Security experts emphasize the need for "defense in depth" to protect corporate networks from cybercriminals. This approach involves layering multiple defenses, including web application firewalls (WAF), application delivery controllers (ADC), and managed file transfer (MFT) solutions. These network security devices have become critical for organizations to safeguard their data, intellectual property, and network assets. They are designed to identify and prevent various security threats, such as DDoS, and offer network traffic management, application, and API protection.
While cloud and network security devices have proven effective at securing networks, they have limitations. To reduce risks caused by these limitations, cloud and network security follow the shared responsibility model. If you are relying solely on network security devices, it is difficult to gain visibility into the content hidden within network traffic, making it challenging for security teams to identify and address more complex threats like zero-days and advanced evasive malware. These limitations highlight the need for content inspection solutions that provide deeper content visibility to enhance an organization's security posture.
Table of Contents
- What is content inspection?
- Cybersecurity challenge: malicious file uploads
- Benefits of content inspection
- Limitations of firewalls, ADC, and MFT solutions
- The shared responsibility model in cybersecurity requires content inspection
- Key content inspection technologies
- Futureproof network traffic: enable content inspection with ICAP
What is Content Inspection?
Content inspection is a method of network-level, anti-malware, and data loss prevention that identifies malicious code and sensitive data by analyzing files in transit.
Content inspection typically begins with a network proxy, load balancer, or similar network appliance. It functions as an intermediary between the user and the requested content. The proxy relays network traffic containing file content, and passes that content to antivirus (AV) software that scans the content for potential threats or policy violations.
When content inspection is enabled, the network appliance examines the files passing through it, including the URL, headers, and payloads. It applies predefined rules and settings to search for specific patterns or keywords that may indicate malicious or inappropriate content. Regular expressions are often used to define these patterns and facilitate more advanced content matching. This technique involves examining data to find patterns in metadata and keywords indicative of safety and sensitivity. For example, creating a custom regular expression for social security and credit card numbers or the keyword "confidential."
The content inspection process can involve multiple stages and actions. It may filter out prohibited domains, block access to specific websites, scan files for viruses, or examine documents such as PDFs for sensitive information.
Content inspection is a helpful tool for organizations to maintain security, control, and compliance over their network traffic. By actively monitoring and filtering content, it helps prevent unauthorized access, data breaches, malware infections, and other potential risks. Content inspection can be customized to align with an organization's specific needs and requirements, allowing administrators to define the level of control and protection.
Content Inspection Cybersecurity Challenges
Malicious File Uploads
Malicious files pose a significant threat to network security. Files are constantly being transferred in and out of the network, and each file may contain known or unknown threats. Malware, viruses, and other malicious content can be uploaded without the administrator's knowledge, putting the entire system at risk.
These files can cause a range of problems, from minor system issues to major data breaches and attacks that can result in the loss of sensitive information. As a result, you need to have effective security measures in place to detect and prevent malicious file uploads, ensuring that users and networks remain secure.
Sensitive Data
Storing and sending sensitive data poses significant risks. Data breaches and cyberattacks can result in the theft of personal and confidential information, leading to identity theft, financial loss, and reputational damage. Furthermore, failing to comply with data protection rules and regulations can result in legal and financial consequences.
Benefits of Content Inspection
Inspecting content that moves through your network provides three major benefits: it detects malware and unknown threats hidden in content, helps your organization meet data protection regulations, and provides visibility into sensitive data moving through your network.
Identify Sensitive Data
Content inspection offers numerous benefits, including data visibility, control over sensitive data, more control, and automatic identification and classification of information. By inspecting file content, administrators can see exactly where sensitive data, such as name addresses, credit card information and personal health data, for example, is stored and control how it is used.
Meet Data Protection Regulations
Content inspection plays a crucial role in helping companies meet data protection regulations such as the Health Insurance Portability and Accountability Act (HIPAA), the Federal Information Security Modernization Act (FISMA), and the Payment Card Industry Data Security Standard (PCI-DSS). Companies can easily follow these regulations by applying protections to their regulated data.
Secure Network Traffic from Malicious Files
Organizations need effective security measures to detect and prevent malicious file uploads to ensure that their networks remain secure and that sensitive data stays protected. Content inspection solutions can be crucial in detecting and blocking malicious files, including those hidden within legitimate traffic, and preventing unauthorized data exfiltration. Content inspection can significantly enhance network security and protect sensitive data from potential breaches.
Limitations of Firewalls, ADCs, and MFT Solutions
Network security devices such as WAF, proxy, ADC, or MFT solutions have limitations in detecting and preventing malicious file uploads. They can't detect new and unknown malware, inspect the content of your files, and may not be effective in preventing file-based attacks. Content inspection solutions are needed to address these limitations. These solutions can detect, scan, and block malicious files, including those hidden within legitimate traffic, and prevent unauthorized data exfiltration. Using content inspection can significantly enhance security and protect sensitive data.
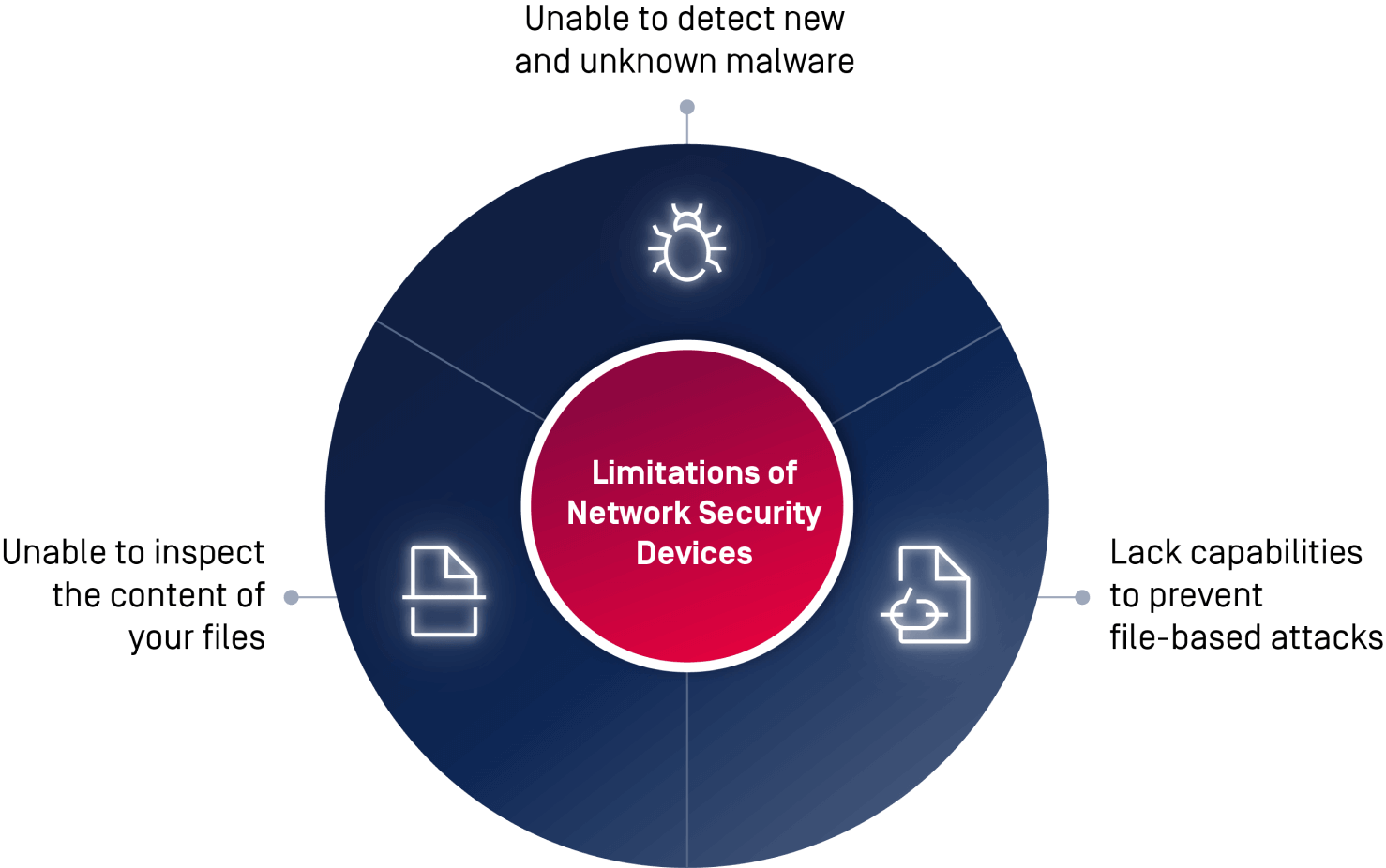
Content inspection solutions are needed to address these limitations. These solutions can detect, scan, and block malicious files, including those hidden within legitimate traffic, and prevent unauthorized data exfiltration. Using content inspection can significantly enhance security and protect sensitive data.
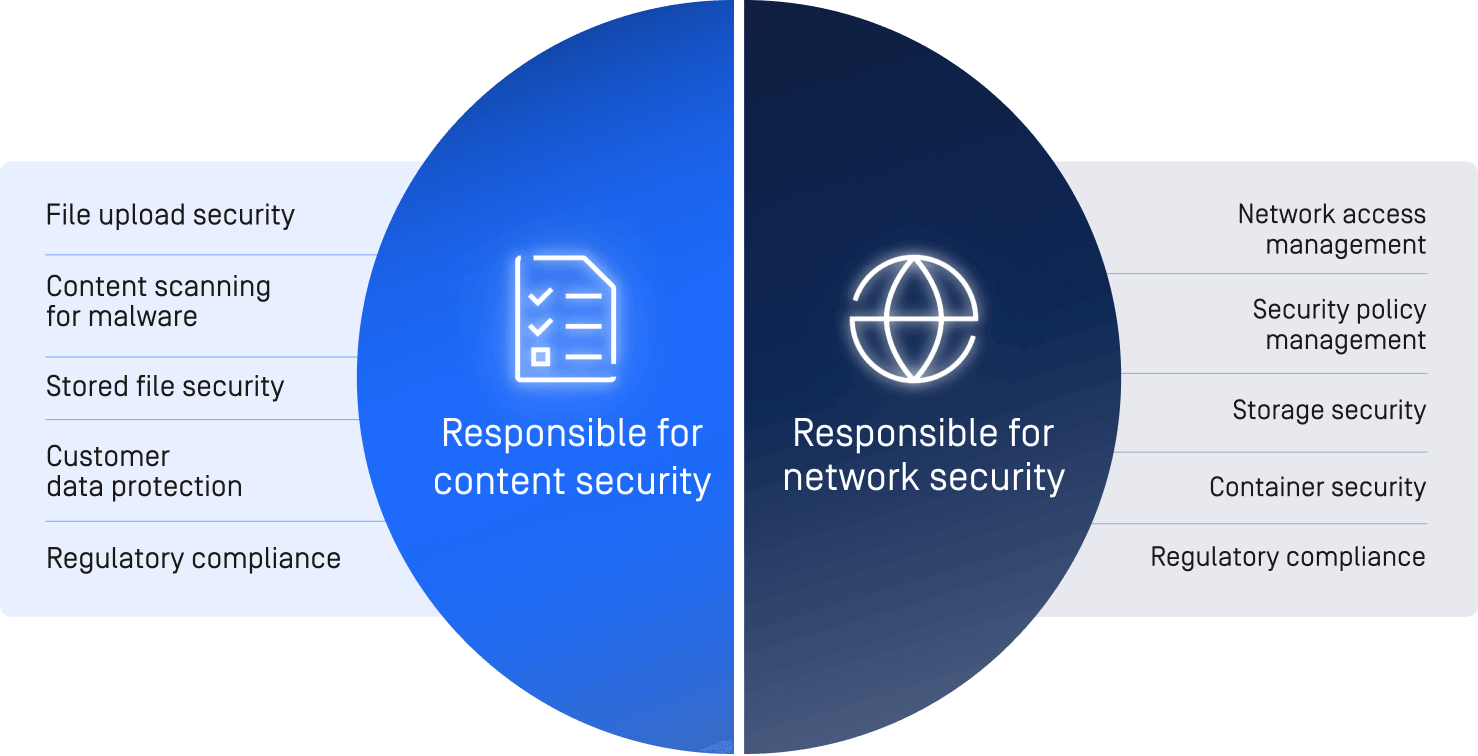
The Shared Responsibility Model in Cybersecurity
When using public cloud services, it's important to understand the concept of "shared responsibility." While cloud providers are responsible for securing their infrastructure, organizations are responsible for securing their data and applications. This division of responsibilities may vary between cloud providers and services.
Key Content Inspection Technologies
Content inspection technologies provide visibility into network traffic. This visibility is crucial in demonstrating compliance, securing against file-based threats, and passing security and compliance audits.

Antivirus Scanning with Multiple Antivirus (AV) Engines
Using a single AV engine offers limited protection. According to OPSWAT research, a single AV engine can detect 40%-80% of malware and viruses. Moreover, each AV engine has its strengths and weaknesses. Scanning with multiple engines, referred to as multiscanning, improves detection rates and reduces outbreak detection times. Multiscanning makes your network more resilient to new malware outbreaks and targeted attacks. You also benefit from multiple technologies like machine learning, artificial intelligence, and heuristics. Each engine specializes in different threats; while one may excel at detecting ransomware, another may be proficient at identifying trojans.

Data Loss Prevention (DLP)
Data Loss Prevention (DLP) plays a crucial role in averting potential data breaches and complying with regulatory standards by identifying sensitive and confidential data such as credit card numbers and social security numbers within files. Optical Character Recognition (OCR) technology can identify and redact sensitive information in image-only PDF files or PDF files containing embedded images. In addition to identifying and redacting sensitive content, DLP goes a step further by removing metadata that may contain potentially confidential information. By detecting metadata, DLP enhances security and reduces the risk of unintentionally exposing confidential data.

Content Disarm and Reconstruction (CDR)
Content inspection technology can also remove threats from files using Content Disarm and Reconstruction (CDR) to deconstruct a file, eliminate potential threats, and reconstruct a safe version. This technology ensures that unknown threats like zero-day threats are neutralized before reaching the user.
Futureproof Network Traffic: Enable Content Inspection with ICAP
ICAP solutions utilize the Internet Content Adaptation Protocol (ICAP) to provide specialized services such as anti-malware scanning. Since ICAP is lightweight, it allows teams to free up resources and standardize the implementation. By diverting your traffic to a dedicated server running an ICAP solution, all files passing through the system can be scanned using the same policy.
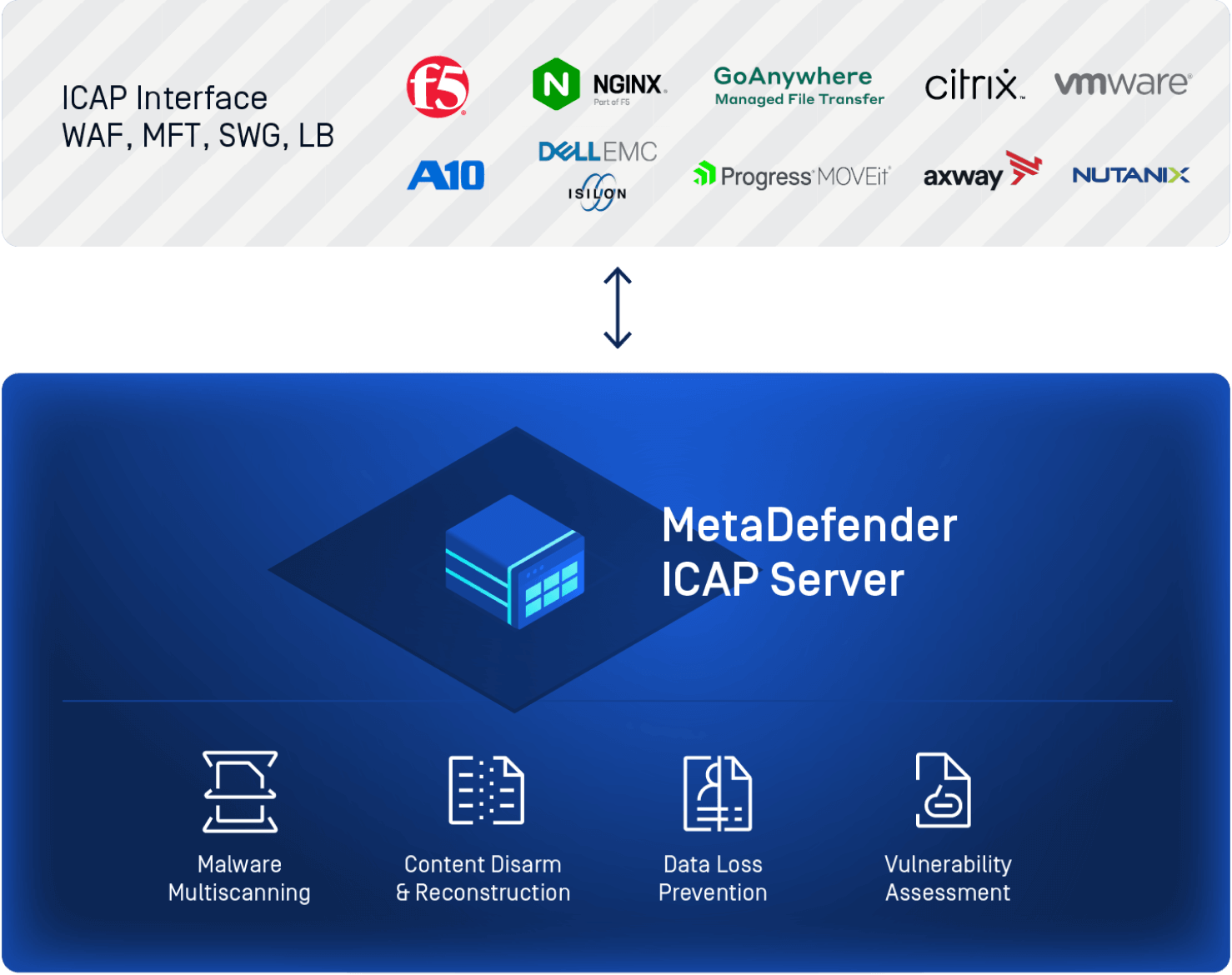
This approach is a highly effective security solution as it allows the network appliance to focus on its primary function, such as performance, while the ICAP service analyzes, assesses, and sanitizes files with minimal impact on performance. ICAP solutions can provide broad protection at the network perimeter and an additional layer of trust within the organization and with third-party partners. It’s important to follow best practices to protect your network traffic.
OPSWAT Content Inspection: MetaDefender ICAP Server
OPSWAT's content inspection solution – MetaDefender ICAP Server can provide deeper content visibility, detect and block malicious files, and prevent unauthorized data exfiltration for a wide range use cases .
To futureproof your organization's network traffic, talk to our security experts.

