Deep CDR™
File Regeneration that Protects from Evasive Malware and Zero-Day Exploits
Traditional antivirus solutions miss unknown threats. Deep CDR eliminates them entirely. Each file is disarmed and regenerated, ensuring only safe, clean and useable content reaches your systems.
Processes Files in Milliseconds
Supports Embedded Objects
Sanitizes 200+
File Types
200+ File Conversion Options
Recursively Scans Archives
Tailored Security Policies
Here’s Why Deep CDR Matters
Insufficient Protection
AI and heuristic-based anti-malware solutions don’t disarm all file-based threats.
Undetected Threats
Zero-day threats, targeted attacks, and evasive malware may go undetected by antivirus engines.
Evasive Malware Tactics
Evasive malware avoids detection by using obfuscation techniques like steganography to deliver compressed, archived, or encrypted payloads.
Macro and Script Limitations
Outright bans on macros in Office docs and JavaScript in PDFs are difficult to enforce and may limit vital functionality.
Incomplete Archive Scanning
Traditional CDR solutions are incapable of recursively scanning archives and zip files.
How It Works
By focusing on prevention rather than just detection, Deep CDR enhances anti-malware defenses, protecting organizations from file-based attacks, including targeted threats. It neutralizes potentially harmful objects in files traversing network traffic, email, uploads, downloads, and portable media before they reach your network.
Core Benefits
Comprehensive
Protection from out-of-policy or potentially malicious code, with support for a wide range of objects beyond just macros.
Powerful
Enough to defeat obfuscation techniques, including steganography, by removing potential threats.
Reliable
Threat removal for complex files that maintains file usability
Flexible
Configuration enables allowlisting, removing, or examining active content such as macros or URLs.
In-Depth
Reporting of sanitized components and forensic data for malware analysis.
Efficient
Enough to disarm and regenerate new, usable files in milliseconds.
See It in Action
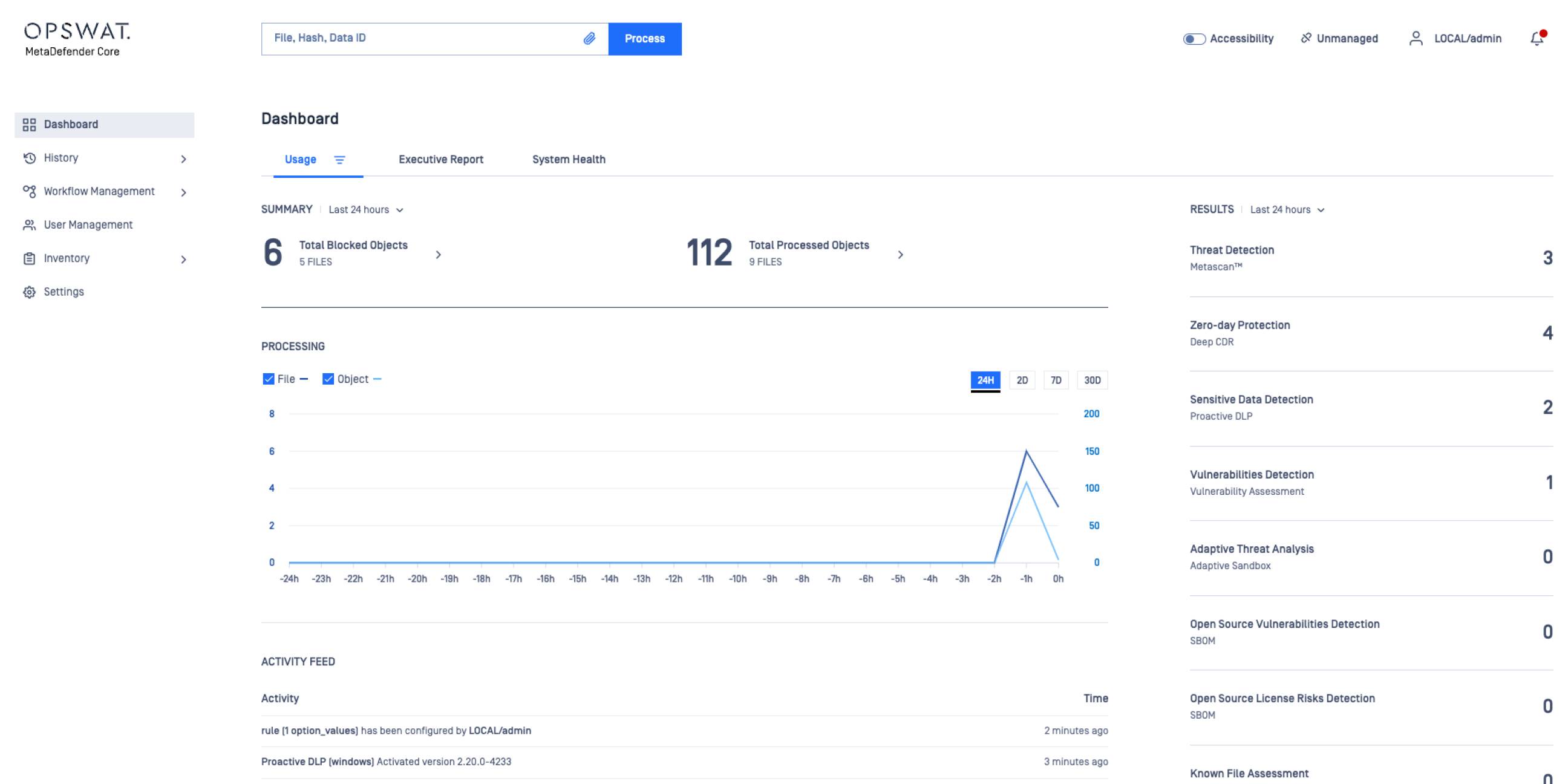
Effectively eliminate zero-day targeted attacks by relying on prevention rather than detection
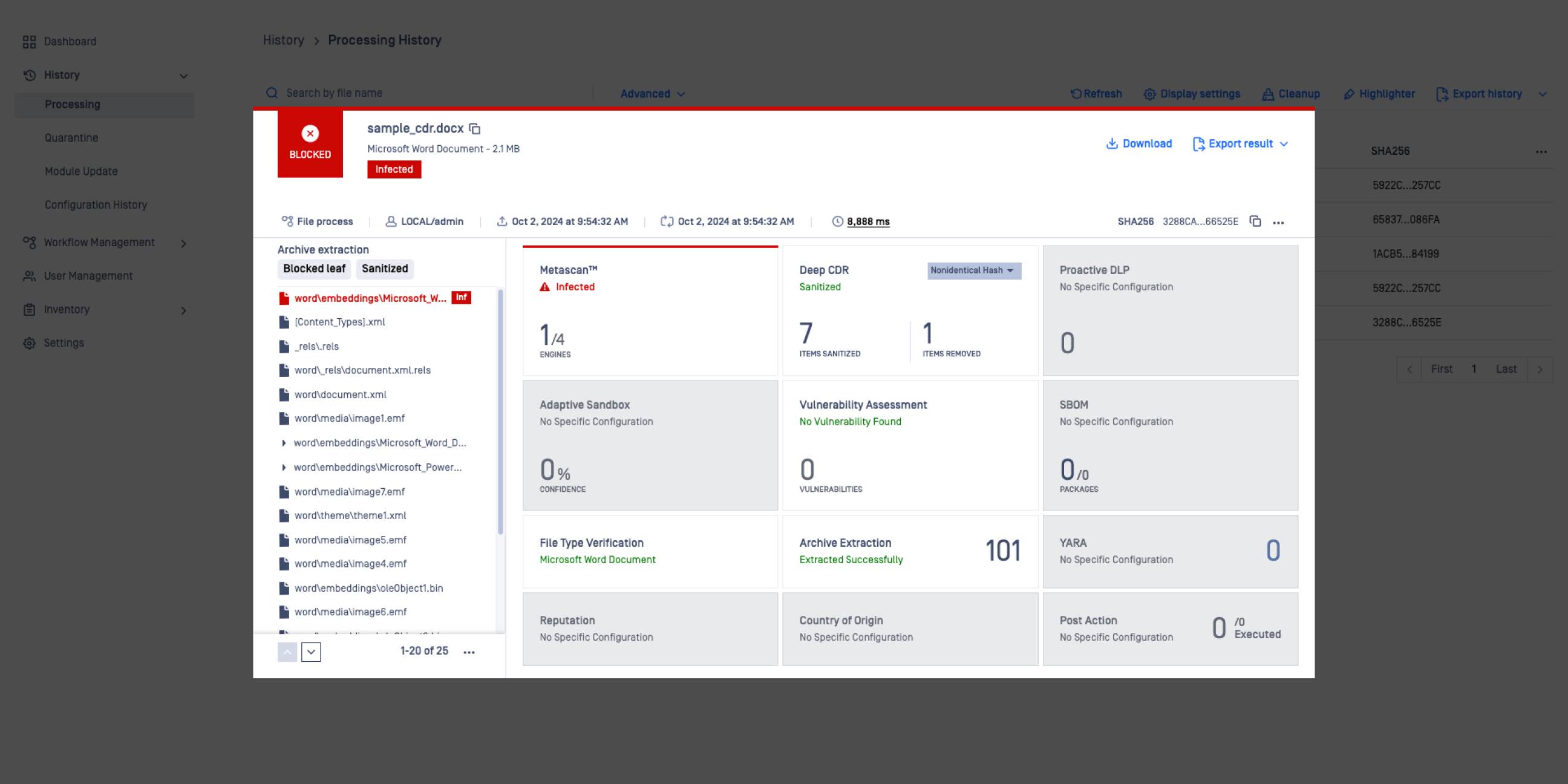
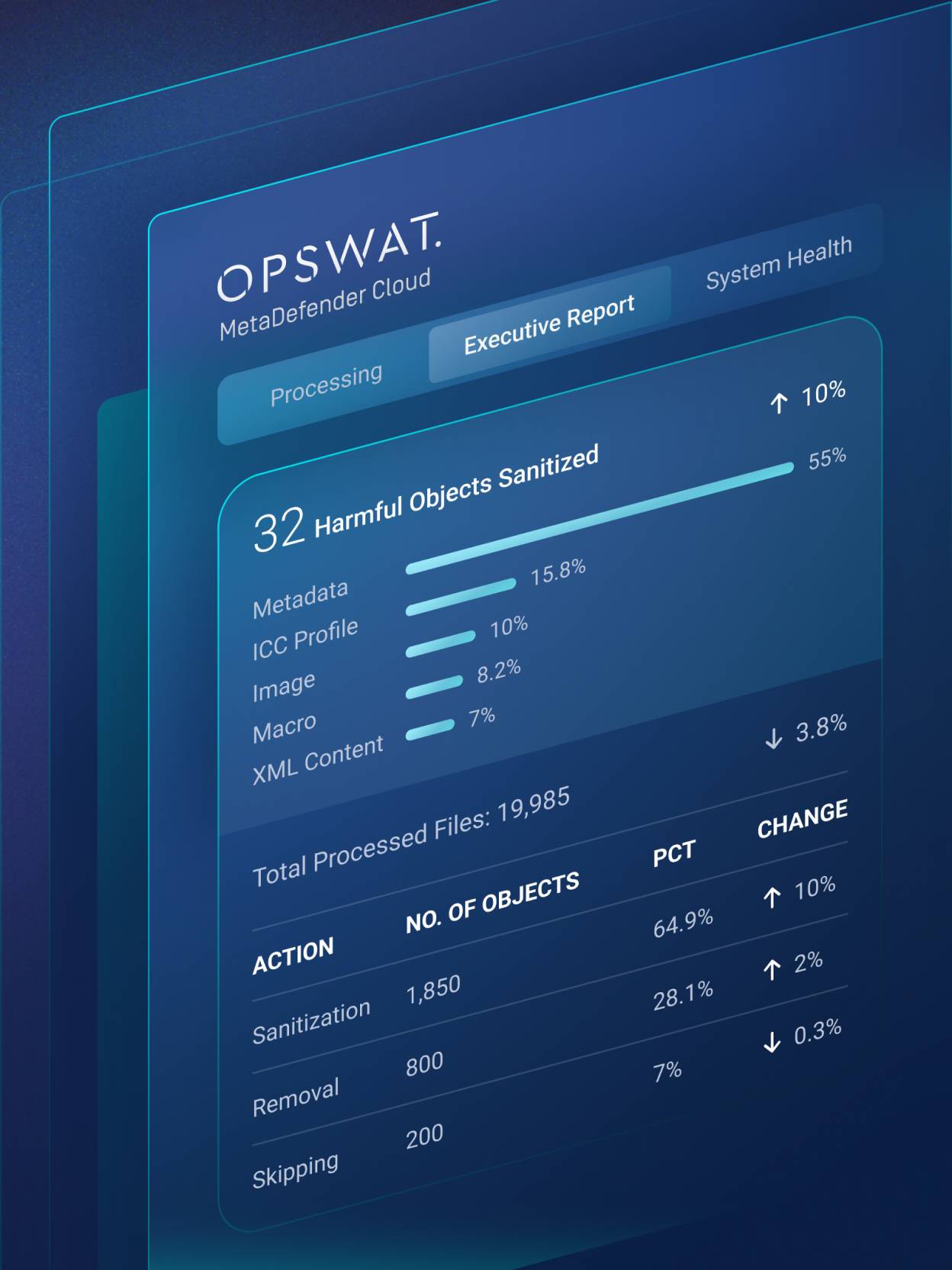
Real-time data enhances visibility and control.
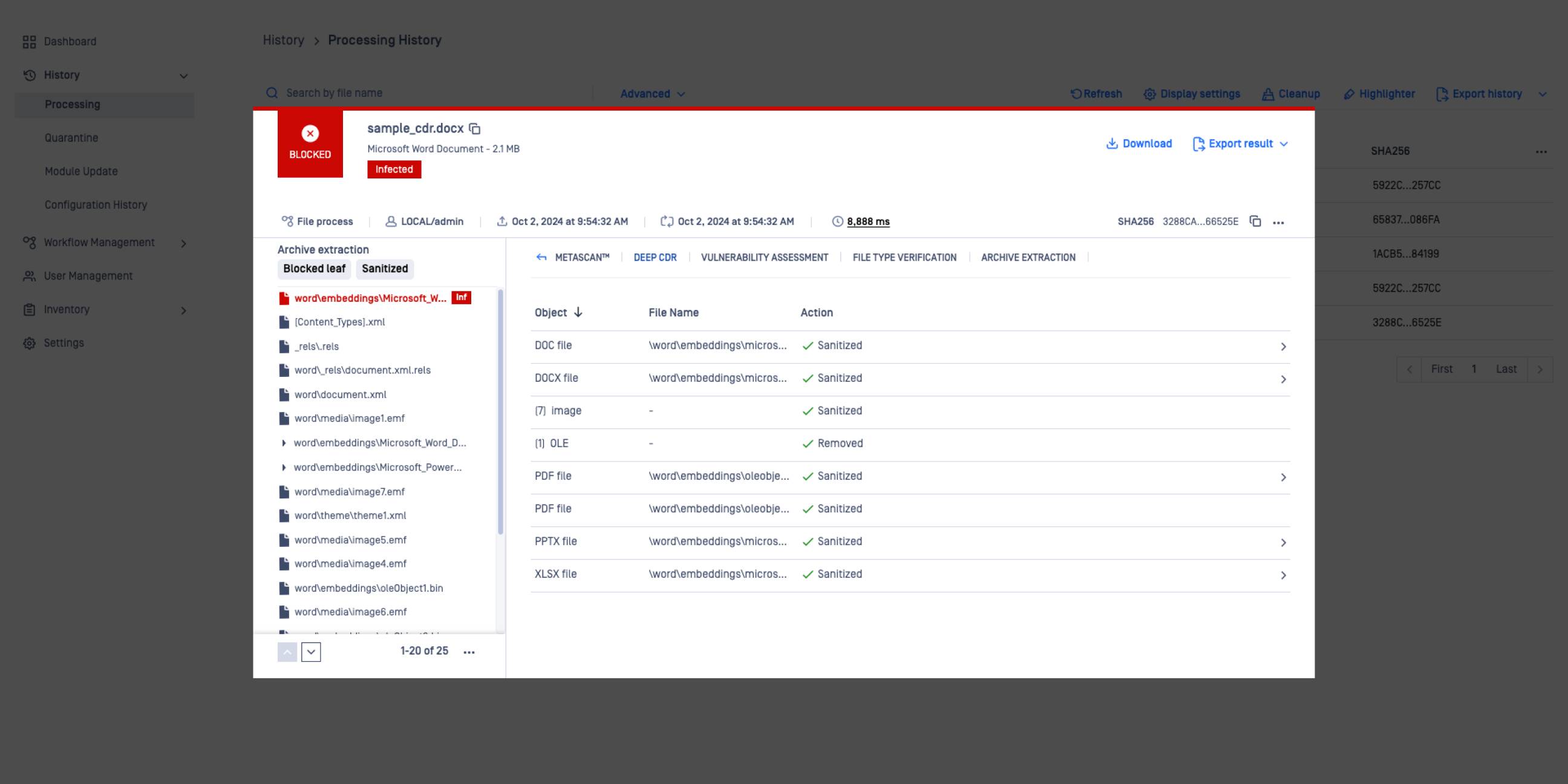
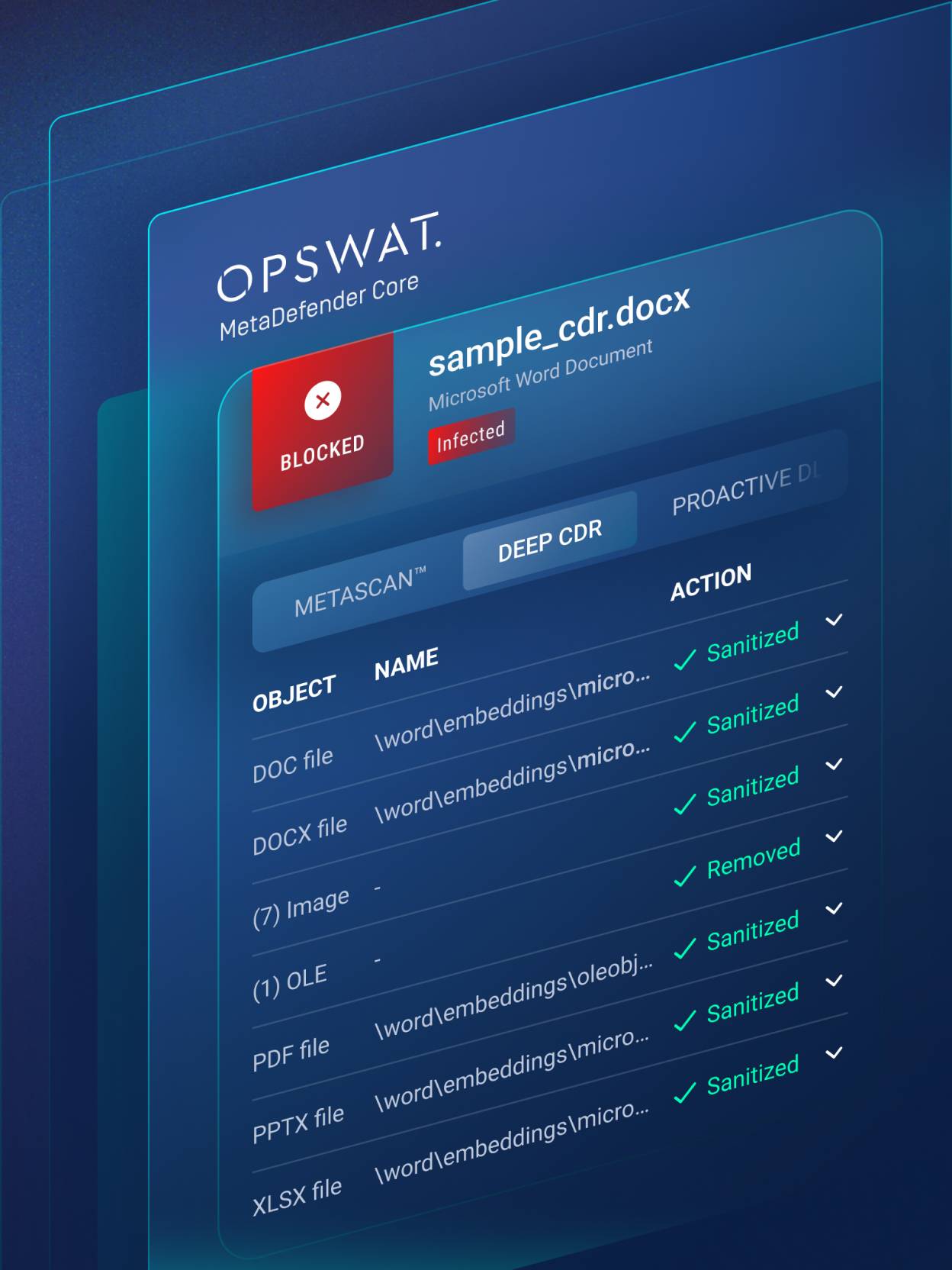
Object listing enhances visibility into all processed objects within a sanitized file.
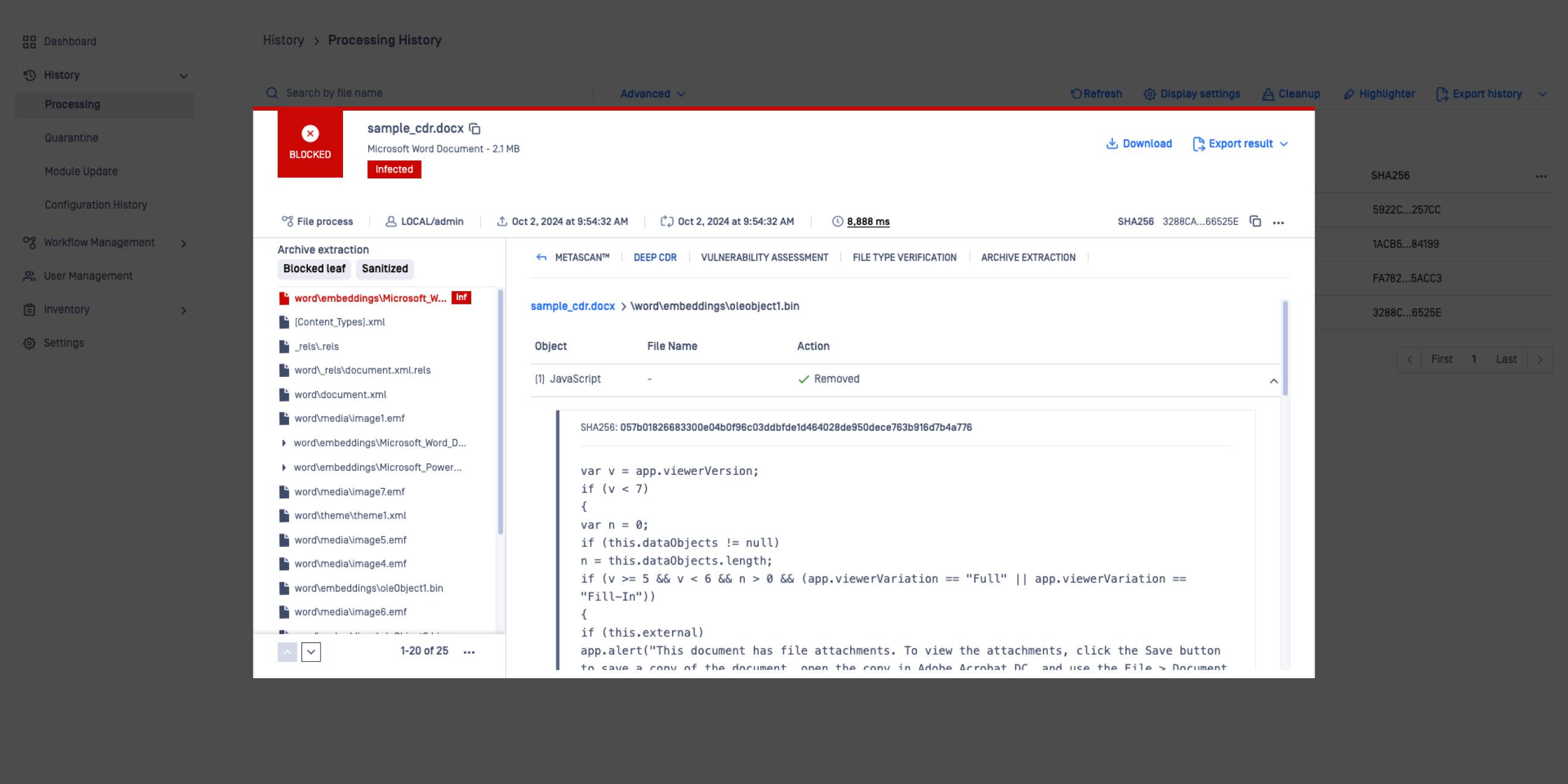
Customize how potentially harmful objects are handled to align with your specific goals.
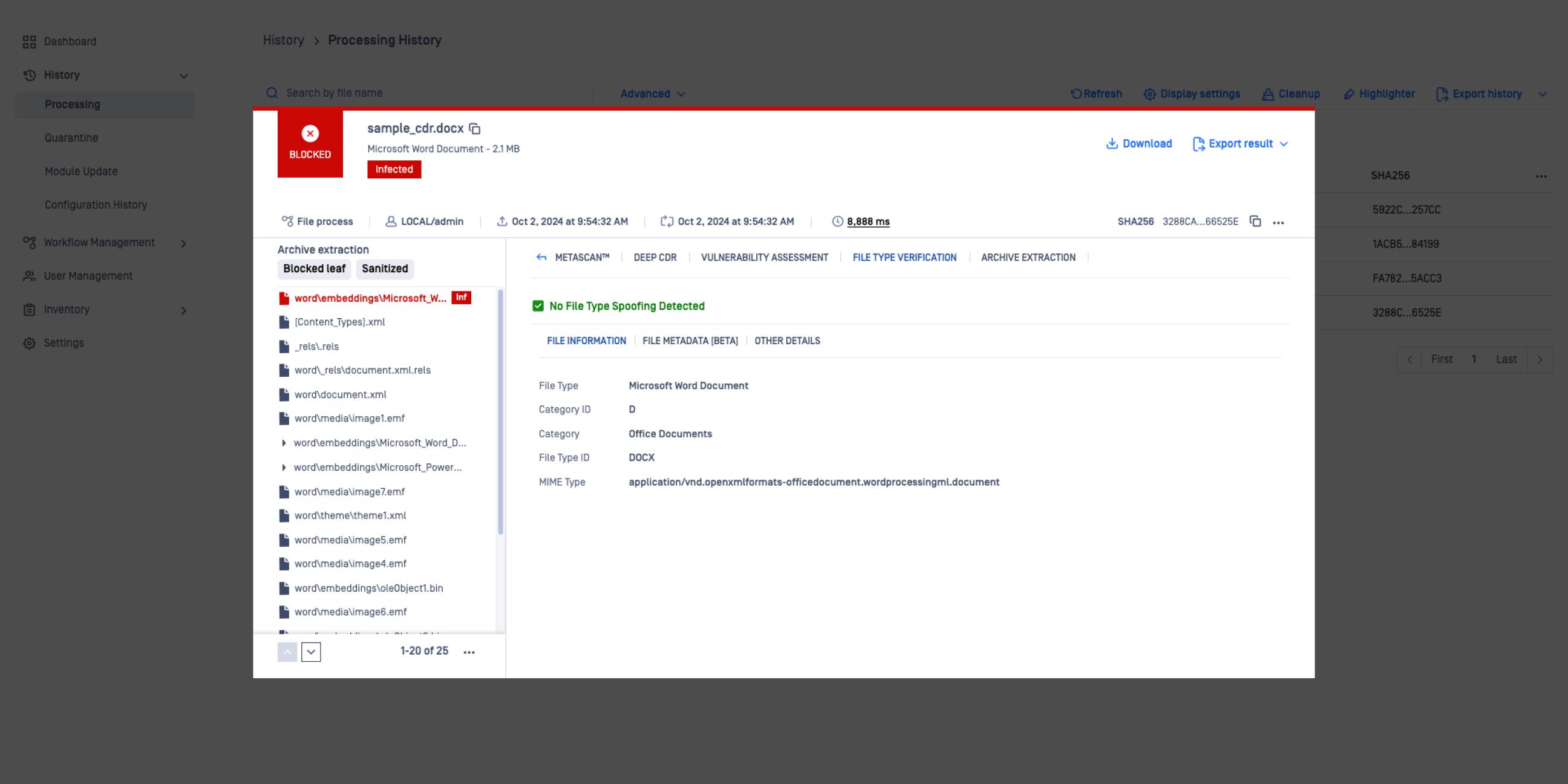
Object listing enhances visibility into all processed objects within a sanitized file.
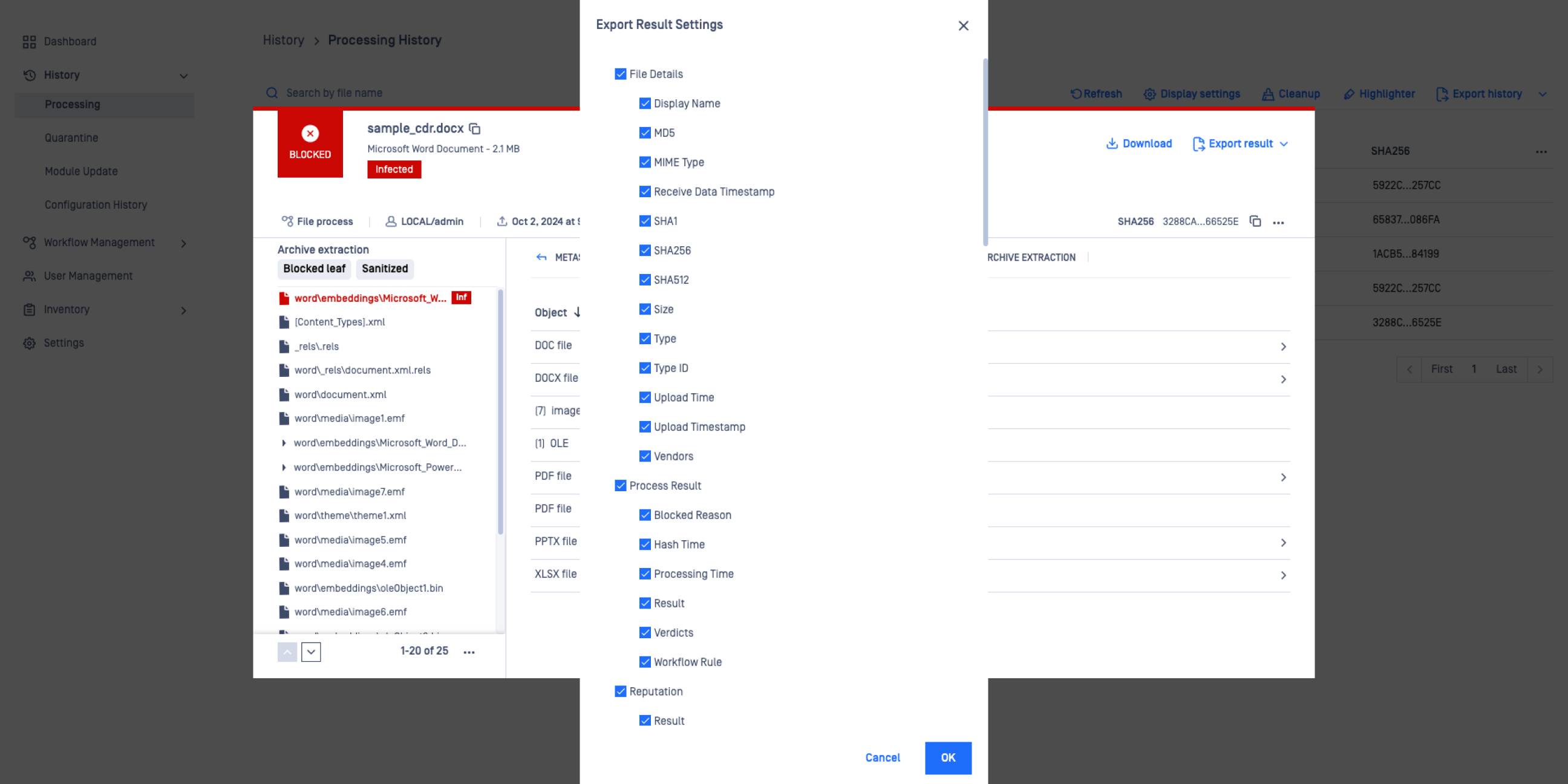
Deep CDR technology returns detailed forensic info for the disarmed files.
Explore 200+ Supported File Types
Explore the file types below and click through to see performance data, supported versions and review sample files.
Deployment Options
Deep CDR Reports & Diagnostics
OPSWAT Deep CDR: First and Only to Achieve 100% Total Accuracy Rating from SE Labs
100% Rating in SecureIQ Lab’s Content Disarm & Reconstruction Test
Deep CDR Performance Testing
See detailed processing speeds of some the most popular file types in different operating environments.
Deep Diagnostic Data
Deep CDR delivers forensic insights on disarmed files, providing SOC analysts with both summary data and detailed JSON responses for thorough analysis.
Customers Talk about Deep CDR