- What is Threat Hunting?
- The Role of Threat Hunters in Strengthening Cybersecurity
- Why Threat Hunting is Crucial for Critical Infrastructure
- How Cyber Threat Hunting Works
- Types of Cyber Threat Hunting
- Threat Hunting Models
- Essential Threat Hunting Tools
- Threat Hunting vs. Threat Intelligence
- The Importance of RetroHunting
- Understanding Tactics, Techniques, and Procedures (TTPs)
- Practical Examples of Threat Hunting
- Strengthening Cybersecurity Through Proactive Threat Hunting
- FAQs
As cyber threats grow more advanced, organizations must take a proactive approach to cybersecurity to safeguard their critical assets. One such essential practice is threat hunting, a strategy that involves actively seeking out potential threats within a network before they can cause harm.
Traditional security tools such as firewalls, antivirus software, and automated detection systems are effective, but they are not foolproof. Threat actors are constantly developing new techniques to bypass these defenses. Cyber threat hunting plays a crucial role in identifying and mitigating threats that evade automated detection systems, enabling organizations to stay ahead of adversaries.
What is Threat Hunting?
Threat hunting is the proactive process of searching through networks, endpoints, and datasets to identify and mitigate cyber threats that have evaded traditional security measures. Unlike reactive approaches that rely on automated alerts, threat hunting emphasizes human expertise to uncover sophisticated threats lurking within an organization's infrastructure. As an organization’s threat hunting capabilities mature, such operations can be augmented by automation and scaled to work in greater capacity.
The Role of Threat Hunters in Cybersecurity
Threat hunters serve as the proactive defenders of an organization’s cybersecurity framework. Their primary responsibility is to detect hidden threats before they escalate into full-blown security incidents.
By applying knowledge of adversary capabilities and behaviors, threat hunters dive deep into network traffic, seek out suspicious tracks in security logs, and identify anomalies that may not have been viewed as critical enough to result in automated detections. In this way, threat hunters play a crucial role in fortifying an organization’s security posture.
Threat hunters utilize behavioral analysis techniques to differentiate between normal and malicious cyber activities. Additionally, they provide actionable intelligence that informs security teams on how to enhance existing defenses, refine automated detection systems, and close security gaps before they can be exploited.
By focusing on both known threats and emerging attack methodologies, threat hunters significantly reduce an organization’s reliance on reactive security measures and instead cultivate a culture of proactive defense.
Why Threat Hunting is Crucial for Critical Infrastructure
Threat hunting has become an indispensable practice in modern cybersecurity due to the increasing sophistication of threat actor tactics. Many adversaries, particularly advanced persistent threats (APTs), may utilize stealthy techniques and evasive malware that remain undetected for extended periods, frequently bypassing conventional security defense tools.
Without active cyber threat hunting, these hidden attacks can dwell within networks for months, extracting sensitive data or preparing for large-scale disruptions. Additionally, threat hunting plays a critical role in reducing dwell time, the period in which a threat actor remains undetected within a system. The longer an attacker remains undetected, the better their chance to firmly entrench in an environment and the greater the damage they can inflict on an organization’s infrastructure and data.
Beyond reducing dwell time, threat hunting enhances an organization’s incident response capabilities. By proactively identifying threats before they manifest into breaches, security teams can respond swiftly and effectively, minimizing the impact of potential attacks.
Furthermore, organizations that integrate threat hunting into their security frameworks gain deeper insights into adversary tactics, enabling them to improve their defenses continually. This approach also aids in regulatory compliance, as many cybersecurity regulations mandate proactive threat detection practices.
Ultimately, threat hunting strengthens an organization’s overall security culture, ensuring that security teams remain vigilant and well-prepared against evolving cyber threats.
How Cyber Threat Hunting Works
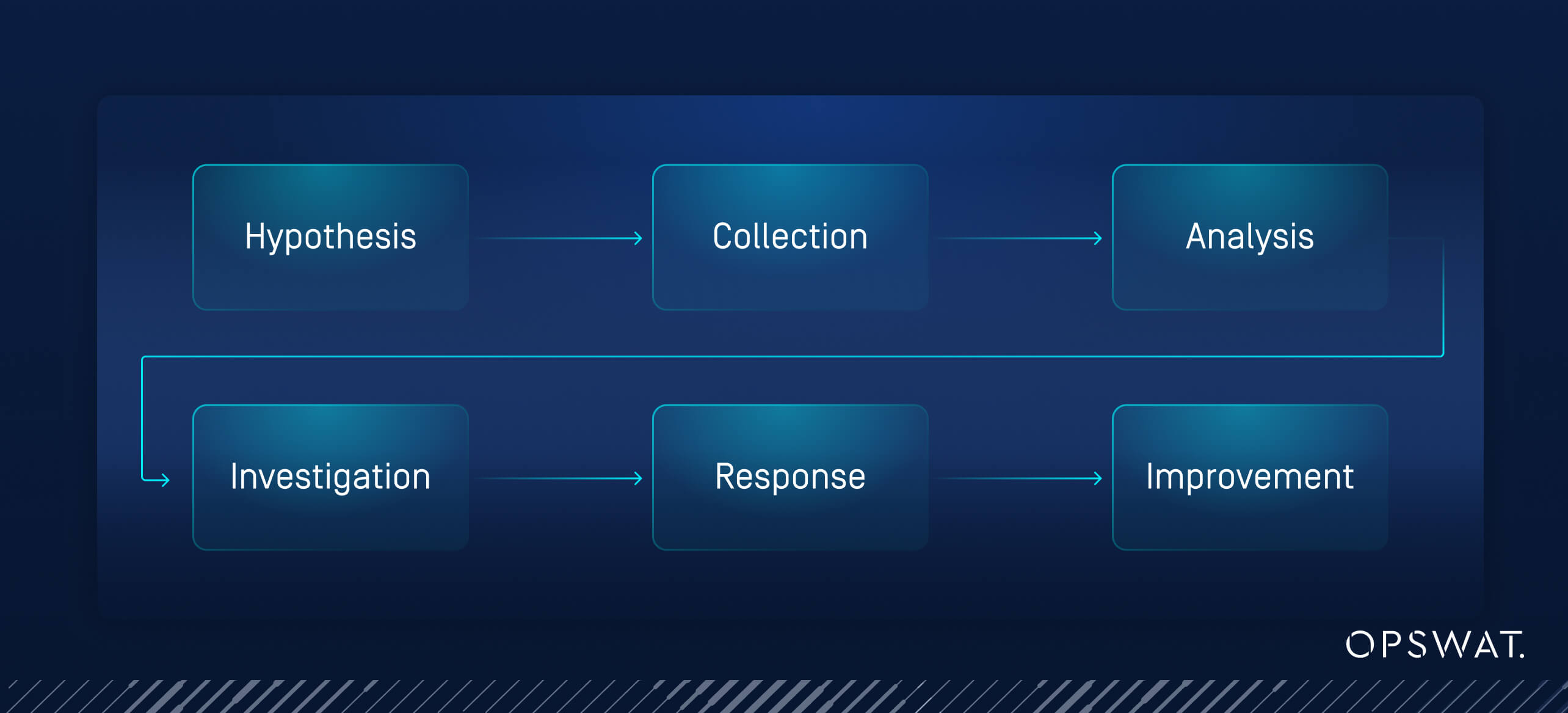
The cyber threat hunting process typically involves several key steps:
- Hypothesis Generation: Based on threat intelligence and knowledge of the organization’s environment, cyber threat hunters formulate hypotheses about potential threats, considering past attacks and industry-specific threats.
- Data Collection: Relevant data from various sources, such as network logs, endpoint telemetry, and cloud environments is gathered for comprehensive analysis.
- Data Analysis: Hunters scrutinize the collected data to identify anomalies, unusual patterns, and behaviors that may indicate malicious activity, sometimes leveraging machine learning and statistical models.
- Investigation: Suspicious findings undergo a deep-dive investigation to determine whether they represent real threats or false positives, ensuring resources are allocated efficiently.
- Response: Confirmed threats are swiftly addressed through containment, eradication, and recovery measures to mitigate potential damage.
- Continuous Improvement: Insights gained from each proactive threat hunt are used to refine security policies, enhance automated threat detection systems, and improve future hunts.
Types of Cyber Threat Hunting
Threat hunting methodologies can be categorized into four primary types:
| Structured Hunting | Utilizes hypotheses based on the known criteria surrounding tactics, techniques, and procedures (TTPs) of adversaries to guide the hunt, ensuring a methodical approach. |
| Unstructured Hunting | Driven by intuition and less focused on known indicators of compromise (IOCs), this method involves a more flexible search for malicious activity before and after identified triggers. |
| Situational or Entity-Driven Hunting | Focused on high-risk or high-value entities, such as sensitive data or critical computing resources, helping prioritize cyber threat investigative efforts. |
| Machine-Learning Assisted Hunting | Uses artificial intelligence to detect anomalies and assist human analysts in identifying potential threats more efficiently, improving scalability. |
Threat Hunting Models
Several models guide threat hunting practices:
- Intel-Based Hunting: Relies on threat intelligence feeds, such as IOCs, IP addresses, and domain names, to identify potential cyber threats based on external intelligence sources. This is often considered a less mature and less effective approach to hunting for adversaries but may be useful in some cases.
- Hypothesis-Based Hunting: Involves creating hypotheses based on analytics, intelligence, or situational awareness to guide the hunting process toward unknown threats.
- Investigation Using Indicators of Attack (IOA): Focuses on identifying adversary behaviors and attack patterns to detect cybersecurity threats before they execute.
- Behavioral-Based Hunting: Detects anomalous user and network behaviors rather than relying on predefined indicators, providing a more dynamic detection method.
Essential Threat Hunting Tools
Effective threat hunting requires a suite of specialized tools:
- Security Information and Event Management (SIEM) Systems: Aggregate and analyze security alerts from various sources.
- Endpoint Detection and Response (EDR) Solutions: Monitor endpoint activities to detect and respond to threats missed by automated systems. EDR products produce a rich set of data about activity occurring on an organization’s endpoints, providing opportunities to continually surface findings as new host-based tactics, techniques, and procedures (TTPs) are researched.
- Network Detection and Response (NDR) Solutions: Monitor and analyze network traffic to detect adversary activity based on network communications. Multiple common adversary tactics rely on networks, including Lateral Movement, Command & Control and Data Exfiltration. Signals generated at the network layer may be useful for identifying signs of threat actor activity.
- Managed Detection and Response (MDR) Services: Provide outsourced threat hunting and response capabilities.
- Security Analytics Platforms: Utilize advanced analytics, including machine learning, to identify anomalies and potential threats. These types of systems are critical for aggregating event data, analyzing it in meaningful ways, and surfacing insights to key cyber threat hunting outcomes.
- Threat Intelligence Platforms: Aggregate threat intelligence data from various sources to assist in identifying threats.
- User and Entity Behavior Analytics (UEBA): Analyze user behavior patterns to detect potential insider threats or compromised accounts.
Threat Hunting vs. Threat Intelligence
While threat hunting and threat intelligence are closely related, they serve distinct yet complementary roles in cybersecurity.
Threat intelligence involves the collection, analysis, and dissemination of information regarding existing and emerging threats, enabling organizations to anticipate potential attacks. It provides security teams with valuable insights, including attack vectors, adversary behaviors, and emerging vulnerabilities, which can be used to enhance defensive measures.
On the other hand, threat hunting is an active, hands-on approach where analysts proactively search for threats within their organization’s network. Rather than waiting for alerts or known indicators of compromise, threat hunters use the insights provided by threat intelligence to investigate potential hidden threats that automated security tools might miss.
While threat intelligence supports threat hunting by providing crucial data, threat hunting refines threat intelligence by uncovering new attack methodologies and vulnerabilities, making both practices essential for a well-rounded cybersecurity strategy.
The Importance of RetroHunting
Much of the discussion of threat hunting concerns data that has been collected and can later be analyzed to surface awareness of threats when fed with new information. Many cybersecurity solutions work in this way, providing data that can be analyzed in real-time or at a later point.
However, some solutions only work in real time; they analyze data that is in context at that moment, and when that data has passed out of context, it is not possible to analyze at the same level of depth in the future. Examples include some forms of network data analytics such as intrusion detection systems (IDS), antivirus software that inspect file content at the moment it is accessed or crated, as well as several types of detection pipelines that are built to analyze streaming data and then discard it.
Cyber threat hunting reminds us that some threats are difficult to detect in real time, and that often the only time they will be detected is at a future point when more intelligence about a threat is known.
Retroactive hunting (“RetroHunting”) is a lookback method that enables previously collected network and file data to be analyzed using today’s enhanced awareness of the threat landscape. Built for threat hunting teams, OPSWAT’s suite of Triage, Analysis and Control (TAC) solutions, including MetaDefender NDR, implement RetroHunting to help defenders re-analyze data using updated detection signatures, surfacing threats that slip past defenses.
This is a proven method to fuse the benefits of threat intelligence, detection engineering, threat hunting and incident response into a comprehensive defensive model. Customers that use RetroHunt detect and remediate more active adversary footholds in their environments than using standard real-time analytics alone.
Understanding Tactics, Techniques and Procedures (TTPs)
Tactics, Techniques, and Procedures (TTPs) are fundamental to understanding and countering cyber threats.

Tactics refer to the high-level objectives that an attacker aims to achieve, such as gaining initial access to a system or exfiltrating sensitive data.

Techniques describe the specific methods used to accomplish these objectives, such as spear-phishing for credential theft or privilege escalation to gain deeper network access.

Procedures outline the step-by-step execution of these techniques, often varying based on the attacker’s skill level and available resources.
By analyzing TTPs, threat hunters can anticipate and identify cyber threats before they materialize. Instead of reacting to individual alerts, security teams can focus on tracking adversary behavior patterns, making it easier to detect ongoing attacks and predict potential next steps.
Understanding TTPs allows organizations to develop better defensive strategies, harden their systems against specific attack techniques, and enhance their overall cybersecurity resilience.
Reducing Dwell Time
Dwell time refers to the duration a threat actor remains undetected within a network. Reducing dwell time is vital to minimize the potential damage from cyber threats. Proactive threat hunting can significantly decrease dwell time by identifying and mitigating threats before they can fully execute their malicious objectives.
Practical Examples of Threat Hunting
A security team notices unusual authentication requests across multiple endpoints. Using threat hunting methodologies, they uncover an attacker attempting to move laterally within the network, allowing them to contain further impact and prevent data exfiltration.
A company experiences a sudden spike in network traffic to an unknown domain. Threat hunters investigate and discover a backdoor trojan communicating with a command and control (C2) server, enabling them to contain the threat before it spreads.
Threat hunters detect anomalous behavior from a privileged user account attempting to access sensitive files. Investigation reveals that an insider was exfiltrating proprietary data, leading to immediate action to prevent further damage.
Adversaries may use a number of stealthy persistence methods to retain access to a target environment in case they lose access via primary methods. Threat hunters compile a list of persistence techniques that can be used in their environment, audit for abuse of those methods, and identify a web shell on a compromised server that an adversary planted earlier in the year.
Strengthening Cybersecurity Through Proactive Threat Hunting
Threat hunting is an essential component of a proactive cybersecurity strategy. By continuously searching for hidden threats, organizations can significantly enhance their security posture, reduce attack dwell time, and mitigate potential damage from cyber threats.
To stay ahead of cyber adversaries, organizations should invest in threat hunting tools, develop in-house expertise, and leverage advanced threat intelligence solutions.
Take the Next Step
Explore how OPSWAT’s Threat Intelligence solutions can enhance your threat hunting capabilities and strengthen your organization’s security defenses.
FAQs
What is threat hunting?
Threat hunting is the proactive process of searching through networks, endpoints, and datasets to detect cyber threats that have bypassed traditional security measures. Unlike reactive security, threat hunting relies on human expertise to uncover hidden or advanced threats that automated systems may miss.
What role do threat hunters play in cybersecurity?
Threat hunters are cybersecurity professionals who actively seek out threats before they cause harm. They analyze network traffic, review security logs, and identify anomalies that may signal an attack. Their work strengthens security by uncovering hidden threats, refining detection systems, and guiding defensive improvements.
Why is threat hunting important for critical infrastructure?
Threat hunting is essential for protecting critical infrastructure because advanced threat actors often use stealthy tactics that evade standard security tools. Without active threat hunting, these attacks can remain undetected for long periods. Threat hunting helps reduce dwell time, improve incident response, and support compliance with cybersecurity regulations.
How does cyber threat hunting work?
Cyber threat hunting follows a multi-step process:
Hypothesis Generation: Forming theories based on intelligence and past threats.
Data Collection: Gathering logs, telemetry, and other relevant data.
Data Analysis: Identifying patterns or anomalies that may signal a threat.
Investigation: Validating findings and eliminating false positives.
Response: Acting on confirmed threats to contain and resolve them.
Continuous Improvement: Using insights from each hunt to strengthen future defenses.
What are the types of cyber threat hunting?
The four main types of threat hunting are:
Structured Hunting: Guided by hypotheses based on known adversary tactics.
Unstructured Hunting: Driven by analyst intuition and not limited to predefined indicators.
Situational or Entity-Driven Hunting: Focuses on specific high-risk assets or entities.
Machine-Learning Assisted Hunting: Uses AI to detect anomalies and support human analysis.
What are the main threat hunting models?
Threat hunting models include:
Intel-Based Hunting: Uses external intelligence like IOCs or IP addresses.
Hypothesis-Based Hunting: Builds investigations from analytical or contextual insights.
Investigation Using IOAs: Focuses on adversary behavior and attack methods.
Behavioral-Based Hunting: Detects abnormal user or network behavior patterns.
What tools are essential for threat hunting?
Key tools for effective threat hunting include:
SIEM (Security Information and Event Management) systems
EDR (Endpoint Detection and Response) solutions
NDR (Network Detection and Response) platforms
MDR (Managed Detection and Response) services
Security analytics platforms
Threat intelligence platforms
UEBA (User and Entity Behavior Analytics) systems
These tools help aggregate data, detect anomalies, and support human analysis.
How is threat hunting different from threat intelligence?
Threat intelligence gathers and analyzes external information about threats, such as attack methods and vulnerabilities. Threat hunting uses that intelligence to actively search for threats within an organization’s environment. Threat hunting is hands-on and proactive, while threat intelligence is primarily data-driven and strategic.
What is RetroHunting and why is it important?
RetroHunting is the practice of reanalyzing previously collected data using updated threat intelligence. It helps detect threats that were missed during real-time analysis. This method is especially valuable when dealing with systems that discard data after real-time processing, such as certain IDS or streaming analytics tools.
What are TTPs in cybersecurity?
TTPs stand for Tactics, Techniques, and Procedures:
Tactics: The attacker’s objectives (e.g., data theft).
Techniques: The methods used to achieve those goals (e.g., phishing).
Procedures: The specific steps or tools used by the attacker.
Analyzing TTPs helps security teams detect patterns and anticipate future actions, making threat detection more strategic and effective.
What does reducing dwell time mean in cybersecurity?
Dwell time is the length of time a threat actor remains undetected in a system. Reducing dwell time minimizes potential damage by identifying threats earlier in the attack lifecycle. Threat hunting plays a critical role in reducing dwell time through early detection and response.
What are some examples of threat hunting in practice?
- Detecting lateral movement: Identifying unauthorized access attempts across endpoints.
Identifying stealthy malware: Investigating abnormal network traffic to unknown domains.
Hunting insider threats: Finding unusual behavior from privileged user accounts.
Detecting backup persistence: Auditing persistence techniques and uncovering hidden malware.
How does threat hunting strengthen cybersecurity?
Threat hunting enhances cybersecurity by enabling organizations to detect threats that evade automated defenses. It improves incident response, reduces dwell time, and supports a proactive security culture.

