According to the MidYear 2024 Cyber Risk Report that analyzed trends in hacking activity and industry responses two sectors saw the largest increases in claims in 2024: manufacturing and construction. Manufacturing rose from 15.2% of all claims in 2023 to 41.7% of all claims in 2024.
Innovation Can Attract Threat Actors
Over the past 80 years, this company has pioneered concepts such as changeover, flexible assembly, automation, computer simulation, machine vision, and robotics.
The world’s first programmable logic controller (PLC), introduced by this company in 1969, was a pioneering technology for controlling equipment on production lines. However, 55 years later, these very systems have become a prime target for bad actors aiming to disrupt and affect manufacturing environments.
A compromised PLC can enable attackers to hack into more secure networks that the contractor’s workstation accesses, posing significant risks. Bad actors also target human curiosity with USB drop attacks outside this company's production plants, hoping to spread malware.
How Contractors Can Introduce Risks into Industrial Networks
To breach a highly secure critical network, threat actors often target third-party engineers and contractors.
First, the hacker compromises a Programmable Logic Controller (PLC) which can experience a low level of protection while connected to the internet. Then, they trick the engineer into connecting to the compromised PLC from their engineering workstation.
Vulnerabilities are exploited when an engineer initiates an upload procedure that transfers metadata, configurations, and text code from the compromised PLC to their workstation. The compromised device now enables the attacker to hack PLCs into other, more secure networks that the contractor’s workstation has access to.
Security researchers have identified this very attack method known as 'Evil PLC Attack’. During their research, vulnerabilities were identified in engineering workstation software from several vendors, including ABB (B&R Automation Studio), Emerson (PAC Machine Edition), GE (ToolBoxST), Ovarro (TwinSoft), Rockwell Automation (Connected Components Workbench), Schneider Electric (EcoStruxure Control Expert), and Xinje (XD PLC Program Tool).
Three Main File Transfer Challenges

- Unsecured File Transfers & Non-Compliance: Integrators directly connected to PLCs with potentially malicious workstations, containing unknown or zero-day malware. Bad actors target large entities like this company not only to disrupt business but also the economy and stock market or for large ransoms. Their production lines are air-gapped, with no connection to the outside internet, to protect against such cyber threats.
- High Operational Costs: Prolonged file security checks led to extended wait times for third party contractors, resulting in significant yet avoidable expenditures. When a production line goes down, it costs $1 million per hour of lost revenue. Therefore, the company goes to great lengths to protect its manufacturing lines from cyber threats.
- No Transfer Visibility or Control: Without role-based control, it was not possible to audit what files had been sent, who had been transferring files, and where they had been sent to.
OPSWAT's Solution: MetaDefender Managed File Transfer (MFT)
With MetaDefender Managed File Transfer (MFT), this company significantly improved productivity and security, exercising new visibility and control. A single public-facing MFT guest portal now serves as a primary hub for all file uploads and transfers.
This enables them to maintain a high level of protection for their OT infrastructure while external users and operators experience file transfer flexibility and speed. Employees are in full control over contractor access expiration dates and the cybersecurity risk to vulnerable PLCs is now mitigated.
To ensure the continuous flow of data and maintain plant operations without disruption, they banned peripheral media like USB sticks and SD cards. This impacted the vendors ability to update PLC firmware on production lines.
The goal was to disable the USB ports on all production workstations—12,500 ports globally and stop the sneakernet process permanently.
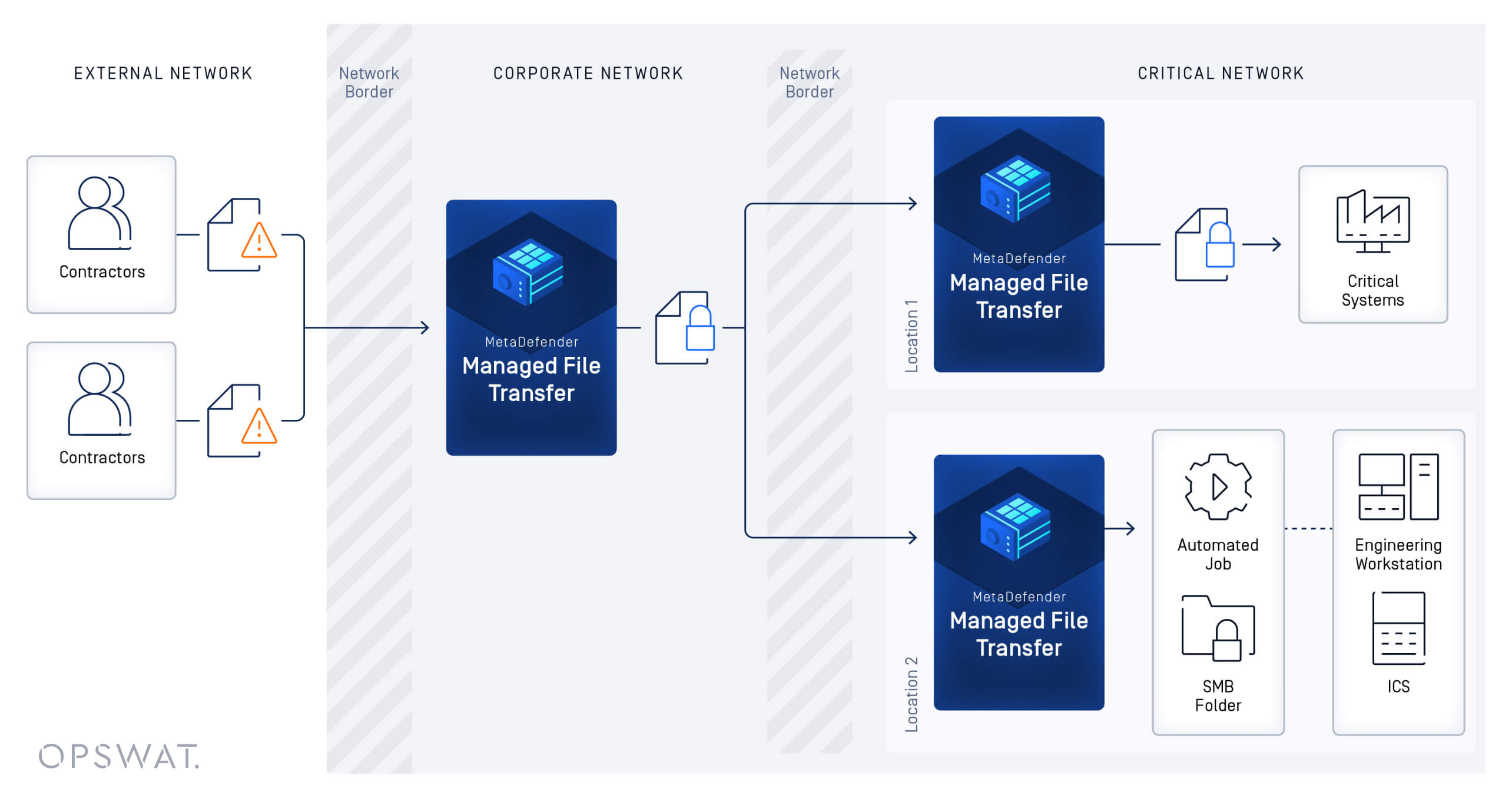
The process begins with secure file transfers, where contractors upload their files to MetaDefender Managed File Transfer (MFT) systems before arriving at the OT/industrial environments. This pre-arrival process not only enhances productivity but also maintains robust security measures against potential attacks on programmable logic controllers (PLCs).
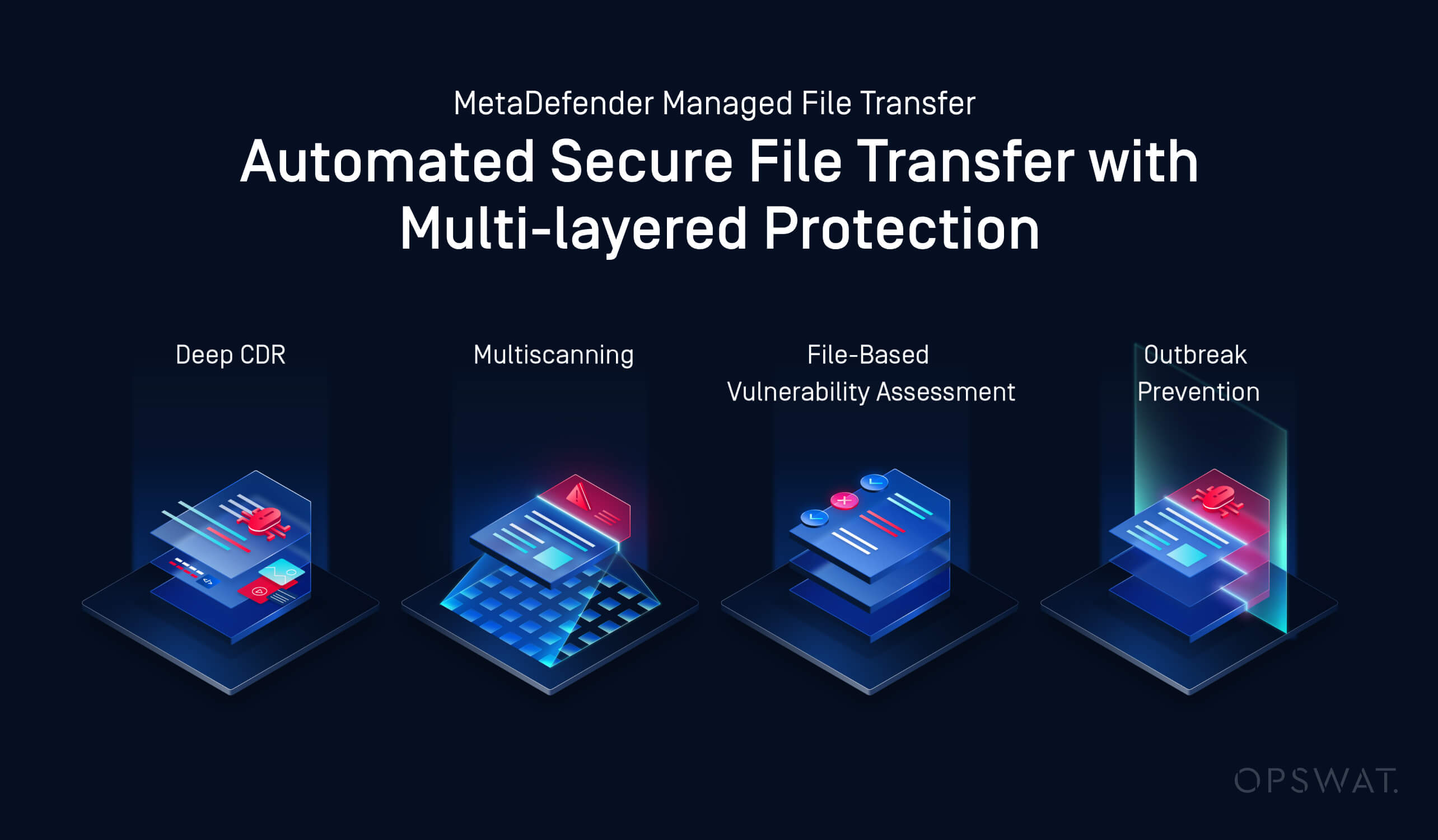
As part of this process, the uploaded files are scanned using a combination of Multiscanning—utilizing up to 30 anti-malware engines—and Deep CDR (Content Disarm and Reconstruction), which neutralizes file-based zero-day threats. Once these files are thoroughly scanned, they are delivered to their designated locations, where additional analyses, including vulnerability assessments and outbreak prevention technologies, ensure their safety.
MetaDefender Managed File Transfer (MFT) also automates the file transfer process, which eliminates the need for manual handling and significantly reduces errors. This automation enables contractors to quickly access the OT environment while their files undergo multiple layers of security verification, allowing the company to achieve new levels of operational agility, control, and efficiency.
Furthermore, the solution provides clear visibility and control for employees. They can easily create guest accounts to facilitate internal OT file transfers and regulate which satellite locations contractors can synchronize with. These guest accounts come with expiration dates, enhancing security by limiting how long a contractor can access the system.
File management has also been centralized, allowing seamless and secure transfers between multiple locations. This centralized approach supports complex distribution scenarios, whether between different organizational units or with external partners.
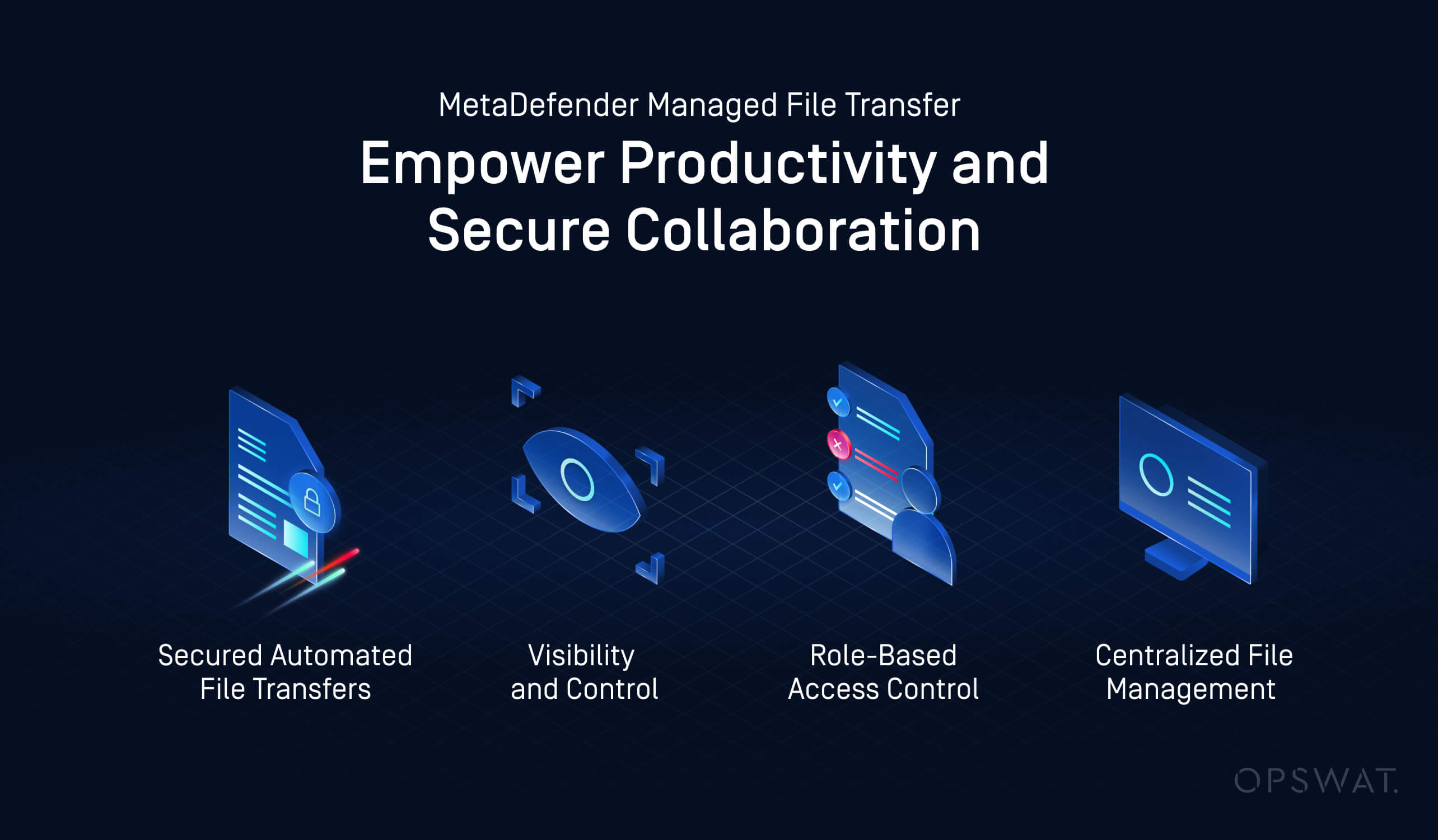
Security is further strengthened through role-based access control, which ensures that contractors and suppliers are only permitted to access files and functions as authorized by their supervisors. This layer of granularity ensures compliance with data protection regulations.
Access control also extends to location-based management. Contractors’ guest accounts are restricted to the MetaDefender Managed File Transfer (MFT) locations designated by their assigned user privileges, ensuring that sensitive systems are only accessed by authorized personnel. To maintain accountability, the system logs all user access, data movements, and system events, generating granular historical records that can be audited.

The solution’s security measures don’t stop there. It continuously monitors for malware outbreaks using recurring file analysis, which leverages both Multiscanning and Sandbox technologies to detect and neutralize potential zero-day malware. Files are checked against the latest virus definitions with each scan, keeping the system protected from evolving threats.
Deep CDR technology plays a crucial role in preventing sophisticated attacks by neutralizing potentially malicious active content embedded within files, all while ensuring that file functionality remains intact. This technology supports over 175 file formats and verifies more than 1,000 file types, providing extensive protection across a wide range of data.
Finally, the Adaptive Sandbox feature combines static file analysis, dynamic threat detection, and machine learning algorithms to classify previously unknown threats. This feature also integrates automated threat hunting and real-time identification with broader threat intelligence systems, ensuring proactive defense measures are in place.
In addition to this, OPSWAT's patented File-Based Vulnerability Assessment detects vulnerabilities within applications and files, using billions of data points to correlate vulnerabilities across software components, installers, and other binary files. This technology effectively mitigates risk before installation, contributing to the overall security and integrity of the system.
Results and Reactions
The implementation of OPSWAT's MetaDefender Managed File Transfer (MFT) has significantly enhanced the security and efficiency of file transfers for this global automotive company, safeguarding their OT infrastructure from potential threats while ensuring seamless operations.
This was truly a collaborative effort not only across teams but across 15 production plants globally, to dramatically increase the organization's cybersecurity footprint and awareness, setting off a new era of cybersecurity culture.
Now, with the solution in place, the automotive company has no interruption to its workflow.
To find out more on how OPSWAT's industry-leading MFT solution, MetaDefender Managed File Transfer (MFT), can benefit your critical infrastructure, reach out to an OPSWAT expert today.





