File security is a complex cybersecurity challenge that impacts organizations across all industries. As companies worldwide transition to digital infrastructure and depend on more third-party tools and services to host and manage their digital assets, the attack surface for increasingly sophisticated malware continues to expand.
Understanding file protection begins with a fundamental understanding of what file security is. We must understand not only what file security means, but why it is such an indispensable part of any organization’s cybersecurity strategy before we can explore file security best practices.
What is File Security?
File security is defined by safe access, distribution, and storage of digital files. These include documents, corporate secrets and business-critical information, log files, and source code. File security measures prevent these assets from being deleted, tampered with, or accessed by unauthorized parties.
Files must often be transferred both in and out of organizations, shared with multiple stakeholders, and distributed to partners working on numerous projects. Files in transit from one secure point to another are inevitably exposed—and therefore vulnerable to attacks. Bad actors may exploit these critical points of vulnerability to penetrate organizational defenses and introduce hidden malware that can easily go undetected.
In 2024 alone, there have been several high-profile data breaches impacting huge organizations from tech companies like Microsoft to financial institutions like JP Morgan. No business, no matter how large or small, is exempt from potential file security risks.
Understanding File Security
Defining the concept of file security and gaining a true understanding are two different exercises; along with the definition, file security can be broken up into five distinct pillars:
To prevent the upload of malicious or sensitive files to protected networks, threats must be stopped from being uploaded at the perimeter. Files need to be scanned for malware, vulnerabilities, and sensitive data before they are uploaded to web applications on platforms such as AWS and Microsoft Azure, or as they pass through load balancers and WAFs.
Securing networks from web-based threats by filtering Internet-bound traffic is critical, especially when it comes to protecting web gateways and enterprise browsers from files downloaded from unfamiliar websites.
Throughout the file transfer process, files need to be transferred securely—internally or externally—across MFT (managed file transfer) solutions. This prevents the interception, alteration, or theft of proprietary data for files in transit
Services like Google Drive, Microsoft 365, or Box allow organizations to share and synchronize files seamlessly. Protect the integrity and confidentiality of these collaborative files to mitigate the risk of data leaks and stay compliant with data protection laws.
Prevent data breaches, downtime, and compliance violations by securing data storage solutions across both cloud and on-premises storage environments such as AWS S3, NetApp, Wasabi, and/or Dell EMC.
Key Threats to File Security
To better understand preventative measures and keep your files secure, it’s important to understand emerging threats that could compromise your organization’s digital assets:
Malicious files, which can be common productivity files like office documents and PDFs, can infiltrate your file system via emails, websites, and any platform that allows the sharing of files and links. Ransomware is an increasingly common and disruptive type of malware, requiring organizations to pay hefty sums in exchange for sensitive data held for ransom.

Your partners’ vulnerabilities are your vulnerabilities, particularly if they interact with your data or systems. Even if your house is in order, weaknesses in third-party libraries or APIs could enable attackers to breach your file system and access sensitive information.

Attackers may exploit weaknesses in an organization's network when it connects with cloud-based applications, often through APIs or simple misconfigurations. While providers like Salesforce may enforce their own security policies, cybersecurity is a shared responsibility between providers and users.
Attackers often manipulate members of an organization to obtain access to sensitive information. Phishing is the most common type of social engineering attack, employing seemingly authentic messages to deceive employees into disclosing login details or unwittingly installing malicious software.
File Security Best Practices
To protect files, organizations must adopt a multi-layered approach encompassing physical, software, and procedural measures:

The principle of least privileges (POLP) mandates granting only the minimum necessary permissions needed to perform a task. This way, in the event of a security breach, employee accounts will be limited only to the resources that are absolutely necessary, rather than giving attackers an entryway into the entire organization’s assets.

Using tools like Deep CDR (Content Disarm and Reconstruction) enables you to sanitize files before they enter your file system, preventing any potentially malicious code from penetrating your organization’s defenses. This prevents zero-day attacks by removing any code that is either non-essential or out-of-policy from over 150 supported file types.

Using multiple antivirus engines to scan files in your organizations can help you eliminate up to 99% of known threats. With tools like Multiscanning, you can quickly and efficiently process files with 30+ AV engines to ensure maximum detection.
OWASP Top 10
The Open Web Application Security Project (OWASP) Top 10 is a list of the most common web application security risks based on extensive research and surveys. This list receives regular updates and is widely regarded as an industry standard for secure web application development. Some of these risks include:
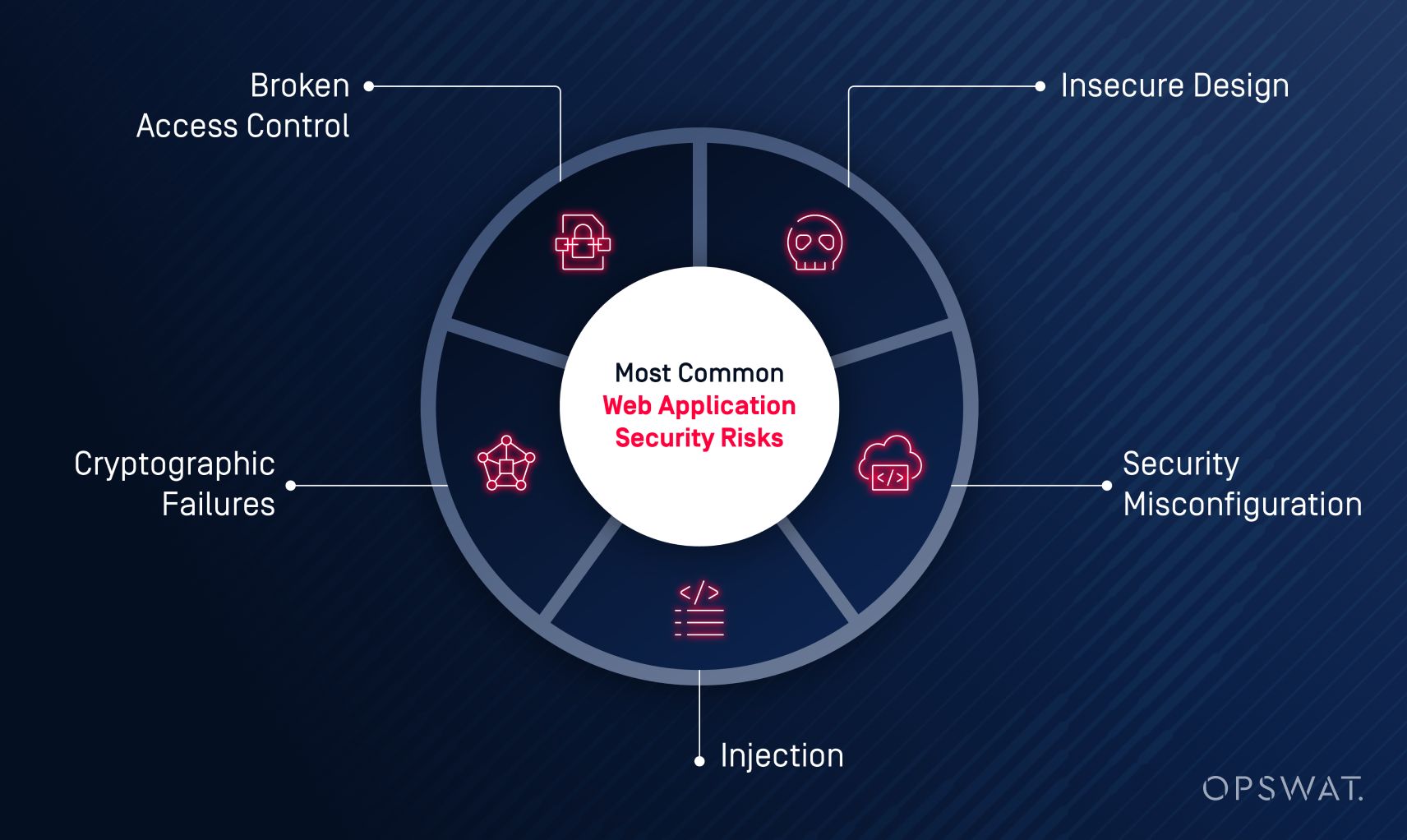

Injection attacks exploit vulnerabilities in web applications that accept easily compromised data, which can take the form of SQL injection, OS command injection, and Cross Site Scripting (XSS). By inserting malicious code into input fields, attackers can execute unauthorized commands, access sensitive databases, and even control systems.

Highly configurable application servers, frameworks, and cloud infrastructure can have security misconfigurations such as overly broad permissions, unchanged insecure default values, or overly revealing error messages, providing attackers with easy ways to compromise applications.
The Impact of Compliance
Stringent data protection regulations such as GDPR and HIPAA make compliance a key component in shaping file security strategies. Non-compliance not only exposes organizations to legal liabilities but also tarnishes their reputations and erodes customer trust.
It’s especially important to have security measures in place to prevent the exposure of sensitive information and reduce your organization’s liability in the event of a data breach. Tools like Proactive DLP (Data Loss Prevention) can scan, detect, and redact secrets and other sensitive information in files to help your organization meet compliance standards.
Further reading: What is Data Loss Prevention (DLP)?
Conclusion: Secure Files and Prevent Data Breaches
File security is an indispensable element in safeguarding organizational assets and preserving data integrity. By embracing robust security measures, organizations can mitigate the risk of malware exposure or ransomware attacks, foster trust, and navigate the evolving threat landscape with confidence. Implementing a multi-layered security strategy and prioritizing proactive measures to mitigate risks and safeguard sensitive information today can prevent costly data breaches tomorrow.