ICAP (The Internet Content Adaptation Protocol) is a specialized protocol designed to enable efficient communication for executing HTTP/HTTPS messages between clients and external servers. It plays a crucial role in content inspection, adaptation and modification. Within the cybersecurity context, ICAP can be implemented for security scanning, and policy enforcement by offloading resource-intensive tasks to other specialized servers. By leveraging ICAP, organizations can enhance their security posture, optimize content delivery, and ensure compliance with security policies without significantly impacting network performance.
Technical Context
ICAP, or Internet Content Adaptation Protocol, is a lightweight, specialized protocol similar to HTTP that allows network edge devices to offload incoming content for specialized analysis. These content transformation activities can happen at edge servers.
At its core, ICAP acts as a communication method that allows an ICAP client to offload content modification, scanning, or analysis to a separate ICAP server, to function as an inline content filter as if the processing were happening locally. The ICAP client does not need to manage the underlying details—only the request and response format. This function works similarly to a Remote Procedure Call (RPC). This improves efficiency, scalability, and resource management within network environments.
The primary purpose of ICAP is content adaptation—modifying, analyzing, or scanning HTTP traffic before it reaches its intended destination. Historically, the ICAP protocol evolved to address the growing need for scalable, distributed content filtering and security processing in web traffic management. Over time, it has become a fundamental component in modern cybersecurity strategies, extending capabilities for various security use cases, such as malware scanning, data loss prevention, and compliance enforcement.
Understanding the basic architecture of ICAP requires recognizing its two key components: the ICAP client (typically a proxy or firewall, but can also be any network device) and the ICAP server (responsible for content processing). These components work together to ensure efficient and secure data handling across network infrastructures.
How ICAP Works
ICAP operates similarly to HTTP, utilizing request and response messages to facilitate content adaptation. This architecture distributes the processing load across multiple servers, moving away from a centralized, monolithic approach. By offloading tasks to ICAP servers, organizations can avoid expensive operations while enabling services such as virus scanning, parental controls, and content inspection.
In the cybersecurity context, ICAP integrates with various network security devices, including proxy servers, load balancers, ingress controllers, WAFs (web application firewalls), and MFT (managed file transfer) solutions. These appliances leverage ICAP for dynamic security processing, ensuring compliance with organizational policies and threat mitigation.
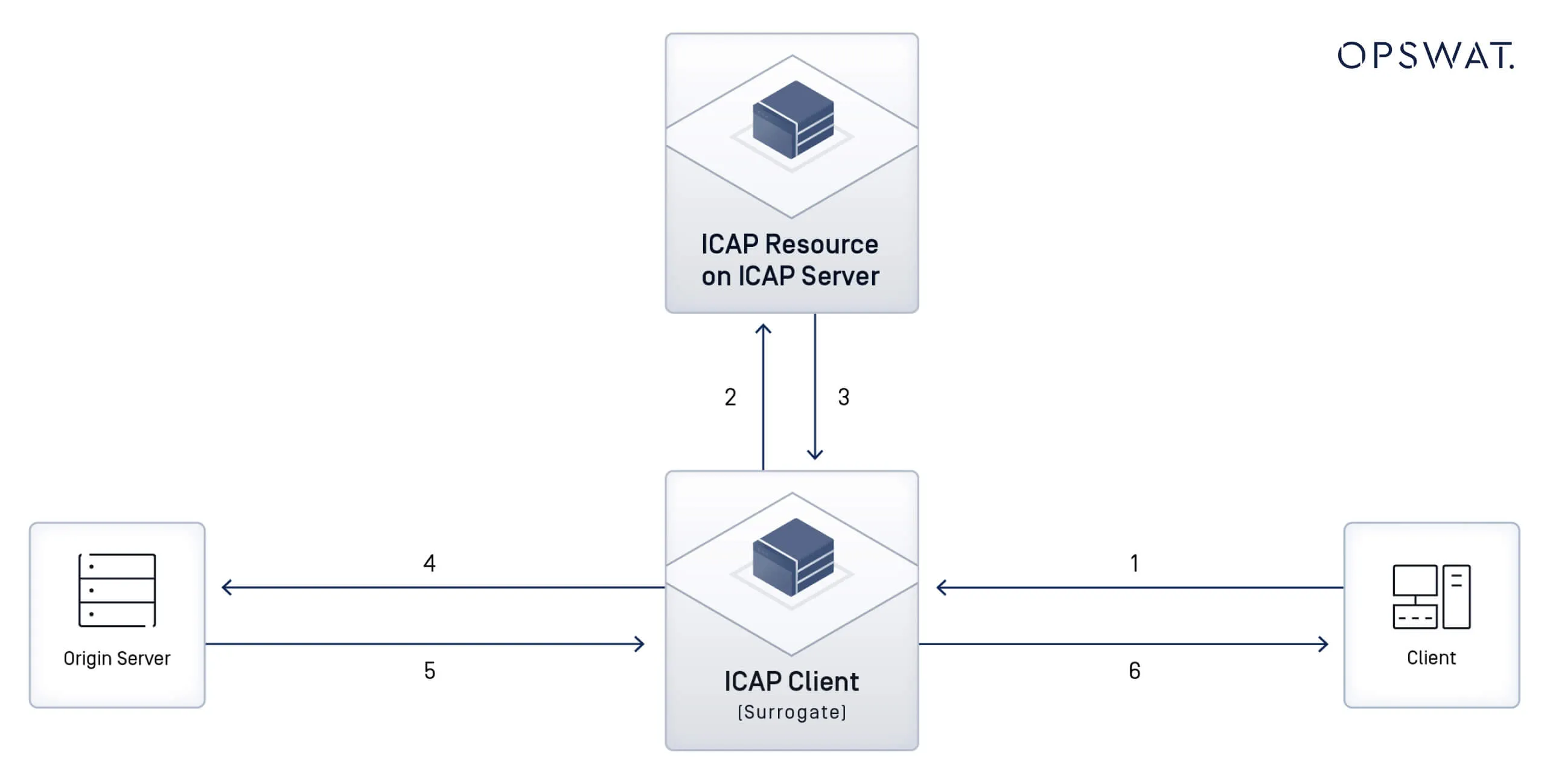
ICAP Client and ICAP Server
An ICAP client is a program that establishes a connection with an ICAP server to send requests for content adaptation. Typically, the ICAP client is a proxy or gateway that processes HTTP/HTTPS traffic on behalf of users.
The ICAP server, similar to an HTTP server, services ICAP requests by performing predefined content adaptation tasks. This may include scanning for malware, enforcing data loss prevention policies, or modifying content based on security rules.
ICAP Request/Response Cycle
- Initiate an ICAP request: The ICAP client (e.g., proxy server or firewall) sends an HTTP/HTTPS request for processing.
- Process the request on the ICAP server: The ICAP server scans, analyzes, or modifies the content based on security policies.
- Return the adapted content: The ICAP server returns the processed data to the ICAP client with necessary modifications or directives.
This cycle enables dynamic, scalable content adaptation, ensuring efficient processing without overloading core network infrastructure.
Key Features of ICAP
- Content preview: Allows partial content processing before full adaptation.
- Pipelining: Supports multiple requests in a single connection, reducing overhead.
- Content encoding support: Ensures flexibility in adapting various data formats.
These features improve efficiency, allowing seamless integration into modern network security frameworks.
ICAP Modification Methods
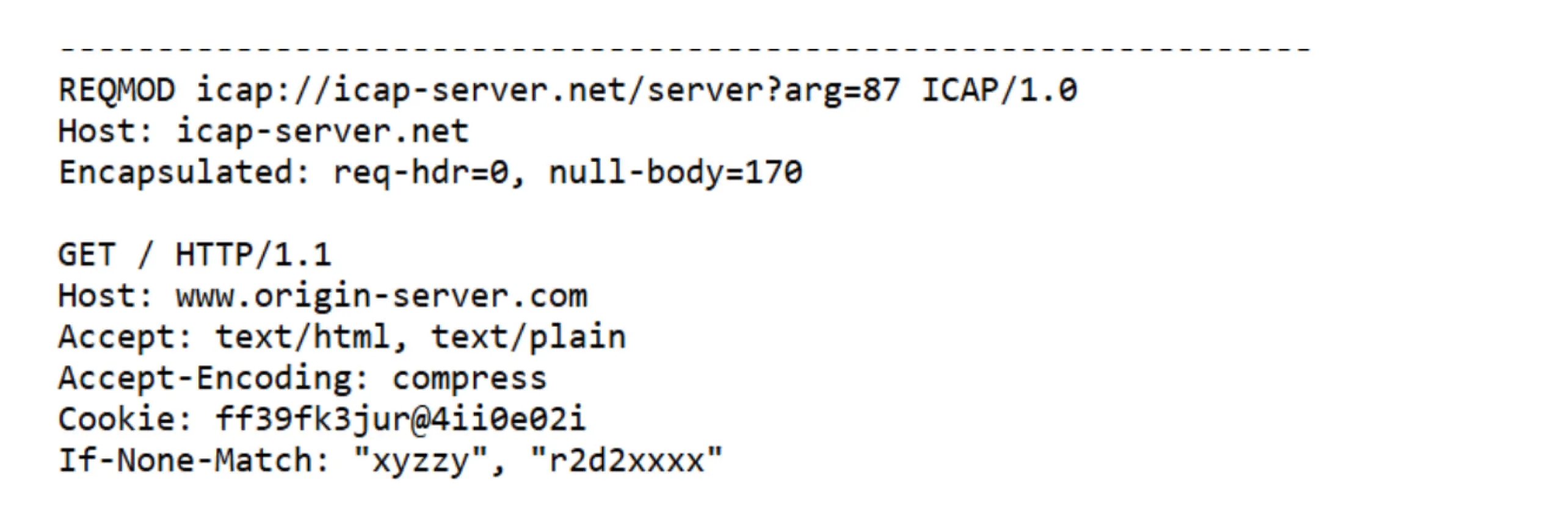
In REQMOD mode, an ICAP client sends an HTTP request to an ICAP server for processing before forwarding it. The ICAP server can:
- Modify the request and return it for forwarding.
- Block the request by returning an HTTP response (e.g., access denied).
REQMOD is commonly used for URL filtering, data loss prevention (DLP), and policy enforcement.
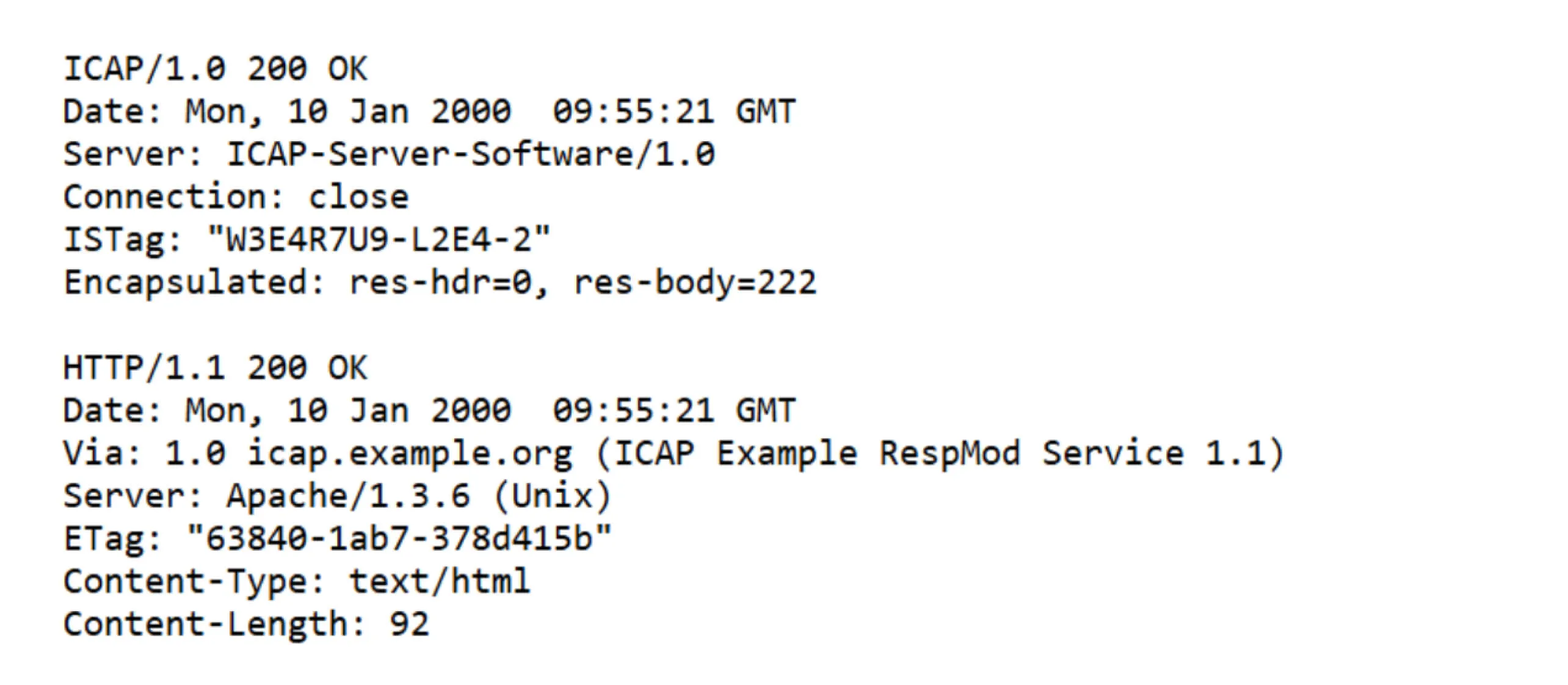
Response Modification (RESPMOD)
In RESPMOD mode, an ICAP client sends an HTTP response to an ICAP server before delivering it to the user. The ICAP server can:
- Modify the response before it reaches the client.
- Block the response by returning an error message.
RESPMOD is used for malware scanning, content filtering, and compliance enforcement.
Benefits and Use Cases
ICAP enhances network security by enabling offloaded processing for critical security functions. Benefits include:
- Content adaptation and modification near the edge of the network server, instead of creating an object copy from the origin server.
- Improved resource management through dedicated ICAP servers.
- Advanced content filtering for compliance and security.
- Seamless security offloading without modifying existing infrastructure.
ICAP Antivirus
Instead of implementing antivirus engines from scratch, organizations can offload virus scanning to an ICAP-enabled AV solution. This reduces operational burdens while achieving robust threat detection.
ICAP DLP
ICAP-integrated DLP engines analyze inbound and outbound traffic for sensitive data, preventing unauthorized exposure of PII, financial records, or intellectual property.
ICAP Malware Analysis
Organizations can integrate ICAP with malware analysis and sandboxing solutions to detect and respond to emerging threats efficiently. This approach combines AV scanning with behavioral analysis, improving detection speed and accuracy.
Common Challenges and Solutions
ICAP deployment can present several challenges, including performance bottlenecks, network connectivity issues, configuration errors, compatibility concerns, and troubleshooting difficulties. Understanding these challenges and implementing proactive solutions can ensure a smooth and efficient ICAP implementation.
Network Connectivity Issues
- Packet loss: Transmission errors between the proxy and ICAP server can cause retransmissions and delays.
- Firewall restrictions: Incorrect firewall rules may block necessary ICAP traffic.
- Misconfigured network settings: Incorrect IP addresses or ports can lead to failed ICAP communications.
Solution: Verify network paths, adjust firewall rules, and ensure IP address and port configurations are correct.
Performance Bottlenecks
- ICAP server overload: High traffic volume can overwhelm the ICAP server, leading to slow performance.
- Slow scanning engines: Some antivirus or content filtering engines may take too long to process data.
- Large file sizes: Processing large files can significantly delay content delivery.
Solution: Optimize ICAP server placement, upgrade hardware, and fine-tune scanning engine configurations to balance performance and security.
Configuration Errors
- Incorrect ICAP command settings: Misconfigured ICAP commands can lead to improper processing.
- Version mismatches: Different ICAP versions between clients and servers can create compatibility issues.
- Improper ICAP service configuration: Misconfigured ICAP services can cause failures in content adaptation.
Solution: Regularly review ICAP configurations, ensure proper versioning across devices, and test configurations before deployment.
Compatibility Issues
- Application-specific limitations: Some applications or security devices may not fully support ICAP.
- Feature constraints: Certain ICAP features, such as content previewing, may not function as expected in all environments.
Solution: Validate ICAP compatibility with security appliances and applications before full deployment.
Error Codes and Logging Issues
- Troubleshooting difficulties: ICAP error codes may be challenging to interpret.
- Inadequate logging: Missing or incomplete logs can make issue diagnosis difficult.
Solution: Enable detailed logging on ICAP servers, review error codes, and use network monitoring tools to diagnose performance problems.
Potential Impacts of ICAP Issues
- Slow website loading times due to delayed content scanning.
- Incomplete security checks if the ICAP server fails to scan content properly.
- Application malfunctions caused by ICAP interfering with functionality.
- User frustration from delays or errors in accessing online content.
Proactively monitoring ICAP deployments, optimizing configurations, and ensuring compatibility can mitigate these common issues and enhance overall network efficiency.
Conclusion
ICAP plays a vital role in modern network environments, enhancing security and efficiency by offloading content adaptation tasks. As organizations continue to face evolving cybersecurity threats, ICAP provides a scalable solution to ensure compliance, threat mitigation, and streamlined network operations.
Interested in integrating ICAP with your existing infrastructure? Learn more about MetaDefender ICAP Server or talk to one of our experts today.
FAQs
What is ICAP (Internet Content Adaptation Protocol)?
ICAP (Internet Content Adaptation Protocol) is a lightweight protocol that allows network devices like proxies or firewalls to offload HTTP/HTTPS content for scanning, adaptation, or modification to a separate ICAP server. In cybersecurity, ICAP is used for threat mitigation, policy enforcement, and compliance without significantly impacting network performance.
How does ICAP work?
ICAP works by enabling an ICAP client, typically a proxy or gateway, to send HTTP/HTTPS requests or responses to an ICAP server. The server analyzes or modifies the content and returns it to the client. This offloaded cycle allows real-time inspection for malware, DLP, or policy enforcement near the network edge.
What is the role of an ICAP server?
An ICAP server processes content adaptation requests from ICAP clients. It performs tasks such as malware scanning, content modification, or enforcing data security policies, then returns the adapted content to the client for delivery.
What is REQMOD vs RESPMOD in ICAP?
REQMOD (Request Modification) is used when the ICAP client sends HTTP requests to the server for adaptation, typically for URL filtering or policy enforcement. RESPMOD (Response Modification) involves sending HTTP responses for scanning or content filtering before delivering to the user. Both are part of ICAP’s core processing methods.
What are the benefits of using ICAP?
ICAP enhances network efficiency and security by allowing edge devices to offload resource-intensive tasks like malware scanning and DLP. It enables content adaptation without copying from origin servers, supports advanced filtering, and integrates with tools like MFT, proxies, and WAFs.
What are common ICAP challenges?
Challenges include network connectivity issues, ICAP server overload, misconfigured commands, compatibility limitations, and troubleshooting errors due to insufficient logging. Solutions involve reviewing firewall rules, optimizing server placement, validating configurations, and enabling detailed logs.
What devices or tools integrate with ICAP?
ICAP integrates with security devices such as proxy servers, load balancers, ingress controllers, web application firewalls (WAFs), and managed file transfer (MFT) solutions. These tools use ICAP for inline content scanning and policy enforcement.

