In early February, the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), the Federal Bureau of Investigations (FBI), and other organizations published an advisory about the urgent risk posted by People’s Republic of China (PRC). At the time, they specifically warned critical infrastructure organizations about state sponsored cyber actors, calling out Volt Typhoon by name, that are positioning themselves to carry out disruptive or destructive cyberattacks against U.S. critical infrastructure.
According to the February advisory, Volt Typhoon (also known as Vanguard Panda, BRONZE SILHOUETTE, Dev-0391, UNC3236, Voltzite, and Insidious Taurus) has already compromised the IT environments of critical infrastructure organizations in the communications, energy, transportation systems, and water and wastewater systems sectors in the United States and its territories, pre-positioned to enable lateral movement to operational technology (OT) assets to disrupt functions. In March, the Five Eyes allies issued another alert and guidance on how critical infrastructure agencies can defend themselves against these threats, urging leaders to recognize cyber risk as a core business risk and fundamental to national security. Most recently, a U.S. Senator warned of the threat posed by Volt Typhoon in a letter to CISA.
Volt Typhoon Plays the Long Game
Unlike some malicious actors, Volt Typhoon doesn’t leverage malware to gain and maintain access to networks. Instead, they rely on valid accounts and use strong operational security to remain undiscovered for extended periods of time — in some cases five years or more. By using the built-in functions of a system, this threat group leverages “living off the land” (LOTL) techniques, including using native tools and processes on systems in multiple IT environments. This helps them evade detection, leveraging in-depth research about the target organization and environment to tailor their tactics, techniques, and procedures accordingly. Volt Typhoon also dedicates ongoing resources to maintain persistence and increase understanding of the target environment over time, far beyond the initial compromise.
Many organizations lack the ability to detect and identify malicious activity, making it more difficult to differentiate between legitimate and malicious behavior. To protect themselves against LOTL techniques, organizations must adopt a comprehensive and multifaceted approach to cybersecurity. The joint guidance provided by CISA offers broad detection and hardening best practices that can help organizations position themselves to be more effective at detecting and mitigating these techniques. Critical infrastructure sectors must apply these best practices, placing additional focus on improving security in the supply chain.
Secure the Supply Chain
Increasingly, organizations are facing sophisticated attacks in the supply chain. According to a European Union Network and Information Security Agency (ENISA) report, “Supply Chain Compromise of Software Dependencies” continues to rank as the highest threat, due doubtless to the integration of third-party suppliers and partners in the supply chain. Critical infrastructure is far from immune to this trend, opening potential avenues for state-sponsored actors like Volt Typhoon to gain and maintain access that could put organizations and individuals at risk. To counteract these threats, organizations must secure both the software and hardware supply chains and adopt secure-by-design principles.
Software Supply Chain
It’s no secret that there are vulnerabilities in the software supply chain, including the insertion of malicious code and use of vulnerable third-party components. Malicious code can allow unauthorized access, lead to data breaches, and sometimes even result in complete system takeovers. Software developers often use third-party components, including open-source software, to accelerate development and add new functionality. Unfortunately, these components may contain known vulnerabilities, newly discovered vulnerabilities, or even have vulnerabilities introduced into the code base by a malicious actor.
As a recent example, it was reported that the Python Package Index (PyPI) – the go-to source for apps and code libraries written in Python Programming language – came under attack by users who likely used automated means to upload malicious packages, exploiting users' typos. They used a technique called typosquatting, creating package names similar to popular ones to infect user devices upon installation. This shows the critical need to verify source code libraries for dependencies and vulnerabilities and to address malware threats amidst the rapid integration of AI technologies without adequate security measures.

Similarly, as organizations adopt containerization and use repositories to manage source code and container images, malicious actors have access to an expanded attack surface. If malware infiltrates code and container repositories, it can propagate across the software application stack and cause widespread damage. Vulnerabilities in a single image can impact multiple applications and organizations.
To address these challenges, organizations must adopt rigorous code review processes, including using a software bill of materials (SBOM) that provides a formal record of all the components used in building software. This capability is critical when a new critical vulnerability is disclosed because it enables organizations to quickly ascertain if their code uses this software, where it exists, whether it poses a risk, and remediate it if it does. An SBOM helps identify vulnerable software components both in open-source software and in source code and containers, reducing risk exposure. This visibility also helps to ensure and demonstrate compliance with legal and regulatory standards by facilitating a rapid response to emerging threats.
Hardware Supply Chain
Securing the hardware supply chain is as critical as securing software components due to the interdependencies between hardware and software. Hardware can also introduce vulnerabilities, particularly via transient cyber assets, including mobile devices, removable media, and temporary networking equipment. Transient assets often enter an environment under the radar of traditional security measures. And because they are easy to move and modify, these assets are susceptible to misuse and tampering, becoming conduits for malware or unauthorized access to sensitive networks.
To address this risk, organizations should ensure that they are scanning and securing such assets before connecting them to any hardware in critical infrastructure environments, including identifying the country of origin. This allows organizations to identify assets containing malware, block unauthorized data access based on origin, identify restricted locations and vendors, and ensure regulatory compliance across regions. Ensuring that the hardware in use is sourced from reputable, secure sources mitigates the risk of embedded vulnerabilities that could be exploited later.
As IT and OT environments become increasingly interconnected, visibility into connected assets is vital to improving security and limiting the capabilities of malicious actors, including Volt Typhoon. Knowing the country of origin, as well as the firmware and software versions of devices, allows organizations to assess vulnerabilities more comprehensively and respond to threats with greater agility. Firmware and software updates often address security flaws, highlighting the need for awareness of version histories to maintain security hygiene. This information can also aid in complying with different regulatory standards and frameworks, as governments increasingly urge improvements in the technology supply chain.
Secure-By-Design Principles
Adopting secure-by-design principles is critical today to combat sophisticated threats such as Volt Typhoon and minimize the risk to critical infrastructure. The secure-by-design approach means that technology products are built to protect against malicious cyber actors successfully gaining access to devices, data, and connected infrastructure. According to CISA, “The authoring agencies recommend that software manufactures incorporate secure by design and default principles and tactics into their software development practices to strengthen the security posture for their customers.”
Volt Typhoon and similar actors are adopting increasingly sophisticated TTPs by exploiting vulnerabilities that might have been mitigated at the design phase of the software development lifecycle (SDLC). By embedding security into technology architectures and development processes, secure-by-design principles enable organizations to build systems that are inherently more resistant to intrusion, manipulation, and exploitation.
Protect Critical Infrastructure
While Volt Typhoon presents a significant threat at present, it would be foolish to believe that this group is the only one capable of the level of infiltration that CISA and others are warning against so urgently. Critical infrastructure organizations must position themselves to detect such intrusions and harden their environments against similar threats. Securing the supply chain is a vital step in improving security, particularly by understanding the complexities of the software supply chain, analyzing the complete SBOM, and being able to respond quickly to emerging vulnerabilities. Similarly, securing the hardware supply chain by ensuring visibility into connected assets enables organizations to block unauthorized access. A comprehensive security strategy rooted in a secure-by-design principles is essential and should leverage zero-trust technologies like content disarm and reconstruction, vulnerability assessments, data loss prevention, multiscanning and more.
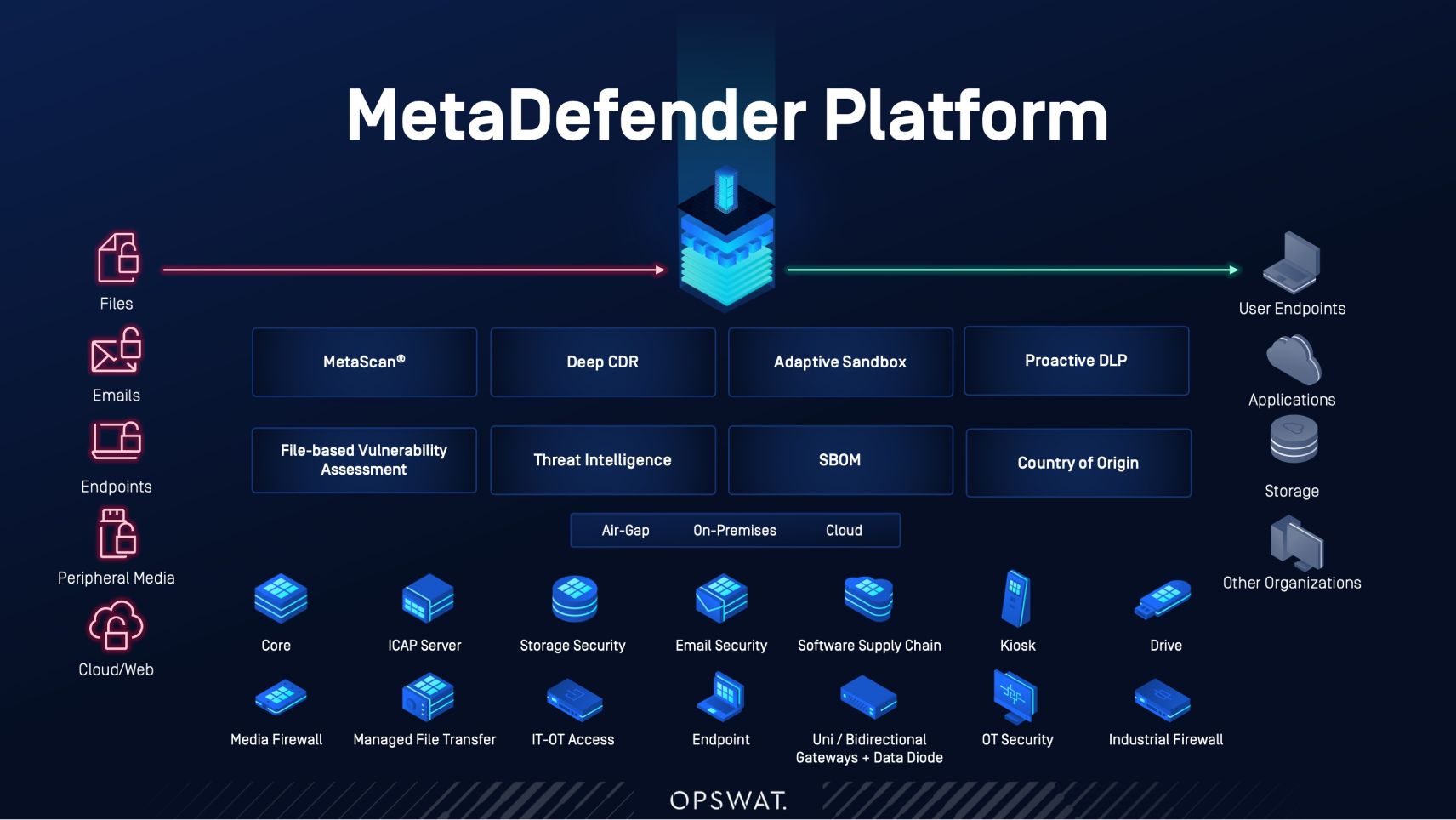
By proactively neutralizing malware and thwarting potential breaches, this approach significantly mitigates the threat of credential theft and other malicious activities. Furthermore, prioritizing software and hardware security ensures inherent resilience against cyber threats. Protecting the supply chain is a vital step organizations must take to ensure the safety and security of critical infrastructure.
Learn how OPSWAT can help protect against Volt Typhoon threats.

