MetaDefender Core
Advanced Threat Prevention Solution
MetaDefender Core enables you to integrate advanced malware prevention and detection capabilities into your existing IT solutions and infrastructure for better handling common attack vectors: securing web portals from malicious file upload attacks, augmenting cybersecurity products, and developing your own malware analysis systems.
Ever-Evolving Cyberattacks
Cyberattacks become ever-more sophisticated. Cyberthreats are incessantly evolving and being built to evade traditional signature-based and behavior-based anti-malware defenses. Nowadays your IT and OT infrastructures need advanced multi-layer threat prevention to beat zero-day attacks, advanced persistent threats (APT) and highly evasive malware.
Detect, Analyze, and Eliminate Malware and Zero-Day Attacks
Prevent Zero-Day and Advanced Evasive Malware
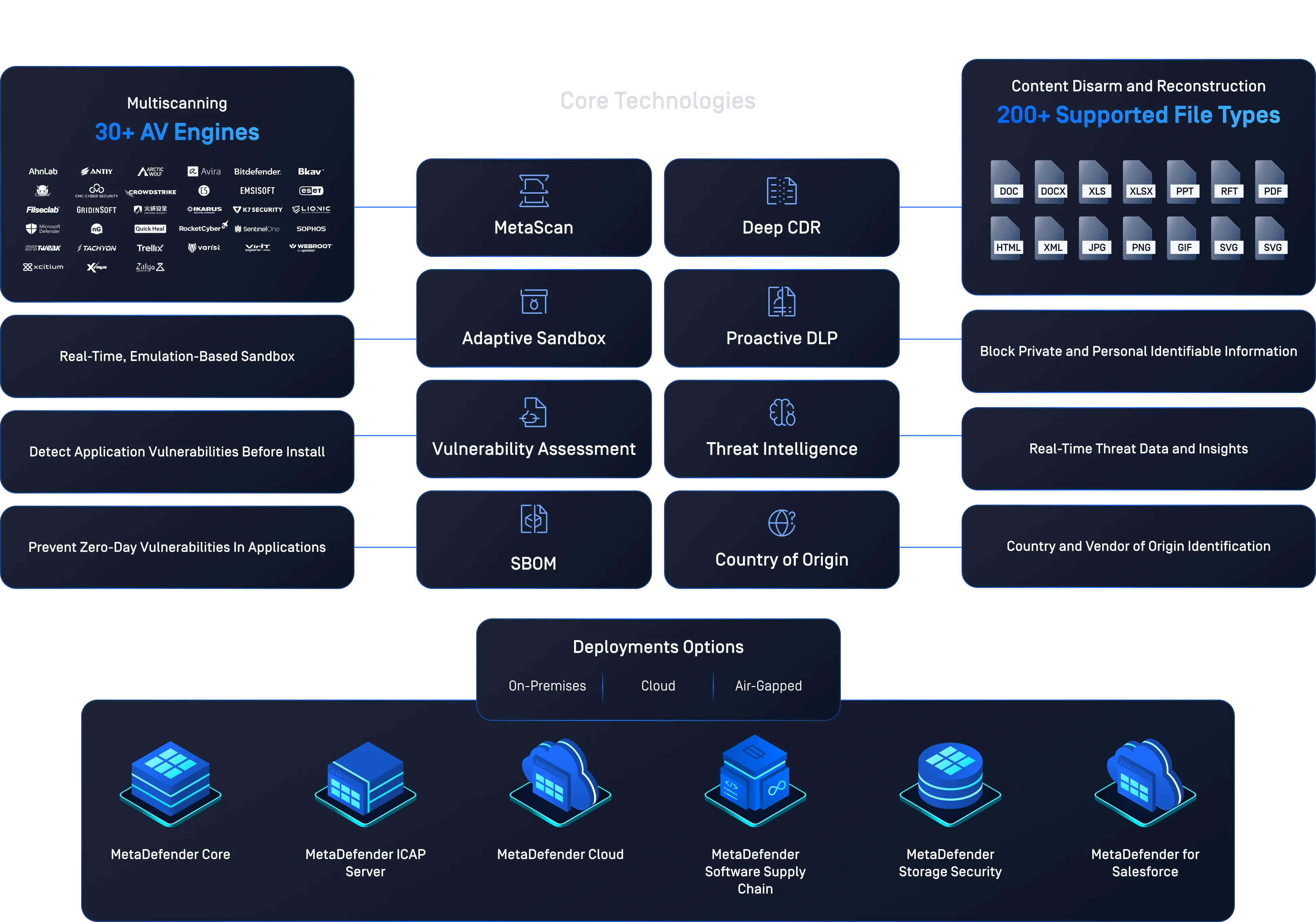
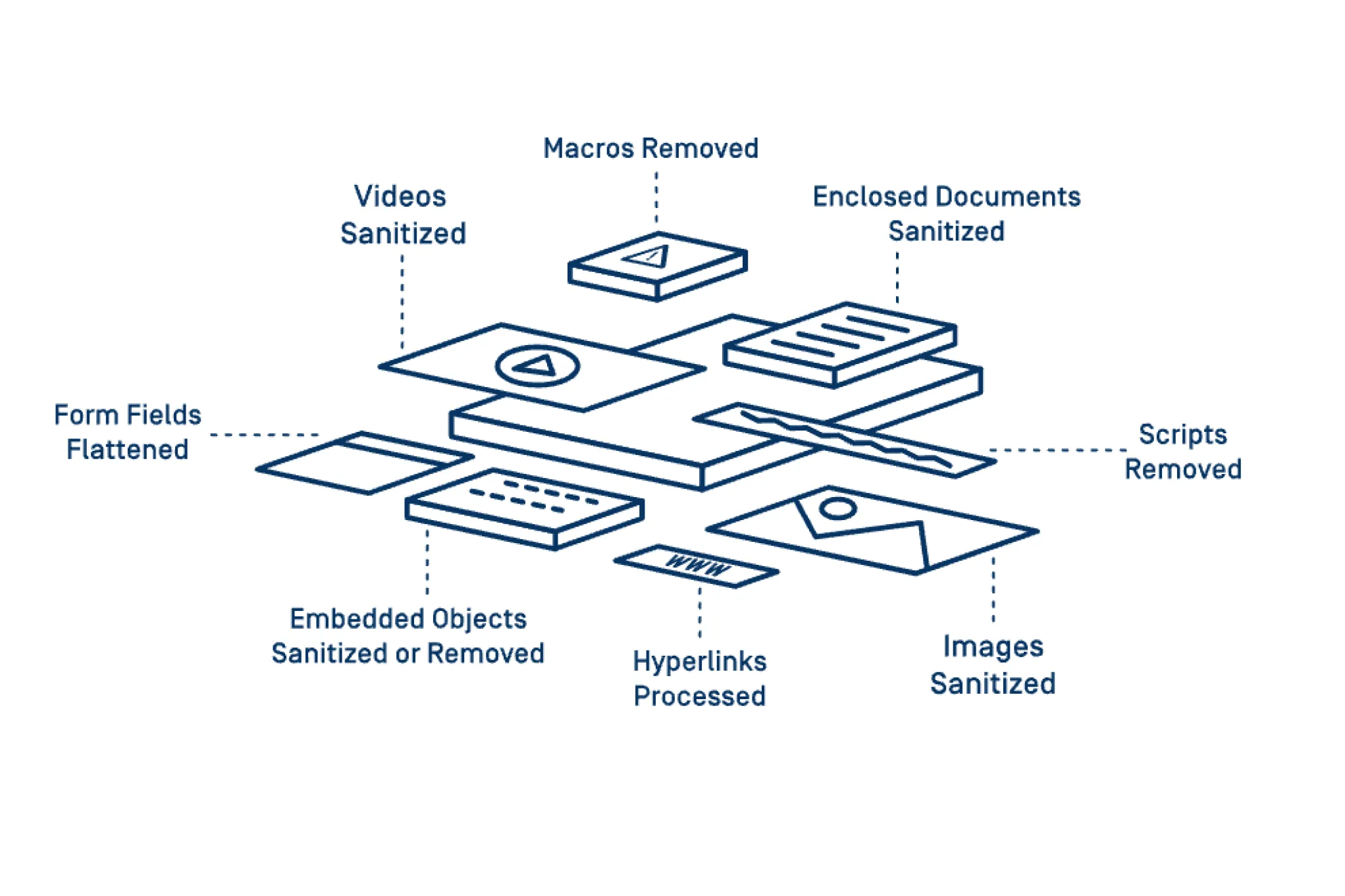
MetaDefender Deep Content Disarm and Reconstruction (Deep CDR) technology protects from known and unknown file-borne threats by sanitizing and reconstructing files. Any possible embedded threats are neutralized while maintaining full usability with safe content.
Rebuild 200+ common file types, hundreds of file reconstruction options are available.
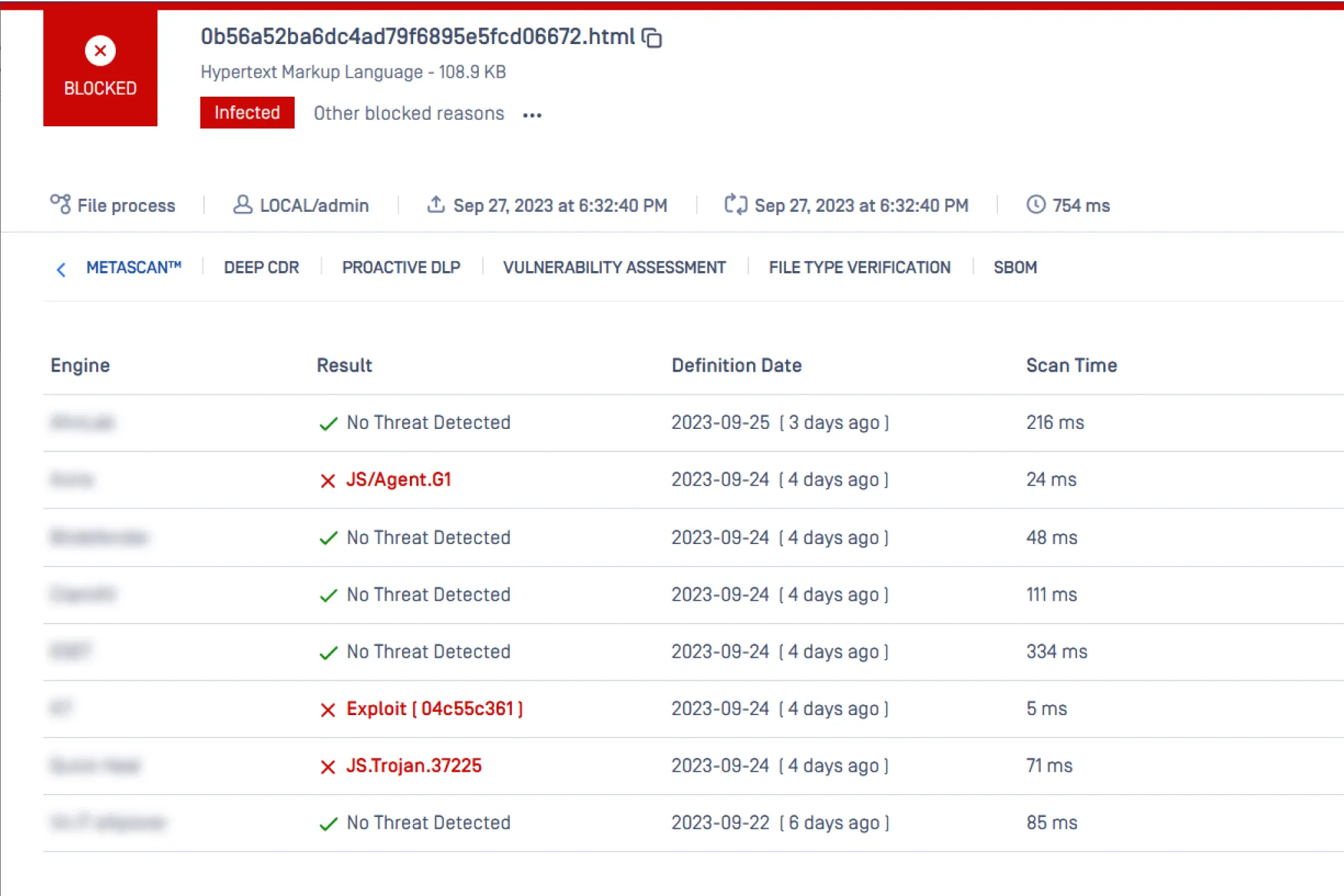
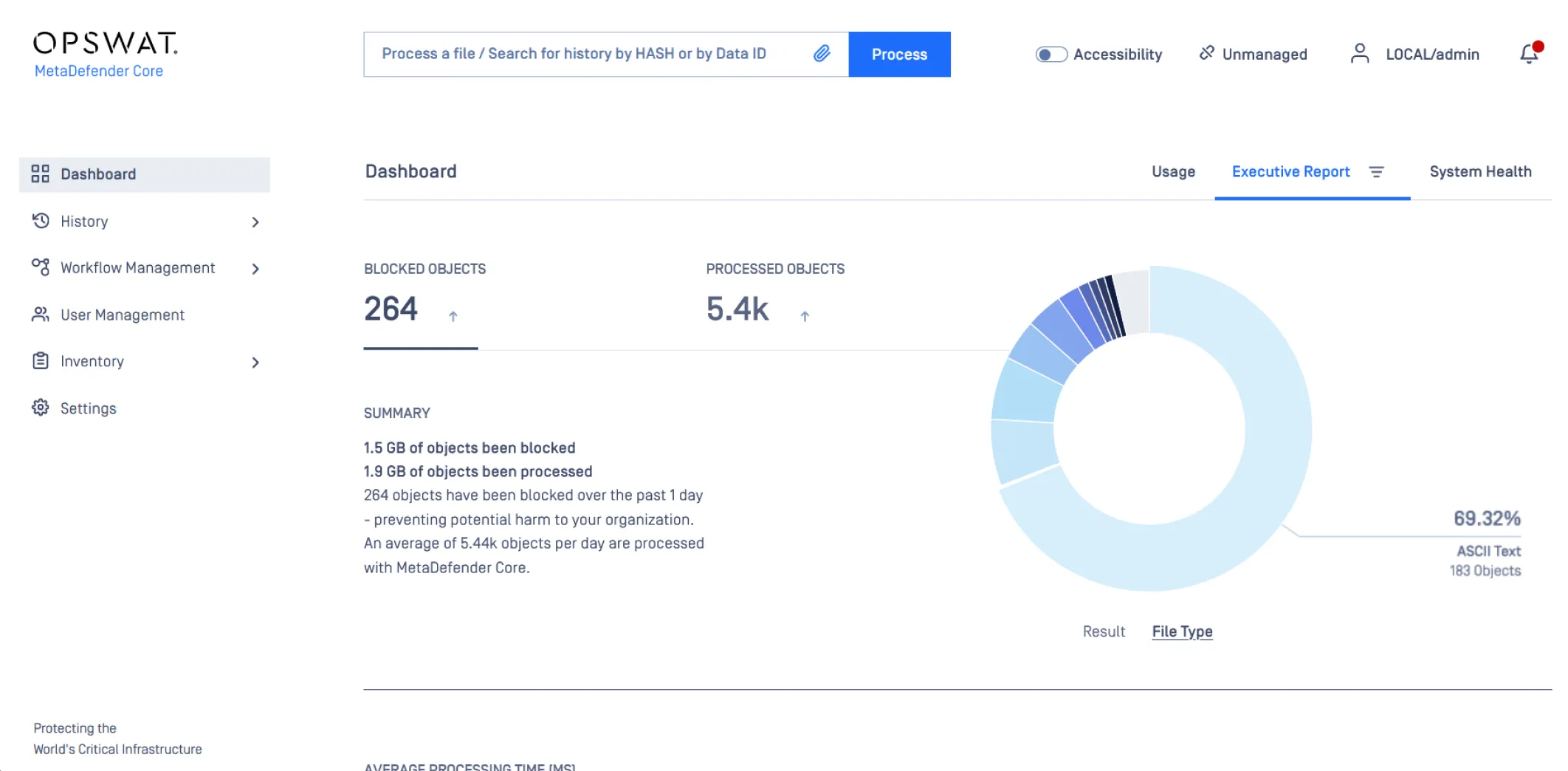
Achieve Over 99% Threat Detection Accuracy
MetaDefender Multiscanning technology leverages 30+ leading anti-malware engines and proactively detects over 99% of malware by using signatures, heuristics, and machine learning. This significantly improves detection of known and unknown threats and provides the earliest protection against malware outbreaks.
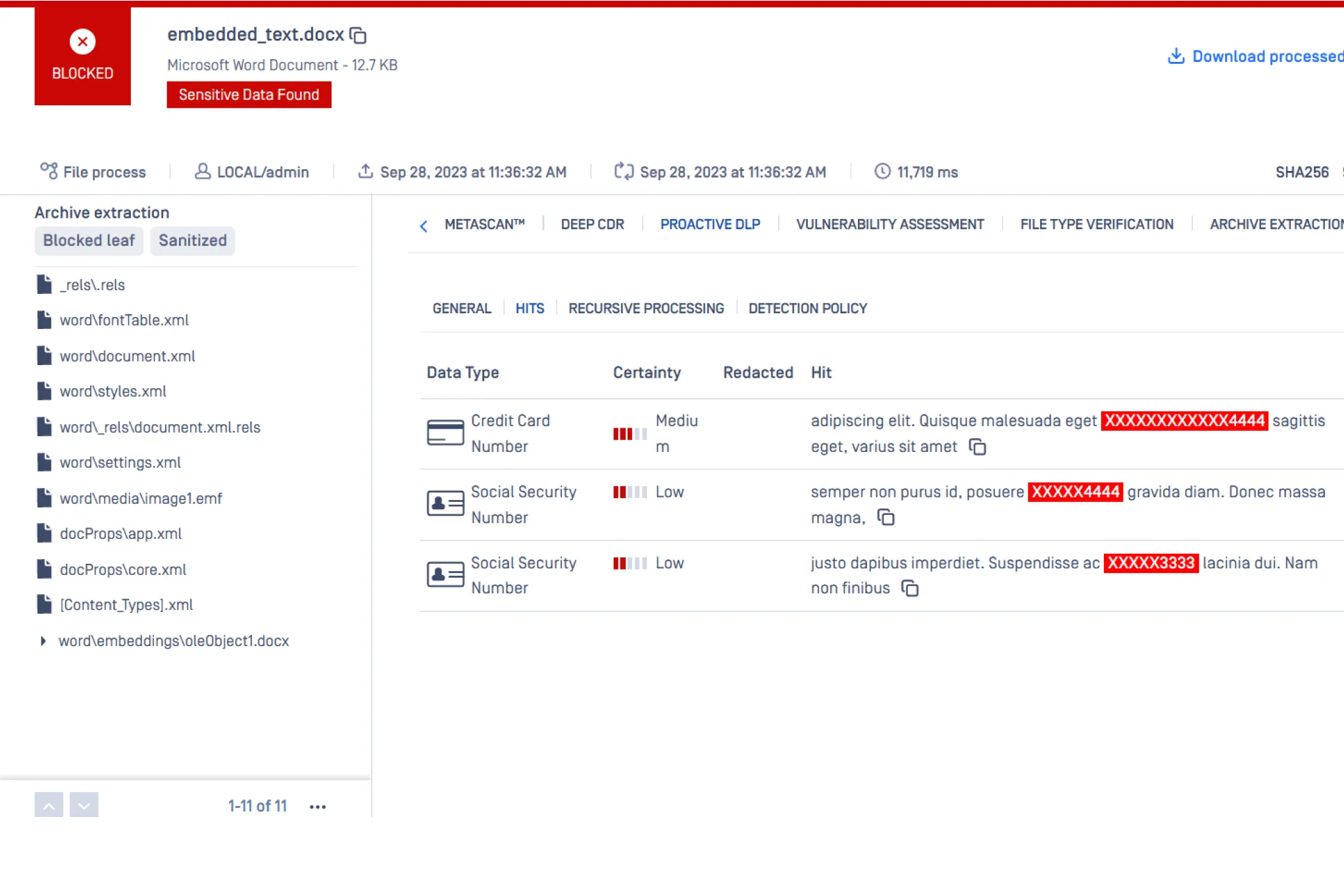
Prevent Regulatory Compliance Violations & Detect Adult Content
MetaDefender Proactive Data Loss Prevention (Proactive DLP) helps companies prevent sensitive and confidential information in files from leaving or entering the company’s systems by content-checking files before they are transferred. This helps enterprises meet regulatory requirements like HIPAA, PCI-DSS and GDPR. Proactive DLP detects adult content in images and offensive language in text using machine learning, computer vision, and AI.
MetaDefender Proactive DLP supports 110+ file types, including Microsoft Office, PDF, CSV, HTML and image files.
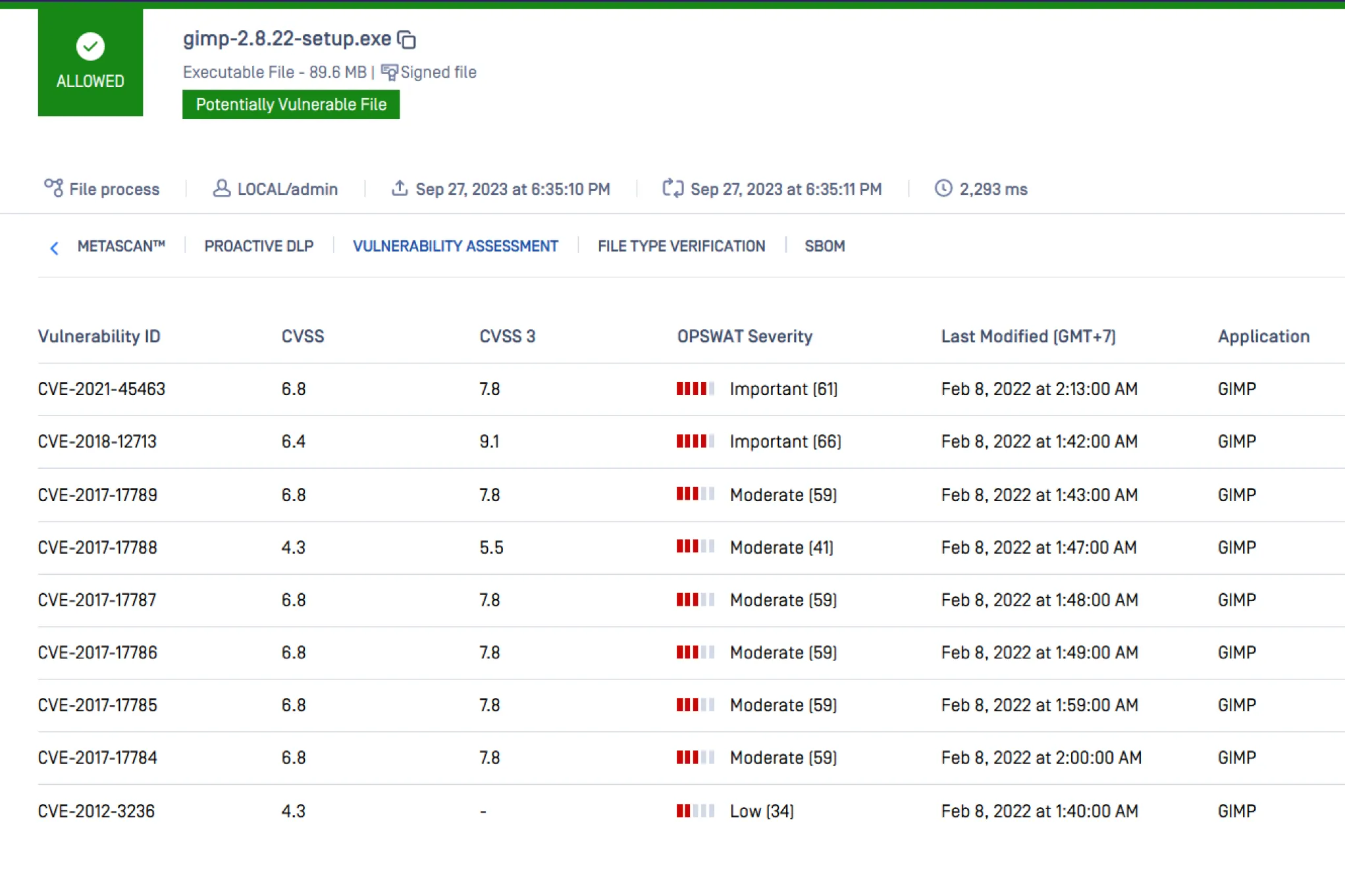
Detect Application and File-Based Vulnerabilities
MetaDefender File-Based Vulnerability Assessment technology scans and analyzes binaries and installers to detect known application vulnerabilities before they are executed on endpoint devices, including IoT devices.
It gives IT administrators the ability to:
- Check certain types of software for known vulnerabilities before installation
- Scan systems for known vulnerabilities when devices are at rest
- Quickly examine running applications and their loaded libraries for vulnerabilities
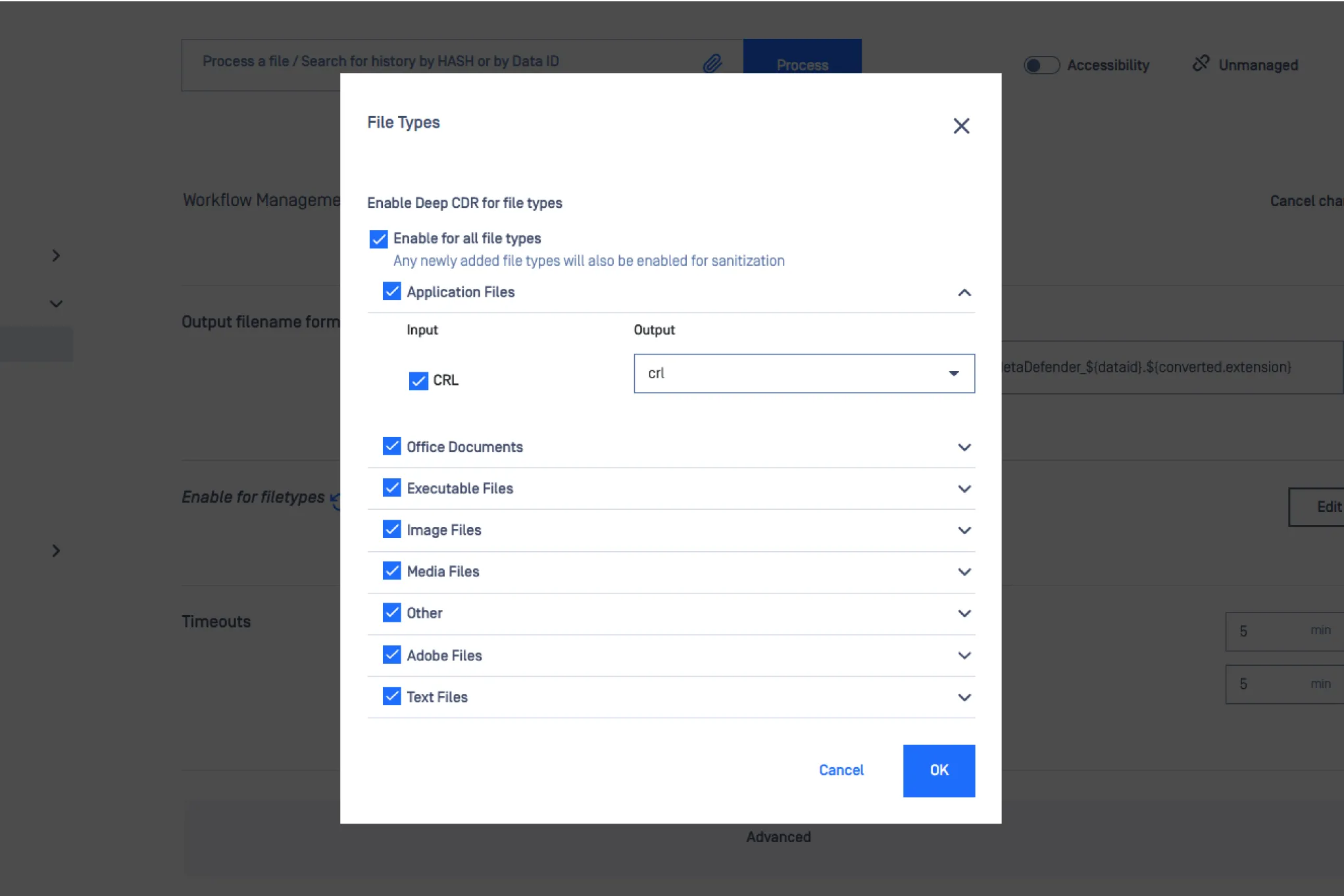
100+ File Conversion Options
Use the file type conversion functionality to flatten files to fewer complex formats. MetaDefender enables administrators to specify that certain file types are converted to other files types (e.g. Microsoft Word documents to PDF). By adding this step to the data processing workflow, zero-day attacks where malicious objects are embedded into office documents or image files can be eliminated, even if they have the ability to evade detection by antivirus engines.
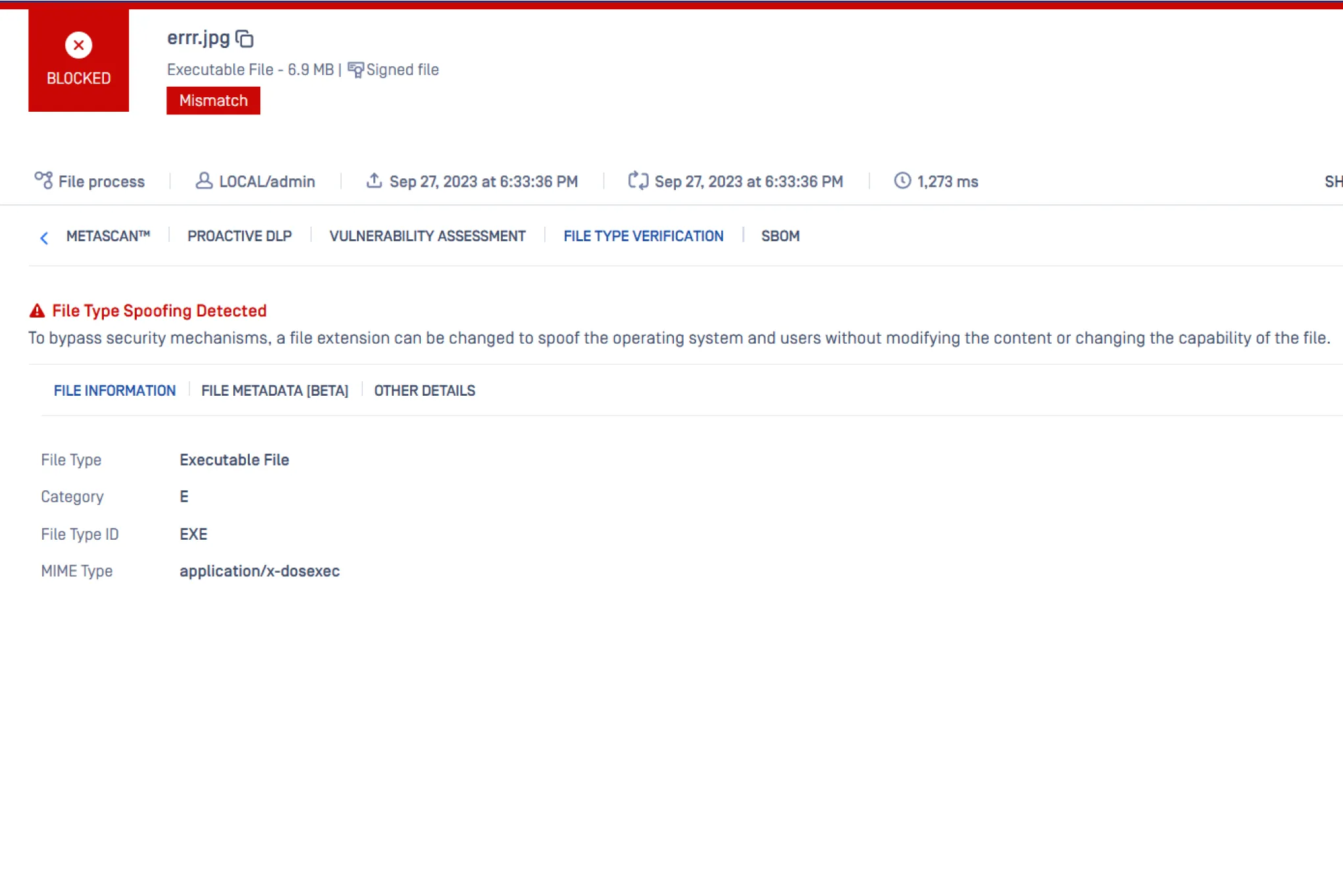
File Type Verification
With MetaDefender's file type verification technology, you can determine the actual file type based on the content of the file, not the unreliable extension to combat spoofed file attacks. You can also configure security processes based on true file type. For example, you can take more precautions with risky file types like EXE and DLL files —setting different policies or workflow rules based on file type.
A spoofed file usually indicates malicious intent, so to mitigate this risk, MetaDefender block files with incorrect extensions. For example, MetaDefender can prevent EXE or DLL files trying to pose as TXT files from entering your organization.
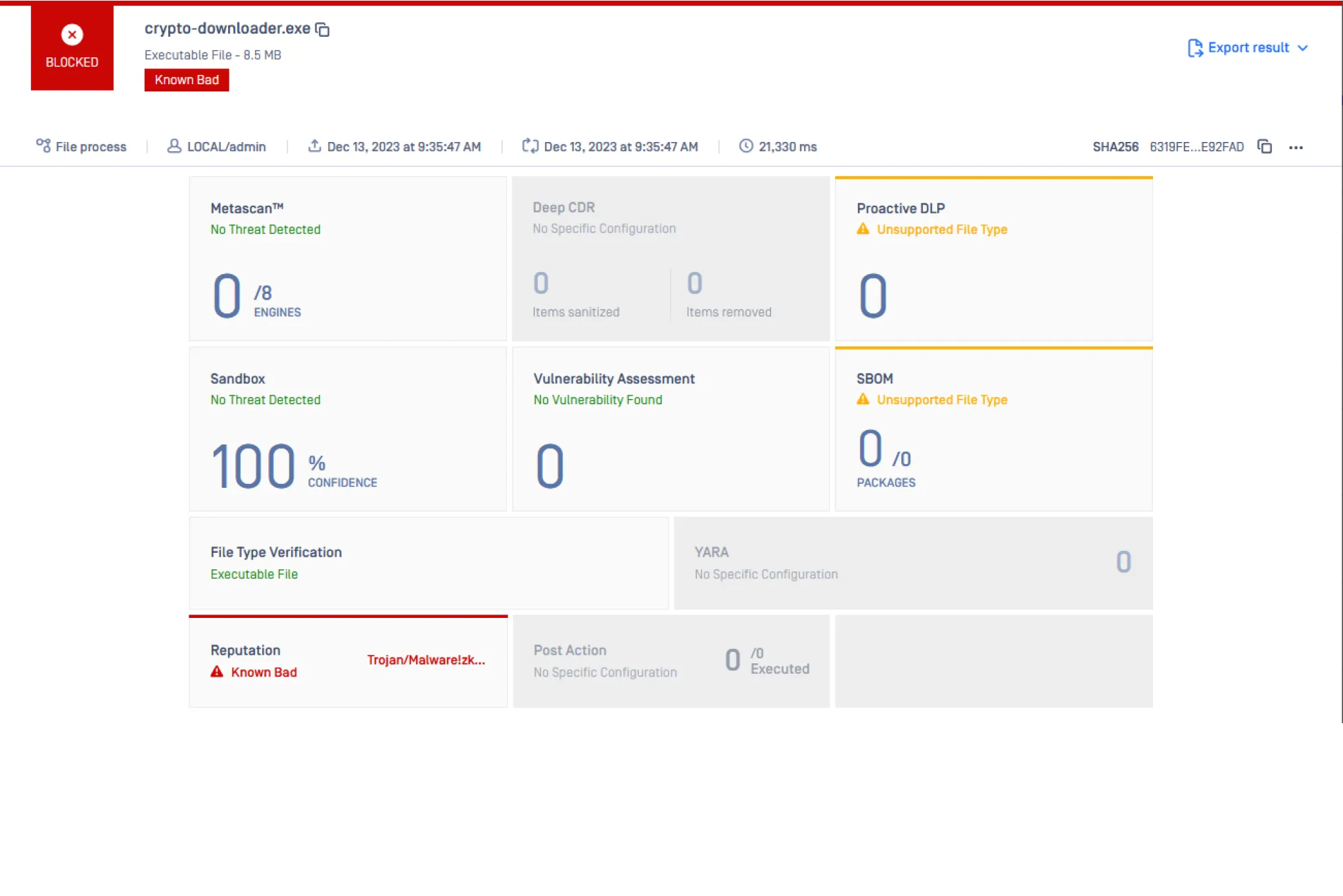
Faster False Positives Remediation
Reputation Engine matches file hashes against database of known good and bad files and leverages advanced analyses to remediate false positives faster.
Benefits of the Reputation Engine:
- Advanced threat detection - Identify uploaded files as “known good”, “known bad” or “unknown” by matching hashes against database of known malicious or safe files.
- Minimized false positives/negatives - Leverage advanced analyses conducted by malware analysts and reverse engineering experts for faster verdicts on suspicious files.
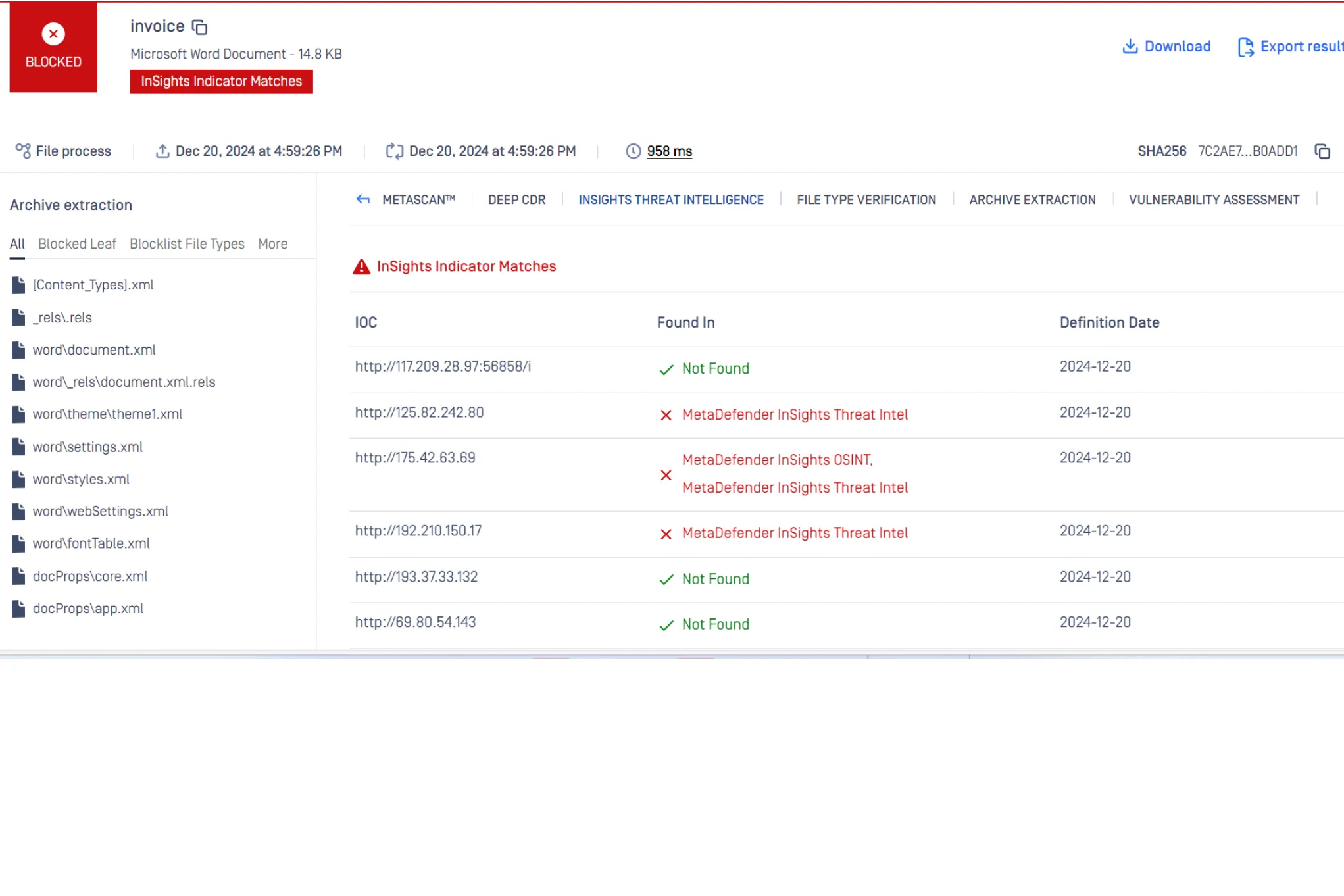
Curated Threat Intelligence for Near Real-Time Detection and Response
MetaDefender InSights Threat Intelligence engine detects known malicious domains and IP addresses in documents and enables real-time blocking of files based on malicious indicator detections. It applies high-quality, curated threat intelligence to extracted indicators, aggregating data from hundreds of sources to ensure the highest quality threat detection and response capabilities.
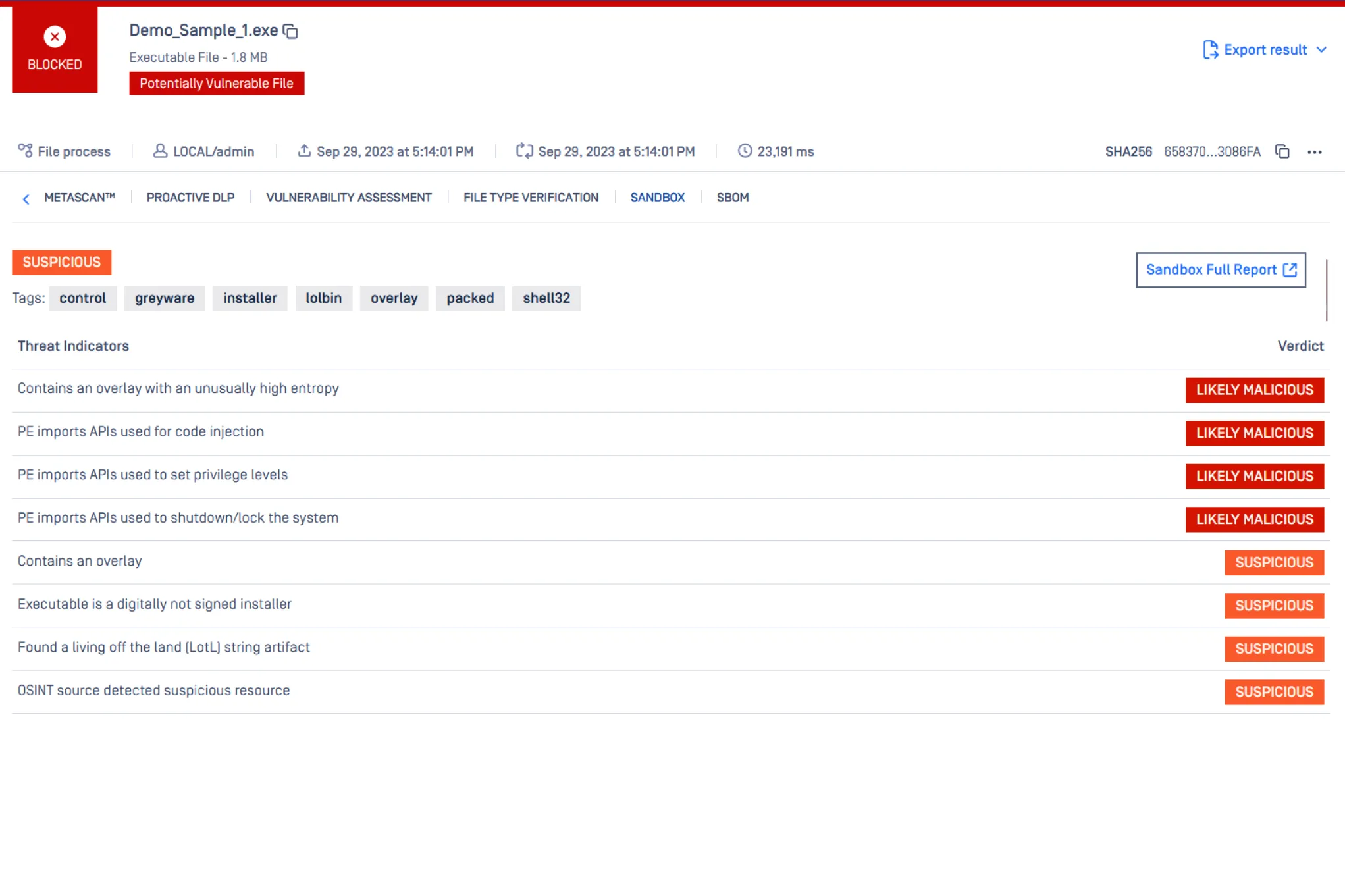
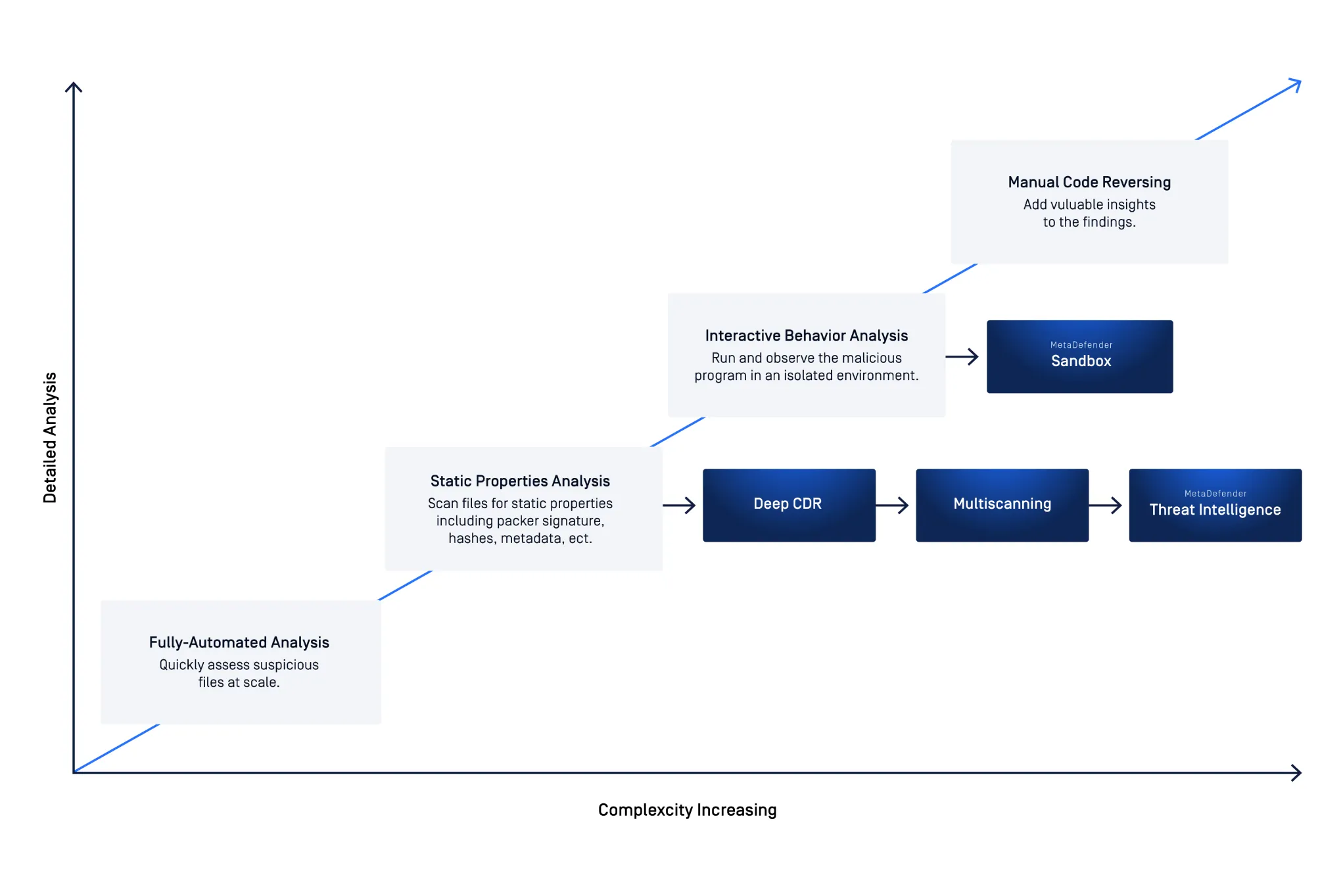
Adaptive Threat Analysis
Detonate and analyze malware in a controlled environment. MetaDefender utilizes MetaDefender Sandbox for a complete set of malware analysis technologies including, threat agnostic analysis of files and URLs, emulation of all targeted applications (Microsoft Office, PDF readers, and more), a focus on Indicator-of-Compromise (IOC) extraction, and Rapid Dynamic Analysis engine for targeted attack detection.
Sample: Geofencing, Targeted financial attack, Pafish UPX
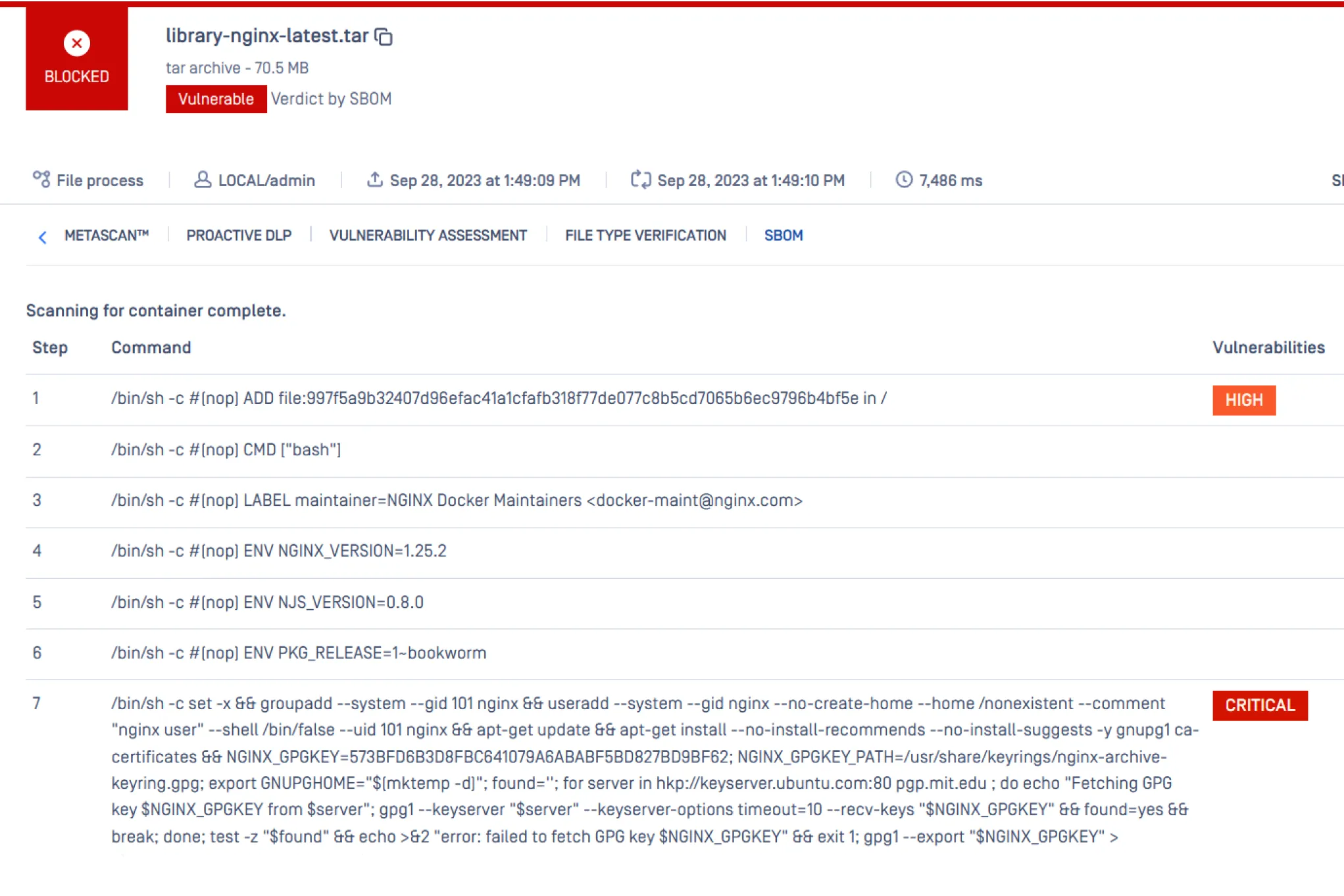
Generate SBOM (Software Bill of Materials)
OPSWAT SBOM secures the software supply chain by providing a comprehensive component inventory for source code and containers.
- Supports 10+ languages, including Java, JavaScript, Go, PHP, and Python.
- Supports 5M+ third-party open-source software components.
- Utilizes a database of 17K+ vulnerabilities sourced from the National Vulnerability Database (NVD) and GitHub (GHSA).
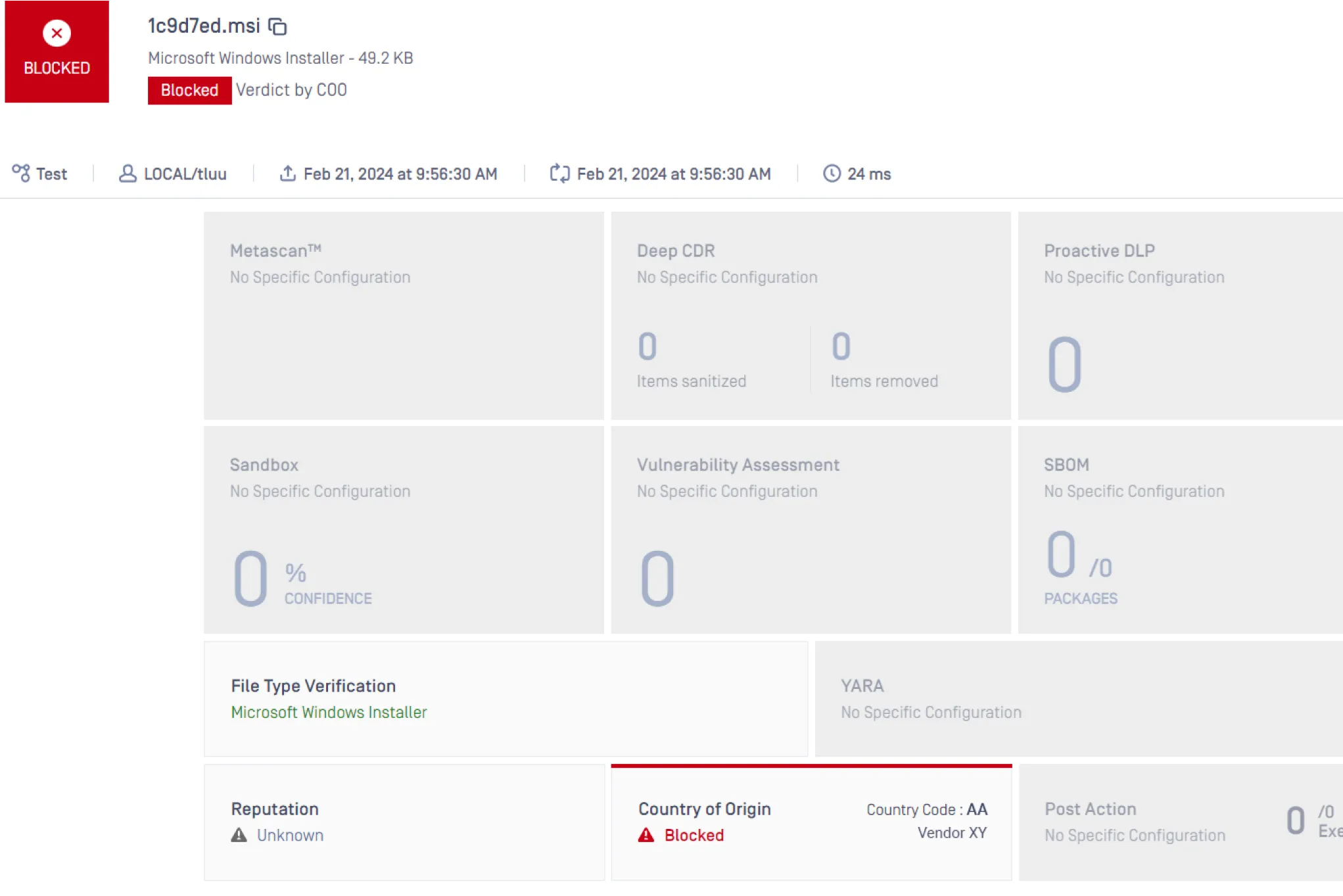
Country of Origin
The OPSWAT Country of Origin engine empowers organizations to instantly detect the geographic source of uploaded files including PE, MSI, and Self-extract.
By analyzing digital fingerprints and metadata, it can identify restricted locations and vendors. This enables automated filtering that blocks unauthorized access to sensitive data while ensuring compliance with data regulations across regions.
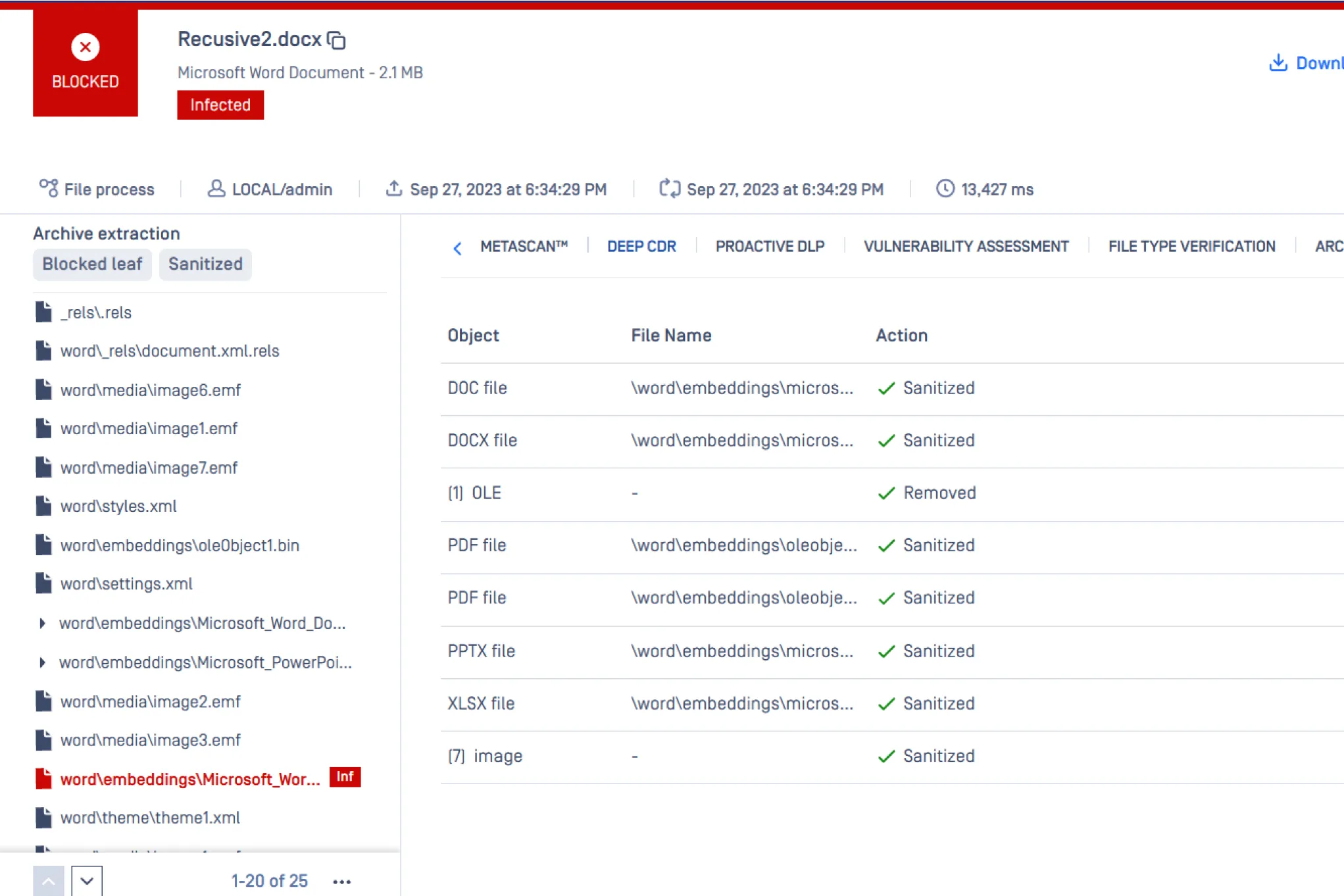
Archive Extraction
MetaDefender currently supports archive scanning for over 30 types of compressed files. Archive handling options are configurable, and encrypted archives are supported.
Benefits of Archive Extraction:
- Improve detection capabilities of anti-malware engines by using both extracted and unextracted scanning
- Decrease scanning time and improve processing time by removing redundant scanning of archives
- Prevent archive bombs by extracting files and scanning them individually
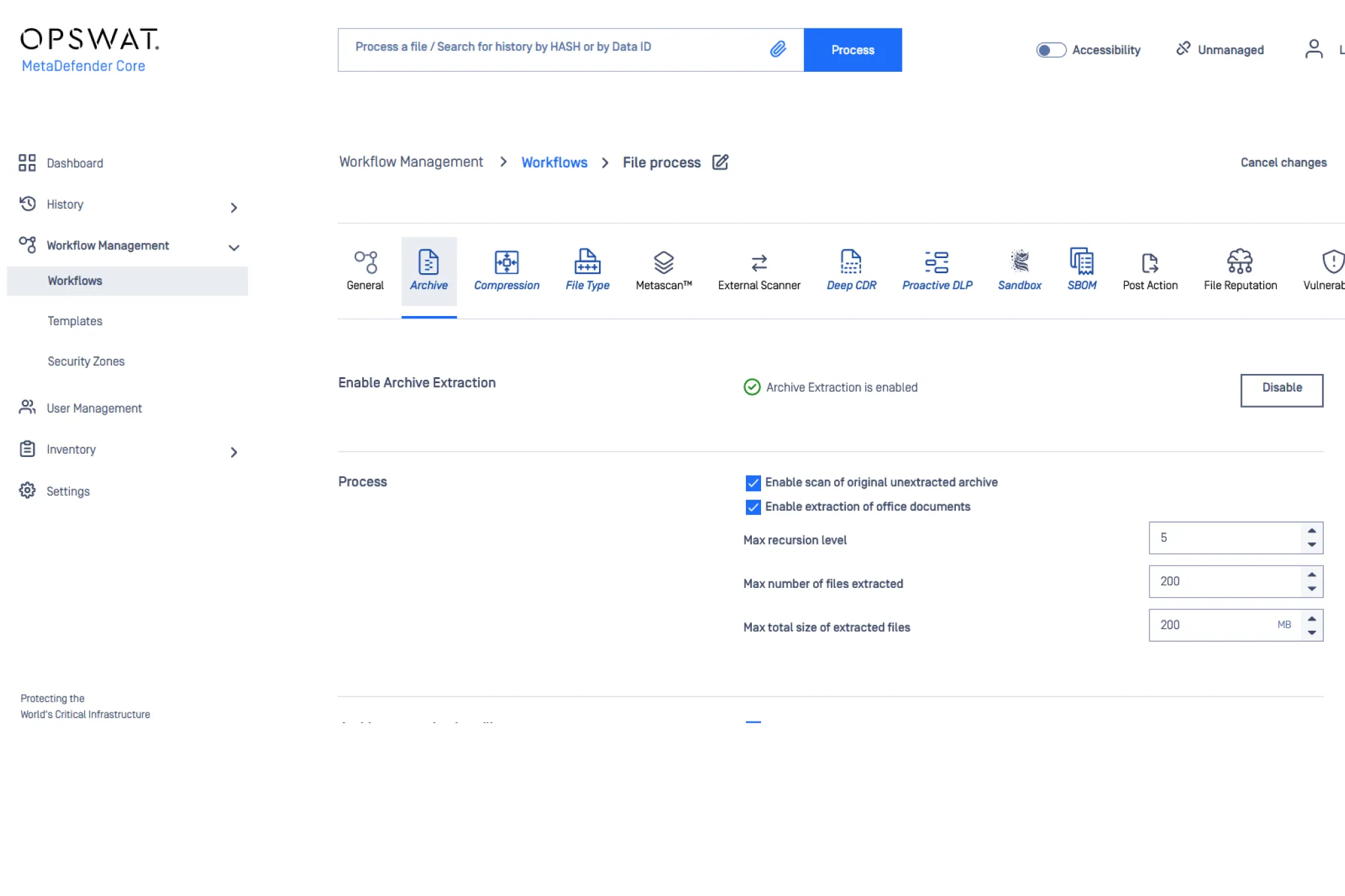
Workflow Engine
MetaDefender’s Workflow Engine allows administrators to create multiple workflows to handle different security policies based on users and file source.
Benefits of the Workflow Engine:
- Improve Security - The workflow engine allows you to set the appropriate security level per user and file type and enables IT to make quick decisions on data security policy.
- Enhance Performance - By blocking certain file types and setting the order of file processing, performance can be enhanced.
- Prioritize Workflows - Users can define the priority and pre-defined scan times per workflow rule, optimizing business processes.
Easy to Deploy, Unrivaled Expertise
Data Privacy Compliance
MetaDefender Core can be deployed on-premises which enables offline analysis of files. In the MetaDefender Cloud platform, your files will be processed privately in a temporary storage and removed immediately after the analytical report is finished.
Simple Deployment
Fast implementation both on-premises and in the cloud via REST API, Webhook or any Internet Content Adaptation Protocol (ICAP) enabled product. Support for both Windows and Linux.
Expert Professional Services
Access to cybersecurity experts to adapt the solution to your existing infrastructure and unique requirements. 24/7 support is available to keep operational at all times.
Centralized Management
From a centralized console, you can perform global operations, view all deployed anti-malware engines, manage virus definition and engine updates, and check licensing status.
High Performance and Scalability
Scale to any volume with our high-performance architecture and load balancing feature. Fast scanning and reconstruction without affecting performance.
Low Total Cost of Ownership
Single-source licensing through OPSWAT helps enterprises avoid complex, costly and time-consuming implementation and management of different vendors.
Maximize Your Protection
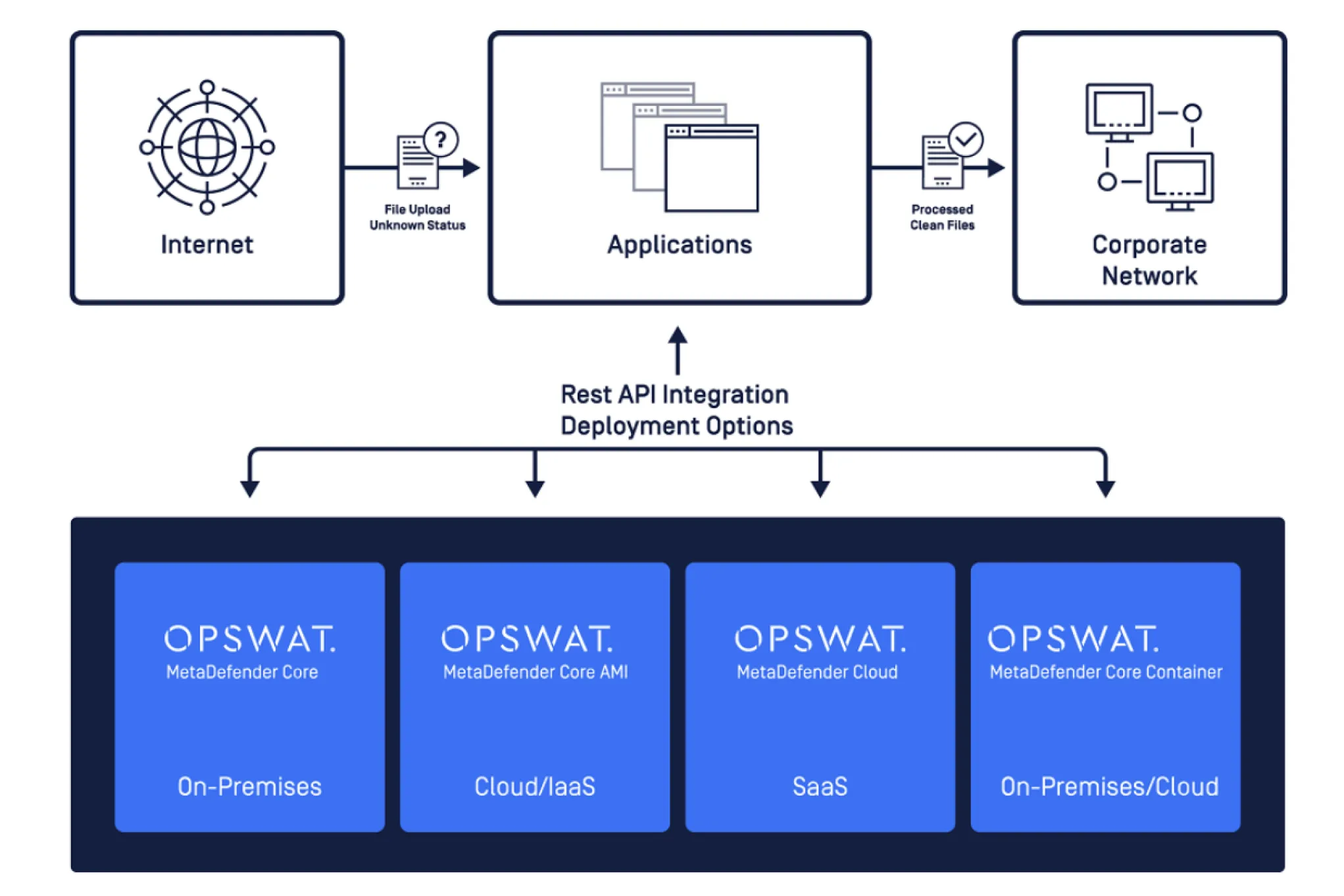
Protect Web Portals from Malicious File Uploads
MetaDefender Core prevents malicious file uploads on web applications that bypass sandboxes and other detection-based security solutions. It also helps protect confidential data, minimize data breaches, and prevent privacy violations with Proactive DLP.
Perform Malware Analysis Safely and Effectively
MetaDefender Core’s multi-layer malware detection and analysis technologies help you to quickly and effectively triage and respond to security incidents, find the root cause of cyberattacks, and improve your defenses. It can be deployed on-premises, enabling offline analysis of malicious files to keep sensitive files private and scan results confidential.
Enhanced Threat Prevention for Security Products
Use MetaDefender Core to reinforce your security solution with OPSWAT advanced threat prevention technologies. We provide sample code and detailed API documentation to help you bootstrap your integration. You can use almost any programming language to leverage MetaDefender technology with our APIs to help your developers get their prototypes done quickly without an additional learning curve.
Technical Documentation
Getting Started
Deployment & Usage
Support
Unlock the Full Potential of Our Products

Recommended Resources
Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.