The increasing frequency and sophistication of cyberattacks on ICS (Industrial Control Systems) and OT (Operational Technology) networks pose significant concerns for industries worldwide. These attacks have demonstrated the vulnerabilities inherent in critical infrastructure, leading to severe operational disruptions and financial losses. This article highlights some of the most prominent ICS/OT cyber incidents, examining their attack vectors and uncovering correlations that can inform better cybersecurity practices.
Stuxnet Attack
Discovered in 2010, Stuxnet is one of the most well-known and sophisticated cyberattacks targeting ICS. It specifically targeted Iran's Natanz nuclear facility, utilizing zero-day vulnerabilities and spreading through infected USB drives.
- Malicious USB Devices: The malware was introduced into the facility through infected USB drives. Once inside, it spread to Siemens Step7 software, which is used to program industrial control systems.
- Propagation: Stuxnet exploited multiple zero-day vulnerabilities and used a rootkit to hide its presence on the infected systems. It targeted Siemens PLCs (Programmable Logic Controllers) to alter the speed of centrifuges, causing them to malfunction and physically degrade.
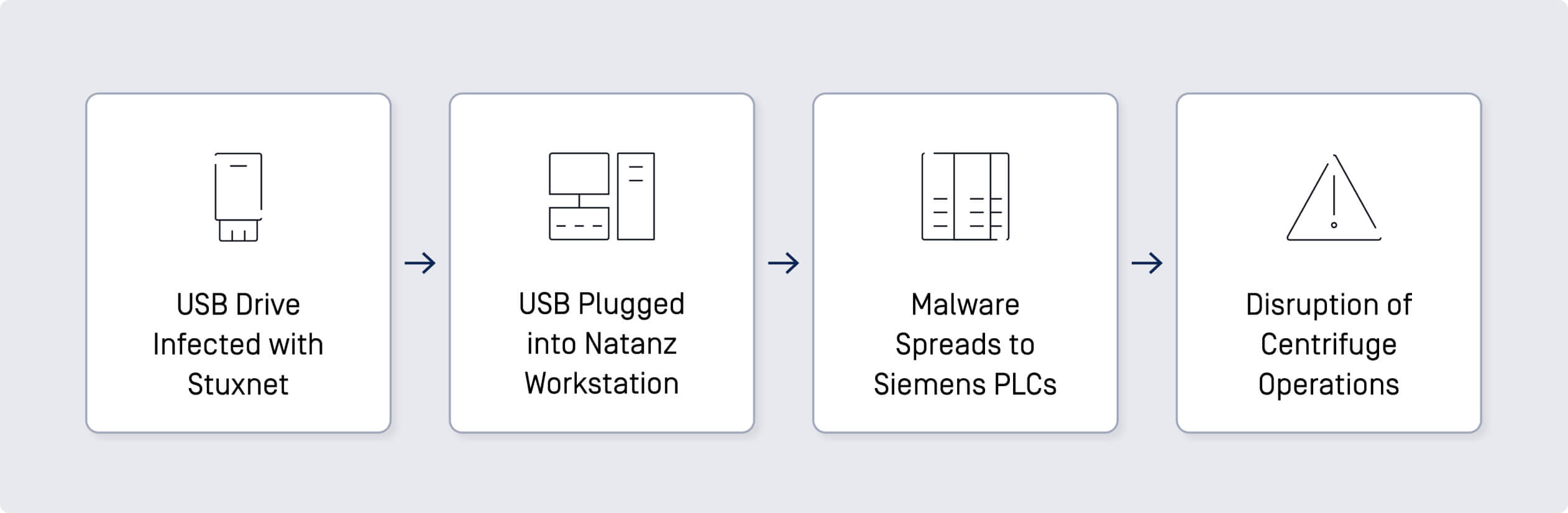
The attack led to significant disruption of Iran's nuclear enrichment capabilities, delaying their program by damaging approximately 1,000 centrifuges. This incident highlighted the risks associated with physical media in secure environments.
Ukraine Power Grid Attack
The Ukraine power grid attacks in December 2015 and December 2016 are notable examples of cyber-physical attacks. These incidents involved advanced persistent threat (APT) groups using sophisticated methods to disrupt the power supply.
- Spear-Phishing Emails: Attackers sent spear-phishing emails to employees of the Ukrainian power companies. These emails contained malicious attachments that, when opened, installed BlackEnergy malware on the target systems.
- IT Network Compromise: Once inside the IT network, the attackers used stolen credentials to gain access to the SCADA (Supervisory Control and Data Acquisition) systems, which control the power grid.
- Manual Interference: The attackers manually operated the breakers, causing power outages across multiple regions.
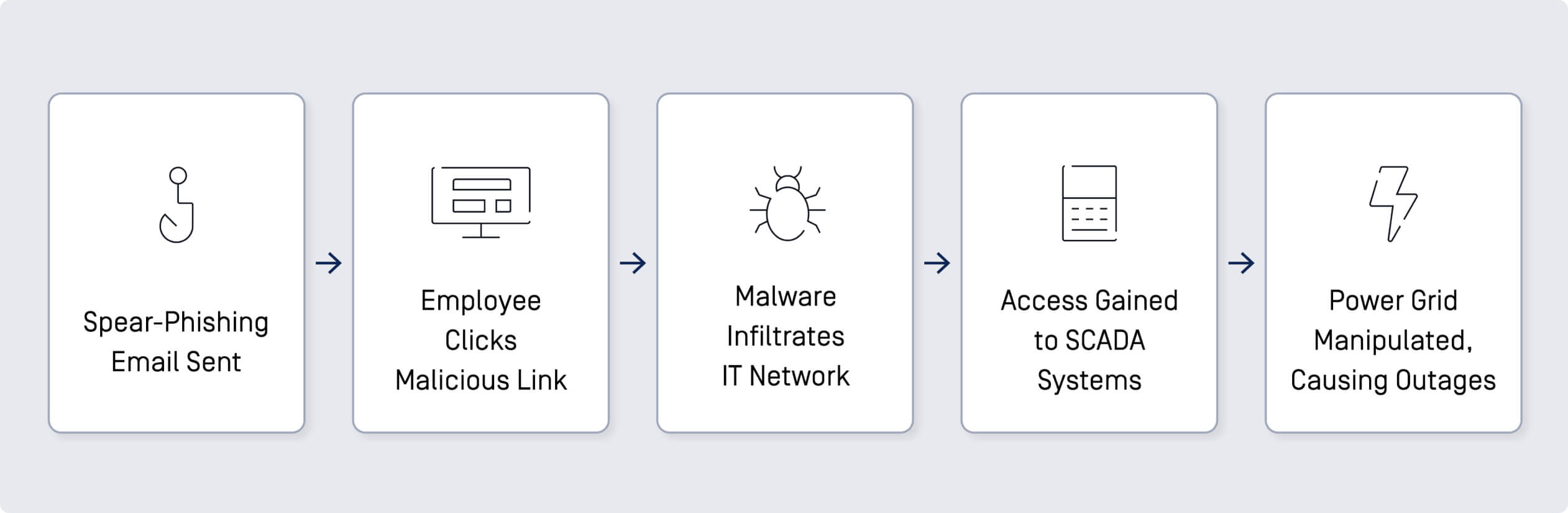
The attacks caused power outages, affecting hundreds of thousands of people, showcasing the devastating impact of cyberattacks on critical infrastructure.
TRITON Attack
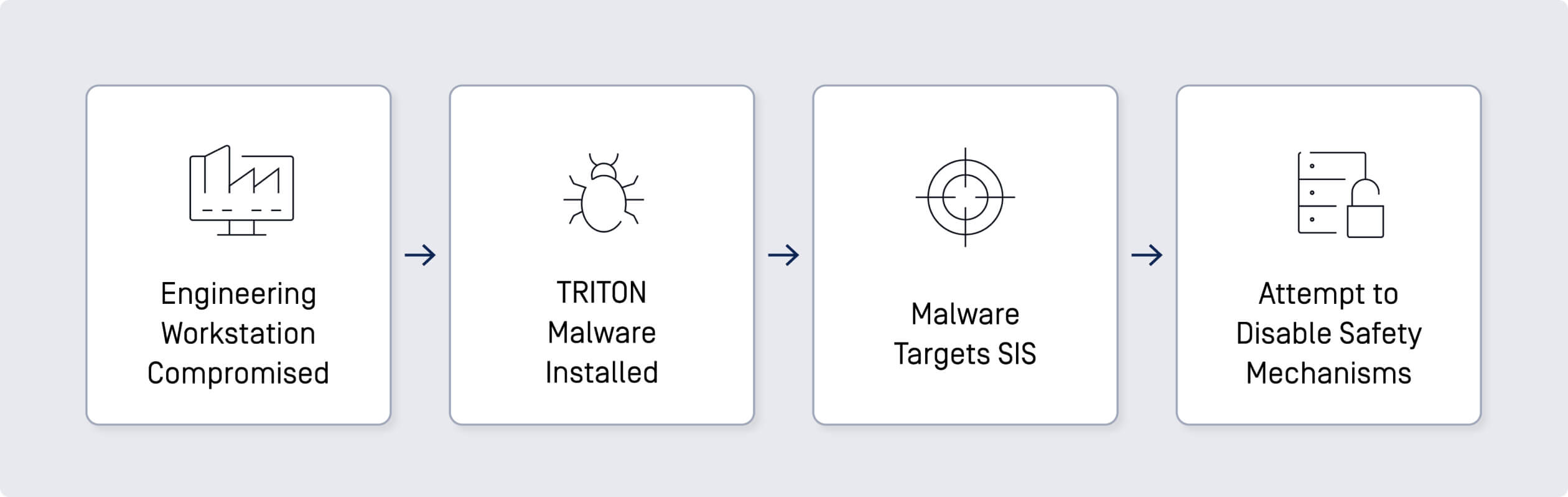
The TRITON malware, also known as TRISIS, targeted the SIS (safety instrumented systems) of a petrochemical plant in Saudi Arabia in 2017. This malware was designed to manipulate SIS controllers, which are critical for the safe operation of industrial processes.
- Compromised Engineering Workstation: Attackers gained access to an engineering workstation connected to the SIS using a VPN.
- Malware Installation: The malware was installed on Triconex SIS controllers, attempting to reprogram them to shut down the plant or cause physical damage.
Colonial Pipeline Ransomware Attack
In May 2021, the Colonial Pipeline, a major fuel pipeline in the United States, was hit by a ransomware attack attributed to the DarkSide ransomware group. This attack disrupted fuel supplies across the Eastern United States.
- Compromised VPN Account: The attackers accessed the network through a compromised VPN account that was no longer in use but still active.
- Ransomware Deployment: Once inside, the ransomware encrypted data on the network, disrupting pipeline operations.
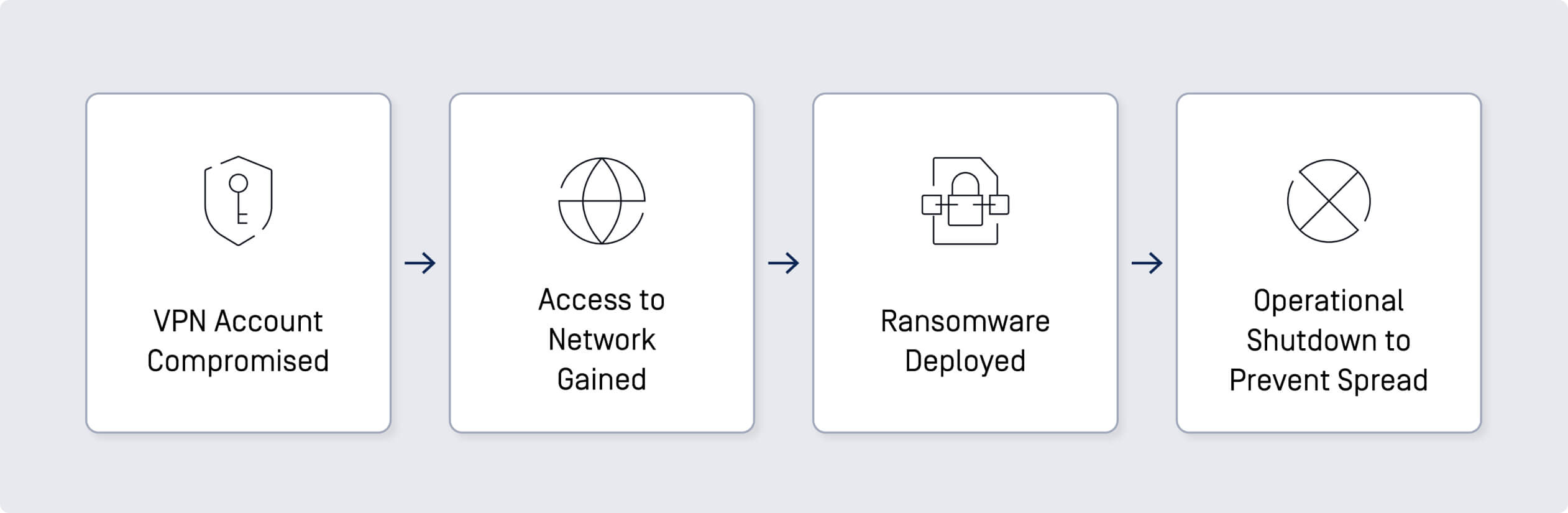
The attack led to a temporary shutdown of the pipeline, causing widespread fuel shortages, and highlighting the vulnerabilities in critical infrastructure.
German Steel Mill Attack
In 2014, a German steel mill experienced significant damage due to a cyberattack that disrupted its control systems. The attackers used spear-phishing emails to gain access to the plant's office network and then infiltrated the production network.
- Spear-Phishing Emails: Attackers sent spear-phishing emails to employees, which led to the installation of malware on the office network.
- IT Network Compromise: The attackers moved laterally from the office network to the production network.
- Control System Manipulation: Once inside the production network, the attackers gained access to control systems, causing massive damage to a blast furnace.
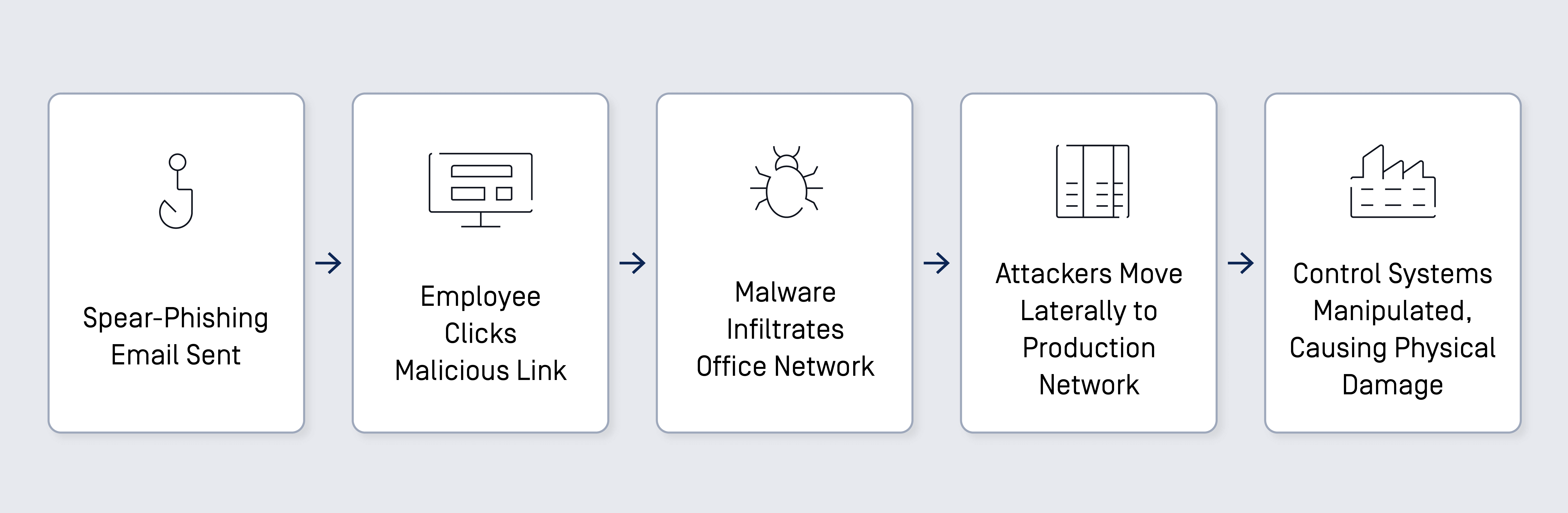
The attack caused significant physical damage to the steel mill, highlighting the devastating potential of cyberattacks on industrial control systems and the critical need for robust cybersecurity measures.
Attack Vector Overview:
Key Takeaways and Implications for Industrial Cybersecurity
The common attack vectors across these notable incidents often involve human error, such as falling for phishing emails or leaving remote access tools unsecured. Physical media, like infected USB drives and compromised VPN accounts, also play significant roles in these breaches. These points of entry highlight the critical importance of implementing a comprehensive cybersecurity platform that protects against a wide range of threats. Furthermore, the role of human factors in these attacks underscores the necessity of continuous education and training for employees to recognize and respond to potential cyber threats effectively. By combining advanced technological solutions with robust workforce development programs, organizations can enhance their resilience against the evolving landscape of cyber threats targeting ICS/OT environments.

Irfan Shakeel is a cybersecurity thought leader, entrepreneur, and trainer. He is currently working as VP of Training & Certification services at OPSWAT. Irfan has enabled a community of more than 150K students to get into cybersecurity, and previously founded a pioneer training platform called eHacking.





