Cloud vulnerabilities are security weaknesses or gaps in cloud computing environments, usually stemming from misconfigurations, poor access controls, lack of visibility, or even the use of insecure APIs.
These cloud security issues are continuously sought after by attackers, as they can be easily exploited for unauthorized network and data access.
Either from a lack of knowledge, or a lack of awareness, organizations can not monitor and mitigate these vulnerabilities, as evidenced by last year's cloud-related security incidents: unauthorized access and misconfigurations caused over 50% of the incidents.
This article aims to address the lack of awareness on the subject covering both the most prevalent vulnerabilities in the cloud and best practices for mitigation.
What are Cloud Vulnerabilities?
Cloud vulnerabilities are security blind spots or entry points which can be exploited by malicious actors.
As opposed to traditional environments, where vulnerabilities can most often be found at the perimeter level (such as firewalls), cloud vulnerabilities can come from multiple spaces; such as misconfigurations, access control, an undefined shared responsibility model, Shadow IT, etc.
A cloud environment is inherently interconnected with multiple users, partners, applications, and vendors.
Such a broad attack surface means cloud assets are exposed to threats coming from account hijacks, malicious insiders, account hijacks, poor identity and credential management, and unsafe APIs.
Cloud Vulnerabilities vs. Cloud Security Threats
An obvious difference between threats and vulnerabilities lies in their urgency.
If a vulnerability represents a weakness existing in limbo, waiting to be exploited, then the threat is a malicious or negative event which usually happens in the present moment, requiring urgent intervention.
Next, the vulnerability is what first exposed the organization to cloud security threats.
For example, cloud misconfigurations represent a vulnerability, which can result in weak access controls, finally leading to the threat of a cyberattack.
In short, vulnerability is a weakness, and a threat is the potential action or event that could exploit that weakness. If the cloud were a locked door, the vulnerability would be a lock with a weak spot, and the threat would be someone forcing it open.
Shared Responsibility Model in Cloud Security
The shared responsibility model is a framework originally introduced by AWS around 2011, which circumscribes security responsibilities between could providers and customers:
- Providers secure the cloud infrastructure, including the physical security of data centers, network infrastructure, and hardware, while also being in charge of patching and updating their own applications.
- Customers are responsible for securing their data, applications, operating systems, defining IAM and configurations.
For example, while the provider manages the physical security of the servers, the customer is responsible for configuring security settings for their own environments.
From a vulnerability management perspective, the shared responsibility model means that organizations are responsible for any gaps in their cloud infrastructure.
This involves monitoring their network and apps, identifying possible attack entry points, and eliminating any issues which later become active threats.
Most Common Cloud Vulnerabilities
At their core, cloud infrastructures are built on various layers and components; vulnerabilities can exist at every layer.
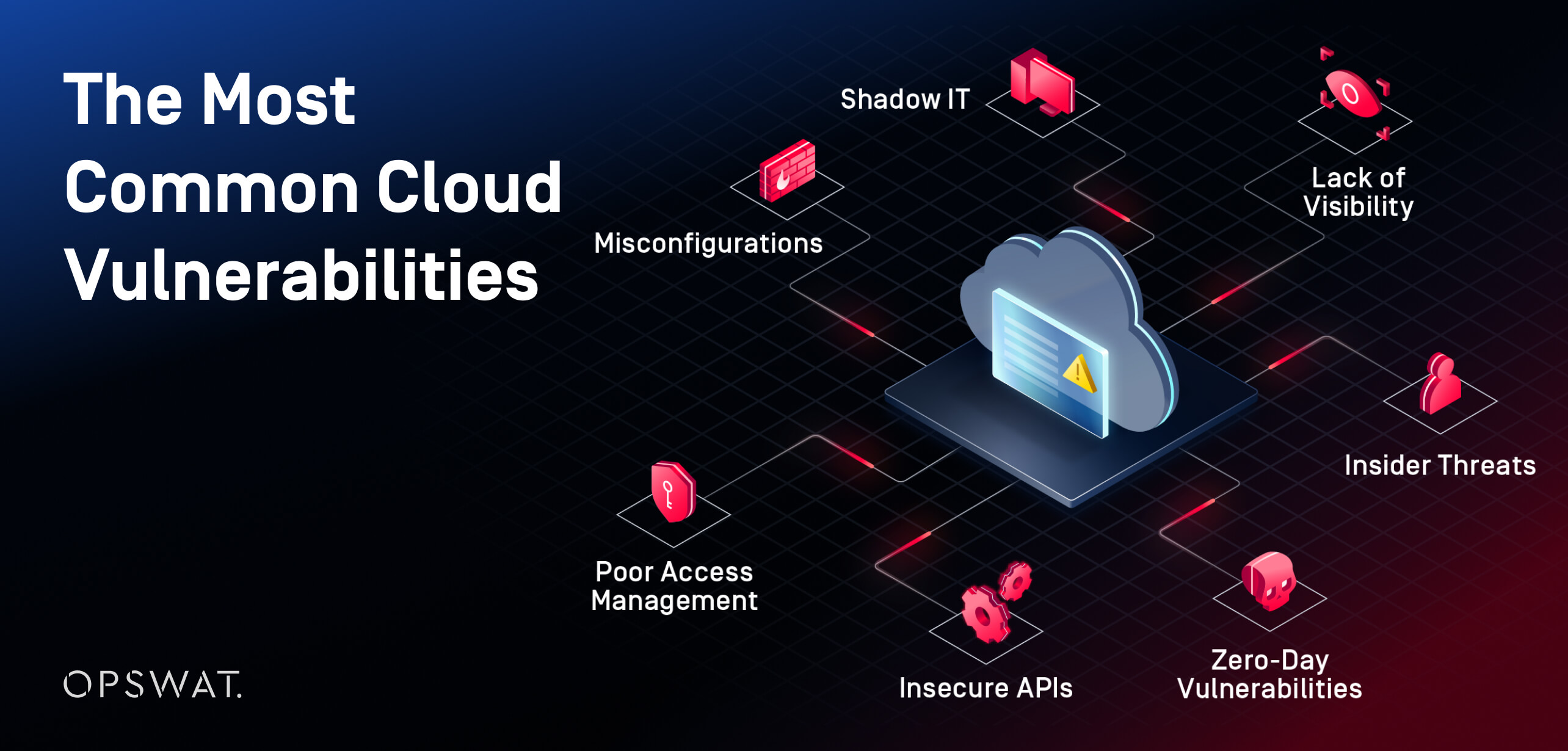
Misconfigurations
A direct consequence of incorrect or overly permissive settings, misconfigurations make a system less secure than it should be. They can happen in cloud-based containers (such as misconfigured S3 buckets), firewalls, or unpatched virtual machines.
Examples of misconfigurations include public read and write access when it should be private, outdated or unpatched permissions, or even lack of encryption settings.
Misconfigurations can happen due to human error, lack of knowledge, or poorly written automation scripts and lead to data loss or leaks, reputational damage in case of an attack, and failure to comply with regulatory standards.
Such was the case with CapitalOne in 2019, when a misconfigured web application firewall enabled the unauthorized access of an S3 bucket containing sensitive data (Social Security Numbers included) on over 100 million customers. CapitalOne had to pay an $80 million penalty, because of the breach.
Lack of Visibility
By definition, cloud environments are fast-moving, decentralized, and often not fully controlled by security teams, so a certain lack of visibility occurs.
It can happen either because providers only offer basic tools for visibility, deeper monitoring coming with an extra cost, or because teams inside an organization are stretched thin and don't have the proper cloud-specific skills needed to truly monitor the infrastructure.
Organizations' tendency to push for speed over security is also a contributing factor.
However, when visibility feels like a cost, not a value-driver, adversaries can penetrate a cloud infrastructure and remain unnoticed for a longer period of time.
With so many tools, dashboards, and logs inside a cloud network it's hard to correlate and gain actionable insights into what is happening.
Poor Access Management
Access management defines which user, or app can access a cloud asset.
It involves managing digital identities and controlling access to cloud services, applications, and data.
Some boundaries and restrictions need to be in place, to ensure sensitive information doesn't end up in authorized hands. In a world where account takeovers are affecting more than 77 million people in the U.S. alone, some practices become paramount:
- Implementing MFA (Multi-Factor Authentication)
- Enforcing the least privilege access principle (grant access only if it's required by the task)
- Using role-based access control to manage access based on job functions
Otherwise, organizations risk data breaches, non-compliance with regulations, and operational disruptions.
Attackers can penetrate a system through a hijacked account and exploit poor access policies, they can move to higher level resources or systems; the goal is to gain more control over the system and potentially cause significant damage.
Insecure APIs
Inside a cloud infrastructure, the API can allow different systems, services, or applications to interact with the cloud environment.
Which means APIs can control access to data, infrastructure, and functionality.
An insecure API may mean that it doesn't require a valid user or token to access it, that it grants more access than needed, or that it logs sensitive data.
If APIs are misconfigured or exposed, attackers access data (user info, financials, healthcare records), even without full credentials.
Such was the case in 2021, when a vulnerability in Peloton’s API allowed anyone to access user account data, even for private profiles. Discovered by Pen Test Partners, the flaw let unauthenticated requests through, exposing details like age, gender, location, weight, workout stats, and birthdays.
Access to such a complex database could have further escalated into doxxing, identity theft, or social engineering attacks.
Shadow IT
Shadow IT refers to the use of software, hardware, or other IT systems within an organization without the knowledge, approval, or control of the IT or security department.
Either for convenience, or out of malice, employees can seek other tools than what’s officially provided, introducing significant cybersecurity risks into the organization.
Shadow IT in practice can look like:
- An employee uploading sensitive engineering documents to personal cloud storage.
- Someone using unauthorized remote access tools (such as AnyDesk) to troubleshoot industrial systems or access SCADA environments in Critical Infrastructure.
- Holding video calls via unvetted platforms (like WhatsApp) instead of the enterprise-standard.
In critical infrastructure or high-security environments, shadow IT can create dangerous blind spots—opening paths for data leakage, malware introduction, or regulatory non-compliance.
Insider Threats
Malicious, negligent, or compromised insiders can be harder to detect due to the trusted nature of the user or system involved.
The potential damage coming from these people can lead to data breaches, service disruptions, regulatory violations, and financial loss.
Zero-Day Vulnerabilities
A zero-day vulnerability is a previously unknown security flaw that has no available fix at the time of discovery, and it can be exploited before the vendor becomes aware of it.
In cloud environments, this includes vulnerabilities in cloud platforms APIs, container orchestration systems, SaaS apps, or cloud-hosted workloads.
The dynamic, interconnected, and multi-tenant nature of the cloud allows flaws to spread quickly and affect many resources, while users lack the necessary visibility into the infrastructure for quick detection.
Additionally, patching cloud systems can take time, increasing the window of exposure to Zero-Days.
Other Vulnerabilities
Less common or emerging cloud vulnerabilities can be just as dangerous as well-known misconfigurations or credential exposures.
One such vulnerability is related to multi-tenancy; a core feature of public cloud platforms, allowing multiple customers to share the same physical infrastructure.
In this situation, if one customer has weak IAM policies, the other can access their resources. If the other is a malicious actor, then the organization is exposed to a data leak risk.
Another common situation in multi-tenancy is one tenant consuming excessive resources which can potentially lead to availability issues and a DoS-like behavior.
Other emerging threats include AI/ML exploits for cloud-based machine learning services. These can be vulnerable to "model poisoning”, where attackers manipulate training data or models to alter behavior, or inference leakage, where sensitive data can unintentionally leak through model outputs.
How Cloud Vulnerabilities Affect Your Business
Starting 2023, preventing cloud misconfiguration has been a primary concern for more than half of companies, according to this report, showcasing the severity of their possible consequences.

Data Breaches and Data Loss
One of the most damaging consequences of cloud vulnerabilities is the exposure or loss of sensitive data.
Organizations often rely on cloud storage solutions to keep their customer records, proprietary information, or operational data.
Thus, a breach can mean the theft of personal identities, financial information, intellectual property, or even trade secrets.
Beyond the immediate effects, such incidents can also lead to long-term reputational damage and a breakdown of customer trust.
Affected individuals may abandon services, and partners may reconsider business relationships.
Even if the breach is contained quickly, the cost of investigation, remediation, customer notification, and potential lawsuits can run into millions of dollars, not including the opportunity costs of lost productivity and brand erosion.
Compliance Violations and Legal Risks
Most industries are governed by strict compliance frameworks—such as GDPR, HIPAA, PCI DSS, or CCPA—that decide how data must be stored, accessed, and protected.
When vulnerabilities lead to unauthorized access or inadequate control over sensitive data, companies risk being found in violation of these laws. Regulators may impose substantial fines, initiate legal proceedings, or enforce operational restrictions.
For example, in jurisdictions like the European Union, penalties under GDPR can reach up to 4% of annual global revenue, turning even a single incident a high-stakes event.
Service Disruption and Business Continuity
Finally, for companies relying on cloud platforms for mission-critical operations, even brief periods of downtime can have severe operational consequences.
Externally, an outage caused by an exploited vulnerability can prevent users from accessing services, completing transactions, or using tools.
Internally, it may stop development, disrupt communication, or interrupt supply chains.
Cloud Vulnerability Management & Mitigation Strategies
Cloud vulnerabilities have been around for enough time so that organizations could develop entire methodologies designed to mitigate vulnerability risks.

Cloud Vulnerability Assessment
Cloud infrastructures are highly dynamic, as new services are deployed and integrations are added regularly.
Each of these changes introduces the potential for misconfiguration or exposures, making vulnerability assessment an ongoing task.
Even when organizations identify vulnerabilities and begin patching, some systems may not function properly with updated versions.
In such cases, certain vulnerabilities must remain for operational continuity, making it essential to manage.
Security teams need a structured approach to document these exceptions, assess the associated risks, and apply appropriate control strategies, such as isolating the vulnerability from the network.
CSPM (Cloud Security Posture Management)
CSPM involves scanning infrastructure for misconfigurations, policy violations, and overly permissive access controls.
Rather than focusing on software flaws, CSPM addresses architectural and configuration risks (misconfigured S3 buckets, unencrypted storage, or IAM transfers) which can lead to data exposure or compliance failures.
CSPM provides real-time visibility into cloud environments, automated checks against compliance frameworks (like CIS, PCI, or GDPR), and alerting on misconfiguration.
Cloud-Native Application Protection Platforms (CNAPP)
CNAPP platforms enhance cloud security unify multiple layers of protection, combining Cloud Security Posture Management Cloud Workload Protection Platforms (CWPP), and vulnerability management into a single framework.
They offer deeper insight across the application lifecycle, from infrastructure configuration to workload behavior and runtime threats.
CNAPPs can integrate with other security tools by embedding host-based detection, behavioral monitoring, and vulnerability scanning directly into virtual machines, containers, and serverless environments.
Access Controls and Multi-Factor Authentication
With strong access controls in place, you can ensure that only authorized users and services can access specific resources, and only to the necessary extent. Access controls include:
- Role or attribute-based access control: permissions are assigned based on roles, identity attributions (such as location, user ID, or clearance level), or conditions (access method, time of access, device security).
- Regular audits and reviews: detect and eliminate excessive or outdated privileges.
- Segregate duties by using different roles for development, operations, and security: reduces risks in the event of credential compromise.
- Granular policies including time-based access, IP restrictions, or specific service-level permissions—to limit access scopes.
- Using automated tools to detect misconfigurations and enforce policy best practices.
An extra layer of protection is added through MFA (Multi-Factor Authentication), requiring users to provide more than one verification method.
MFA combines something users know (like a password), something they have (a mobile device or hardware token), or something that’s a part of them (biometric data like their fingerprint or face).
For cloud environments, MFA:
- Helps prevent unauthorized access in case a password is compromised through phishing, brute force, or data leaks
- Reduces the chance of critical system compromise as it protects privileged accounts
- Supports compliance since it's often required under frameworks such as PCI DSS, HIPAA, and ISO 27001
- Defends environments against lateral movement with stolen credentials in environments with multiple interconnected services.
- Offers low-friction implementation, as most cloud platforms support MFA natively.
Cloud Vulnerabilities: Comparison with Traditional IT Vulnerabilities
In on-prem environments, vulnerabilities would most likely appear at the perimeter level; the boundary between the organization's internal, secured network and the external, often untrusted, network.
Security gaps on-prem could mean outdated software, misconfigured servers, hardware failures, and even physical security breaches.
However, in cloud environments, firewalls and networks no longer form a stable perimeter, as identity becomes the first and most critical security boundary.
Even if foundational security principles remain relevant, the cloud introduces new dynamics, especially around responsibility, visibility, and the volatility of assets.
Cloud vs. On-Premises Security Risks
Cloud environments are mostly exposed to dynamic, API-driven threats, as opposed to on-prem environments where the danger lies in well-understood risks such as unauthorized physical access, insider attacks, or perimeter breaches.
Key differences include the prevalence of misconfigurations as a leading cause of breaches, the presence of short-lived resources (containers, serverless functions), which often evade traditional scanning tools and identity-based attacks becoming more frequent and preferred by attackers.
Moreover, security responsibilities also shift in the cloud, mostly due to the shared responsibility model discussed earlier.
In this framework, organizations are responsible for securing data, applications, configurations, and identities, including all logic around file handling:
- Validating and sanitizing uploaded files.
- Configuring access permissions at the object or bucket level.
- Encrypting data in transit and at rest.
- Implementing monitoring and threat detection on cloud storage interactions.
Industry Terminology and Evolving Threats
Finally, to keep pace with the cloud's velocity and complexity, security leaders must understand both the language and the evolving nature of threats.
A shared vocabulary across DevOps, security, and leadership teams is foundational for coordinated defense, and all team members should be aligned around key industry terms such as:
IAM (Identity and Access Management)
Controls access to resources. Central to cloud security posture.
VM (Vulnerability Management)
The process of continuously identifying, prioritizing, and remediating weaknesses.
CI/CD Security
Ensures that the code pipeline itself isn’t a source of risk, enabling secure, automated deployments.
Ephemeral Resources
Assets such as containers, which are short-lived and challenge traditional monitoring.
Zero Trust
A philosophy where no user or device is trusted by default—even inside the network perimeter.
Moreover, AI and ML risks can no longer be ignored, as organizations embed these technologies deeper into their cloud strategies.
Besides opening new attack surfaces that traditional security models aren’t designed to protect, AI and ML models hosted in the cloud are also susceptible to theft via API abuse, data poisoning through compromised pipelines, and adversarial inputs that manipulate model outputs.
Meanwhile, the widespread use of open-source models and third-party data increases the risk of supply chain attacks, where malicious actors can inject backdoors or tamper with training data undetected.
Threat actors are using AI to evade traditional offensive capabilities, create progressively more convincing phishing attacks, and imitate legitimate behavior to confuse detection-based security.
As both defenders and adversaries adopt AI, cloud environments become a high-stakes battlefield, requiring the large and quick adoption of AI-specific defenses.
A particularly underappreciated vector in the cloud is file handling vulnerabilities, introducing risks such as:
- Weaponized file uploads, where malware is embedded in meta data or executables, and uploaded into a system
- Inadequate visibility into file sharing due to poor logging or weak integration with SIEM tools.
- Exposed data for file downloads where sensitive info isn't properly redacted or access controlled.
Move from Awareness to Total File Protection with MetaDefender Cloud™

With so many malicious actors lurking in the shadows and such a dynamic and unpredictable attack surface, true cybersecurity in the cloud demands continuous monitoring, deep file inspection, and scalable solutions built for cloud-native environments.
That’s where MetaDefender Cloud™ comes in.
Built on the “Trust no file” philosophy, it’s designed to detect, disarm, and prevent known, unknown and AI-generated threats.
With trademark technologies - Deep CDR™ Technology, Metascan™ Multiscanning, Adaptive Sandbox, and Proactive DLP™ - MetaDefender Cloud offers true prevention from file-born threats.
Discover how MetaDefender Cloud can seamlessly secure your cloud workflows, up and running in seconds; before threats become attacks.
Frequently Asked Questions (FAQs)
Q: What are cloud vulnerabilities?
Cloud vulnerabilities are weaknesses or gaps in a cloud environment, which can be exploited by cyber attackers. These vulnerabilities can lead to unauthorized access, data breaches, service disruptions, or other security incidents.
Q: What is cloud computing?
Cloud vulnerabilities are weaknesses or gaps in a cloud environment, which can be exploited by cyber attackers. These vulnerabilities can lead to unauthorized access, data breaches, service disruptions, or other security incidents.
Q: What are the most common cloud vulnerabilities?
Some of the most common cloud vulnerabilities include misconfigured cloud storage or services, weak or stolen credentials, insecure APIs, unpatched software or systems, or insufficient access controls.
Q: How secure is the cloud?
Cloud security depends on both the cloud provider and the customer. Leading cloud providers invest heavily in security, offering strong tools and compliance certifications. However, security gaps can occur due to human error, misconfigurations, or inadequate policies.
Q: How do cloud vulnerabilities affect your business?
Cloud security depends on both the cloud provider and the customer. Leading cloud providers invest heavily in security, offering strong tools and compliance certifications. However, security gaps can occur due to human error, misconfigurations, or inadequate policies.
Q: What are the most common cloud security threats?
Key cloud security threats include account hijacking, data breaches, DDoS attacks, malware or ransomware attacks.
Q: What are the mitigation strategies for cloud vulnerability management?
To secure cloud environments, regularly patch and update systems, enforce strong identity and access management (IAM), and encrypt data both at rest and in transit. Continuously monitor and audit cloud resources, perform vulnerability assessments and penetration tests, establish clear security policies and incident response plans, and use protective tools like firewalls, endpoint security, and intrusion detection systems.

