Image-based attack techniques like steganography and polyglot are not new to security teams. Despite existing solutions to mitigate risks, threat actors are constantly devising new methods to hide malware within trusted image formats. One advanced image-based attack technique is known as cross-site scripting (XSS) polyglot payloads. These payloads exploit polyglot images, which contain both a valid image and concealed code or scripts. The payloads specifically target web browser vulnerabilities to perform XSS attacks that steal data or install malware, evading detection such as Content Security Policy (CSP) restrictions.
To stay ahead of these deceptive new threats, organizations require zero-trust security solutions that go beyond detecting known risks and take preventative measures to ensure any future attacks are thwarted—whether the malware is known or novel. OPSWAT Deep Content Disarm and Reconstruction (CDR) prevents stealthy image-based attacks by sanitizing image files, removing any potentially malicious code and reconstructing them so they can be safely used in any digital environment.
Risk Level of Image-based Malware Attack Vectors
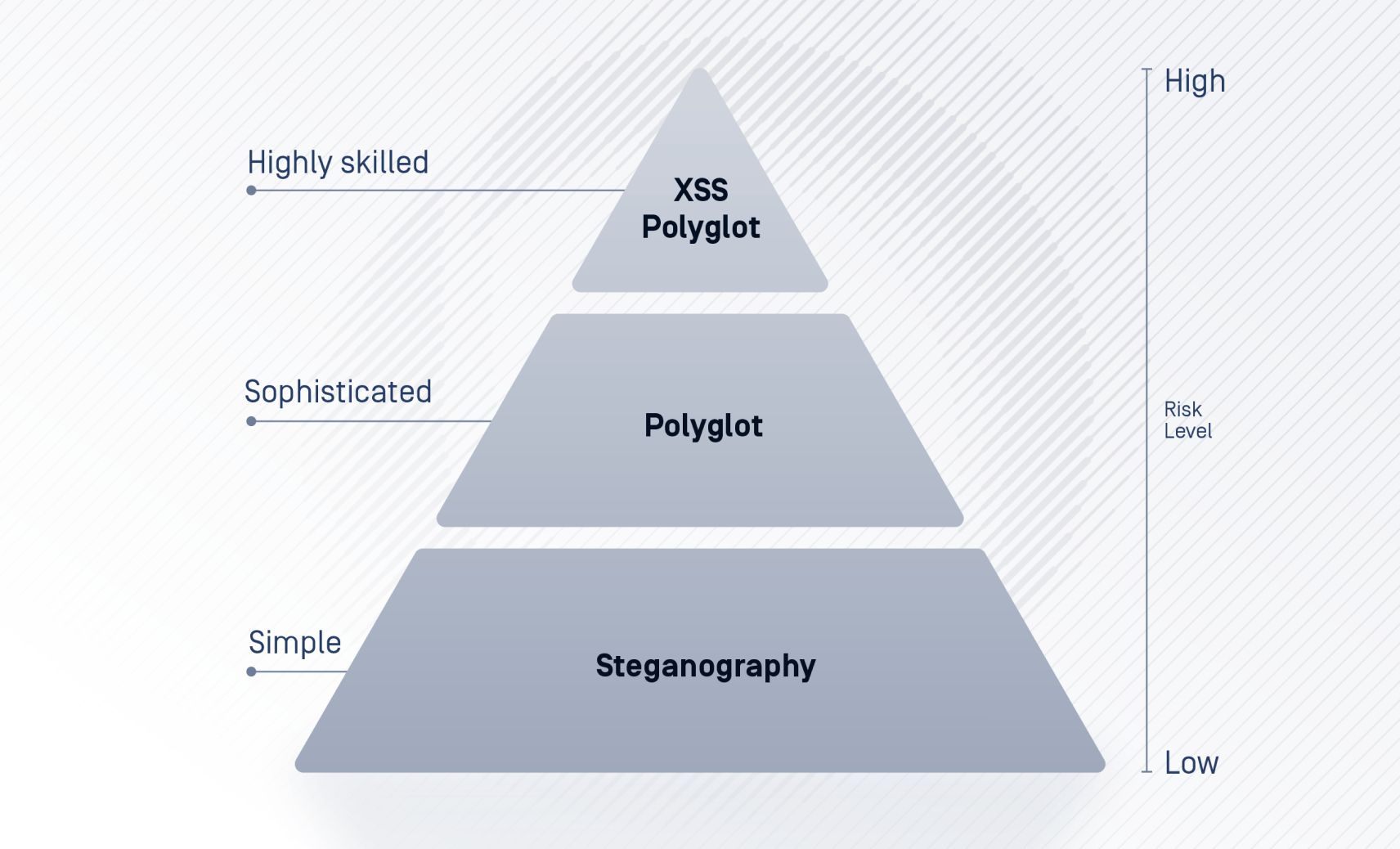
Steganography
Image steganography was first observed in a cyberattack in 2011 with Duqu malware. In this campaign, information was encrypted and concealed within a basic JPEG file, aiming to extract data from the targeted system. Steganography is one way malicious actors fly under the radar. It embeds malware payloads within image files by modifying pixel data, and stays completely undetected until decoded.
Steganography only works, however, if there is a decoding tool available, making it the least sophisticated method of image-based malware delivery.
Polyglot
Seen as more sophisticated than steganography, Polyglot requires a combination of two different file types. For example, PHAR + JPEG (PHP archives and JPEG files), GIFRAR (GIF and RAR files), JS+ JPEG (JavaScript and JPEG files), etc. Polyglot images function perfectly well as normal image files.
However, they can also be exploited to smuggle in concealed malicious scripts or data payloads. These payloads bypass common defenses and execute their embedded attacks when opened in targeted environments like web browsers. The danger of polyglot is that it doesn’t require a script to extract malicious code; the browser function will automatically run it.
XSS Polyglot Payloads
XSS polyglot payloads represent an elevated risk by combining polyglot techniques with XSS attacks. The payloads use polyglot images to conceal scripts that exploit browser vulnerabilities and bypass key protections like CSPs. This enables much more dangerous scripts to be injected into trusted sites and apps.
Utilizing polyglot images can circumvent certain website filters that block external content hosting. To achieve this, the HTML structure preceding the injection must be legitimate, functioning as a valid variable. The process relies on XSS to interpret the injected content as JavaScript, which can bypass restrictions on image uploading, as well as the cross-origin policy and whitelist restrictions that follow. The JavaScript code is then hosted on the specific site in question, allowing it to execute within its intended context.
Advanced Threat Prevention with Deep CDR
Deep CDR technology, which achieved a 100% protection rating in the SE Lab Report, is a market leader in preventing both known and unknown file-based threats, safeguarding against malware and zero-day attacks. Offering superior features such as recursive sanitization and precise file reconstruction, Deep CDR delivers safe and usable files. Additionally, it supports hundreds of file types, including PDFs, archives, and formats compatible with archives.
Back in 2018, OPSWAT covered two blog posts explaining the risk of steganography and polyglots and using Deep CDR to prevent these attack techniques. In this guide, we will focus more on the XSS Polyglot Payloads.
Exploiting XSS using Polyglot JPEG and JavaScript to bypass CSPs
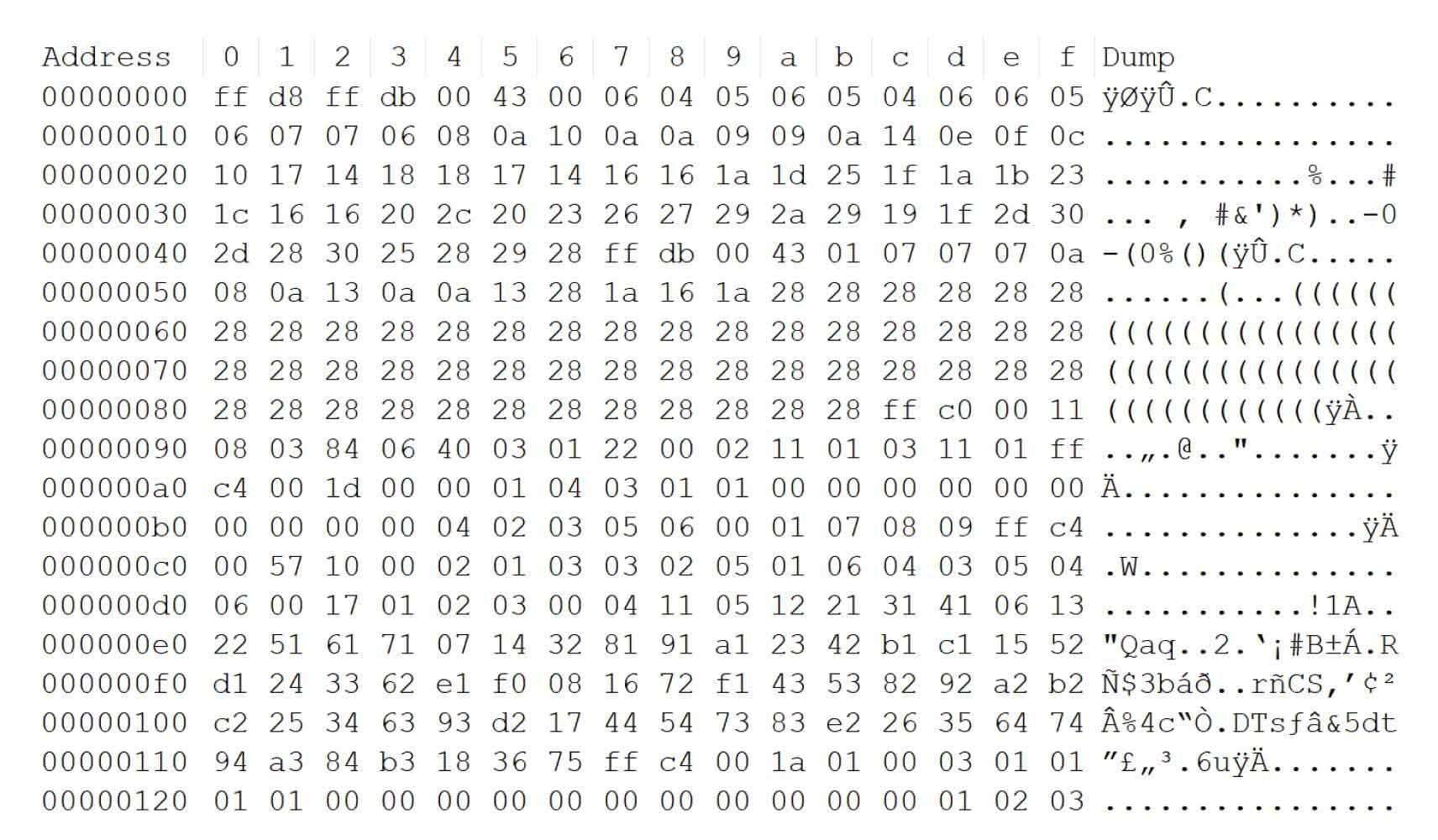
A XSS polyglot payload can execute in multiple contexts, including HTML, script strings, JavaScript, and URLs.
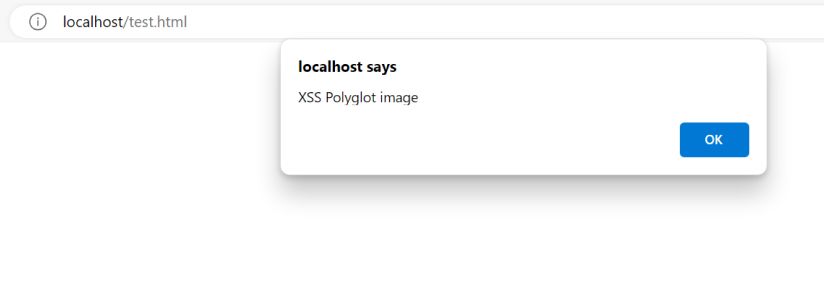
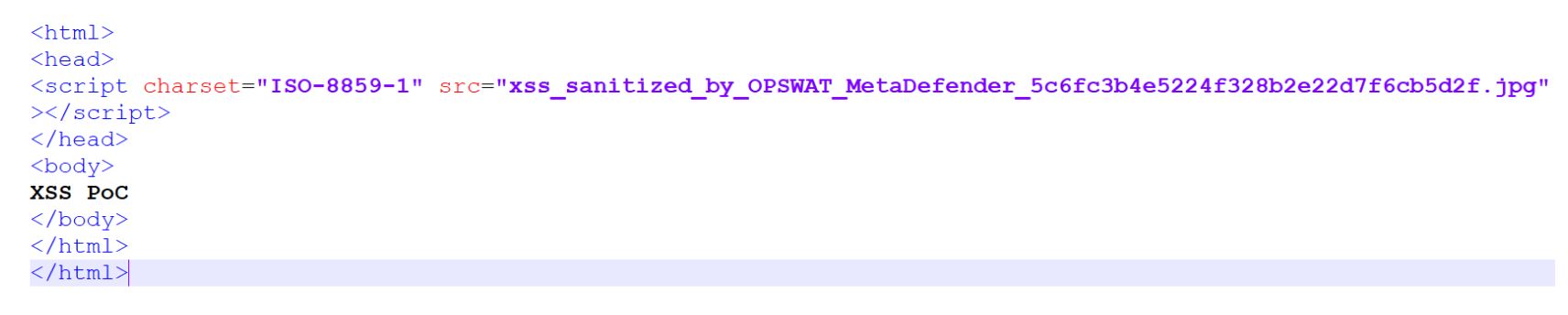
The threat actor will then change src attribute value in index.html to the output file name, run HTTP server and open http://localhost:8000 in browser. See the samples below.
Preventing XSS Polyglot step-by-step with Deep CDR
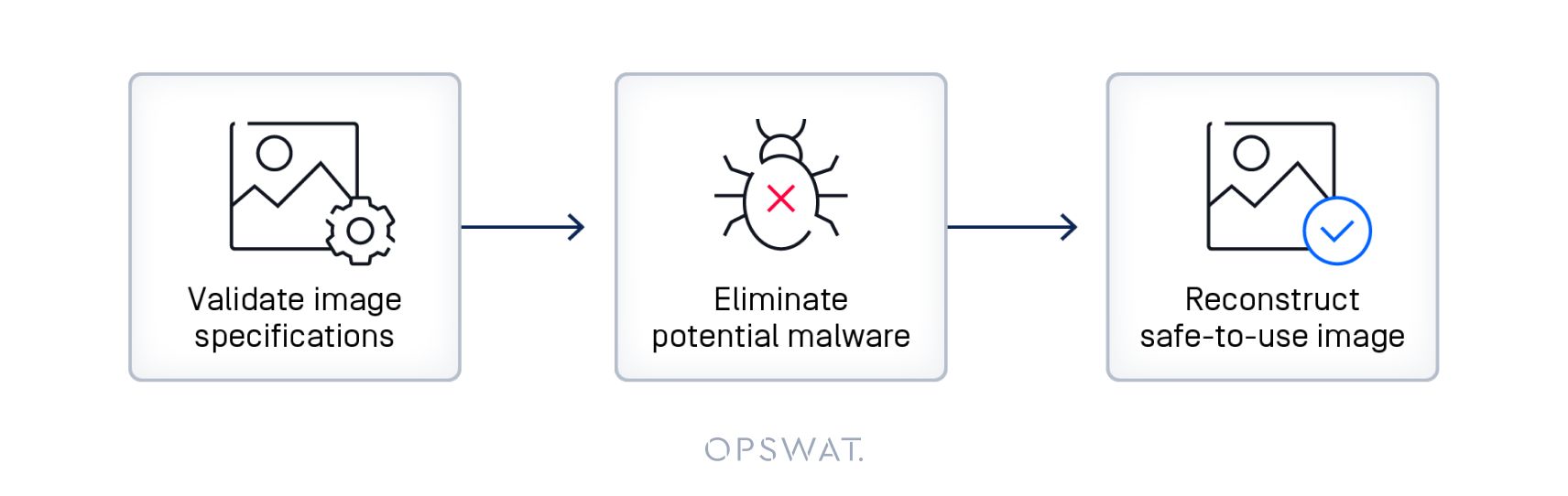
- Analyzes image structure to validate against known trusted image specifications. Deep CDR optimizes bitmap data, removes unused data, and then processes metadata.
- Neutralizes potential malware through payload extraction to safely remove hidden scripts and data.
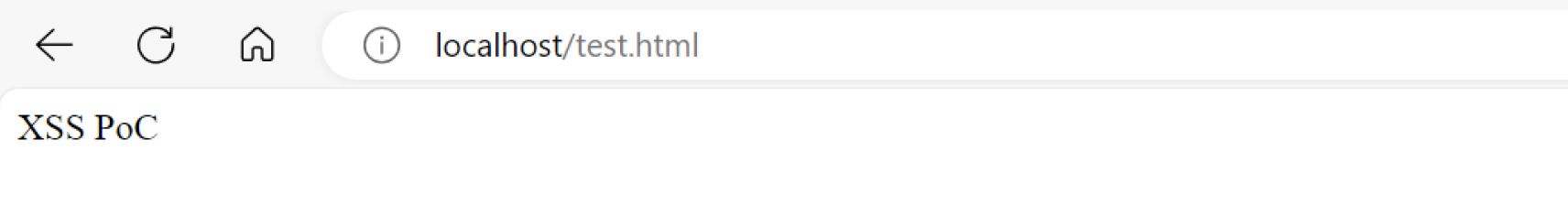
- Sanitizes images by disarming and removing threat vectors while keeping the image safe-to-use. Users will see only the image as intended without any extraneous or unknown potentially malicious code.
Defense-in-depth with OPSWAT MetaDefender Platform
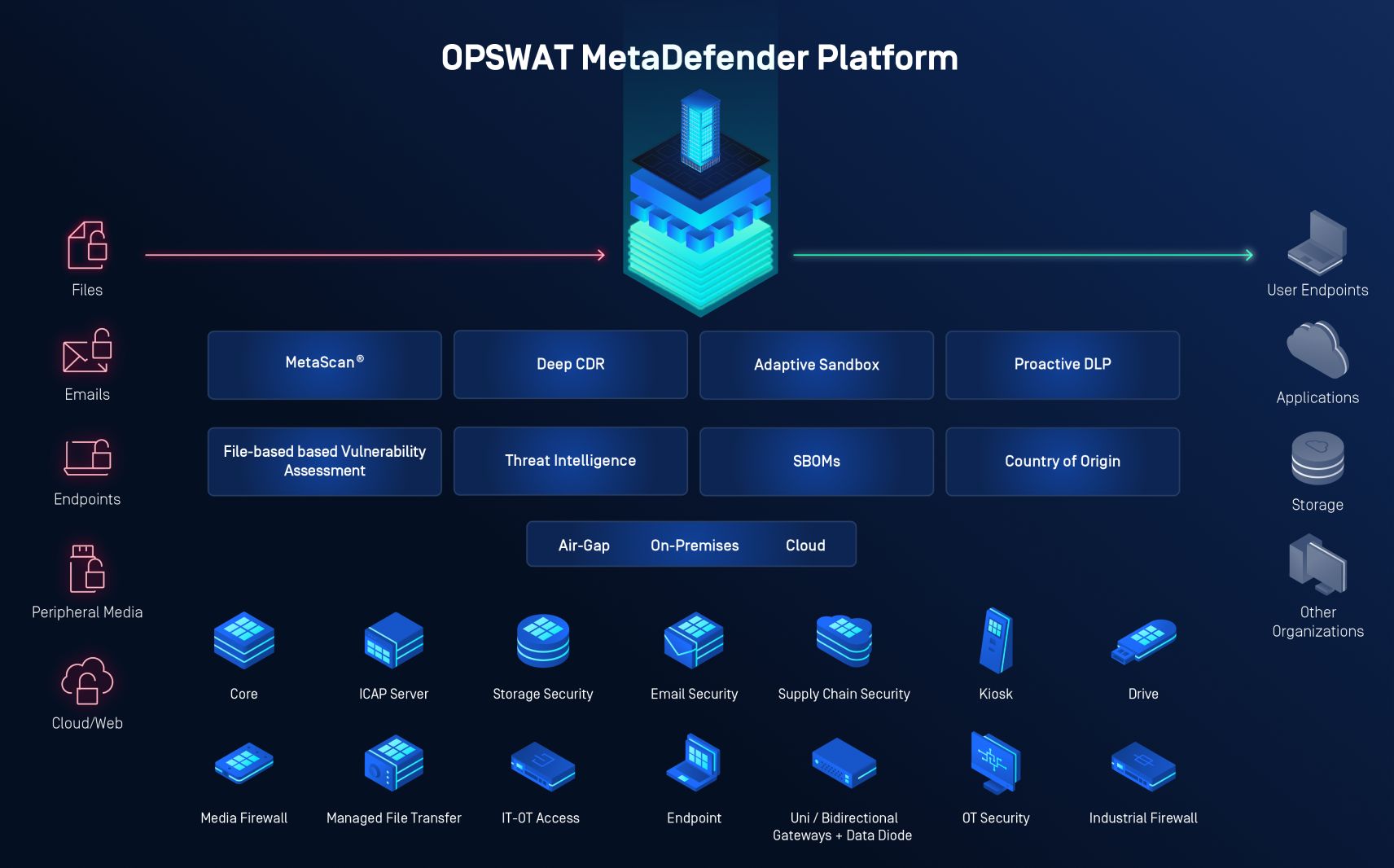
Going beyond images, the OPSWAT MetaDefender platform provides multilayered protection against file-based threats. OPSWAT MetaDefender combats the constant evolution of new attack types by:
- Blocking hundreds of known threats out of the box.
- Applying behavioral analysis to detect zero-day threats.
- Ensuring that every suspicious file is safely sanitized or blocked.
This ecosystem approach secures your most sensitive data and systems even from unconventional attack vectors.
Final Thoughts
As adversaries' techniques grow more advanced, security technology must evolve even faster. OPSWAT boasts over 20 years of deep security expertise, built into products like MetaDefender platform and Deep CDR technology. This experience brings together continuously updated threat intelligence, advanced detection algorithms, and configurable layered defenses to stop attacks before they compromise your organization.
To learn more about neutralizing covert image-based threats and strengthening enterprise security defenses with OPSWAT MetaDefender, contact our team today. When it comes to outsmarting tomorrow's cyberattacks, it pays to install the right security defenses today.