At OPSWAT, we enjoy solving complex problems. Enabling our partners to build tools that protect over 100 million endpoints is a challenge we take seriously.
Complying with internal and regulatory frameworks such as HIPAA, GDPR, and PCI is costly and burdensome. Monitoring and maintaining compliance on endpoints in heterogeneous environments require powerful tools.
We provide integrated Endpoint Compliance technology as part of the OESIS Framework Framework, a cross-platform, modular software development kit (SDK) that enables technology vendors to build advanced endpoint security products for their clients.
For over eighteen years, the OESIS Framework Device Compliance Module has helped industry leaders such as Cisco, Palo Alto Networks, HP Aruba, and IBM deliver more secure remote access, compliance, network access control, device posture check, and more to their end customers.
Let's take a closer look at why the Device Compliance Module is a popular and effective solution.
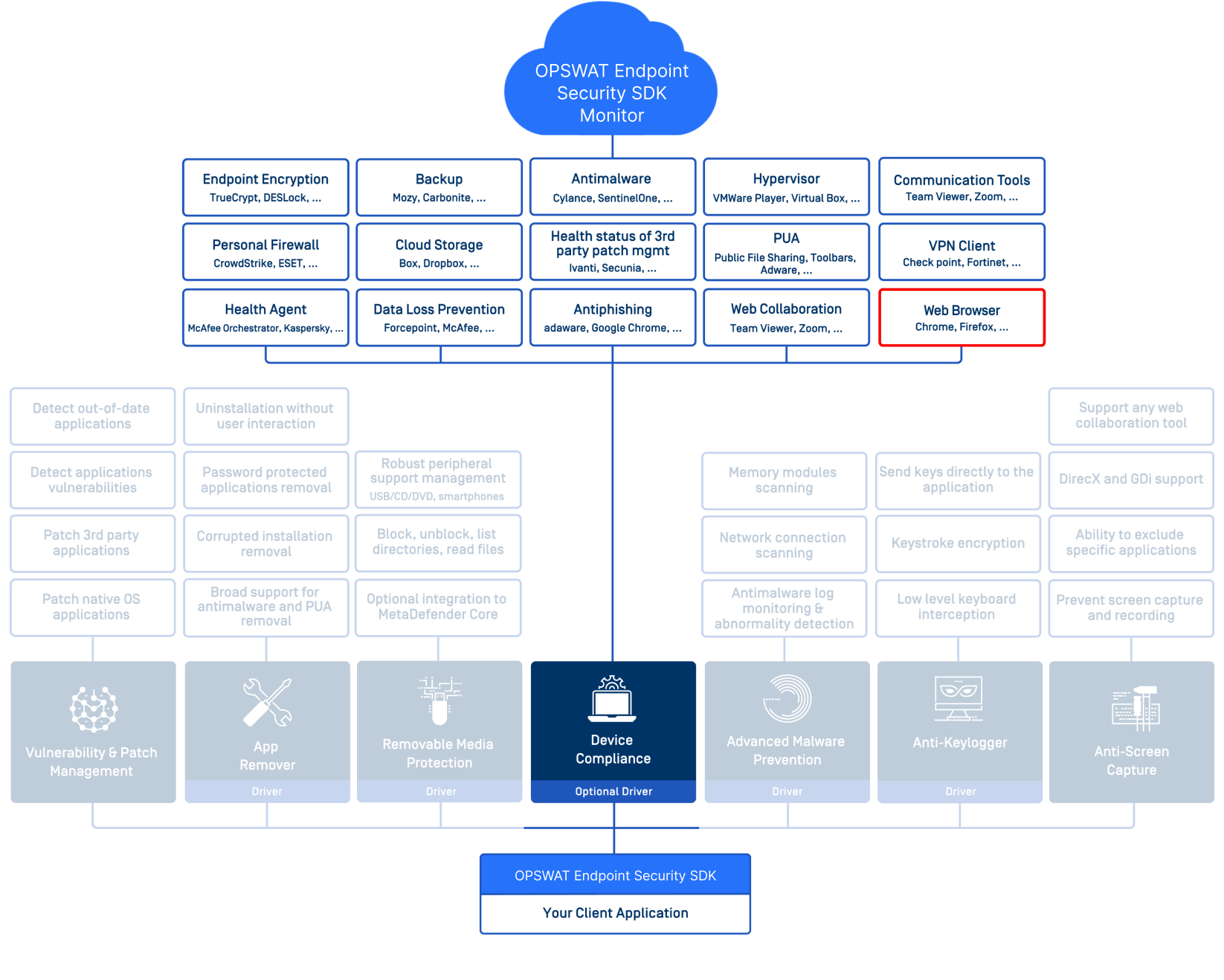

Device Compliance Module Overview
The Device Compliance Module empowers software engineers to add device posture checking (compliance) to their products, often as part of VPN and ZTNA (Zero Trust Network Access) solutions. We've added a rich set of features that work with various industries and meet an ever-growing list of compliance requirements.
Our Endpoint Compliance technology supports over 5,000 applications, grouped into 16 categories, like anti-malware, personal firewall, disk encryption, patch management, and browsers. For each detected product, it reports on vendor, categories, product version, running state, authenticity, installation directories, as well as category-specific information. Over 30 different remediation actions are also available to help enforce compliance policies.
Risk Score Calculation
Our Risk Score Calculation feature quickly determines endpoint compliance. A risk score combines the security and vulnerability status on an endpoint. With the OESIS Framework, you can easily calculate a score based on multiple categories, including Antimalware, Firewall, Encryption, and Vulnerability Status.
By using endpoint risk scores for all devices in an organization, you can quickly determine security health and, by extension, if an endpoint is compliant. For example, you can set a policy that only endpoints with an aggregate risk score of 8 or more (out of a maximum of 10) can access secured resources.
We’ve put together a short video to show how easy it is to calculate a simple risk score on the endpoint using the OESIS Framework below.
Buy vs. Build: The High Penalty of Failure
Building your own endpoint security solution makes sense in an ideal world of unlimited resources, deadlines unfettered by delays, and teams capable of maintaining software well into the future.
But for most organizations, long-term maintenance, technical debt, shifting requirements, and priorities make a build-it-yourself approach risky. Failure to meet compliance brings high penalties and missed opportunities for your organization and clients.
Transferring risk to a highly specialized team of security experts who can focus on maintaining and testing software while adapting solutions to the current threat landscape pays dividends.
Organizations responsible for building compliance software for their customers benefit from centralized, collaborative solutions that provide automation and visibility to endpoint security software. Consolidating compliance efforts reduces pressure on your internal staff while adopting a unified approach to security initiatives produces hardened, well-tested solutions.
OPSWAT is a trusted security partner that frees up your organization's resources, allows your team to focus on your core business, and lets us do the heavy lifting.

Security at Scale: Protecting Millions of Endpoints
After eighteen years of experience securing millions of endpoints across a wide range of industries, we’ve gained unique insights and expertise into security problems organizations encounter. This rewarding opportunity enabled us to build best-in-class solutions.
We've learned that our clients must provide best-in-class security solutions for their customers. Supporting a wide range of compliance checks, taking immediate action when needed, and the ability to apply granular policies are all essential to building successful products. We know that having broad vendor support is crucial to you and your end-users. Our modular security solution lets your organization stay competitive and confidently enter new markets.
Over the years, we've learned to listen to our clients to develop feature-rich solutions for their customer's unique requirements. The result of these close relationships is best-in-class endpoint security solutions.
Build advanced endpoint security into your solutions. Contact us for more information.

