
For cyber criminals, image malware is the ideal way to launch a surprise attack. The vast majority of users do not expect a simple image file to be remotely risky. This makes attacks like "Stegosploit" particularly dangerous to both enterprises and private users.
Data sanitization (CDR) blocks these kinds of attacks, as we explain below.
What is Stegosploit?
Stegosploit is a type of malware that is inserted into certain extra-data sections of an image. The malware is JavaScript code that can be loaded and executed by a browser. The script can automatically download malicious payloads, upload data, and execute malicious code.
The remarkable thing is that the malware is inserted into an image and the image still looks harmless. For that reason, it is difficult to detect and block this kind of attack.
Image-borne malware has been a risk for some time now, but the term "Stegosploit" was coined by cyber security researcher Saumil Shah in a presentation at a 2015 cyber security conference. Shah described a method by which JavaScript could be concealed in an image in such a way that a browser would execute the code when loading the image.
The name "Stegosploit" comes from the word "steganography," which refers to a technique of concealing information by hiding it in an image, in video, or in other text.
Potentially Malicious BMP, GIF, JPG, and PNG Files
The following image formats can carry Stegosploit: BMP, GIF, JPG, and PNG. (SVG files can also be used as vehicles for malware.)
- For BMP and GIF files, malware is appended at the end of the image binary data. The image is then referred to by the img tag in an HTML file and used as a script file in the script tag. When opened, the HTML file will show the image and run the script.
- For JPG files, malware is inserted into the APP0 segment of the image.
- For PNG files, malware is inserted into tEXt chunks of the image.
Using OPSWAT Data Sanitization (CDR) to Remove Malware
The OPSWAT team created Stegosploit samples for each of these file types, and we used them to test whether our data sanitization (CDR) technology would protect users from Stegosploit.
The sample images we created contained a script which, when run, resulted in this harmless popup appearing. (An attacker would instead trigger a more malicious action.) The below screenshot is from a script concealed within a BMP file.
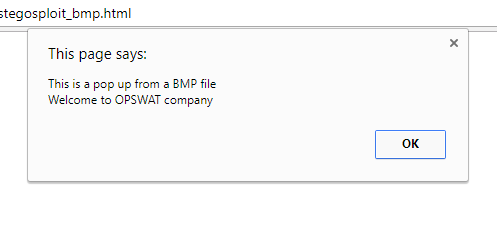
A BMP file conceals JavaScript
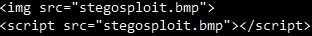
Image file used as script
We then sanitized the images. Any embedded data, including scripts, was removed as invalid by the data sanitization process.
We could still open the image file like normal, but the script had been removed. Although in this case the script was harmless and only triggered a popup, an attacker could conceal much more dangerous scripts within the images.
We tested data sanitization with the following file types:
- BMP
- GIF
- JPG
- PNG
Copy of one of the sample images after sanitization — image still looks normal
Conclusion
After testing our data sanitization on images with malware, we concluded that data sanitization (CDR) does indeed provide protection against Stegosploit attacks by stripping away the unnecessary and malicious scripts.
Additionally, data sanitization works with multiple kinds of image files. Learn more about data sanitization.

