Data loss prevention is a security measure that protects organizations from unauthorized access, transfer, or sharing of sensitive information and data.
Often referred to as data loss protection, this solution encompasses strategies, policies, and technologies aimed at preventing the unauthorized dissemination or loss of sensitive data. DLP helps organizations detect and prevent potential data breaches by monitoring and controlling data transfers, identifying sensitive information and preventing access by redacting or restricting access.
Financial institutions, hospitals, public services, and many other organizations around the world frequently handle private, highly sensitive information about their customers and clients. As that information continues to be digitized and stored both on-premises and in the cloud, the attack surface for data breaches continues to grow. Data loss prevention (DLP) is a critical component in safeguarding sensitive information from unauthorized access and breaches.
DLP solutions protect various types of sensitive data, including:
- Personally Identifiable Information (PII)
- Payment Card Information
- Intellectual Property (IP)
- Protected Health Information (PHI)
- Company Confidential Information
- How Data Loss Prevention Works
- Why is DLP Important?
- Main Causes of Data Leakages
- Types of Data to Protect with Data Loss Prevention
- Defining and Setting Up DLP Policies
- Customizing Data Loss Protection Policies to Meet Business Needs
- DLP Data Loss Prevention Best Practices
- How to Investigate and Resolve Data Loss Prevention DLP Incidents
- Data Loss Prevention – What to look for in a DLP Solution
- AI and Machine Learning in Data Loss Protection
- Conclusion – Why Data Loss Prevention Matters
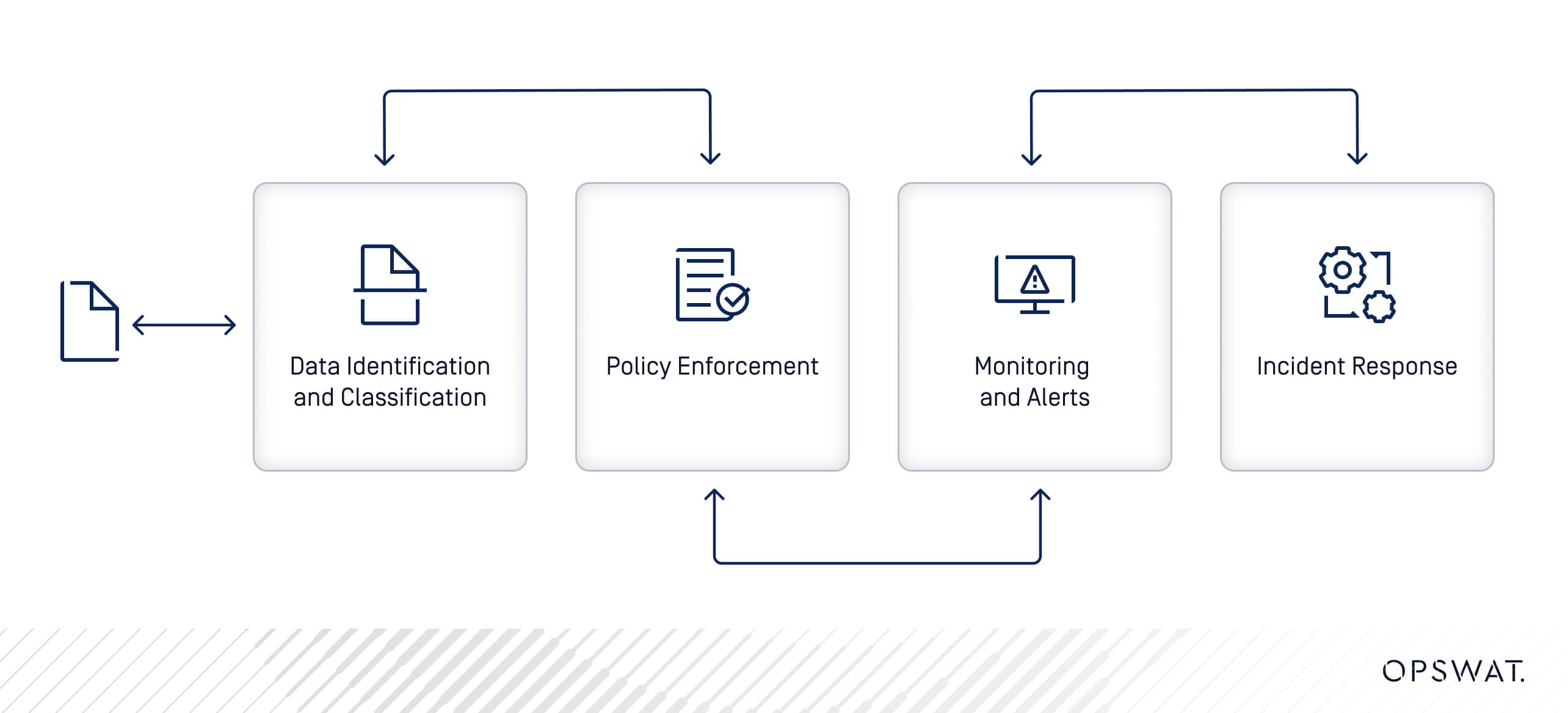
How Data Loss Prevention Works
DLP operates by identifying, monitoring, and protecting sensitive data through various mechanisms:
- Data Identification and Classification: DLP solutions scan data repositories to identify and classify sensitive information.
- Policy Enforcement: DLP solutions enforce predefined policies to control access and data transmission.
- Monitoring and Alerts: Continuous monitoring of data movement triggers alerts when potential breaches are detected.
- Incident Response: DLP data loss protection solutions provide tools for investigating and mitigating data breaches.
Why is DLP Important?
Data Breaches and Their Impact on Businesses:The average cost of a data breach in 2023 was approximately $4.45 million. The financial and reputational damage from data breaches underscores the importance of robust data protection measures.
Legal and Compliance Reasons for Implementing DLP: Regulations such as GDPR, HIPAA, and PCI-DSS mandate strict data protection standards. Implementing DLP helps organizations comply with these regulations, avoiding legal penalties and fines.
Implementing DLP Solutions for Cost Savings: While the upfront investment in data loss protection DLP solutions may seem like a financial sacrifice, it pales in comparison to the potential costs associated with data breaches, including financial losses, legal fees, and reputational damage.
Main Causes of Data Leakages
Internal Leaks (Insider Threats)
Threats to sensitive information often come from within organizations. Sensitive data may be compromised due to unintentional actions by employees, such as sending emails to incorrect recipients or mishandling data. This could be due to lack of training and awareness, as well as weak or poorly enforced security policies that leave organizations vulnerable to exposure of sensitive data.
While accidents are most often to blame, disgruntled employees or contractors with access to sensitive data can intentionally steal or misuse information for personal or financial gain.
External Attacks (Hackers, Malware)
Cybercriminals use various techniques, including social engineering, phishing, compromised files, and network vulnerabilities to gain unauthorized access to sensitive data. Malware can be embedded in productivity files, email attachments, removable media, or through exploitation of system bugs and unpatched vulnerabilities.
Types of Data to Protect with Data Loss Prevention

Personally Identifiable Information (PII)
PII includes any information that can identify an individual, such as names, addresses, and social security numbers. Protecting PII is critical to protect customer privacy and ensure compliance.

Payment Information
This category includes credit card details and related financial information. Safeguarding this data is essential to prevent financial fraud and comply with PCI-DSS standards.

Intellectual Property (IP)
IP encompasses proprietary data, trade secrets, and patents. Protecting IP is vital for maintaining a competitive edge and fostering innovation.
Protected Health Information (PHI)
Protected Health Information (PHI) includes medical records and health-related data. Compliance with HIPAA ensures the privacy and security of patient information.

Company Confidential Information
This category includes sensitive business information, such as financial records, strategic plans, and internal communications, which must be protected to maintain business integrity.
Defining and Setting Up DLP Policies
Thanks to the increasing complexity of corporate networks, as well as the evolving nature of advanced cybersecurity threats, it’s important to implement effective DLP strategies to combat data leaks. Part of this defense strategy must involve a robust set of DLP policies, especially for organizations looking to maintain compliance with regulations such as HIPAA, PCI DSS, and GDPR.
Effective DLP policies define how sensitive data should be handled and protected within an organization. These policies should align with the organization’s risk profile and regulatory requirements. Data classification rules categorize data based on sensitivity and importance, guiding the application of appropriate security measures.
Some examples of common data loss protection DLP policies include:
- Preventing the transmission of credit card details outside the secure network. This ensures only authorized users with privileged access can obtain this data without inadvertently exposing it to third parties.
- Blocking emails containing social security numbers and other sensitive information from being sent to unauthorized recipients. DLP software can automatically detect sensitive information like this and redact it before it is sent to its recipient, or block the file from being shared.
Customizing Data Loss Protection Policies to Fit Business Needs
DLP policies must be tailored to the specific needs of the organization, ensuring effective protection and compliance with relevant regulations. It’s also important to factor in existing security measures, which may be integrated with the organization’s DLP strategy. That could include firewalls or other monitoring systems that may serve a key role in enforcing DLP policies.
DLP Data Loss Prevention Best Practices
To stay ahead of the curve, these best practices will go far in ensuring your organization stays prepared for incoming threats and maintains effective DLP strategies within.

Conduct Risk Assessments
Regular risk assessments help identify where sensitive data resides and how it is used, informing the development of effective DLP policies. Failure to conduct risk assessments may leave openings for threat actors to access sensitive data via access points that receive little attention or monitoring.

Implement Strong Access Controls and Authentication
Limiting access to sensitive data and enforcing strong authentication methods reduces the risk of unauthorized access. This includes implementing an organization-wide principle of least privilege, which only gives employees the access they need for assets relevant to their roles, rather than access to the entire organization’s assets.
Regularly Update and Patch Systems
Keeping systems and software up to date with the latest patches and security updates is crucial for preventing vulnerabilities. Finding automated solutions is critical, as most code bases include numerous third-party dependencies that also need to be identified, checked regularly, and patched whenever updates are made available.

Employee Training and Awareness Programs
Educating employees about data security best practices and the importance of DLP helps prevent accidental data breaches. This prevents instances of social engineering like phishing, as trained employees are more readily able to identify deceptive links, emails, and messages from threat actors.

Incident Response Planning and Management
Having a well-defined incident response plan ensures that data breaches are promptly and effectively addressed, minimizing their impact. An incident response plan should adequately assess and alert the organization to data breaches, enact an automatic containment and assessment response, and adjust operations accordingly to ensure minimum exposure.

When a DLP alert is triggered, it’s important to:
- Investigate the incident to determine its cause.
- Contain the breach to prevent further data loss.
- Assess the impact of the breach.
- Notify relevant stakeholders.
- Implement corrective actions to prevent future incidents.
How to Investigate and Resolve Data Loss Prevention DLP Incidents
Effective incident investigation involves analyzing logs, identifying the source of the breach, and implementing measures to mitigate risks. Automation tools can enhance incident response by providing real-time alerts, automated remediation actions, and detailed forensic analysis. Minimizing the impact of data loss incidents involves prompt detection, effective containment, thorough investigation, and continuous improvement of security measures.
Data Loss Prevention – What to look for in a DLP Solution
When implementing a DLP solution, organizations should ensure the following needs are accounted for:
- Securing data in motion: Implementing technology at the network perimeter can monitor traffic to identify sensitive information being transmitted in breach of security policies.
- Securing endpoints: Endpoint-based agents manage the transfer of information among users, user groups, and external entities. Some of these systems can intercept and block communications in real time, providing feedback to users.
- Securing data at rest: Access control, encryption, and data retention policies are used to protect stored organizational data.
- Securing data in use: Certain DLP systems can track and flag unauthorized actions by users, whether intentional or accidental, during their interaction with data.
- Data identification: It is essential to determine whether data requires protection. This can be done manually by applying rules and metadata or automatically using machine learning techniques.
- Data leak detection: DLP solutions, along with other security systems like IDS, IPS, and SIEM, can detect abnormal or suspicious data transfers and alert security personnel to potential data leaks.
AI and Machine Learning in Data Loss Protection
AI and machine learning technologies enhance DLP by enabling advanced threat detection, anomaly detection, and predictive analytics. AI can crawl through hundreds of documents quickly and find instances of sensitive data that may be at risk of exposure. With machine learning (ML), these tools can even adapt and improve their efficacy over time.
AI can be particularly adept at behavioral analysis, identifying unusual patterns and anomalies in data activity, providing early warning signs of potential breaches. Detecting unusual behavior can be a critical preemptive measure for organizations to minimize the exposure and damage of a data breach.
Conclusion – Why Data Loss Prevention Matters
Data loss prevention (or data loss protection) is a crucial element of modern cybersecurity strategies. By implementing comprehensive DLP solutions, organizations can protect sensitive information, comply with regulatory requirements, and mitigate the risks of data breaches. As cyber threats continue to evolve, adopting robust DLP measures will be essential for maintaining data security and business integrity.
To see how OPSWAT’s innovative solutions can keep your critical infrastructure secure, talk to an expert today.

