- What is Cloud Vulnerability Management?
- Types of Cloud Vulnerabilities
- Cloud Vulnerability Management Process & Lifecycle
- Key Components and Techniques in Cloud Vulnerability Management
- Implementation Approaches & Best Practices
- Parallel and Related Security Concepts
- Benefits and Challenges of Cloud Vulnerability Management
- Frequently Asked Questions (FAQs)
Introduction
The latest data shows that cloud environments are increasingly targeted by cybercriminals, as seen in IBM’s Cost of a Data Breach report, which showed that 15 % of initial attack vectors exploited cloud misconfigurations.
While 15% might not seem a concerning metric, it means; one in six breaches start because cloud vulnerabilities were not detected in time.
Every system has vulnerabilities that attackers can target, especially in dynamic environments with rapid deployments and large volumes of third-party components.
These blind spots demand dedicated cloud-native solutions, not retrofitted on-prem tools.
In this context, cloud vulnerability management - the act of detecting, evaluating, prioritizing, and resolving security issues within a cloud setup – becomes an urgent focus for security professionals everywhere.
What is Cloud Vulnerability Management?
Cloud Vulnerability Management (CVM) is the process of identifying, assessing, prioritizing, and fixing security gaps in cloud environments.
These might be problems that administrators can fix, issues that require vendor updates, or hidden threats that have yet to be discovered.
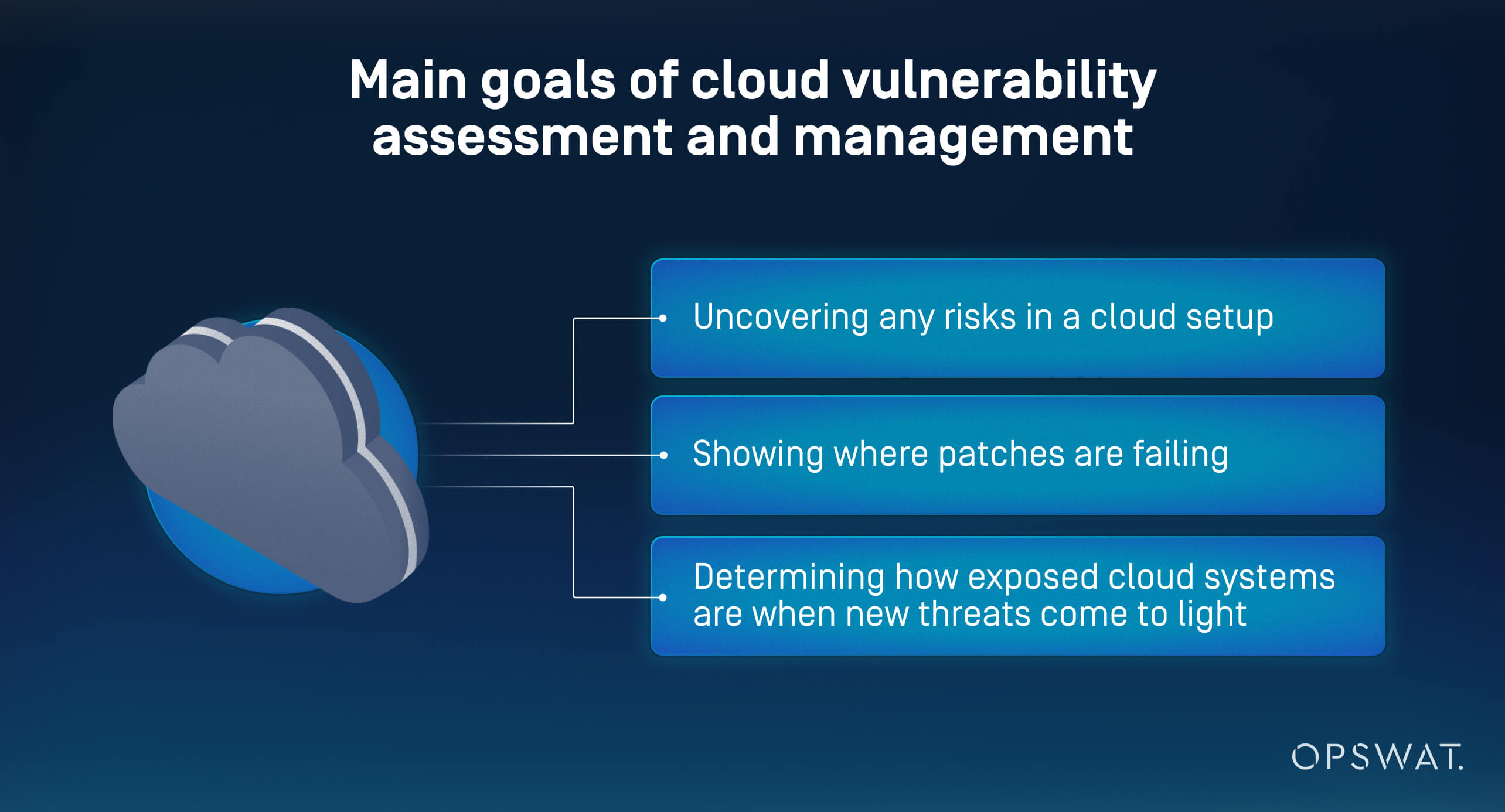
The main goals of cloud vulnerability management and assessment are:
- Uncovering any risks in a cloud setup
- Showing where patches are failing
- Determining how exposed cloud systems are when new threats come to light
In short, CVM helps reduce the chance of cyberattacks and shortens response time when urgent issues arise.
Modern platforms like OPSWAT’s MetaDefender Cloud go beyond basic vulnerability scanning by including threat intelligence and advanced malware detection across multi-cloud environments.
Cloud Vulnerability Management vs. Traditional Vulnerability Management
Traditional vulnerability management was built for on-premises systems, where assets rarely change, and threats are easier to track.
For on-prem systems, tools like firewalls, AV engines, and intrusion detection systems were built to secure a predictable infrastructure and often focus on fixed schedules.
Cloud environments are different therefore, cloud-specific vulnerability management is built for constant change.
A cloud-focused approach also allows for risk-based prioritization, weighing context like asset exposure, versioning, and runtime behavior.
Traditional tools simply aren’t equipped to handle that level of detail in cloud environments.
A cloud-first, purpose-built approach avoids unnecessary drag on performance and better fits the way cloud systems actually operate.
Types of Cloud Vulnerabilities
When talking about vulnerabilities, we are referring to weak points in a system (flaws, oversights, or gaps) that attackers can use to gain access or cause damage.
Unpatched software is a source of risk, especially for self-propagating attacks. These usually rely on a combination of unpatched systems and poor AV control processes to penetrate a system.
Exposed APIs are easy targets when not secured properly, as they can allow attackers to disrupt services or drain resources.
Another major concern relates to weak IAM (Identity and Access Management) controls, which can allow attackers to move through systems once they get in.
Cloud Misconfiguration
A common and more cloud-specific weakness lies in misconfiguration, when cloud resources are set up in a way that creates unintended access or exposure.
Leaving cloud storage open to the public or failing to restrict access to computer resources can expose sensitive data. In one 2021 case, over 38 million records were exposed through a misconfigured Microsoft Power Apps portal.
Misconfigurations are rarely the result of negligence. They are often linked to the speed of deployment, lack of clear policies, or limited visibility across cloud assets.
The risks are wide-ranging: data exposure, lateral movement, unauthorized changes, and service disruption.
Because misconfigurations usually don’t require much effort to exploit, they remain a favored entry point for attackers.
Vulnerabilities in Cloud-Native Applications
Cloud-native applications built with containers, serverless functions, and microservices bring their own set of risks. These aren’t always about insecure settings, but about how code runs and interacts across dynamic environments.
With frequent deployments and short-lived workloads, traditional scanning tools can’t keep pace.
New code, third-party packages, and runtime behavior all introduce unknowns that don’t show up during pre-deployment testing.
One growing concern in cloud-native stacks is weaponized file uploads.
Many cloud apps accept user-uploaded files. If validation is weak or missing, attackers can inject files containing malware or scripts designed to exploit backend services.
Weaponized file uploads can be neutralized through threat extraction, achieved with CDR (Content Disarm and Reconstruction) technologies. CDR removes embedded malware from file uploads, without compromising the file.
Because cloud-native systems often use object storage like AWS S3 or Google Cloud Storage, improperly secured upload endpoints can also expose sensitive files or allow unrestricted access.
To address these risks, some tools and platforms, built to handle the speed and scale of cloud-native environments, have become essential. Such platforms include:
CNAPP (Cloud-Native Application Protection Platform)
CNAPP helps connect security across the full lifecycle.
It gives visibility into how applications behave in the cloud, flags suspicious behavior, and helps prevent insecure code from being deployed.
CWPP (Cloud Workload Protection Platform)
CWPP focuses on the workloads themselves, monitoring running containers, VMs, and functions. The scope is detecting any unusual activity and preventing malicious code from being executed.
Cloud Vulnerability Management Process & Lifecycle
CVM makes security strategic rather than reactive.
Instead of waiting for threats to appear, teams scan for weak spots across their environments, making vulnerability management more precise and aligned with how cloud systems work.
Step 1: Vulnerability Identification
Knowing what to fix starts with finding the problem, but in cloud environments, traditional scanning isn’t enough.
In this first step, cloud applications, data storage services, and infrastructural elements such as networks are scanned to identify exploitable vulnerabilities.
These include unpatched vulnerabilities, misconfigurations, and IAM issues.
Step 2: Vulnerability Assessment
Vulnerability assessment involves identifying, assessing, prioritizing, and remediating security weaknesses.
It should result in a report showcasing at-risk assets which need patching or further investigation and remediation.
Risk assessment, informed by threat intelligence, involves analyzing exposure, potential impact, and exploitability. Sandbox environments can be used to simulate malware behavior, giving teams clearer insight into how a specific threat would behave within their systems.
Step 3: Prioritization
Since most teams don’t have time to fix every issue at once, professionals will perform risk-based prioritization to focus efforts accordingly.
Prioritization factors include whether the asset is public-facing, how easy the exploit is to run, and what damage it might cause.
A low-severity flaw on a critical production service often matters more than a high-severity one buried in test code.
Step 4: Remediation & Mitigation
Remediation involves applying patches, hardening configurations, or disabling exposed services.
Many teams use remediation workflows integrated into CI/CD pipelines or security orchestration tools.
When a full fix isn’t possible right away, mitigation steps (like isolating a vulnerable workload) can reduce risk in the short term.
Step 5: Verification & Reporting
After patching, teams need to confirm that the problem has been resolved.
This step includes rescanning to check for the issue again, reviewing logs, and testing the fix. Reporting helps document the process. It also supports audits and shows progress on internal teams.
Key Components and Techniques in Cloud Vulnerability Management
SoC (Security Operations Center) teams rely on a mix of tools, workflows, and data to stay ahead of threats in cloud environments.
Since detection is only step one, SoC teams also apply patch management strategies to close gaps, and they maintain strict IAM controls to limit exposure when flaws are present. These efforts work together to reduce the number of entry points available to attackers.
Cloud Vulnerability Management Tools & Platforms
These tools and platforms scan systems for known flaws, often referencing large vulnerability databases like CVE and NVD to detect issues before attackers do.
At a minimum, effective tools must:
- Run scheduled and continuous scans for bugs, misconfigurations, and security weaknesses
- Track user roles, access rules, and account behavior through profile controls
- Trigger alerts through clear and customizable notification settings
- Rank vulnerabilities by severity using scoring models and visual dashboards
- Assess policy compliance
- Show attack paths and surface exposure across cloud-facing assets
- Support centralized management of agents and scanners
- Provide patch version control and change tracking
- Generate exportable reports for audits and internal review
- Include automated maintenance, updates, and upgrade options
- Offer authentication control beyond the basics (MFA, SSO, etc.)
- Model attack vectors and identify potential lateral movement paths
- Use Deep CDR to sanitize uploaded and shared files, to ensure only safe content reaches cloud storage or applications
Other criteria for choosing a cloud vulnerability management tool include coverage and scalability, ease of deployment, automation or workflow integration, and compliance capabilities.
Metrics and KPIs for Cloud Vulnerability Management
No matter how high-tech your tools are, raw scan results aren’t too revealing when running in a void.
This is why teams use metrics to convert findings into clear, trackable figures that support decisions, prioritize fixes, and show whether the process is working.
Key metrics to track include:
- Vulnerability Detection Rate: how many real issues are found during scans or manual checks
- MTTD (Mean Time to Detect): how fast new vulnerabilities are found once disclosed or deployed
- MTTR (Mean Time to Remediate: time from detection to resolution or patch
- Exploitability Score: shows whether a vulnerability is actively being exploited or targeted
- Patch Compliance Rate: how many known issues are patched within a set timeframe
- Number of Open Vulnerabilities: tracks the total backlog and whether it’s shrinking or growing
- Percentage of Critical Vulnerabilities Addressed: how quickly high-risk items are resolved; often tracked against targets like 24 hours, 7 days, or 30 days
- Risk Score per Asset/Subnet: rank assets by severity, exposure, and likelihood of attack
- Scan Coverage Rate: the percentage of assets scanned per cycle
These numbers make it easier to spot where processes break down, where investment is needed, and whether existing efforts are aligned with the risks that matter most.
Implementation Approaches & Best Practices
Cloud Vulnerability Management into action means going beyond basic scanning for weak points, becoming a system which prioritizes real risks and scales with your cloud architecture.
The most effective approach combines risk-aware decision-making with automation that’s wired directly into cloud assets and workflows.
Vulnerability management doesn’t stop at detection but continues to push fixes through infrastructure-as-code or policy engines, closing the loop fast.
Of course, it all depends on strong continuous monitoring across both the cloud control plane and your workloads.
Just as important is making sure your vulnerability management framework fits into the rest of your cloud security stack. Otherwise, there's a risk of slowing down developers or wasting time on redundant alerts.
Automating Cloud Vulnerability Management
Through automation, teams can detect and respond to threats faster, reduce operational overhead, and create a consistent approach to managing vulnerabilities across sprawling, fast-moving environments.
It also lays the groundwork for continuous compliance by enforcing policy-driven controls and generating audit trails automatically.
End-to-end automation, from detection to remediation, removes the lag between identification and action and reduces human error.
Integrating with Cloud Security Frameworks
A well-designed vulnerability management program must align with broader cloud security frameworks and regulatory standards like the NIST Cybersecurity Framework, CIS Benchmarks, ISO/IEC 27001, and others.
For example, ISO/IEC 27001 frames vulnerability management as part of a broader Information Security Management System (ISMS).
If you want to read more about ISO/ICO 27001, you can download this free compliance guide.
MetaDefender Cloud aligns with multiple security frameworks, ISO/ICO included, by offering detailed audit logs and scan reports as part of a broader compliance strategy.
Frameworks drive a more policy-driven approach: risks must be documented, mitigations must be auditable, and processes must be repeatable.
In practice, that means CVM must integrate with incident response plans, asset classification, and configuration management databases (CMDBs), not just exist as technical control.
Benefits and Challenges of Cloud Vulnerability Management
The true CVM value is visible when it becomes part of the DevOps’ DNA.
When DevOps, IT, and security teams share scan results at every stage, from code commit to deployment, the entire organization embraces a “shift‑left” mindset.
Security reviews aren’t checkboxes at the end of a sprint; they’re integrated into pull requests, build pipelines, and sprint planning.
As a result, engineers learn secure coding practices, security champions emerge, and preventive security transforms from policy to practice.
Other clear benefits include:
Better Security and Compliance
Proactive vulnerability scanning in the cloud ensures that misconfigurations, unpatched services, and insecure interfaces are detected and remediated before attackers exploit them.
Improved Visibility and Control
Automated scans across workloads, containers, serverless functions, and APIs provide near‑continuous asset discovery and risk scoring.
Security teams can prioritize high‑impact issues, track remediation progress, and integrate findings into DevOps pipelines.
Resource Efficiency and Cost Savings
Automated scans across workloads, containers, serverless functions, and APIs provide near‑continuous asset discovery and risk scoring.
Security teams can prioritize high‑impact issues, track remediation progress, and integrate findings into DevOps pipelines.
EarlyNotification of Zero‑Day Threats
Integrations with threat‑intelligence feeds and anomaly detection engines allow CVM solutions to flag indicators of compromise and zero‑day exploits the moment they emerge.
Overcoming Common Challenges
Real‑world cloud environments come with their own challenges for CVM; here are two of the most common ones.
Addressing Cloud Complexity
Modern applications span across virtual machines, containers, managed databases, and third‑party services. Often, these are spread across multiple accounts, regions, and teams.
Every new microservice or environment can introduce an unscanned attack surface.
To address it, use an agentless, API‑driven scanning approach that automatically discovers every cloud resource across your organization’s accounts and subscriptions.
Implement IaC (Infrastructure as Code) scanning plugins to catch misconfigurations before they’re deployed.
Managing Multi-Cloud Environments
Enterprises increasingly leverage AWS, Azure, GCP (and sometimes smaller providers) in parallel.
Each comes with its own security model, APIs, and best practices. Tools that excel in one cloud may be blind to another.
Managing multi-cloud environments involves deploying a single, centralized CVM platform that natively integrates with all your cloud providers via their respective APIs.
Standardize your vulnerability remediation workflows so that risks are sorted, assigned, and tracked in the same system.
Whenever possible, leverage cross‑cloud policies and automate policy enforcement.
Eliminating File-Based Threats One Scan at a Time
Preventing cloud‑focused attacks demands continuous, proactive vigilance. That’s exactly why our “Trust no file” philosophy powers OPSWAT’s MetaDefender Cloud.
As more applications move to the cloud, we’ve built a cybersecurity platform which can scale to meet changing requirements and the growing need for advanced application security services.
By combining Deep CDR with Multiscanning, plus real‑time sandbox analysis and OPSWAT’s threat intelligence, MetaDefender Cloud blocks zero‑day and file‑based attacks before they ever reach your environment.
Ready to make cloud vulnerability management truly preventative? OPSWAT MetaDefender Cloud offers multilayered file security, increased visibility and effortless integration with your existing cloud workflows.
Start protecting your environment today!
Frequently Asked Questions (FAQs)
What is cloud vulnerability management?
Cloud vulnerability management is the process of detecting, evaluating, prioritizing, and resolving security issues within a cloud setup.
How does cloud vulnerability management work?
Cloud vulnerability management uses automated tools and processes to scan for vulnerabilities, analyze their potential impact, and implement fixes or mitigations to reduce the risk of exploitation.
What are the types of cloud vulnerability?
Most common cloud vulnerabilities are misconfigurations, insecure APIs, insider threats, lack of visibility, poor access management, shadow IT, system vulnerabilities, and zero-day exploits.
What is vulnerability management in cloud computing?
Specifically for cloud computing, vulnerability management is the proactive process of identifying, assessing, prioritizing, and remediating cloud-specific security vulnerabilities within cloud infrastructures.
What is vulnerability management in cloud computing?
Specifically for cloud computing, vulnerability management is the proactive process of identifying, assessing, prioritizing, and remediating cloud-specific security vulnerabilities within cloud infrastructures.
How do you mitigate cloud vulnerabilities?
Mitigating cloud vulnerabilities involves implementing strong IAM policies, enforcing encryption for data at rest and in transit, and regularly patching systems.
Use cloud-native security tools for monitoring, audit access controls periodically, and ensure secure network configurations like firewalls and segmentation. Lastly, have a comprehensive backup and disaster recovery plan in place.
What are the benefits of cloud vulnerability management?
Better security and compliance, improved visibility and control, resource efficiency and cost savings, and early notification of Zero‑Day threats are some of the benefits of CVM.
What are the challenges of cloud vulnerability management?
The main challenges of cloud vulnerability management are addressing cloud complexity and navigating multi-cloud environments.
What are the 5 steps of vulnerability management?
- Identification
- Assessment
- Prioritization
- Remediation & Mitigation
- Verification & Reporting