Every organization depends on files. They carry contracts, sensitive data, customer information, intellectual property, and they remain one of the most common vehicles for cyberattacks. According to the Ponemon Institute’s latest research, 61% of enterprises experienced a file-related data breach in the last two years, with each incident costing an average of $2.7 million.
Compounding the problem is that confidence in file protection is low. For example, fewer than half of organizations express high confidence in securing files across common workflows: uploads, transfers, downloads, and third-party sharing.
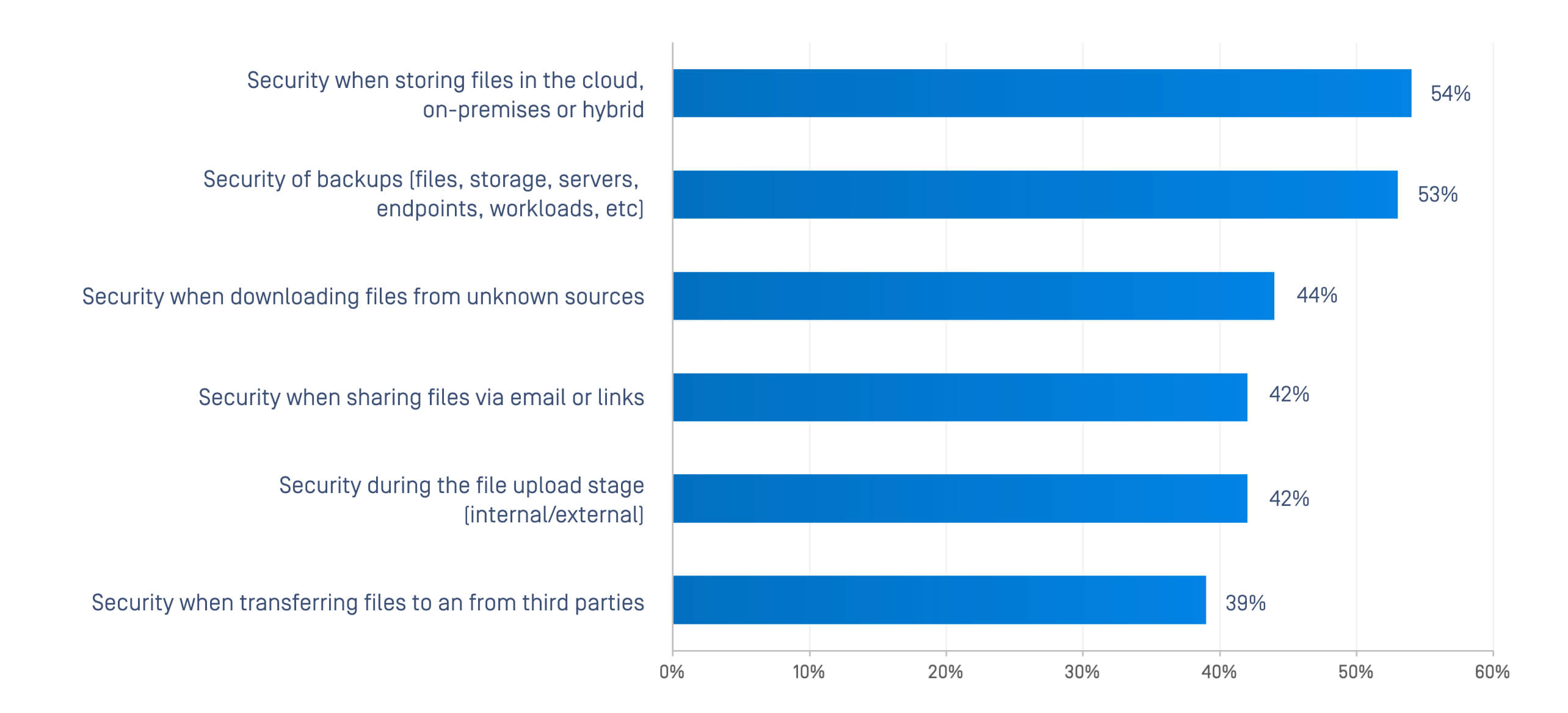
Legacy point solutions like single antivirus engines, isolated data loss prevention tools, and basic gateways were not built for the complexity of modern threats. Attackers now weaponize everyday files with hidden malware, embedded scripts, and exploitable libraries. Insider risks, whether negligent or malicious, compound the problem, as do growing regulatory requirements around data privacy and governance.
Enter the multi-layered file security platform: an integrated approach that applies a defense-in-depth strategy to every file across its lifecycle. Unlike fragmented tools, platforms combine multiple complementary controls, from malware detection to CDR (content disarm and reconstruction), boosting resilience, audit-readiness, and reduced operational complexity.
This article explores what a multi-layered file security platform is, why enterprises are adopting them, and how they drive measurable security and business outcomes.
What is a Multi-Layered File Security Platform?
A multi-layered file security platform is a unified system that integrates multiple detection, analysis, and prevention technologies to protect sensitive files across hybrid IT and OT environments.
Core Principles of Multi-Layered File Security
At its heart, this approach reflects the principle of defense in depth for file security: no single tool can stop all threats, but multiple layers, working together, dramatically reduce risk.
- Files are scanned, sanitized, and analyzed at every entry point.
- Security layers are orchestrated centrally, not bolted on piecemeal.
- Platforms extend coverage across cloud, endpoint, and critical infrastructure environments.
Essential Security Layers in a Modern Platform
Leading platforms consolidate technologies such as:
- Multiscanning with dozens of anti-malware engines
- CDR to strip hidden macros or malicious objects
- Sandboxing for dynamic analysis of suspicious files
- File-based vulnerability assessment to block files with outdated or risky libraries
- SBOM (Software Bill of Materials) analysis to uncover hidden dependencies (e.g., Log4j)
- DLP (data loss prevention) to stop accidental or malicious exfiltration
- Threat intelligence correlation for emerging risks
- Country-of-origin analysis to flag high-risk files from specific regions
How Multi-Layered File Security Protects Sensitive Data
By layering these controls, platforms protect against:
- File-borne malware and ransomware hidden in ordinary formats
- Accidental leaks of sensitive data (PII, PHI, PCI)
- Exploitation of vulnerabilities in embedded components
- Insider threats exploiting poor file visibility
- Regulatory non-compliance, by generating audit-ready file security logs
Why Single-Point File Security Solutions Fall Short
Single-point products were designed for a simpler time. Today, adversaries exploit the gaps between them.
Evolving File-Borne Threats That Evade Point Solutions
- Malicious macros launching ransomware from Office docs
- Obfuscated malware bypassing single antivirus engines
- Exploitable file formats like CAD, ISO, and ZIP images
- Metadata leaks that AI tools can inadvertently expose
Operational Inefficiencies and Hidden Costs
Fragmented tools increase total cost of ownership. Multiple consoles, duplicated policies, and lack of workflow integration waste time and budget. Point products also fail to scale across hybrid environments, leaving blind spots in cloud storage, remote endpoints, or OT networks.
Regulatory and Compliance Gaps
Compliance frameworks such as GDPR, HIPAA, and RBI cybersecurity guidelines demand demonstrable control over sensitive data. Point tools rarely provide the audit trails, reporting, and centralized governance enterprises need to prove compliance.
Research Insights: Enterprise Adoption and Efficacy
The data is clear: organizations are shifting to multi-layered defense solutions as part of unified security platforms that combine multiple technologies to detect, disarm, and analyze files at scale.
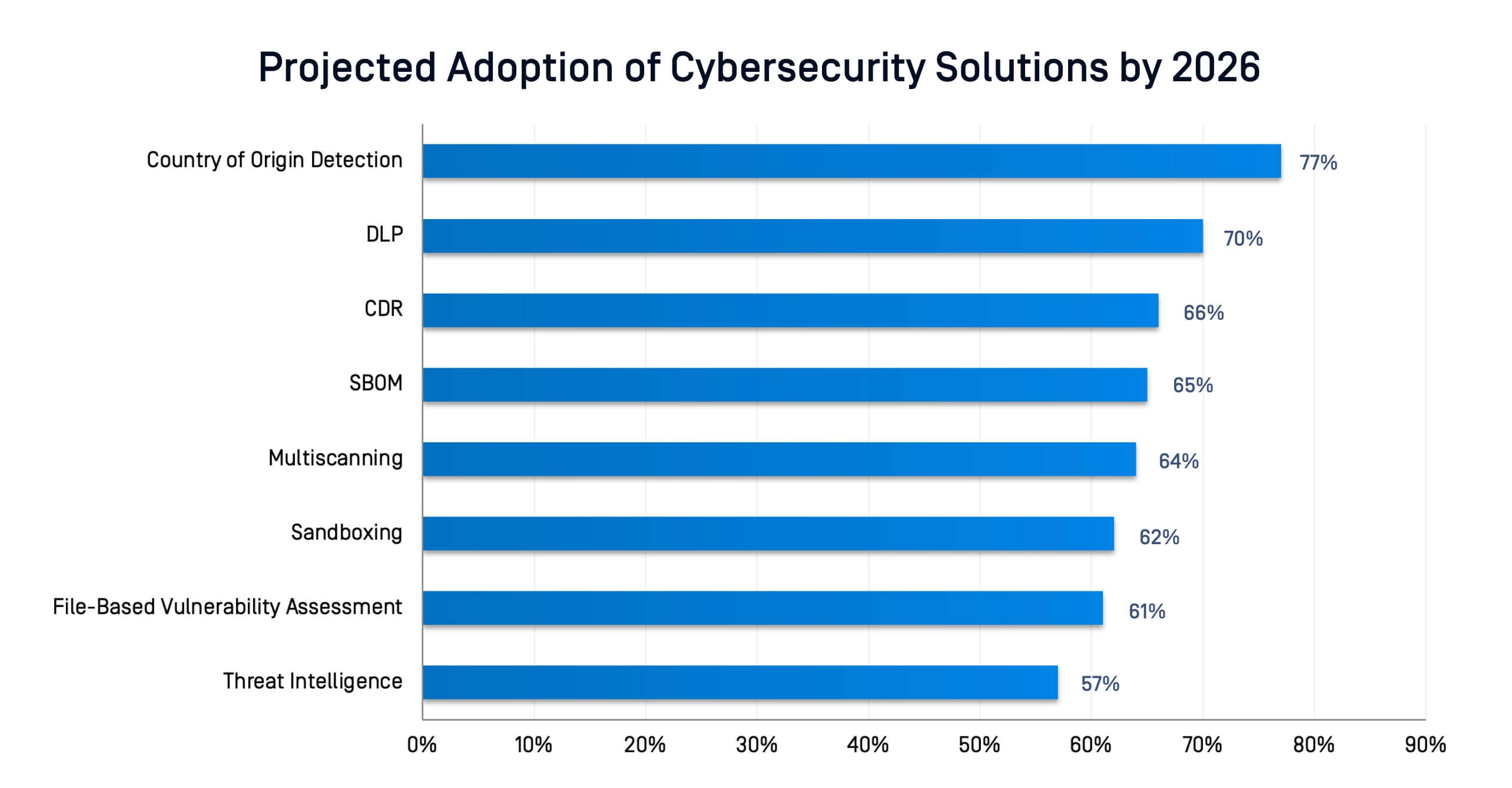
Trends in Enterprise Investment and ROI
CIOs and CISOs report measurable ROI through:
- Reduced or avoided breach costs (Ponemon cites an average cost of $2.7M per incident)
- Lower operational complexity by consolidating tools into a single platform
- Improved compliance posture, reducing the risk of fines and regulatory penalties
Read more about how global industries are responding to modern cyberthreats.
Threat Drivers: Insider Risks, File-Borne Attacks, and Regulatory Pressure

Insider Threats in Hybrid Environments
Ponemon’s research shows 45% of file breaches come from insiders leaking data, while 39% stem from poor visibility and control. Hybrid environments make this worse, as files now move fluidly across cloud platforms, endpoints, and third-party systems, creating more opportunities for misuse.
File-Borne Malware, Ransomware, and APTs
Attackers continue to weaponize files as delivery mechanisms for ransomware and advanced persistent threats. Exploits in everyday file formats allow malicious payloads to bypass legacy defenses, establishing footholds inside enterprise networks.
Compliance, Data Sovereignty, and Regulation
Regulatory mandates, from GDPR and HIPAA to India’s CERT-In SBOM guidelines, make file-level controls a necessity. Data sovereignty requirements also mean organizations must know exactly where sensitive files are stored, accessed, and transferred.
How Platform-Level File Security Reduces Risk, Cost, and Complexity
Centralized Management and Visibility
Platforms unify security policies across workflows—uploads, transfers, downloads, and collaboration. CIOs gain a single pane of glass for file security monitoring, with comprehensive audit logs for compliance.
Integrated Security Controls
Instead of juggling separate tools, platforms orchestrate layered controls in one workflow. Files are scanned, sanitized, and analyzed automatically, whether moving through cloud storage, email, or an OT network.
Lower TCO and Improved ROI
By consolidating multiple point products into a single multi-layered platform, enterprises reduce licensing, integration, and management costs. Ponemon’s findings show that organizations adopting platforms report significant savings in TCO (total cost of ownership) alongside improved resilience.
Get the latest insights on how to get your organization up to speed.
Key Features, Evaluation Criteria, and Best Practices

Must-Have Features
- Multiscanning with multiple anti-malware engines
- CDR to remove embedded threats and zero-day attacks
- Sandboxing with fast dynamic analysis
- File-based vulnerability and SBOM analysis
- DLP and sensitive data classification
- Threat intelligence integration
- Country-of-origin checks
- Centralized policy enforcement
Evaluation Criteria: What to Look For
- Cross-platform compatibility (cloud, endpoint, OT)
- Centralized management console
- Customizable workflows and automation
- Strong reporting and audit capabilities
- Vendor track record in regulated industries
Implementation Best Practices
- Start with high-risk workflows (e.g., third-party uploads, cross-domain transfers)
- Integrate with existing CI/CD pipelines and secure file transfer systems
- Train teams on zero-trust file handling policies
- Regularly update policies to match regulatory mandates and threat intelligence
Building Resilience Against File-Borne Threats
Files are one of the most common attack vectors for threat actors, and traditional solutions can no longer keep up.
Enterprises must adopt a multi-layered file security platform that delivers defense in depth across every file, at every point in its journey.
OPSWAT’s MetaDefender Platform consolidates Metascan™ Multiscanning, Deep CDR, Adaptive Sandbox, Proactive DLP™, SBOM generation, and more into a single, unified framework—helping enterprises reduce cost, strengthen compliance, and protect sensitive files across IT and OT environments.
Discover how OPSWAT can help your enterprise achieve end-to-end file security resilience with advice from industry experts and a live Q&A session.



