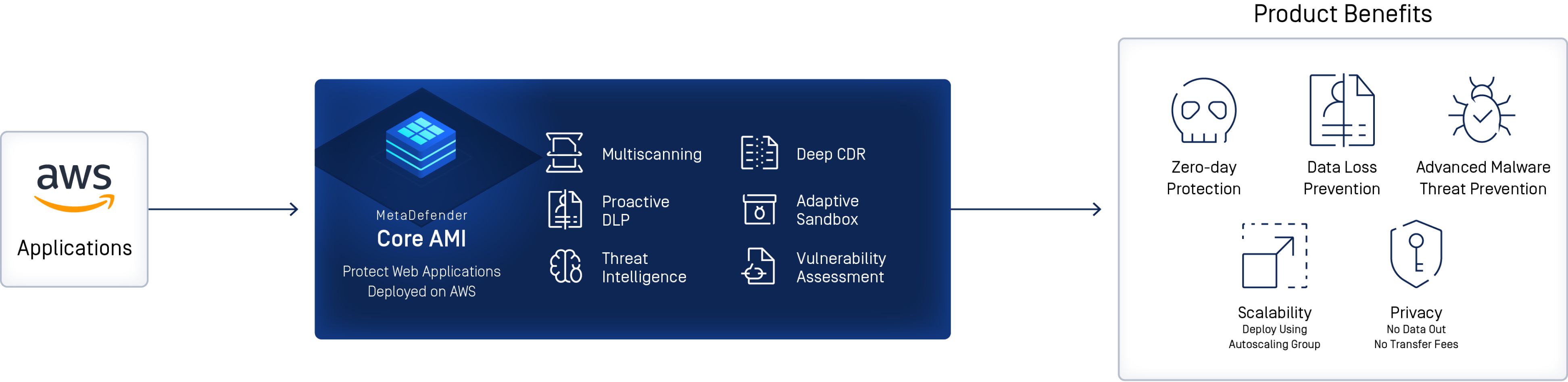
MetaDefender Core AMI™
Protect Web Applications Deployed on AWS
MetaDefender Core AMI™ (Amazon Machine Image) offers an advanced, multi-layered security platform that prevents malicious traffic from infiltrating your AWS Cloud deployment and protects your mission-critical data from deliberate theft, inadvertent leakage, and compromise.
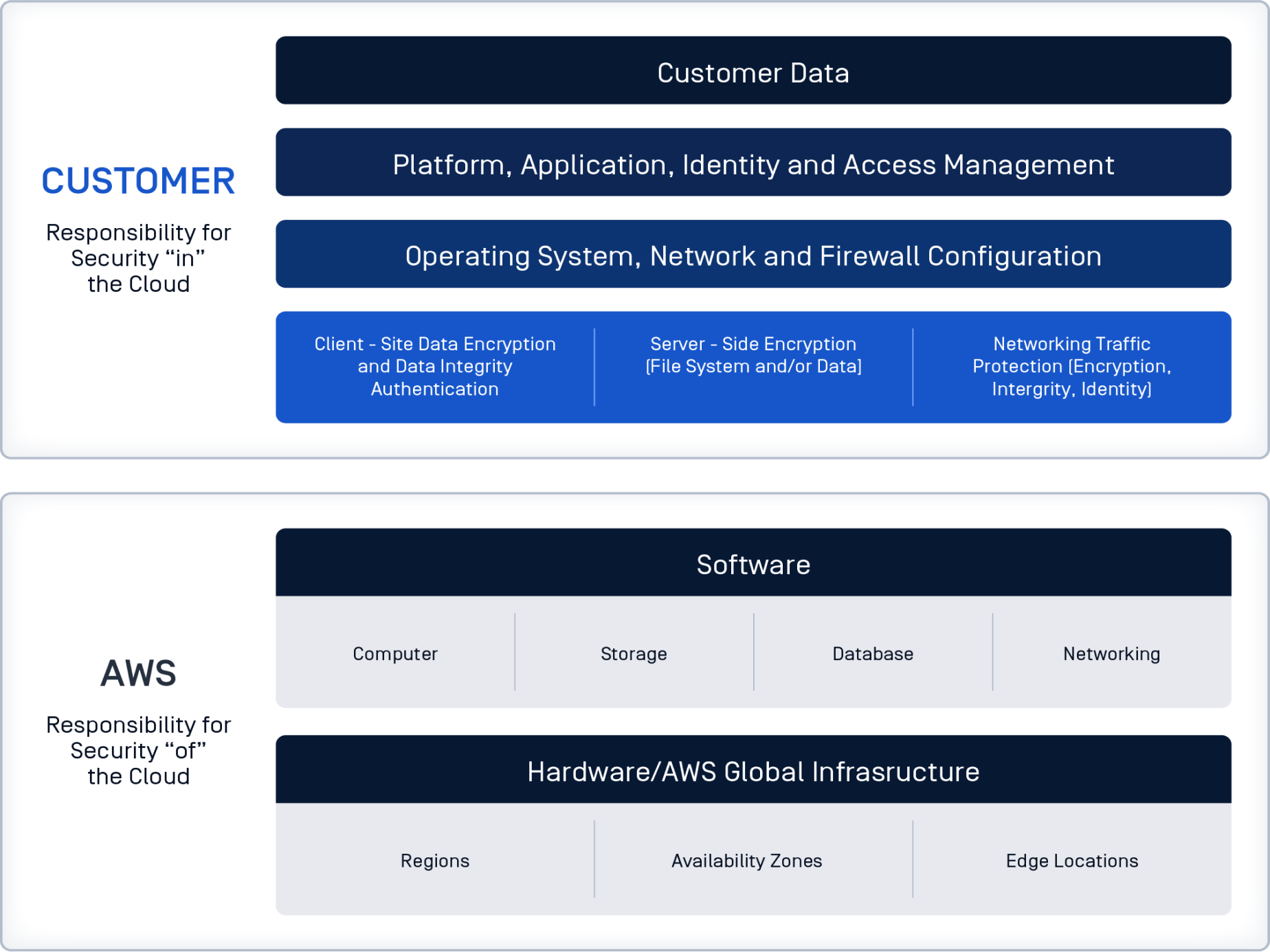
Sensitive Cloud Data At-Risk
Cybersecurity is critical for enterprises building their cloud infrastructure on Amazon Web Services (AWS). Under the AWS shared responsibility model, customers are responsible for securing their content, platforms, applications, systems, and networks deployed on the cloud. This aligns with the security practices required for on-premises systems.
Prevent. Detect. Respond
- Scan files uploaded to your AWS web applications deployed on AWS with 30+ antivirus engines and block more than 99% of known malware.
- Sanitize with industry-leading Deep CDR technology and remove 100% of potential threats.
- Sensitive and confidential data in files can be blocked, redacted or watermarked before entering or leaving your applications.
- Identify vulnerabilities in installers, binaries, or applications before deployment, leaving no security gaps.
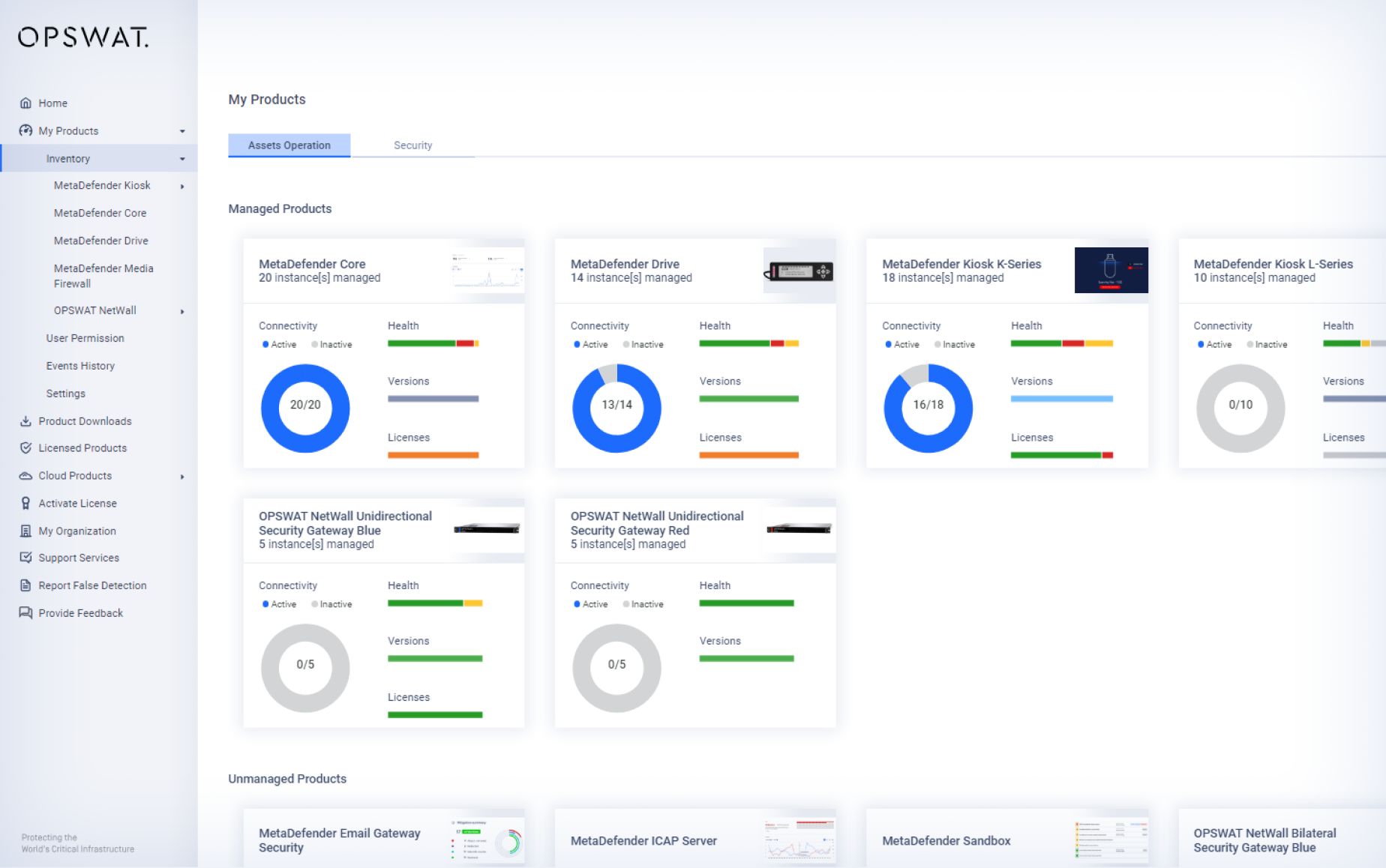
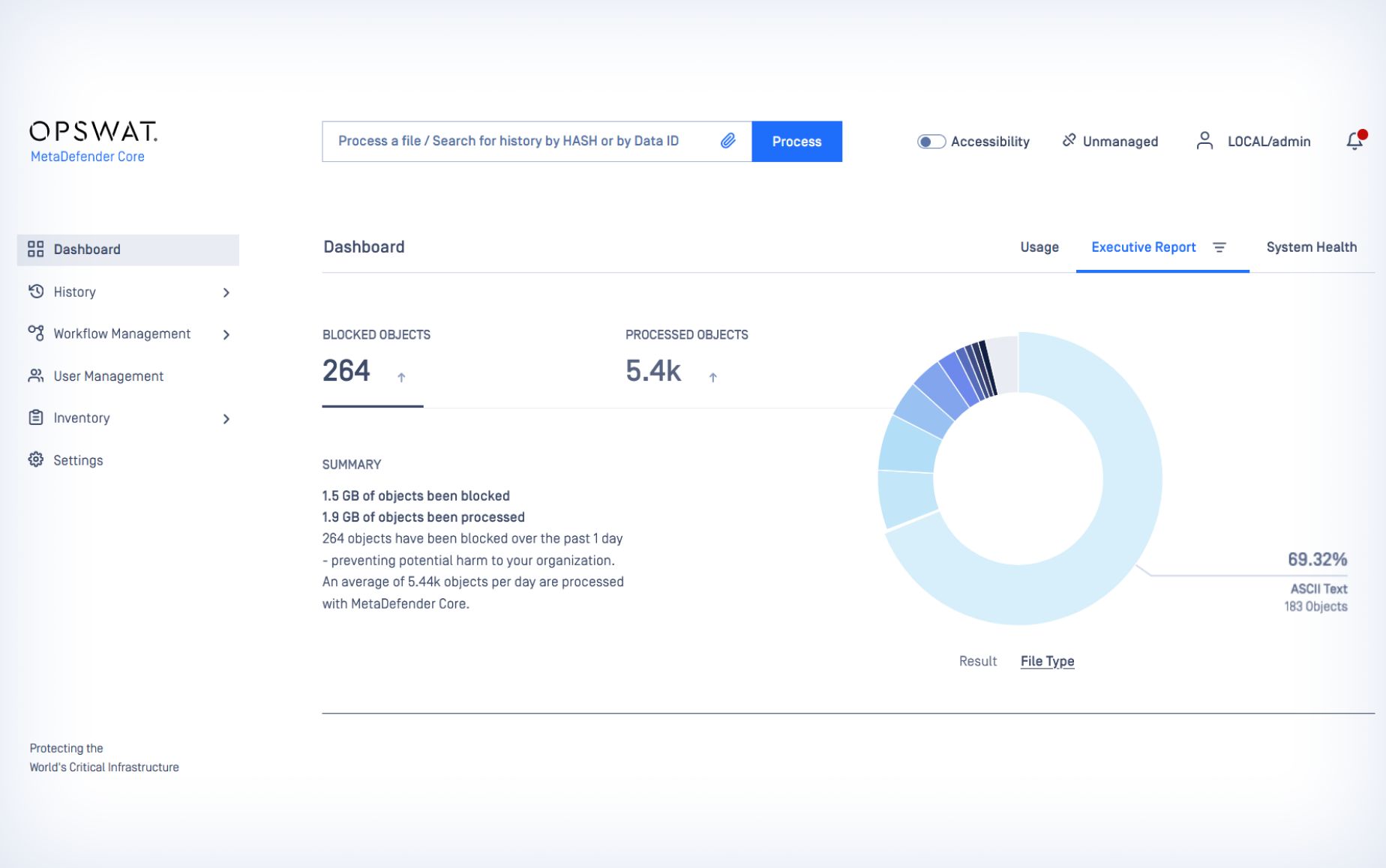
- Monitor and secure all cloud workloads in real-time via a Central Management console and interactive dashboard.
- Automated reports identify and prioritize user and service risks. enabling quick remediation.
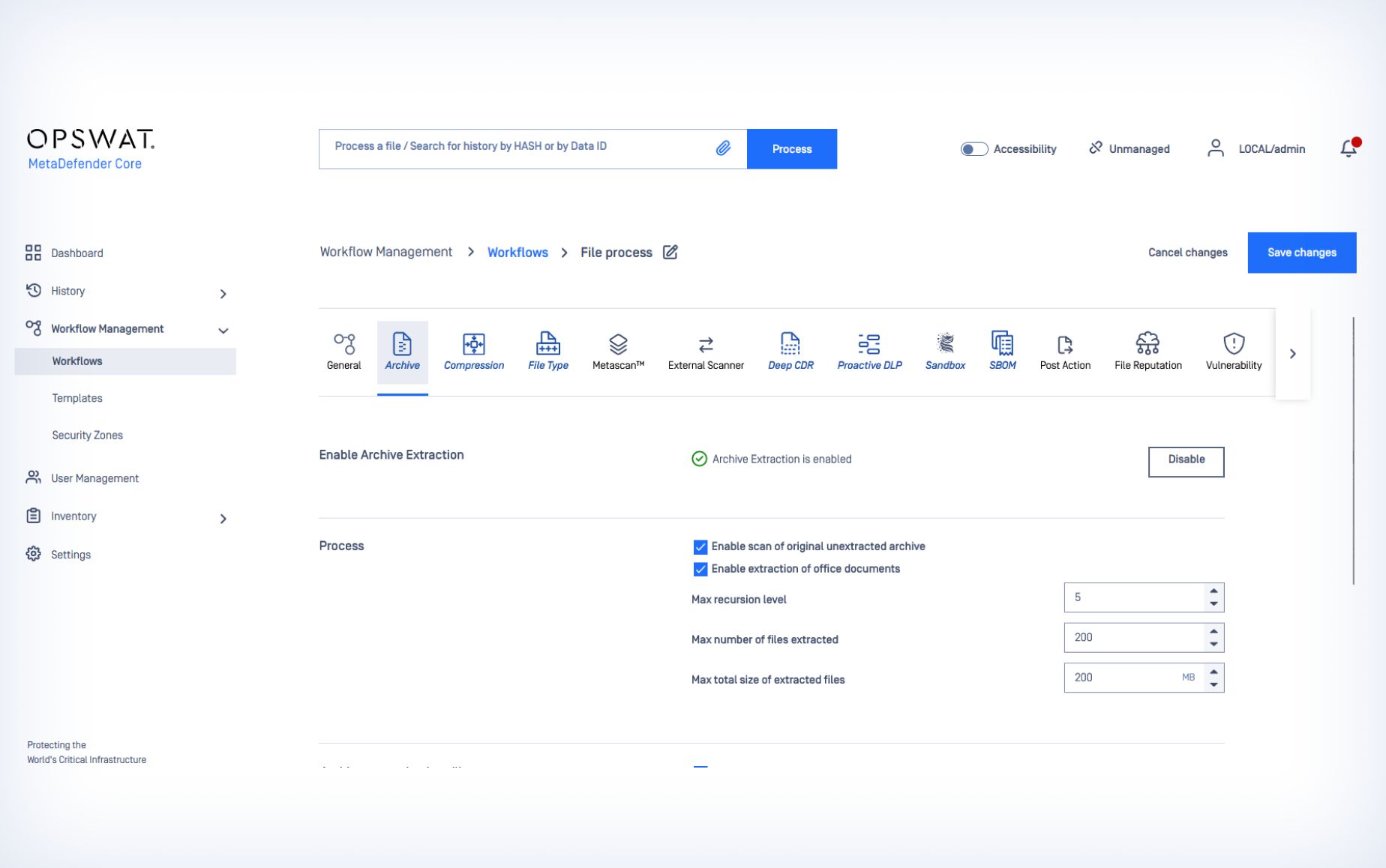
- Configure workflow and analysis rules based on user, file source, and file type to meet your specific security requirements.
- Flexible deployment options: download and install MetaDefender Core on your existing AWS deployment, or choose pre-installed deployment on Amazon Elastic Compute Cloud (EC2).
Why OPSWAT
Simple Deployment and Seamless Scalability
Each MetaDefender Core deployment becomes operational within minutes of activation. Deploying My OPSWAT further streamlines the process by pre-caching licensed modules and engines, significantly reducing deployment time.
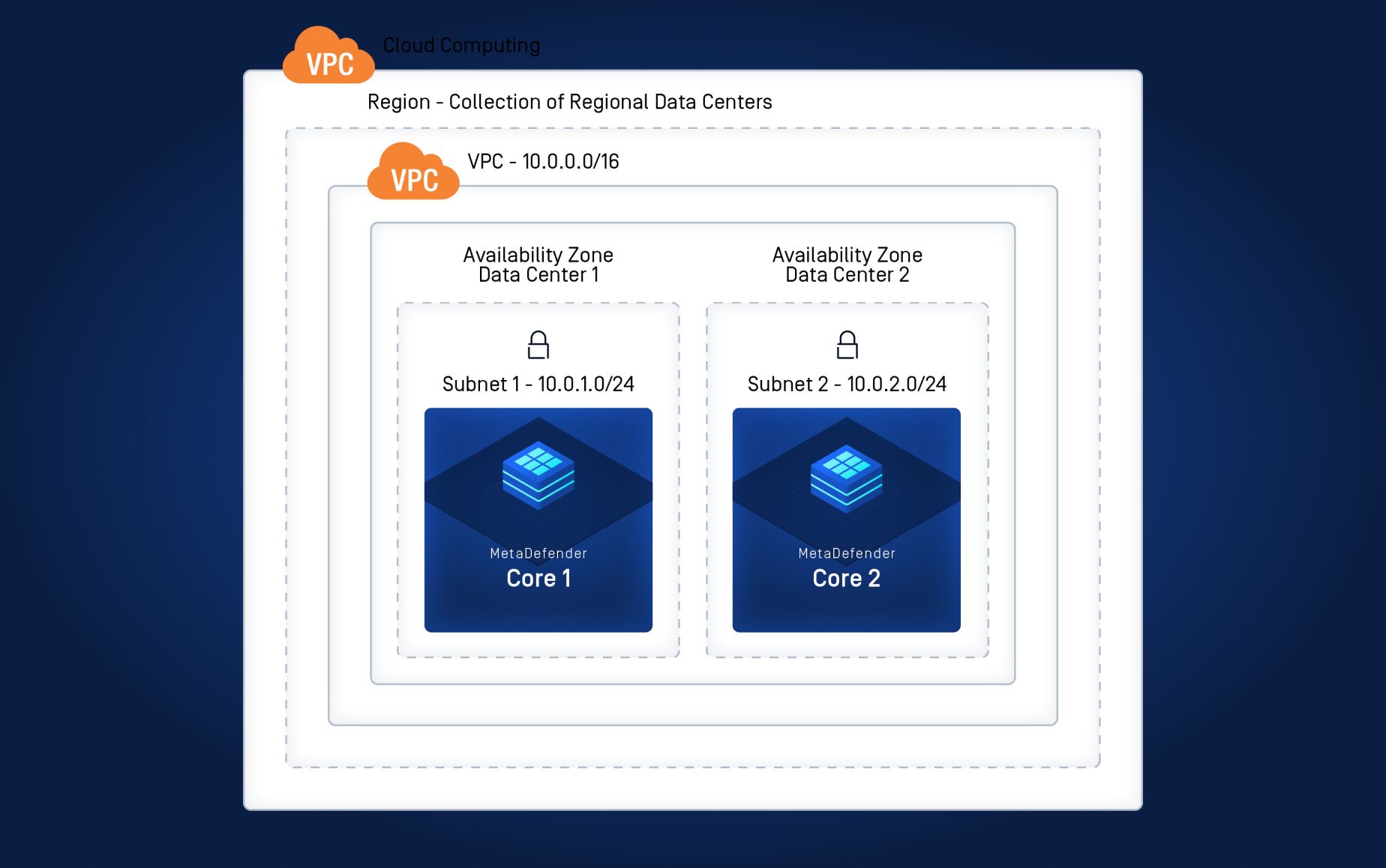
High-Performance and Reliability
Deploy MetaDefender across Availability Zones with a load balancer for automatic failover, ensuring continuous operation. Details can be found in the AWS Deployment Guide.
Custom Policies and Workflows
Create custom policies to manage diverse security needs. Define workflows based on users, file sources, and file types for comprehensive protection.
Continuous Visibility and Control
Gain complete real-time visibility into your assets and receive instant alerts to potential threats.
Metadefender Core AMI Provides Comprehensive Protection For Your Cloud Assets
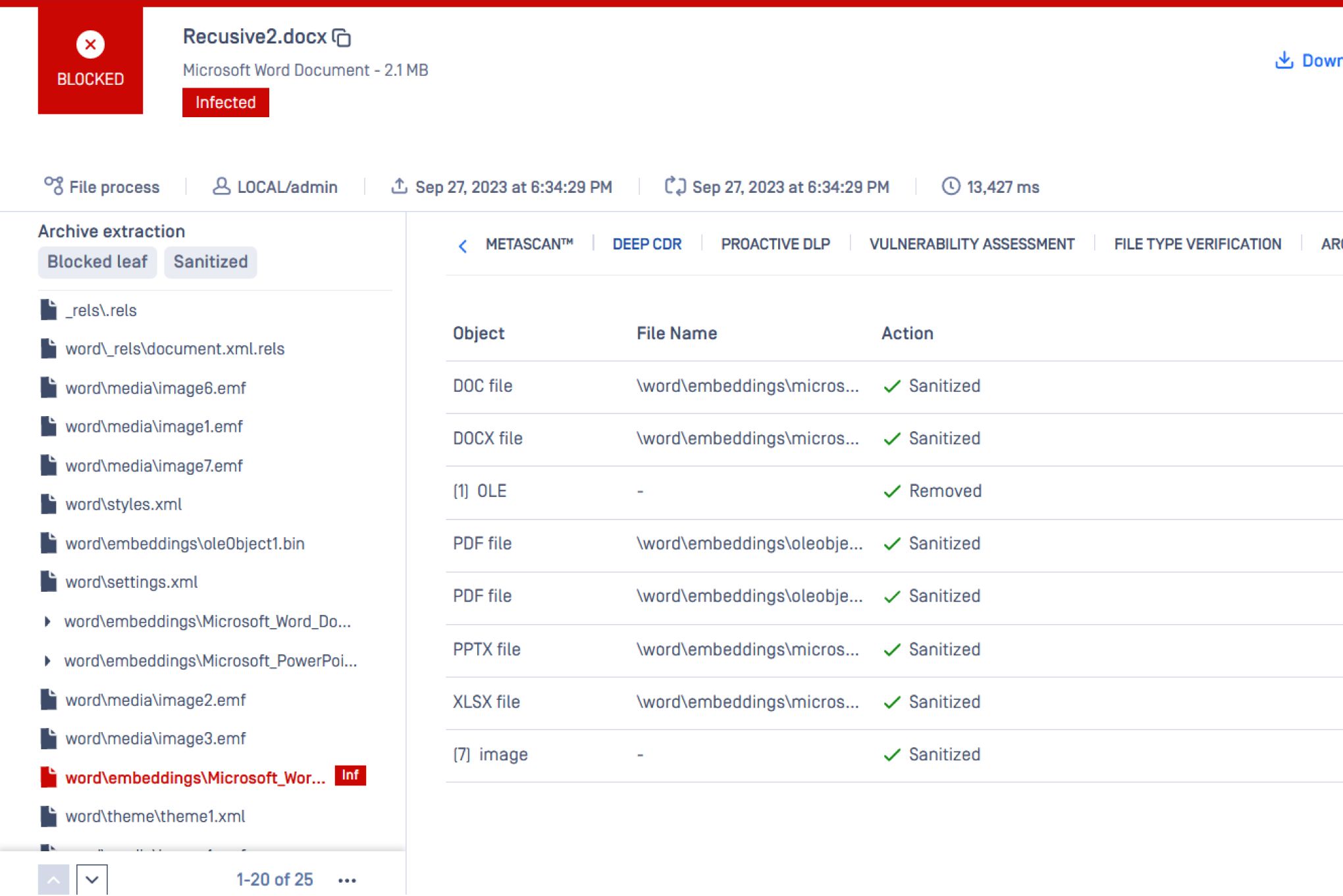
Prevent Zero-Day Attacks and Evasive Malware
Analyze and sanitize files entering or exiting your AWS deployment using Deep CDR.
Leverage AI to analyze and verify thousands of file types to combat spoofed file attacks and detect complex files disguised as simpler ones. Identify and neutralize embedded threats, such as macros, hyperlinks, and OLE objects. Red-flag and alert organizations for malicious content to prevent potential cyberattacks.
Deep CDR supports sanitization for over 200+ common file types, including PDF, Microsoft Office files, HTML and various image types. Specialized formats like JTD and HWP are also supported.
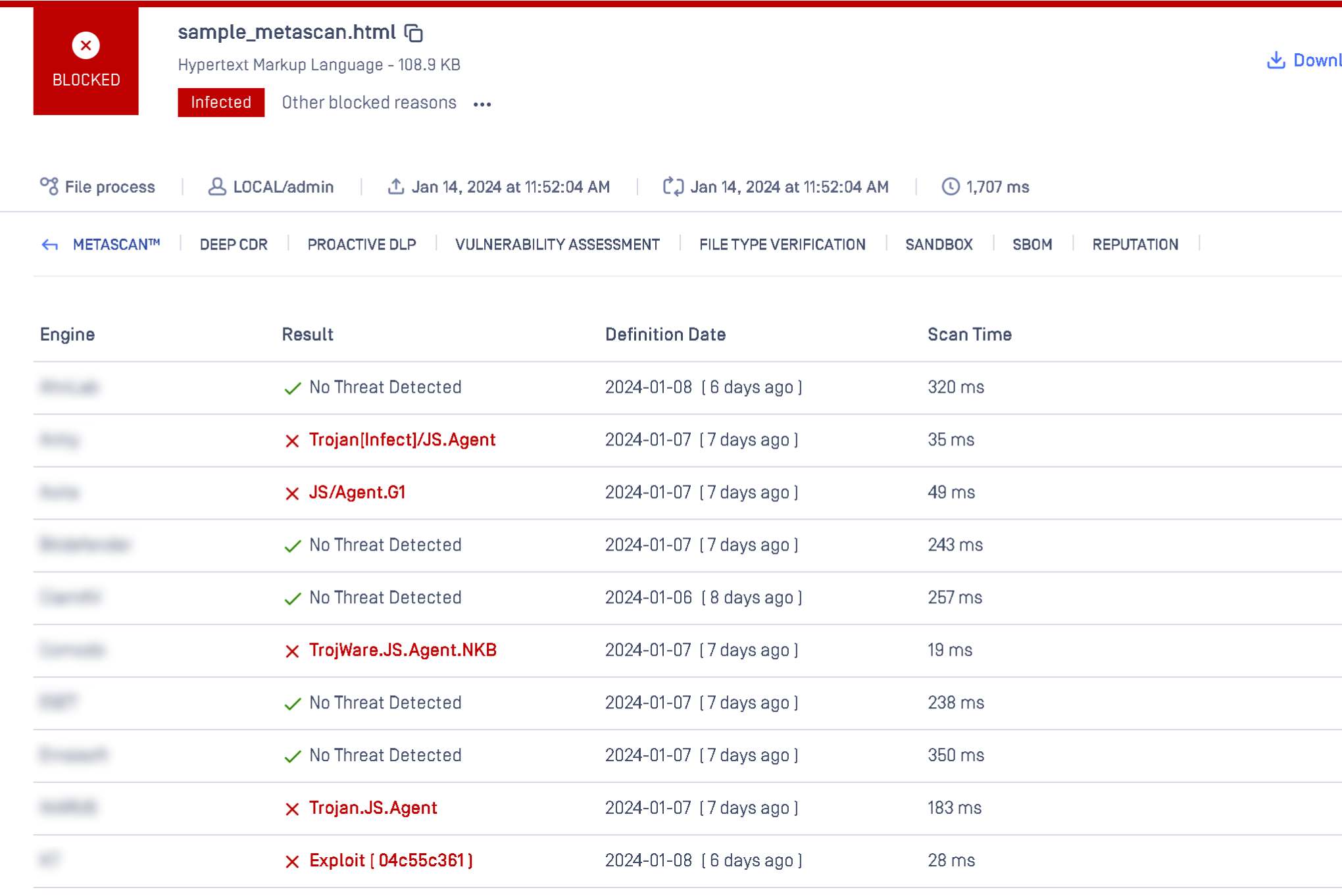
Maximum Known Malware Detection
OPSWAT Multiscanning technology leverages 30+ anti-malware engines, combining signature-based, heuristics-based, and machine learning detection methods. By combining the results of multiple scanning engines, you can significantly improve detection rates, reduce outbreak exposure times and achieve virtually zero exposure.
As shown in our Multiscanning test of more than 10,000 of the most active threats, we achieved over 95 percent detection with 12 combined engines, over 97 percent detection with 16 engines, and over 99 percent detection with 20 or more engines.
Single-source antivirus licensing through OPSWAT helps reduce overhead cost.
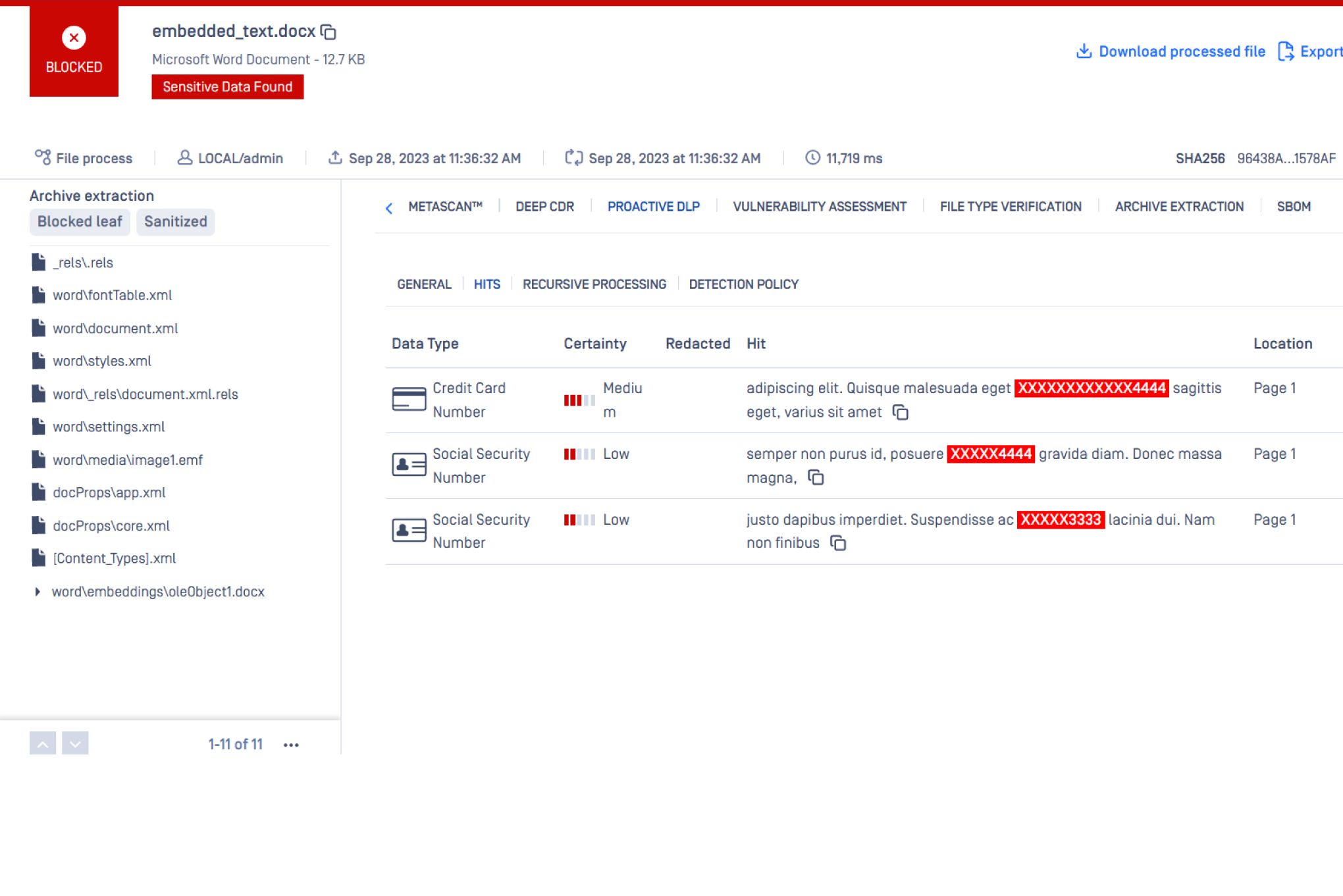
Detect Sensitive and Secret Data in Files
Aid compliance with data regulations and industry-standard security requirements for PCI, HIPAA, Gramm-Leach-Bliley, FINRA, etc. by using Proactive DLP. Redact, remove, watermark, or block sensitive and confidential data in files. MetaDefender Core AMI can content-check over 110 file types for sensitive content, including:
- Social Security Numbers
- Credit Card Numbers
- IPv4 addresses
- Classless Inter-Domain Routing (CIDR)
- Custom Regular Expressions (RegEx)
- Secrets in text files (AWS, Microsoft Azure, and Google Cloud Platform)
- Protected health information (PHI) and PII in Digital Imaging and Communications in Medicine (DICOM) files
- Adult content in images and inappropriate language in text
- Personal identity documents
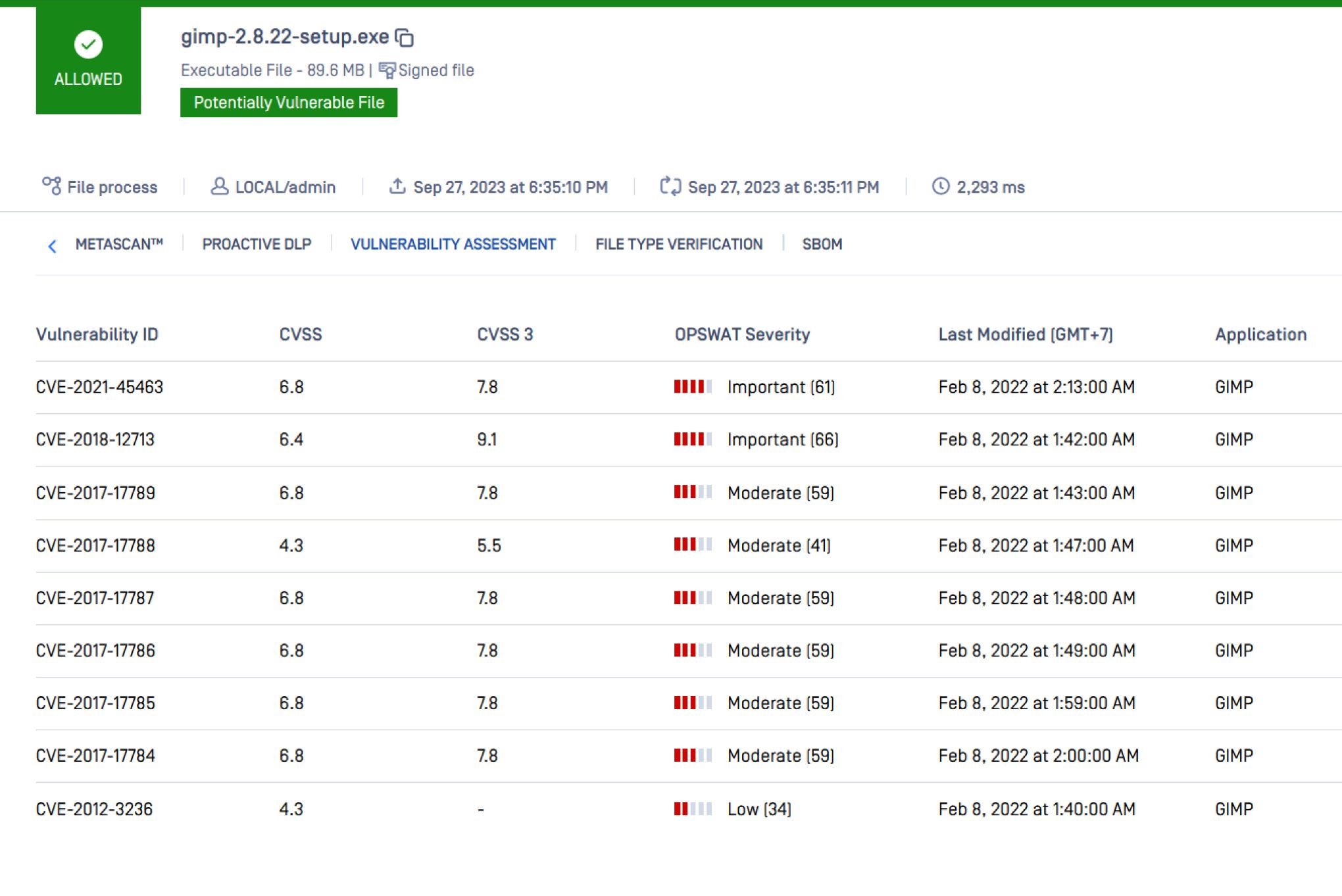
Assess Vulnerabilities Before They Are Deployed
Traditional vulnerability scanning often struggles to identify vulnerabilities within specific binary components. Our patented technology (U.S. 9749349 B1) leverages a vast database of over one billion (and growing) vulnerable software data points collected from real-world devices to accurately assess software component vulnerabilities. This empowers IT administrators to:
- Check specific software types for known vulnerabilities before deployment.
- Conduct comprehensive scans of systems for known vulnerabilities when inactive.
- Identify vulnerabilities in running applications and their associated libraries.