The Imperative of OT Security
When operational technology systems come under attack, the consequences extend far beyond individual organizations. Recent high-profile incidents, such as the ransomware attack on an American oil pipeline, have illustrated the fragility of critical infrastructure and its dependence on secure OT environments.
This particular breach resulted in a $4.4 million payout and interrupted millions of barrels of oil production, causing widespread economic and operational disruptions. The incident highlighted a key vulnerability: even air-gapped OT networks are not immune to cyberthreats, especially when reliant on physical media for updates and maintenance.
This article explores the role of secure file transfer solutions in protecting industrial environments. By integrating file-based threat prevention tools into their networks, organizations can create a robust, multi-layered defense against evolving cyberattacks while securing the continuity of their business operations.
4 Main Differences Between IT & OT Cybersecurity
The convergence of IT (Information Technology) and OT (Operational Technology) environments introduces complex security challenges, driven by their differing operational priorities and technological requirements. Find out about the 4 key challenges of bridging IT and OT environments here.
IT systems prioritize flexibility and efficiency, while OT systems demand reliability and continuity, often operating without interruption in high-security industries. Bridging these priorities requires solutions designed to facilitate seamless, secure and compliant data flows across both domains, while addressing the distinct vulnerabilities inherent to OT environments.
Routine vulnerability and penetration testing in IT is challenging to replicate in OT environments due to outdated systems, infrequent updates, supply chain vulnerabilities and flat network architectures. Additionally, OT systems are more sensitive to disruptions caused by testing.
Passive assessments and limited active testing are thus common approaches, but these methods may not fully uncover vulnerabilities in live systems or address risks introduced by external data and updates. While these practices reduce immediate operational risks, they lack the comprehensive security needed to safeguard OT systems against evolving threats.
IT environments typically enforce device locking to prevent unauthorized access during inactivity. In OT settings, Human Machine Interfaces (HMIs) are often shared among multiple users in production halls and locking them is impractical due to life safety considerations.
Physical barriers can restrict access to authorized personnel, but these alone may not provide the level of security required to protect sensitive OT systems from insider threats or unauthorized usage.
In OT environments, components are often unable to generate or transmit logs to appropriate destinations. Even when logs are available, they may not be interpretable in standard IT environments. As a result, OT experts rely on manual checks to assess equipment status.
Relying on manual checks to assess equipment status introduces inefficiencies and potential blind spots, making it difficult to maintain comprehensive oversight and address security risks effectively.
IT systems commonly define recovery points to revert to a consistent state after disruptions. OT environments, however, require unique approaches due to real-world constraints. For example, an aluminum foundry cannot resume production at the exact point it was interrupted without accounting for changes, such as molten aluminum solidifying.
This reliance on tailored, manual approaches can increase the risk of prolonged downtime and make it harder to ensure a smooth and secure restoration of operations.
Strengthening Security Through Managed File Transfer
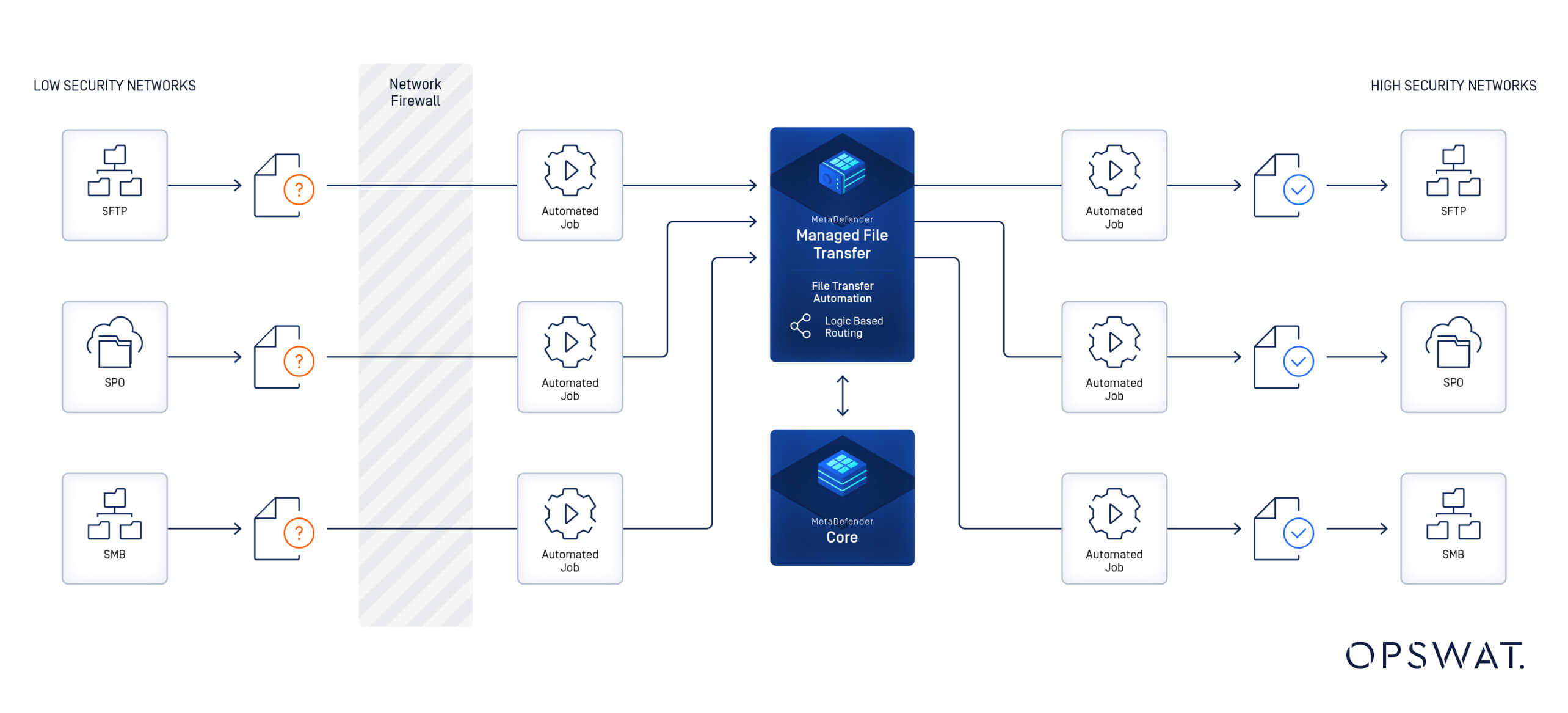
Operational stability requires robust solutions tailored to the distinct needs of IT and OT environments. Secure Managed File Transfer (MFT) solutions serve as an essential tool for ensuring secure, compliant and efficient file exchanges across IT and OT systems.
By addressing key vulnerabilities such as unauthorized access, data tampering and file-based threats, MFT provides the foundation for resilient cross-system cybersecurity.
Authentication and Authorization
The critical importance of authentication is highlighted by the Finastra data breach, where incomplete security steps during an SFTP-based file transfer allowed attackers to compromise sensitive customer information.
Such risks can be mitigated with file transfer solutions that incorporate essential security measures such as MFA (multi-factor authentication) to verify user identities, SSO (Single Sign-On) for streamlined access management and robust role-based access controls to limit authorized access. Additionally, supervisory approval workflows ensure that sensitive file transfers are reviewed and authorized by designated personnel, adding an extra layer of security and accountability.
While many MFT solutions provide these foundational capabilities, OPSWAT’s MetaDefender Managed File Transfer (MFT) offers advanced authentication measures tailored to critical infrastructure environments. These include RBAC (role-based access control), MFA (multi-factor authentication) and integration with SSO (Single Sign-On) solutions. These features ensure that only authorized individuals can access sensitive data while meeting stringent regulatory requirements.
Visibility and Control
The 2024 AT&T breach via a Snowflake account revealed significant gaps in monitoring and access control for third-party cloud platforms. Attackers used stolen credentials to exfiltrate vast amounts of sensitive customer data, affecting over 100 million individuals. This incident underscores the importance of real-time monitoring and centralized management in file transfer processes to promptly detect unauthorized access and secure sensitive information.
To prevent similar incidents, OPSWAT’s MetaDefender Managed File Transfer (MFT) provides detailed audit logs, offering complete visibility into file activities. This ensures traceability and regulatory compliance while enabling organizations to identify and address potential risks swiftly. By consolidating file management on a single system, inefficiencies are minimized, and operational oversight is enhanced.
Complementary Cross-Domain Solutions
In combined IT and OT environments, securing file transfers requires more than standalone solutions. To address the diverse challenges of secure data exchange, a comprehensive approach is essential. From safeguarding physical media to ensuring secure cross-network data transfers, combining multiple tools and strategies can create a cohesive, multi-layered cyber defense.
OPSWAT’s range of solutions are specifically tailored to the unique needs of high- and low-security environments. By integrating these tools, organizations can establish a comprehensive, cross-domain strategy that addresses IT and OT cybersecurity challenges effectively, maintaining operational integrity.

A leading healthcare provider faced a ransomware attack that targeted its IT and OT systems, disrupting file transfers and data workflows. MetaDefender Managed File Transfer (MFT) with Multiscanning technology provided the backbone for secure and compliant file transfers, enabling automated workflows and regulatory adherence.
Multiscanning technology leverages 30+ leading anti-malware engines to proactively detect over 99% of malware by using signatures, heuristics, and machine learning. Deep CDR™ Technology removes malicious content from files while preserving usability, providing zero-day protection for OT environments.

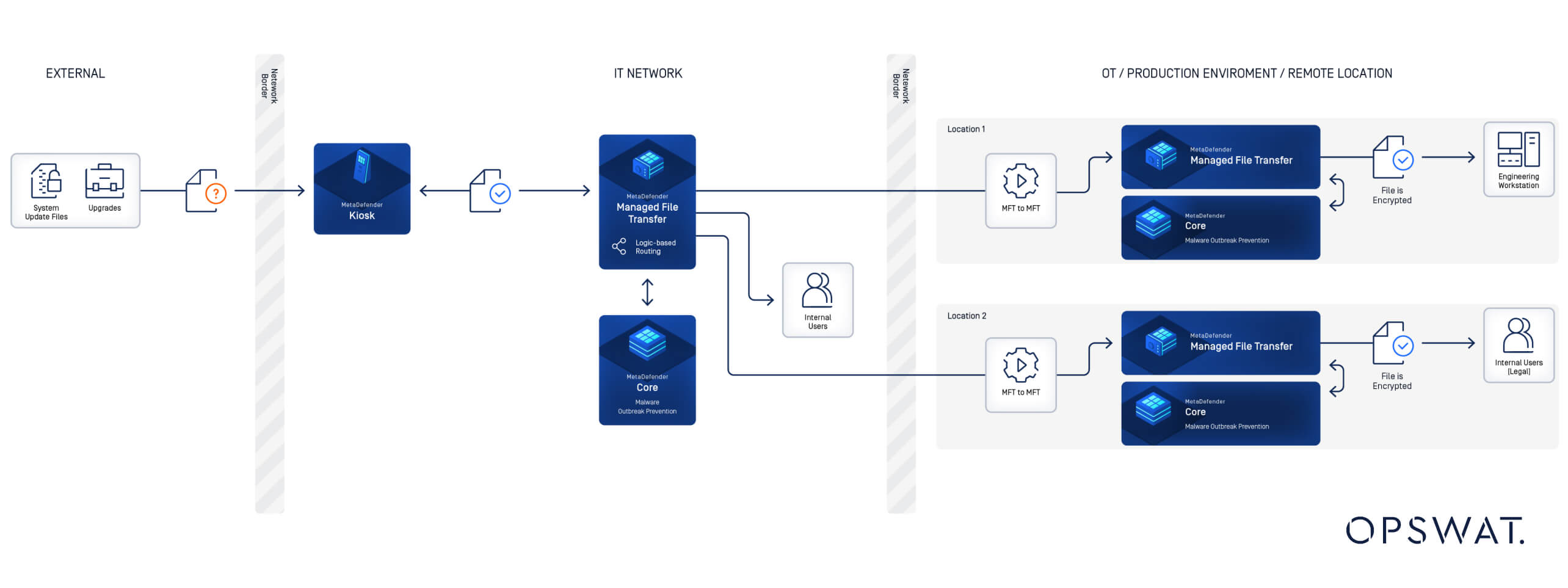
A major energy company needed to secure its OT systems against vulnerabilities introduced by removable media, which was frequently used by contractors and engineers for updates. MetaDefender Managed File Transfer (MFT), combined with Kiosk, played a central role by enabling secure file transfers and ensuring compliance with industry standards.
In OT environments, removable media remains a major source of vulnerabilities. MetaDefender Kiosk mitigates these risks by scanning and sanitizing files from USB drives, CDs, and other devices before they enter secure domains. Equipped with advanced malware detection and file sanitization capabilities, it ensures that only safe files are introduced into the network.
A Seamless Defense Strategy for Converged Systems
As critical infrastructure industries face mounting cybersecurity challenges, the convergence of IT and OT systems demands innovative and comprehensive solutions. MetaDefender Managed File Transfer (MFT) emerges as the cornerstone of this defense strategy, enabling secure, compliant, and efficient data transfers across complex environments.
When integrated with complementary MetaDefender solutions such as Kiosk, NetWall and Email Security, MetaDefender Managed File Transfer (MFT) delivers a robust, multi-layered approach to cybersecurity. This synergy not only protects sensitive OT assets from evolving cyberattacks but also ensures operational continuity and regulatory compliance—factors that are indispensable in high-security environments.
The stakes are too high to rely on fragmented or outdated security measures. By adopting an integrated defense strategy powered by OPSWAT’s MetaDefender solutions, organizations can build resilient infrastructures capable of withstanding modern cyberattacks while maintaining seamless operations.
For critical industries, the path forward is clear: embrace a proactive, unified approach to OT security, with MetaDefender Managed File Transfer (MFT) as the foundation of a secure and resilient future. To learn more about MetaDefender Managed File Transfer (MFT), visit our product page.