critical for proactive threat management. MetaDefender offers that visibility, so you can feel certain about all activities occurring in every area of your company.
MetaDefender is user-friendly, simplifying visibility into risks like vulnerable software and files while preventing other vulnerabilities like the exposure of PII (personal identifiable information).
Keeping Compliance in Mind
Compliance plays a significant role in many industries. While regulatory compliance encompasses many factors, cybersecurity is often a major player in these standards. Organizations need to prove they are actively mitigating risks and protecting their data.
MetaDefender is your central threat prevention platform where your organization can thoroughly document risk mitigation techniques. With features like Deep CDR and vulnerability assessments, your organization is equipped to prepare for auditing.
Increased Communication Among Security Products
Many organizations rely on a disparate collection of security products to improve their security posture. While these collections of products and technologies are designed to address the many areas of cybersecurity, the lack of communication between these moving parts leads to more management responsibilities and an increased likelihood that vulnerabilities will slip through the cracks.
The MetaDefender Platform layers threat prevention technologies across an organization. Work with a single vendor and experience a unified cybersecurity network that detects a broad range of potential risks.
Greater Business Integrity
A business that effectively manages threats maintains productivity and builds trust with customers. The MetaDefender Platform addresses an array of vulnerabilities to improve your cybersecurity posture.
With MetaDefender solutions in your arsenal, your business is more stable and prepared to respond to risks. Keep your business at the forefront of cybersecurity with and prove to your customers that your organization can be trusted.
Trust No File
MetaDefender's exhaustive multilayered set of technologies prevents threats in multiple areas and shrinks the overall attack surface, from anti-malware multiscanning to file sanitization across thousands of third-party applications. Get a bird's-eye view of the platform and its many moving parts.
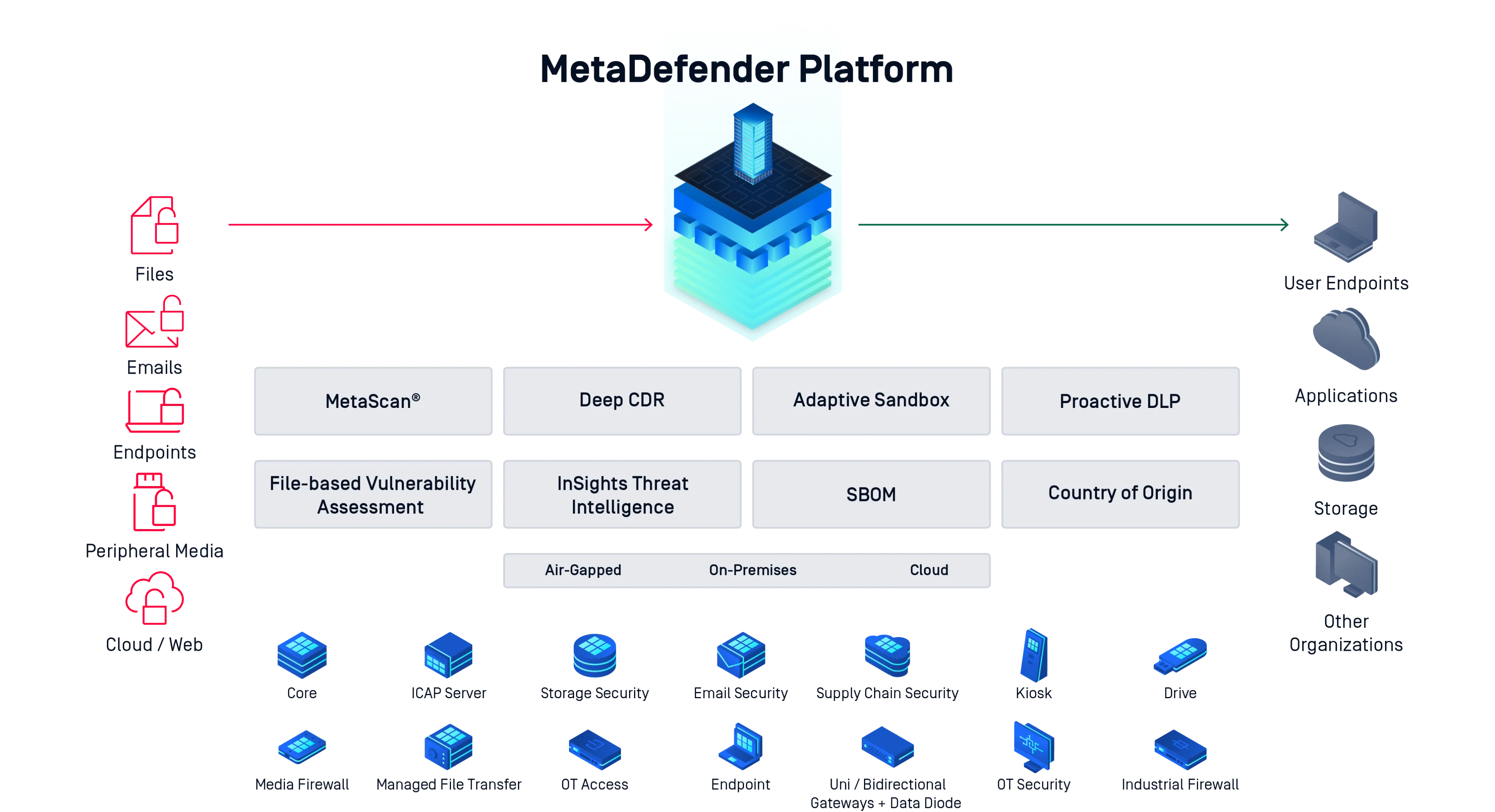
MetaDefender Technologies
Deploy MetaDefender at Major File and Data Entry Points
In a single organization, there can be an extensive amount of file and data entry points that are vulnerable to attacks. Learn more about how the MetaDefender Platform can meet your organization’s unique challenges and uses cases.