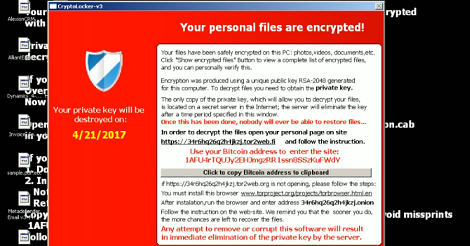
The world can't seem to catch a break — yet another large-scale ransomware attack broke out on June 27th, this time largely affecting critical infrastructure providers including oil and gas, energy, and nuclear plants, in addition to other enterprises.
At this time, Kaspersky has released data that identifies Ukraine as the main target of the ransomware, with 60% of total infections, followed by the Russian Federation (30%) and Poland (5%). Major critical infrastructure plants and corporations hit include:
- Maersk — Danish Shipping Company
- Rosneft — Russian Oil Company
- Merck — U.S. Pharmaceutical Company
- Oschadbank — Ukraine State-Owned Bank
Anders Rosendahl, a spokesman for Maersk, commented (via CBS), "We are talking about a cyberattack. It has affected all branches of our business, at home and abroad."
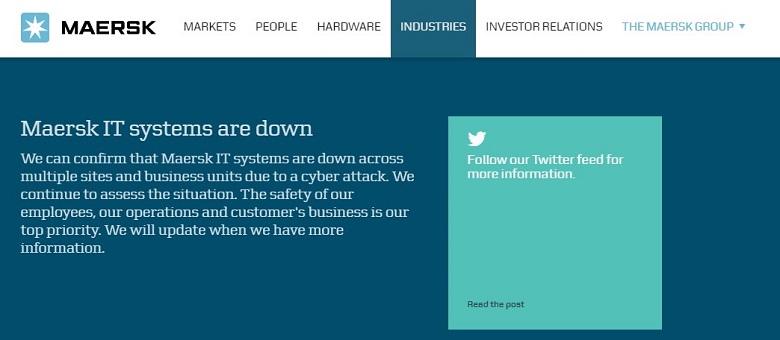
Message from Maersk's website
Per The Verge, initially a researcher from Kaspersky had reported that the malware was a variant of the Petya ransomware. Later, Kaspersky reported that it's actually a unique ransomware infection, calling it "NotPetya."
While victims of any large-scale cyber-attack must deal with repercussions such as financial loss, compliance fines, and stolen customer information, the critical infrastructure industry arguably has the most to lose. As a precaution, the organization monitoring radiation levels at the Chernobyl Nuclear Power Plant had to shut down all Windows computers, causing them to switch to manual monitoring of the zone's industrial sites.
How does it spread?
Government officials in Ukraine have released pictures of their infected computers and claim that the whole network was taken down as a result of the infection.
Similar to WannaCry, this ransomware uses a Microsoft Windows Vulnerability called EternalBlue to spread (according to multiple reports). Interestingly, Windows released a patch for this vulnerability on March 14th of this year, which means that any system that patched the vulnerability should not be exposed to this attack.
This raises a bigger issue — why are so many systems still left unpatched?
How OPSWAT Can Help: The Importance of Multi-scanning
Whether this new malware is indeed related to Petya ransomware or is a new strain of malware altogether, organizations need the ability to detect it and block it.
Because MetaDefender Core multi-scanning technology leverages multiple anti-malware engines to detect malware, detection rates are higher, and it's more likely to catch even unknown threats.
From MetaDefender Core 4 on up, the engines in our engine packages do detect the malware from these recent attacks. MetaDefender Core engine packages contain up to 35+ anti-malware engines, and MetaDefender Cloud uses over 40.
Contact us today to learn more about multi-scanning.

