The latest release of MetaDefender Sandbox 2.5.0 delivers threat detection updates, marking a major step forward in strengthening defenses against today’s most evasive threats. Together, these updates bring faster deployment of new protections, broader detection coverage, and deeper visibility into both known and unknown attack vectors. By unifying sandboxing innovations with expanded threat detection logic, OPSWAT delivers a resilient platform to critical infrastructure organizations that must continuously stay ahead of adversaries.
MetaDefender Sandbox 2.5.0 Release Notes
MetaDefender Sandbox now allows detection logic and threat indicators to be updated independently. This capability enables faster rollout of new defensive measures and significantly reduces the time it takes to respond to emerging threats. By decoupling updates from full releases, security teams gain greater agility and resilience against today’s rapidly evolving attack landscape.
What’s New
With this release, MetaDefender Sandbox introduces targeted upgrades designed to improve adaptability, accuracy, and filetype coverage. From Rocky Linux support to MP3 analysis and certificate validation in offline mode, the updates expand operational reliability across a variety of environments. These improvements empower security teams to detect hidden threats faster and with fewer blind spots.
Rocky Linux Support
Added full support for Rocky Linux, including installation pipelines, testing, and release documentation, ensuring reliable Sandbox deployments on this platform.
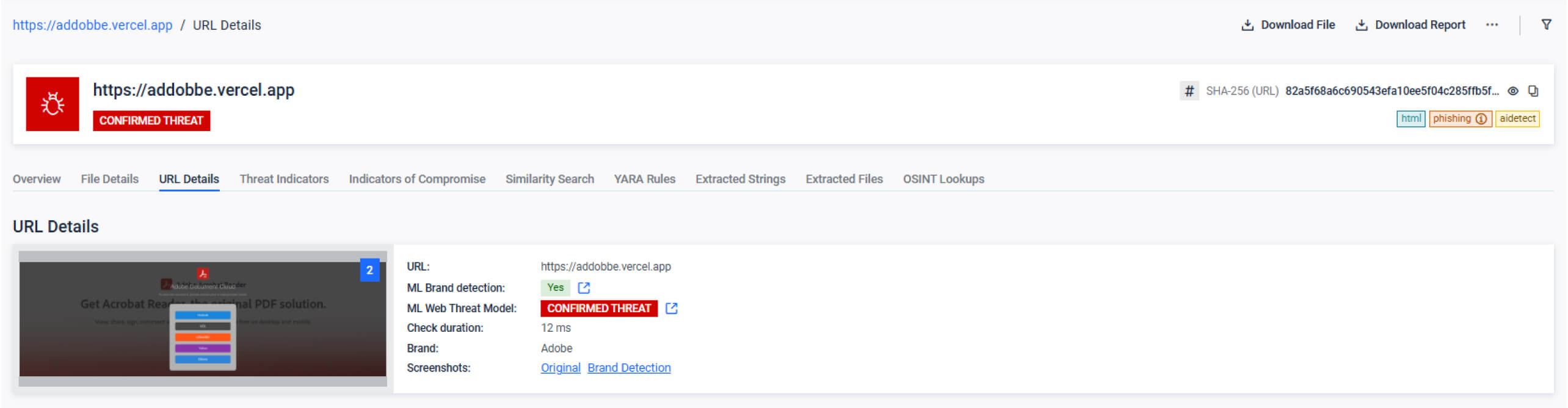
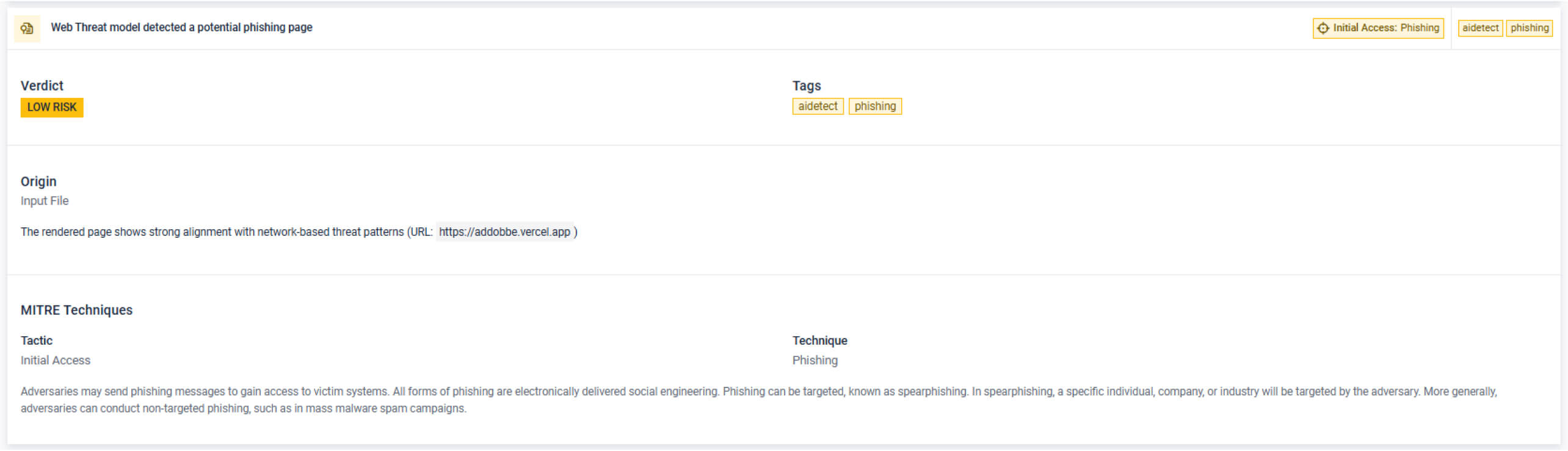
Web Threat Detection
Enhanced ML-based detection with multi-label classification, advanced content analysis, automated data pipelines, improved false positive handling, and style analysis.
Offline Mode Certificate Validation
Added a transform configuration to whitelist signed files without revocation checks; auto-enabled in air-gapped environments but can be disabled for maximum security.
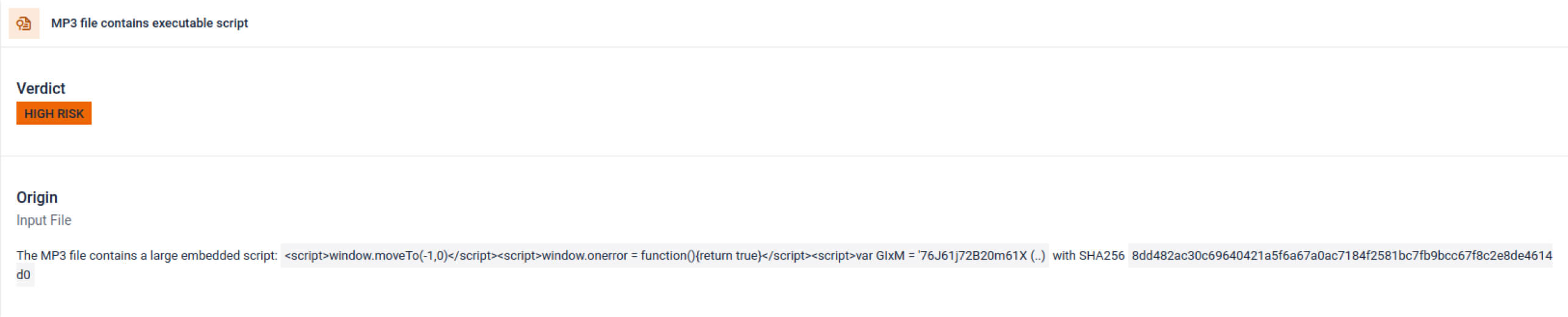
MP3 Filetype Support
Expanded filetype coverage with MP3 parsing and analysis.
By extending support for more platforms and file types while streamlining offline workflows, Sandbox 2.5.0 builds on its reputation as a versatile detection engine. Security practitioners gain not only wider coverage but also operational flexibility that fits into highly regulated or air-gapped deployments. The result is faster, more confident decision-making on an enterprise scale.
Improvements
Beyond new capabilities, this release delivers critical refinements to usability, performance, and threat visibility. Enhanced trends reporting, multilingual translation, and dynamic verdict mapping ensure more clarity and responsiveness for analysts. At the same time, improved emulation graphs highlight suspicious activity more intuitively, reducing time-to-insight.
Trends Page Updates
Redesigned Trends pages with new tabs, filters, charts, and components, improved mobile responsiveness, and connected statistics and backend jobs for better performance.
Language Translation
All language translations were improved using the latest AI technologies.
Verdict Renaming
Implemented UI-only renaming of verdicts with dynamic mapping to maintain backward compatibility in the API and database, including the addition of a SYSTEM_ERROR verdict and support for both old and new verdicts in API responses.

Emulation Graph Enhancements
Updated the emulation graph to highlight processes by threat level, making malicious or suspicious activity easier to identify.
These updates reflect OPSWAT’s commitment to making advanced sandbox analysis not only powerful but also accessible. Analysts now benefit from more intuitive interfaces and accurate verdicts that align with evolving workflows. Combined, the improvements elevate both user experience and forensic depth.
PE Emulator (Beta)
The beta release of the PE Emulator extends low-level emulation capabilities for more granular detection of malicious executables. By refining section handling and surfacing covert API lookups, the emulator provides visibility into hidden behaviors that traditional monitoring often misses. This empowers analysts to detect stealthy techniques before they escalate into incidents.
- PE Section Handling – Improved emulation memory management for emulated PE mapping.
- Covert API Lookups – Sandbox now reports API lookups directly from the export table (as opposed to conventional GetProcAddress)
As this capability matures, it promises to redefine how defenders understand executable behavior at scale. Even in its beta form, it offers valuable forensic signals for uncovering advanced malware operations. This positions Sandbox 2.5.0 as a proactive tool for zero-day defense.
Threat Detection Updates
MetaDefender Sandbox now supports independent updates to Detection Logic and Threat Indicators. This advancement accelerates the deployment of new protections and enables faster, more precise responses to emerging threats. Security teams can adapt in real time, reducing exposure windows and strengthening overall resilience against zero-day attacks.
What’s New
Powerful new signatures and heuristics have been introduced, expanding detection across modern attack surfaces. From double-encoded payloads to supply chain exploits hidden in machine learning models, the release addresses evolving adversary tradecraft. Enhanced evasion detection and extended installer package support further bolster readiness against advanced malware.
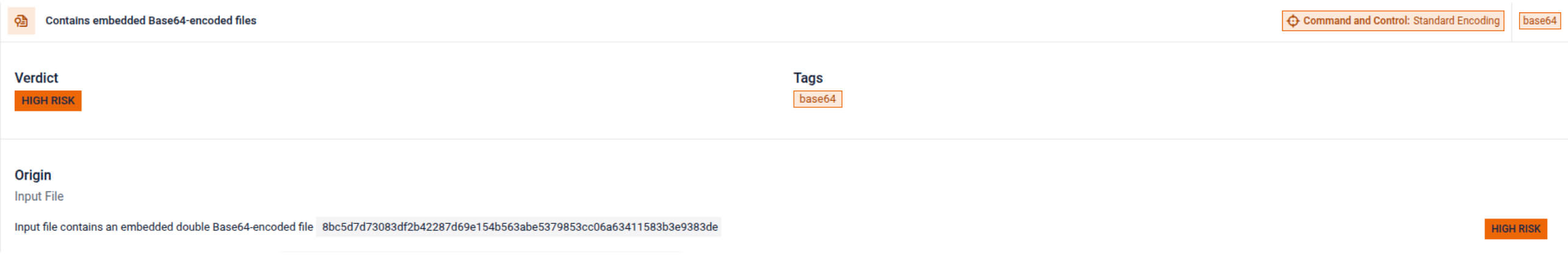
Double Base64 Decoding
Detects payloads hidden in multiple layers of Base64 encoding, commonly used by advanced malware to evade security controls.
Extended Threat Indicators for Pickle & PyTorch
Detects weaponized Python serialization and machine learning model files often used for supply chain and AI-related attacks.
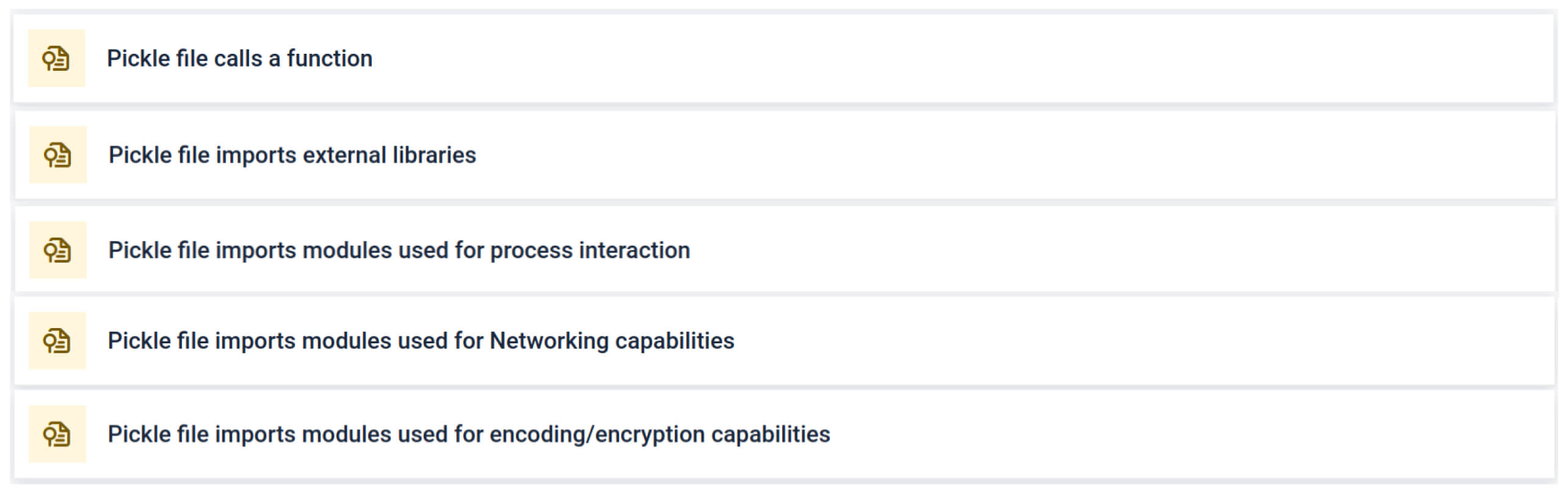
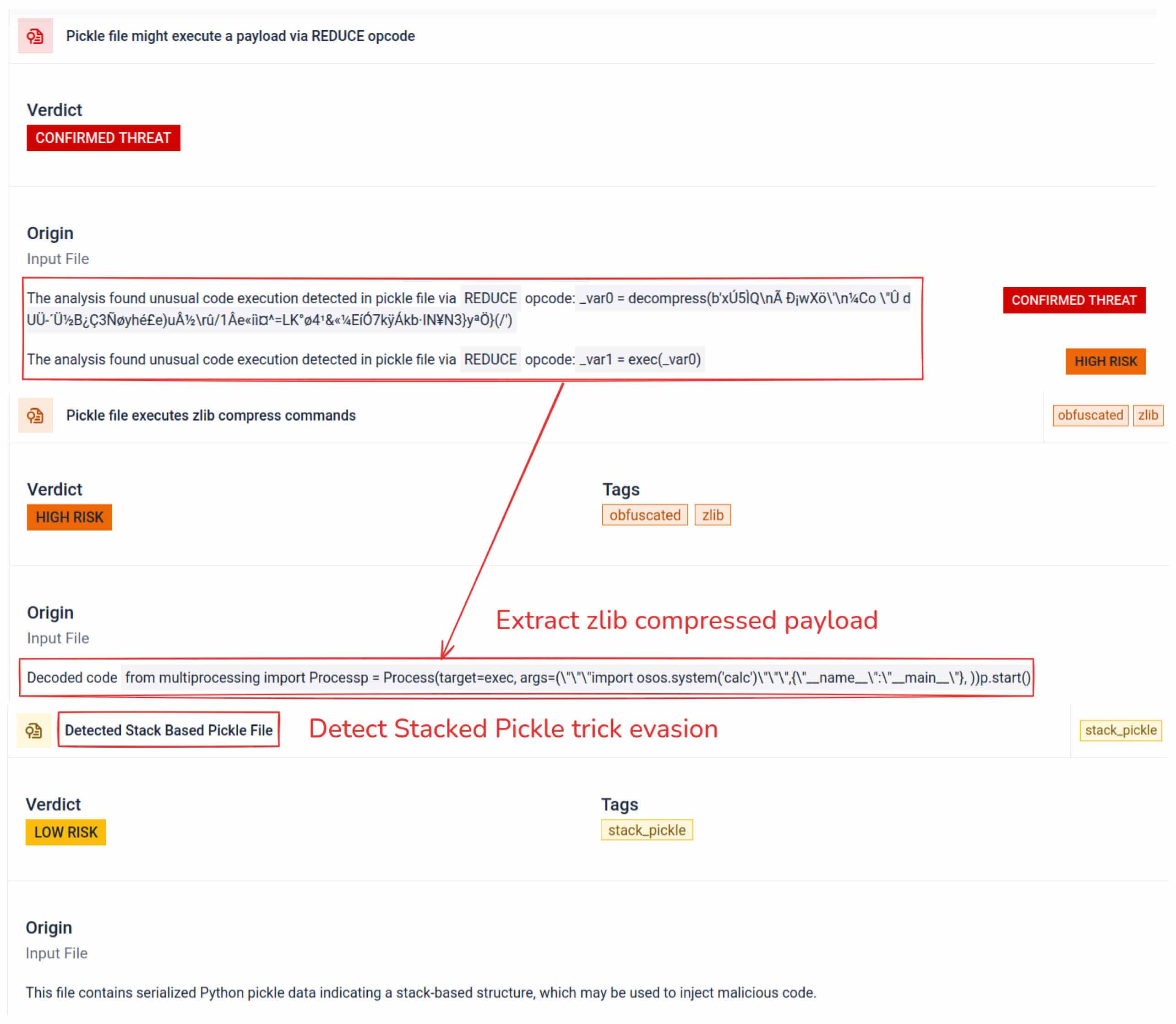
Improved AI Evasion Detection
Enhanced identification of the nullifAI evasion technique and stack pickle manipulations, strengthening AI/ML malware defense.
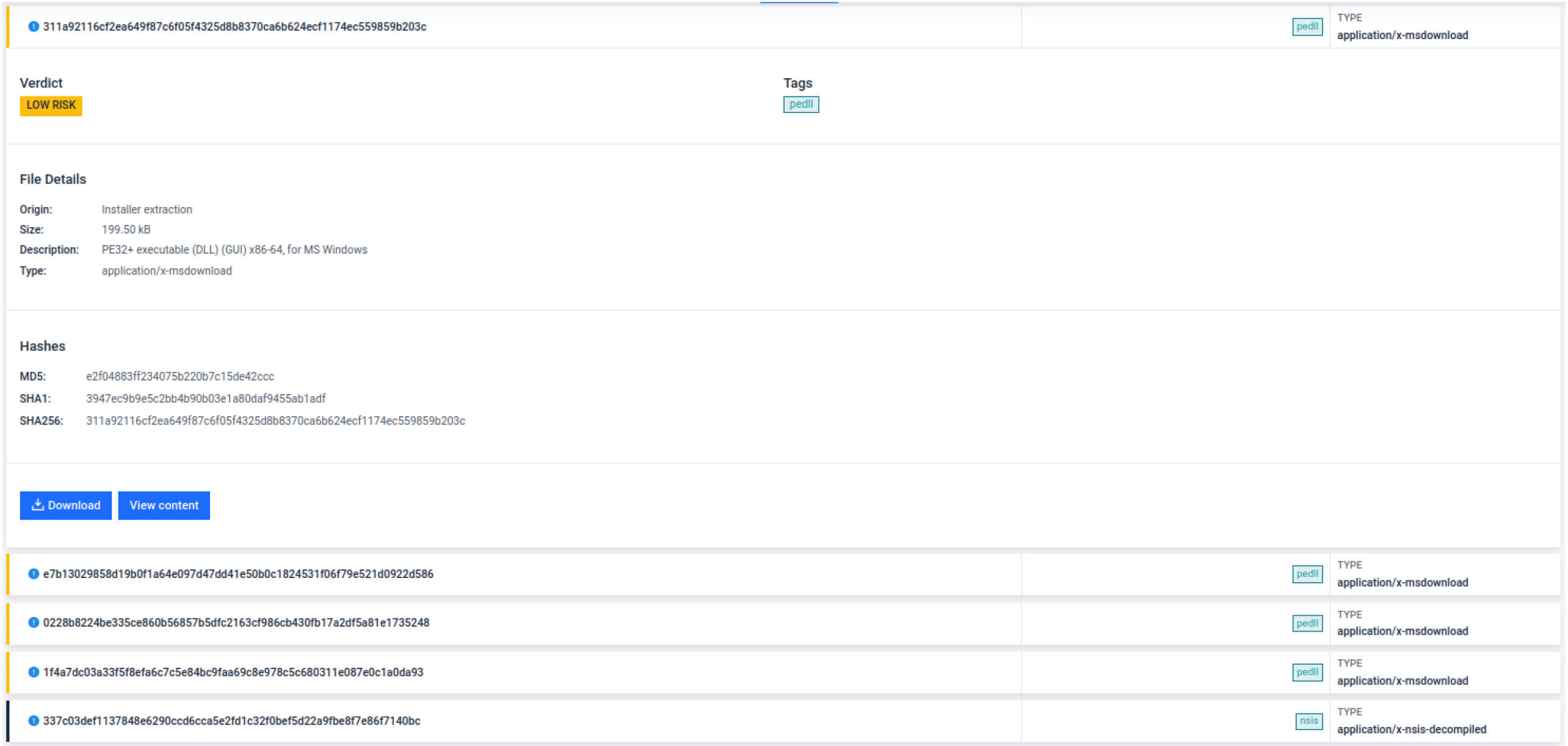
New Installer Package Support
Added extraction and analysis for:
- Advanced Installer packages
- NSIS (Nullsoft Scriptable Install System) packages
- Inno Setup packages
This expands coverage for malware distributed via custom installer frameworks.

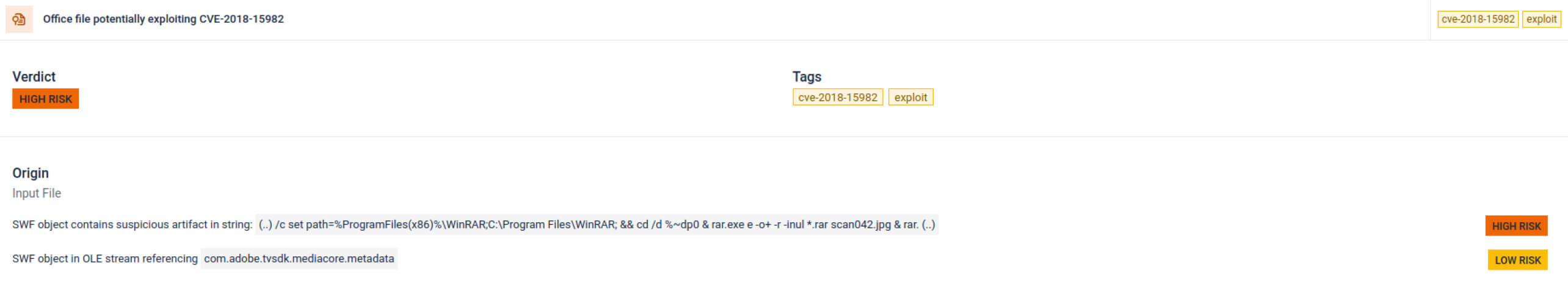
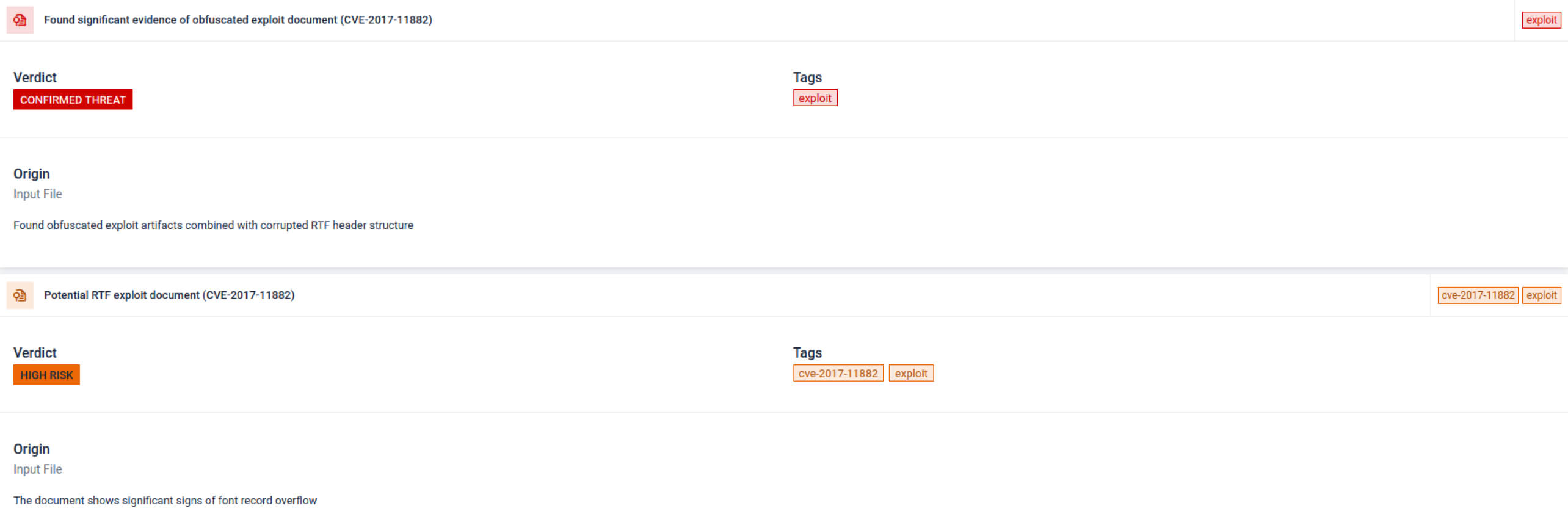
CVE-2018-15982 Detection
Identifies exploitation of a critical Adobe Flash vulnerability.
Equation Editor Exploit Detection
Detects obfuscated versions of this long-abused Microsoft Office exploit.
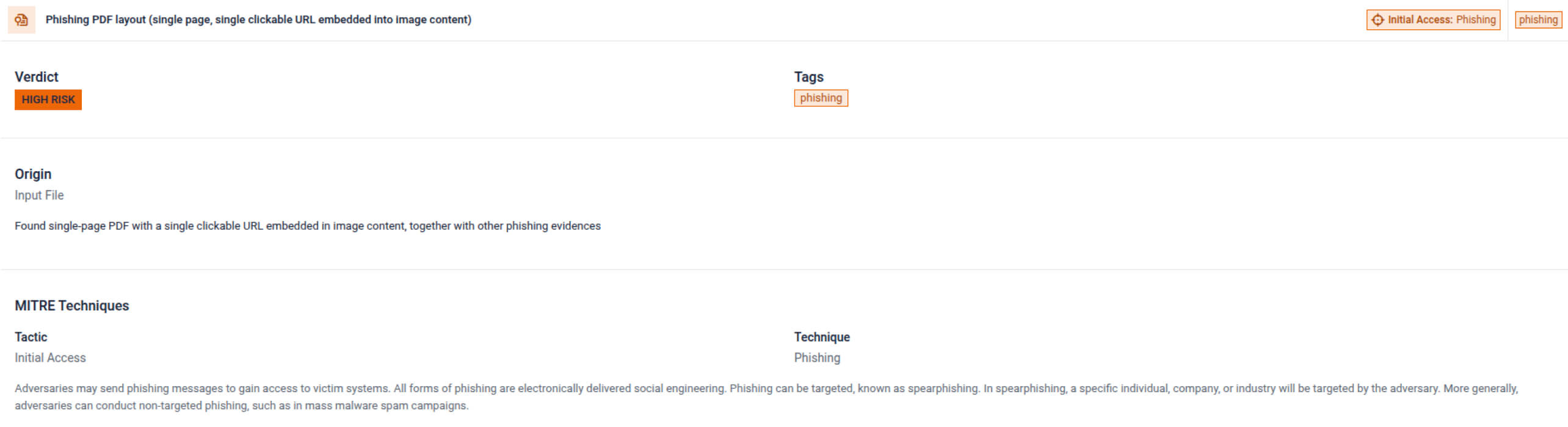
Extended PDF Threat Indicators
Better phishing detection in PDF documents, with new heuristics for malicious links and embedded content.

By targeting sophisticated encoding, serialization, and evasion tactics, this release ensures defenders can spot threats before they propagate. Expanded coverage across installer frameworks and document exploits closes critical blind spots in enterprise environments. Ultimately, it equips organizations with actionable intelligence against some of the most dangerous attack vectors in circulation.
Delivering Faster Protection, Broader Coverage
MetaDefender Sandbox 2.5.0 threat detection updates deliver a unified leap forward in zero-day readiness. This release extends filetype coverage, strengthens detection against evasive techniques, and streamlines workflows for both connected and isolated environments.
By integrating sandbox emulation depth with threat intelligence precision, OPSWAT equips organizations with a proactive defense posture that keeps pace with the evolving threat landscape.

