Over the past decade, a convergence of technologies has made network security a challenging undertaking. The growing prevalence of web applications using file sharing portals has expanded the attack surface.
The cybersecurity risks associated with uploading files are numerous. Malware can infiltrate networks through file uploads containing malicious code or URLs, or by exploiting previously undetected zero-day vulnerabilities.
In this article, we'll outline best practices for protecting networks against these types of attacks. Lastly, we'll outline how an ICAP antivirus (AV) solution can add an extra layer of protection, securing your applications against malicious file uploads.
1. Find the Best Combination of Network Security Solutions for Your Needs
There are a variety of network devices, many of which provide network security. These networking devices handle network security tasks such as managing network access, security policy management, storing regulatory compliance data, and ensuring container security.
Proxies, such as forward and reverse proxies, shield connections by hiding IP addresses and providing a single point of entry and exit. Load balancers offer similar functionality, but also provide orchestration, policy management, and automation for large-scale applications.
Web application firewalls (WAFs) inspect network traffic to prevent unauthorized access and protect against threats like cross-site scripting and distributed denial of service attacks. Next-generation firewalls (NGFWs) focus on traffic moving through layers 3-4 to protect internal networks from external attacks. Ingress controllers are similar to load balancers and proxies but designed for container environments.
Secure web gateways (SWGs) act as a filter between users and internet traffic, blocking connections to unapproved internet applications and services and encrypting traffic. Application delivery controllers (ADCs) offer proxy, load balancing, and WAF functionality, as well as an API gateway, application acceleration, and SSL termination. They are typically managed by the development operations team instead of a security team. Finally, managed file transfer (MFT) enables secure and managed large file transfers, which is not provided by traditional FTP or HTTP services.
2. Scan Files Entering Your Network and Storage Devices
Even with these solutions in place, there is still a risk of malicious files entering your network or being stored in your system. To mitigate this risk, it is crucial to implement antivirus scanning on all files entering into and stored within your network. This way, you can detect and remove any malware before it can cause harm. With a comprehensive security strategy that includes multiple layers of protection, organizations can better safeguard against the ever-evolving threats in today's digital landscape.
Along the same lines, the transfer of large numbers of files among internal teams and customers can create opportunities for attackers. External sources (third-party vendors, external partners) may inadvertently introduce malware into the environment. For this reason, it is highly advisable for organizations to examine the content of all files being transferred into their networks by performing scans to detect and block malware at the perimeter.
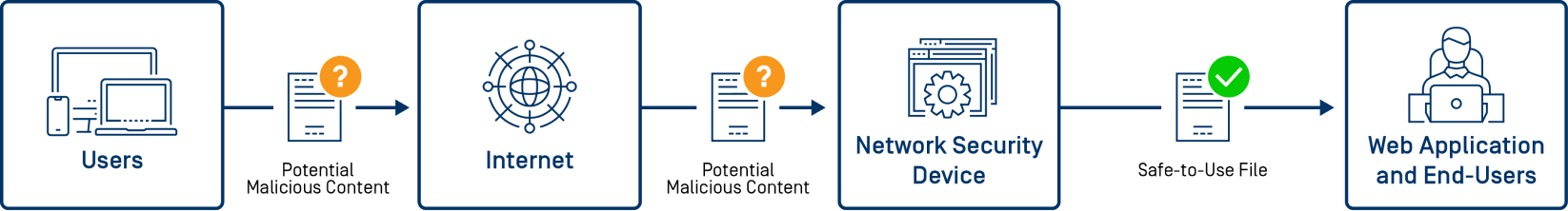
3. Secure Against Common Threats
Antivirus and anti-malware engines struggle to keep pace with the volume of new threats developed by attackers. The situation gets worse when you consider the increasing complexity of malware and advanced persistent threats (APTs) targeting organizations. Further, unknown malware and zero-day threats continue to plague security teams.
Scanning files for known threats is an effective first layer of defense against malicious file uploads. However, legacy AV solutions using just one or two engines aren’t able to detect enough malware fast enough to adequately protect the network. Antivirus research reveals that it takes more than 20 antivirus and anti-malware engines to reach detection rates greater than 99%.
4. Detect unknown threats beyond traditional antivirus scanning
The increase in sophistication and complexity of malware allows it to bypass traditional defenses. For example, anti-malware engines detect known threats, allowing zero-day malware to easily defeat signature-based antivirus solutions. Productivity files like Word, Excel, PDF, archives, or image files can be used to hide embedded threats in macros and scripts—which are not always detectable with AV engines or dynamic analysis solutions like sandboxes.

One effective prevention technique is to remove all potential malicious embedded object with data sanitization, or Content Disarm and Reconstruction (CDR). Deep CDR technology removes malicious file content without relying on malware detection. It processes the incoming files, then regenerates these files in a way that ensures the new files are both usable and harmless. In other words, Deep CDR helps secure network traffic by preventing both known and unknown threats.
5. Redact Sensitive Information
Even with the best automated solutions in place, malicious insiders and negligent users may leak sensitive data. Additional solutions are needed to protect against data leaks and compliance violations.
Organizations have multiple reasons to worry about the exposure of personally identifiable information (PII), ranging from compliance regulations like PCI-DSS and GDPR to targeted cyber-attacks or unintentional insider leakage. To mitigate the risks of data loss, it is crucial to redact sensitive information in files that are uploaded or shared externally.
6. Increase Efficiency with an ICAP Solution
Using the Internet Content Adaptation Protocol (ICAP), an ICAP solution allows network security appliances to offload network traffic to a dedicated server for tasks like antivirus/anti-malware scanning or data sanitization. This ensures that all files are scanned using the same policy.
By diverting traffic to an ICAP server, network appliances can focus on their primary purpose, such as network performance, while the specialized ICAP server quickly analyzes and sanitizes passing files with minimal impact on performance. This approach is particularly effective for network security, as it provides broad protection at the perimeter, value-added services, and an additional layer of trust for both the company and third-party partners.

FAQs
What is an ICAP Server?
Internet content adaptation protocol servers (ICAP servers) are similar to an HTTP server, except that the application services ICAP requests. RFC3507 states, "ICAP requests MUST start with a request line that contains a method, the complete URI of the ICAP resource being requested, and an ICAP version string."
What is an ICAP Client?
An ICAP client is a software application that establishes connections with ICAP servers to send requests.
How to intercept the connection between an end-user or device and the internet?
You can extend transparent proxy servers. A transparent proxy, also known as an inline proxy, intercepting proxy or forced proxy, is a server that intercepts the connection between an end-user or device and the internet.
What are transparent HTTP proxy caches?
Transparent HTTP proxy caches are servers that intercepts the connection between the internet and an end-user or device and Internet content adaptation protocol servers (ICAP servers) are generally used to implement virus scanning and content filters in them.
What is content filtering?
You can use an ICAP filter to send a message to a pre-configured server for content adaptation. For example, this includes specific operations such as virus scanning, content filtering, ad insertion, and language translation.
What is an ICAP Resource?
Like an HTTP resource, but the Uniform Resource Identifier (URI) refers to an ICAP service that performs adaptations of HTTP messages.
What are request modification mode and response modification mode?
In "request modification" (reqmod) mode, a client sends an HTTP request to an ICAP server. The ICAP server may then:
- Send back a modified version of the request.
- Send back an HTTP response to the request.
- Return an error.
ICAP clients must handle all three types of responses.
OPSWAT MetaDefender ICAP Server – Trust Your Network Traffic
OPSWAT MetaDefender ICAP Server provides advanced threat protection for network traffic against malicious file uploads, zero-day attacks, and sensitive data exposure. MetaDefender ICAP Server scans and inspects all incoming file content before it reaches your organization’s network. The solution can be integrated with any ICAP-enabled network devices: load balancer, forward/reverse proxy, ingress controller, managed file transfer (MFT), and more. Learn more about MetaDefender ICAP Server

